This repository contains some python tools that may be of some help in pentesting, CTFs or information security assignments in general:
- revshell.py (reverse shell generator)
- shconverter.py (objdump2shellcode converter)
- explorer.py (processes dirsearch results and then pops a browser with every url we can visit)
- qrutils.py (easily decode/encode QR codes)
- vtamper.py (verb tampering/avalaibility checker)
- dnz.py (dns zone transfers)
- irc_bot.py (an IRC bot main template using twisted framework)
- fakeid.py (fake id generator)
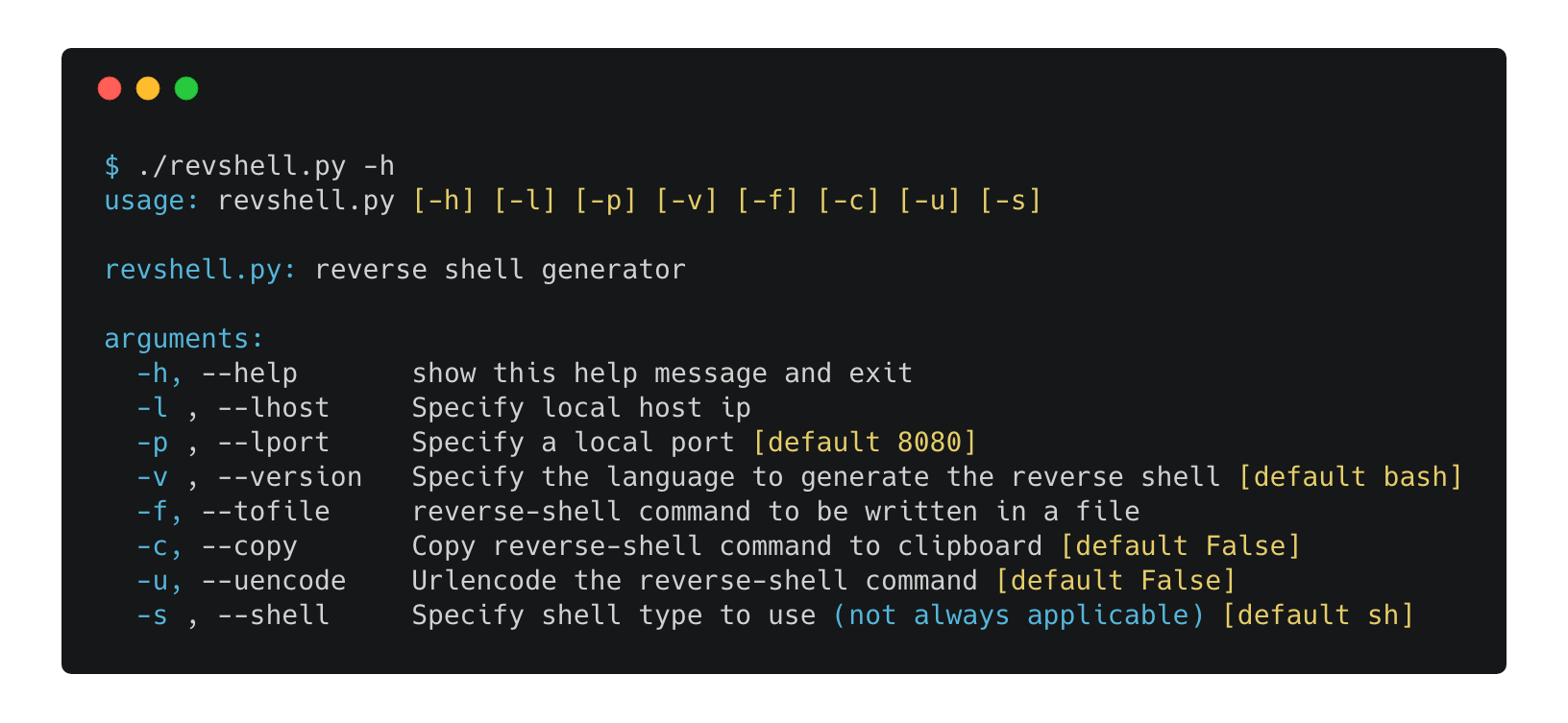
This is a simple script to automate the process of generating a reverse-shell command like those described in pentestmonkey blog:
Note: You can find a more updated and featured version of the revshell.py script here!
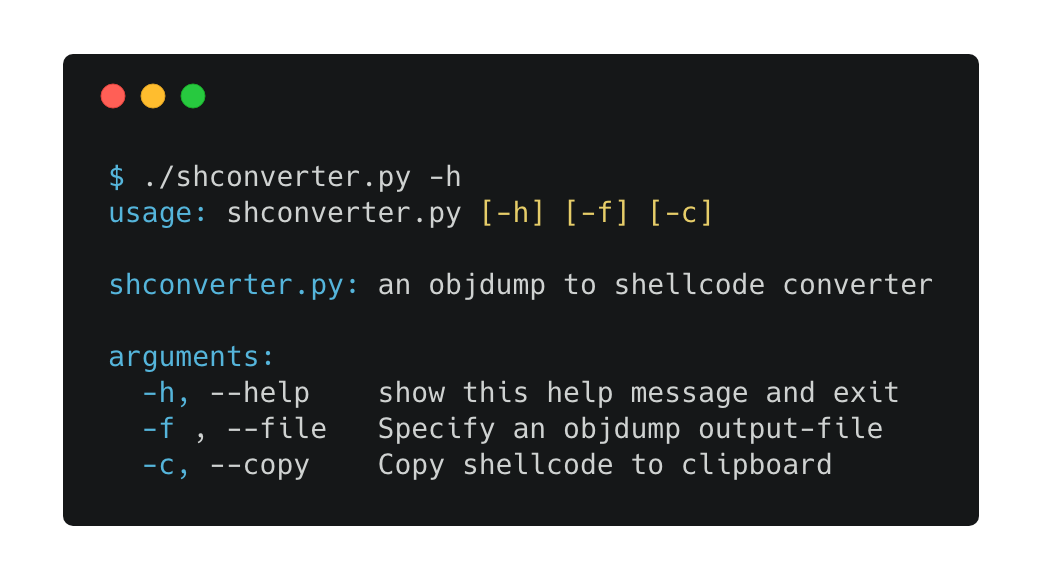
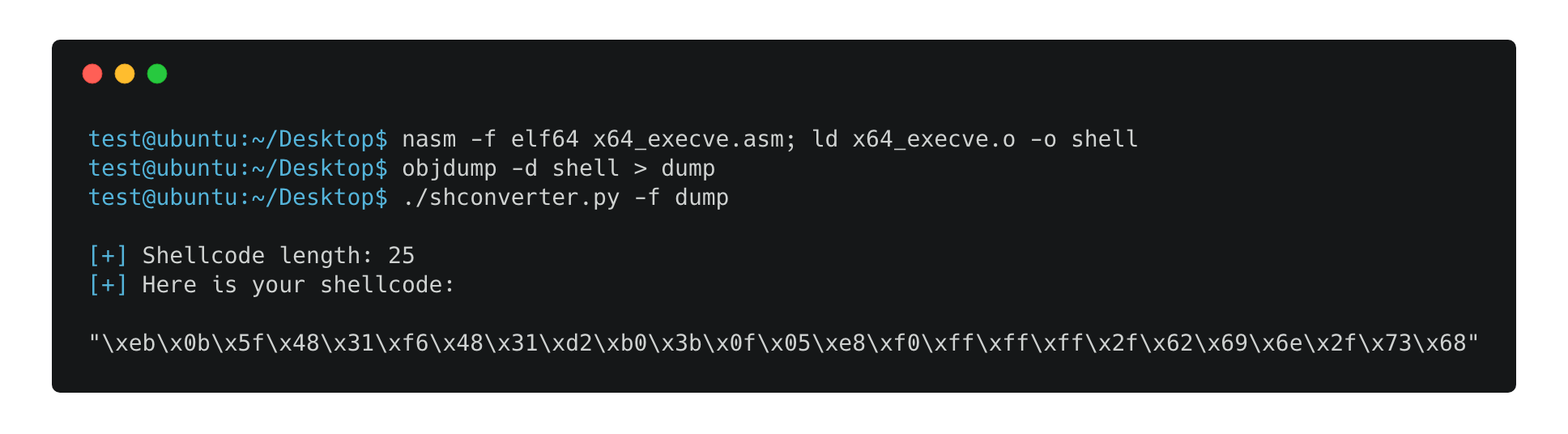
This is a small script that takes as input an objdump output and extracts the shellcode:
Example - asm snippet from here:
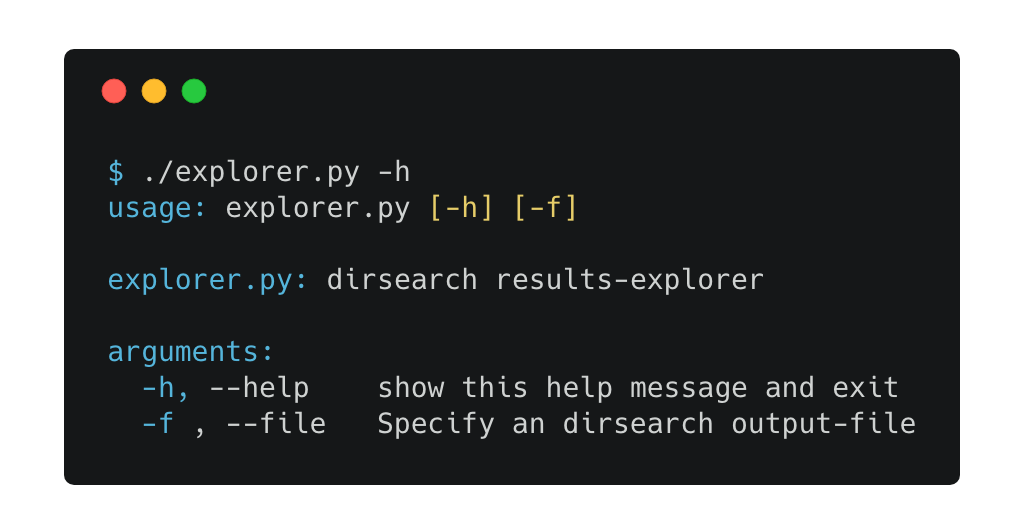
This script uses selenium with chromedriver (can work with other web-drivers also) to open every url (with a status code of 200) from a dirsearch output (specified with --plain-text-report):
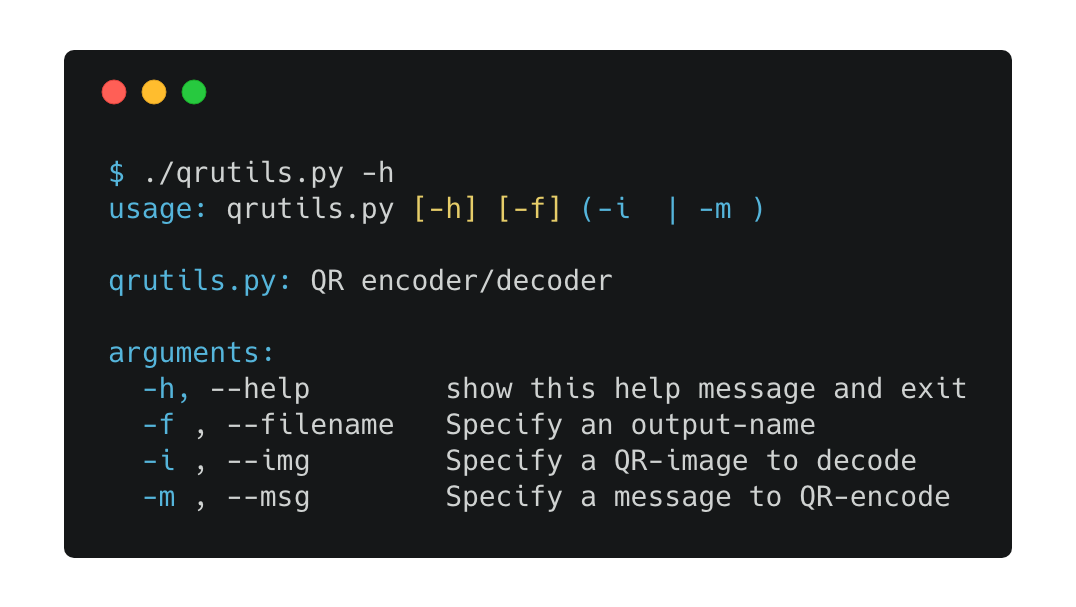
Easily decode a QR code using zxing online service or QR-encode a message using qrencode utility:
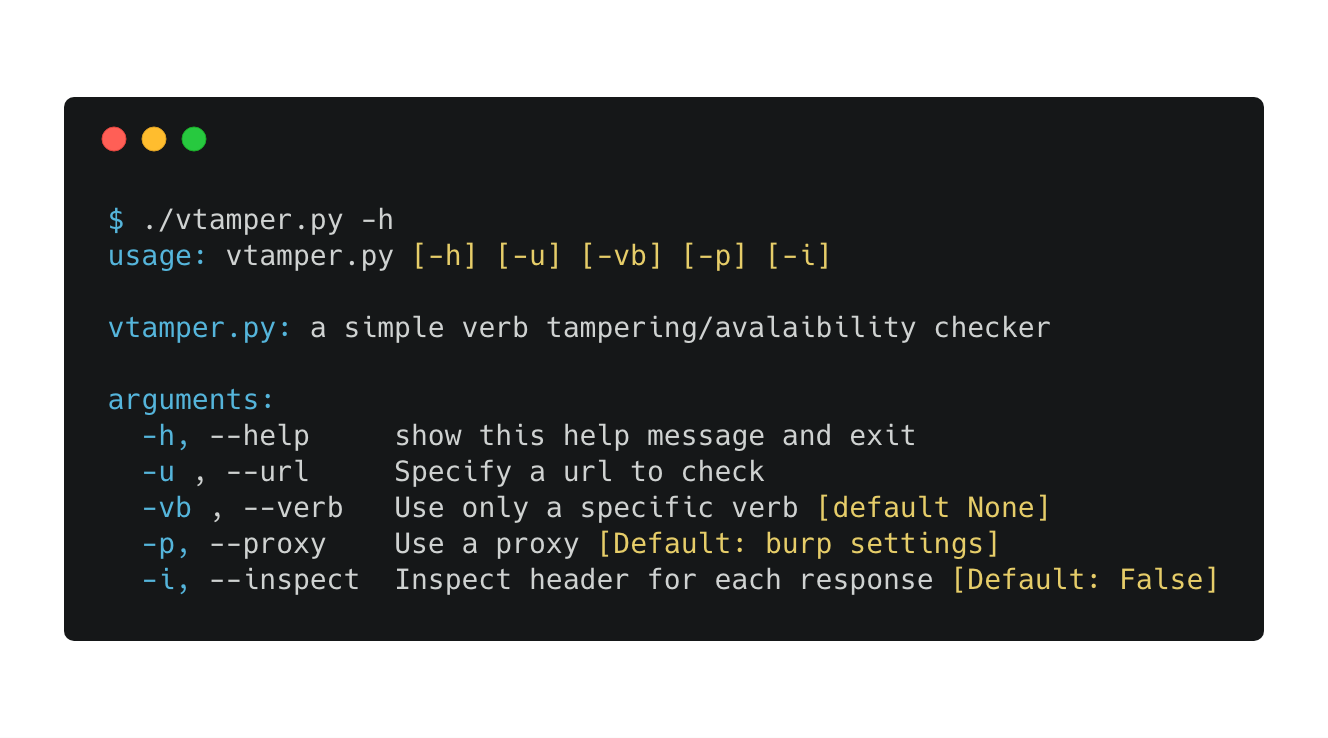
Simple verb avalaibility/tampering checker. Using the -i switch it checks also for common header-vulnerabilities:
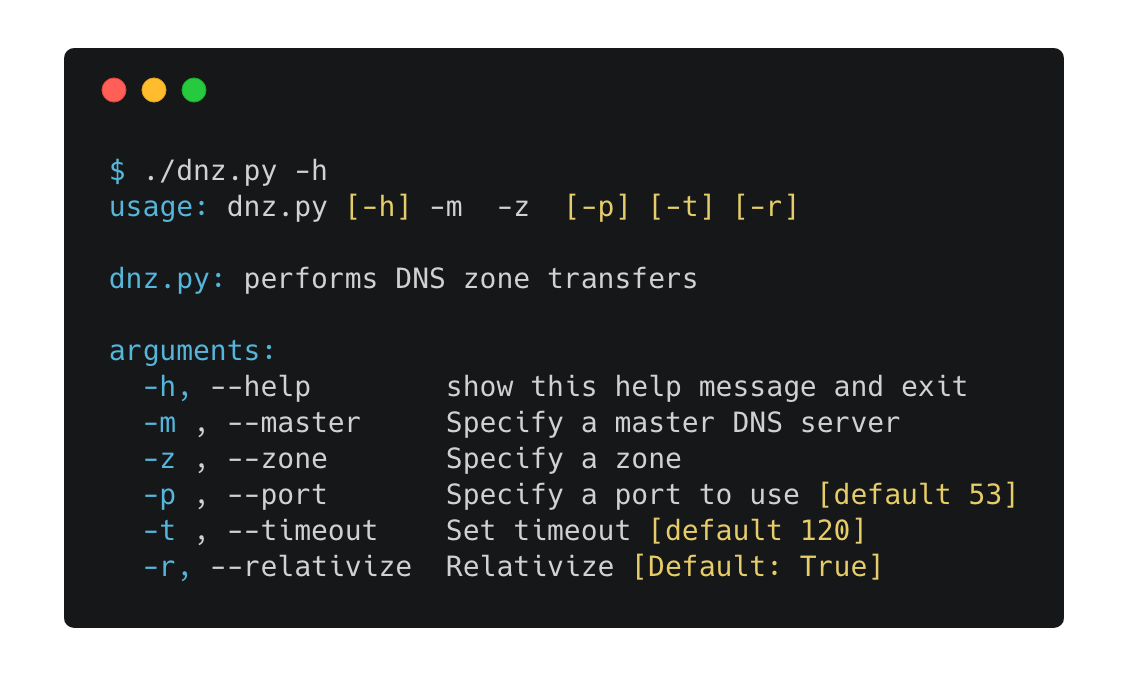
This script uses dnspython to perform DNS zone transfers easily:
This script can be used as a template to built an automated IRC-bot using twisted framework.
This script uses fakenamegenerator.com to generate a completely random person's id.
Note: To install the requirements (except for qrencode and chromedriver):
pip install -r requirements.txt --upgrade --user
These tools are only for testing and academic purposes and can only be used where strict consent has been given. Do not use them for illegal purposes! It is the end user’s responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by these tools, programs, scripts and software.
This project is licensed under the GPLv3 License - see the LICENSE file for details