Complete CNAPP Demo using Prisma Cloud demonstrating Cloud Code Security, Cloud Workload Protection (Agent, Agentless, Web Application and API Security) , Cloud Infrastructure Entitlement Management, Cloud Data Security, Cloud Security Posture Management . Demonstrates how the platform adds value to different persona's starting from developers to executives. Uses Github actions for CI and CD process.
This demo only focuses on some capabilities of modules within Prisma Cloud. Please refer to documentation for full list of capabilities
Intent:
Demo intent is to showcase Prisma Cloud Capabilities across
- Multiple clouds. (EKS,GKE,AKS)
- Multiple form factors. (Container, Host, Serverless, Google Run)
- Different phases of application lifecycle.
- Multiple teams.
- Processes which are already part of organizational day to day activities.
AND you have a copy-paste coder like Sandeep in your team :)
Also want to showcase how not following best practices at dev/devops level might have increased blast radius.
Installation:
- Terraform templates are provided in IaC folder. These are for reference only. Please modify as per your requirements.
- Yaml files for K8s deployment are provided in root folder
- Github action files can be found in .github folder and secrets configured can be found here
Code Security:
Coding phase (Persona: Developer/Devops)
- Install Checkov plugin for VSCode (or IntelliJ)
- Copy copy_to_req file to requirements.txt
- The developer/devops will be notified of misconfigurations/vulnerabilites within IDE while coding.
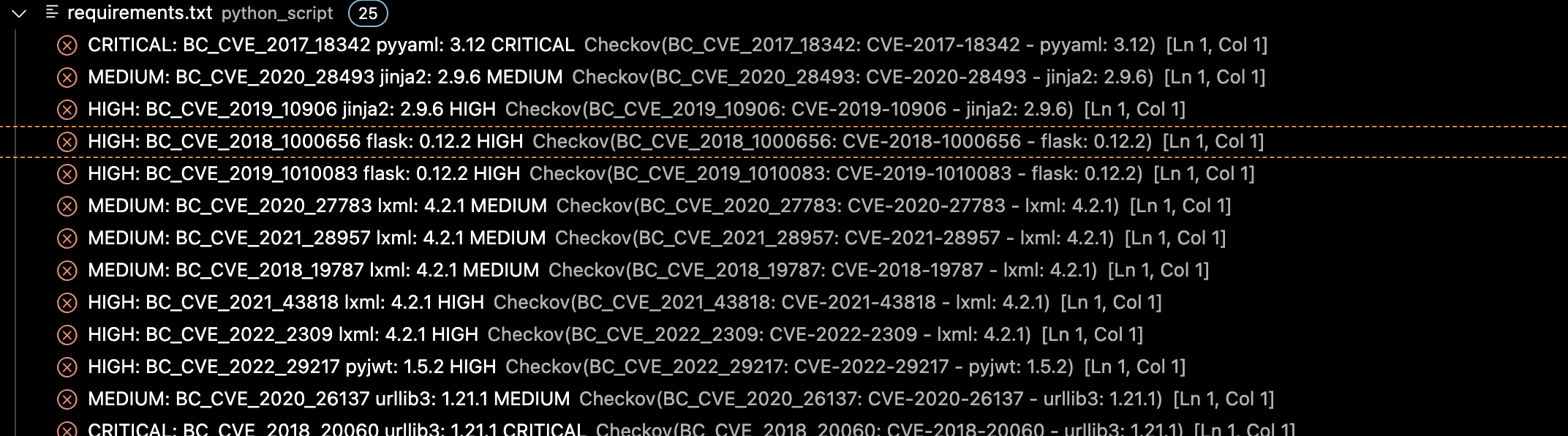
Example files for terraform,yaml,secrets can be found in fake_commits folder. Please use as per your requirement.
Review/CI phase (Persona: Dev/Devops Leads/Managers)
- Integrate your Github repo with Primsa Cloud Code Security module.
- Push the code to your branch and raise pull request
- The reviewers will be notified of misconfigurations/vulnerabilites in review process.This makes reviewers aware of the security issues in addition to coding issues.
- Code-checkins are gated by security as PC scan becomes one of the checks during CI process
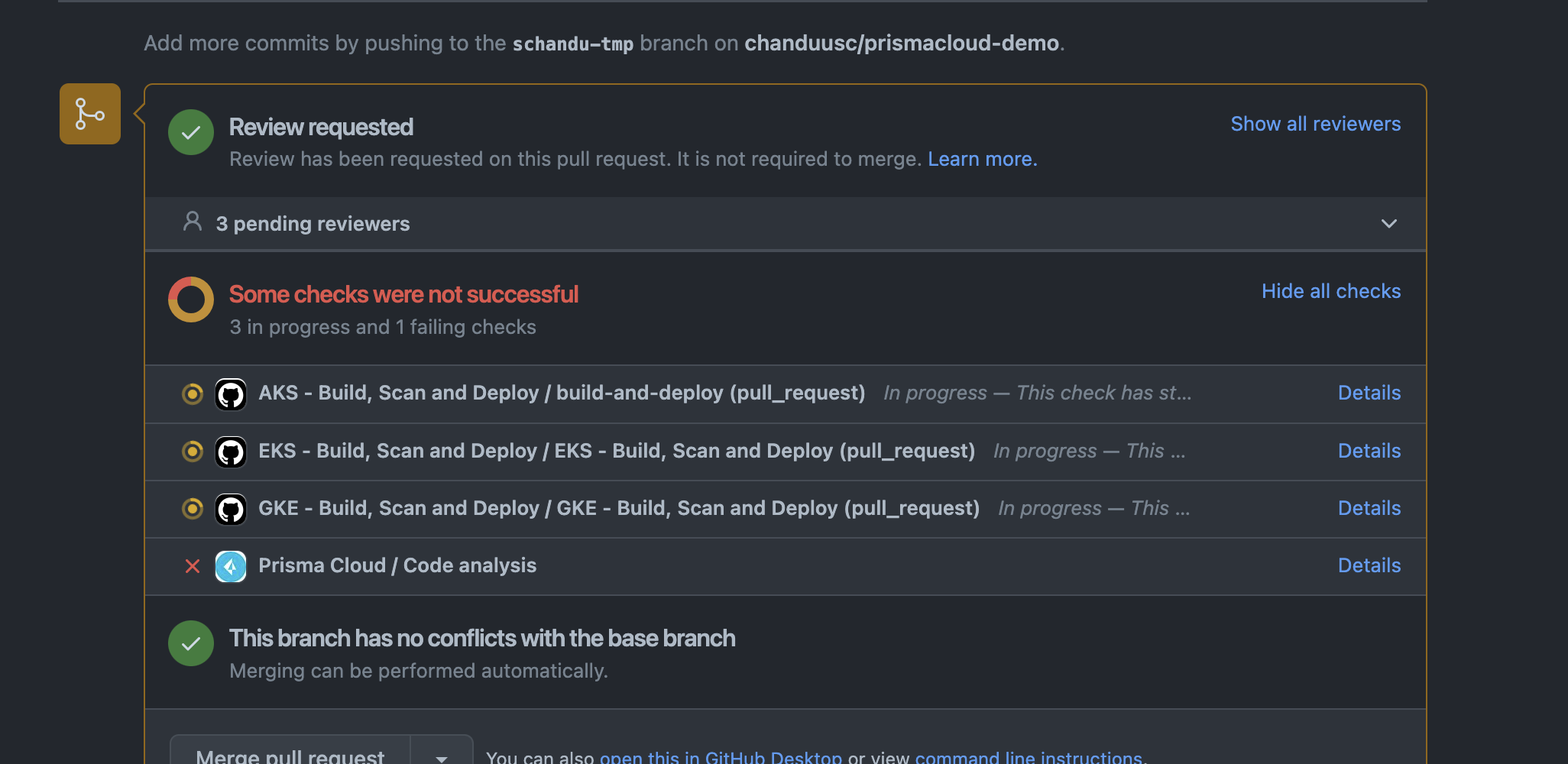
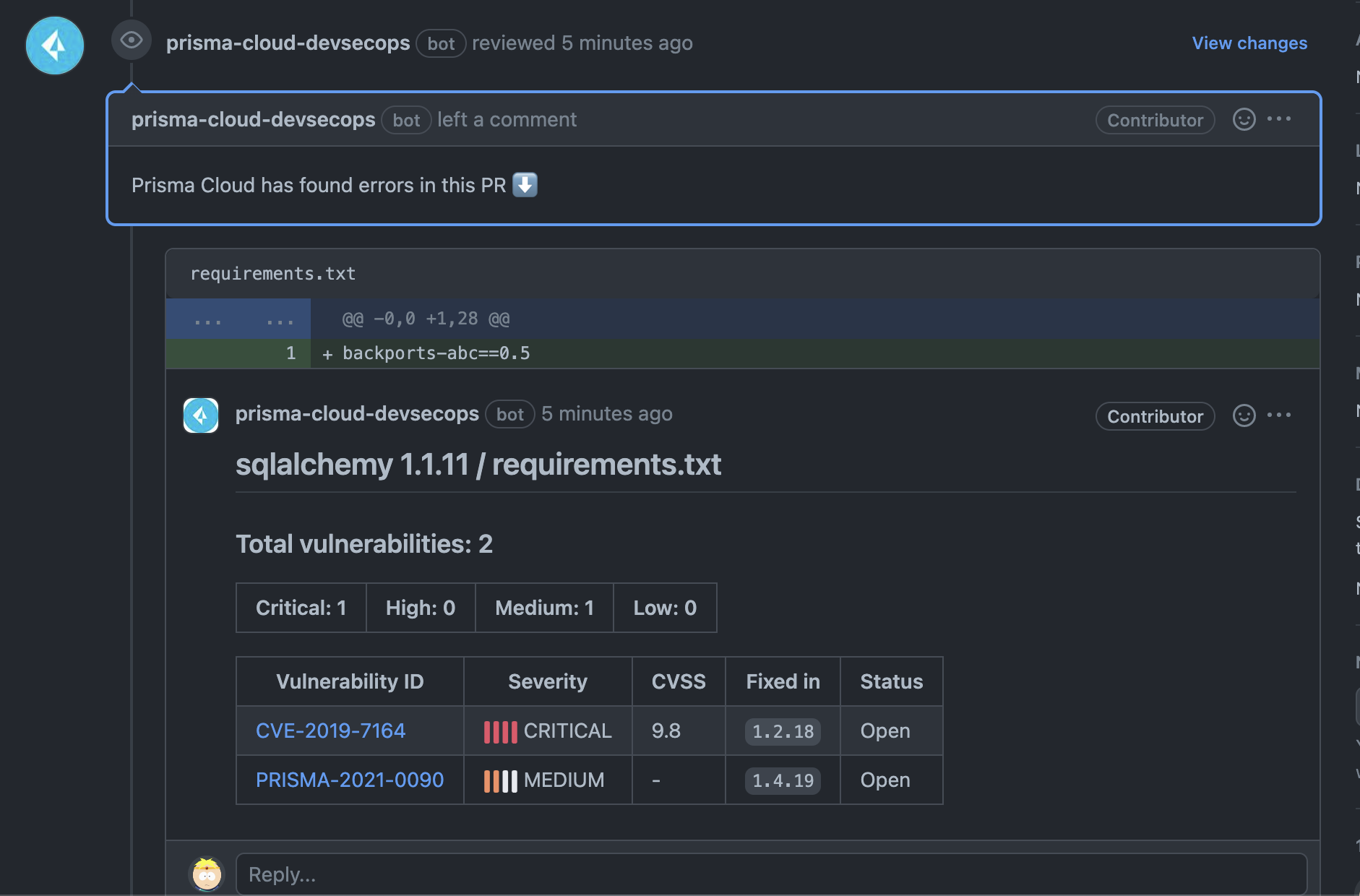
Review/CI phase (Persona: Secops/Security Team)
- Security team can see the same failures in Prisma Cloud console.
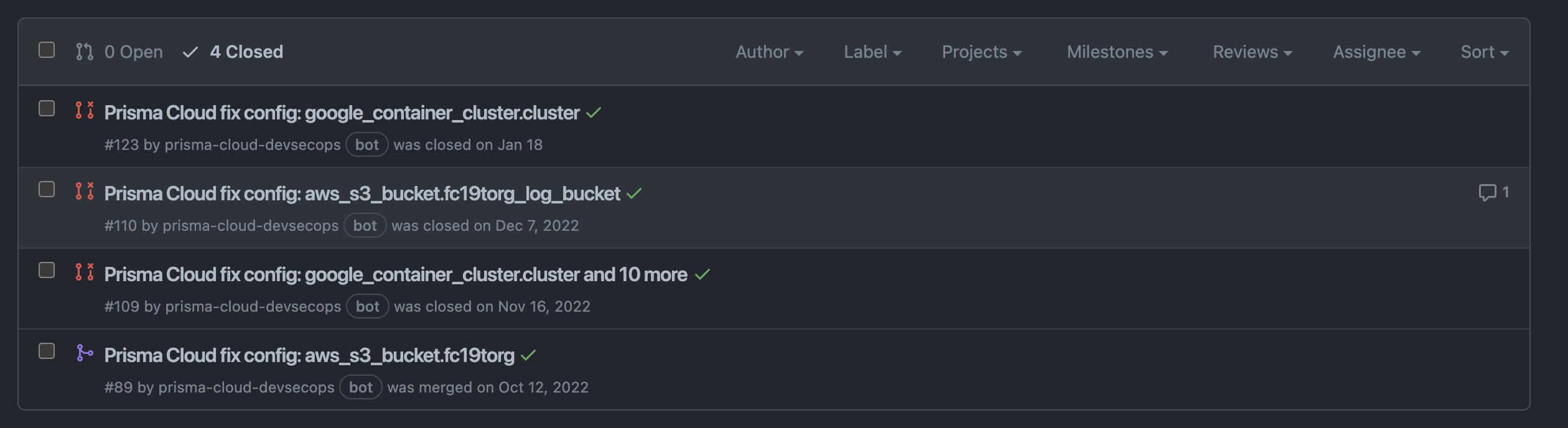
- Security team can submit fixes from Prisma Cloud console which will open a new PR against your repo.
- Prisma bot will mark the comments outdated once fixed.
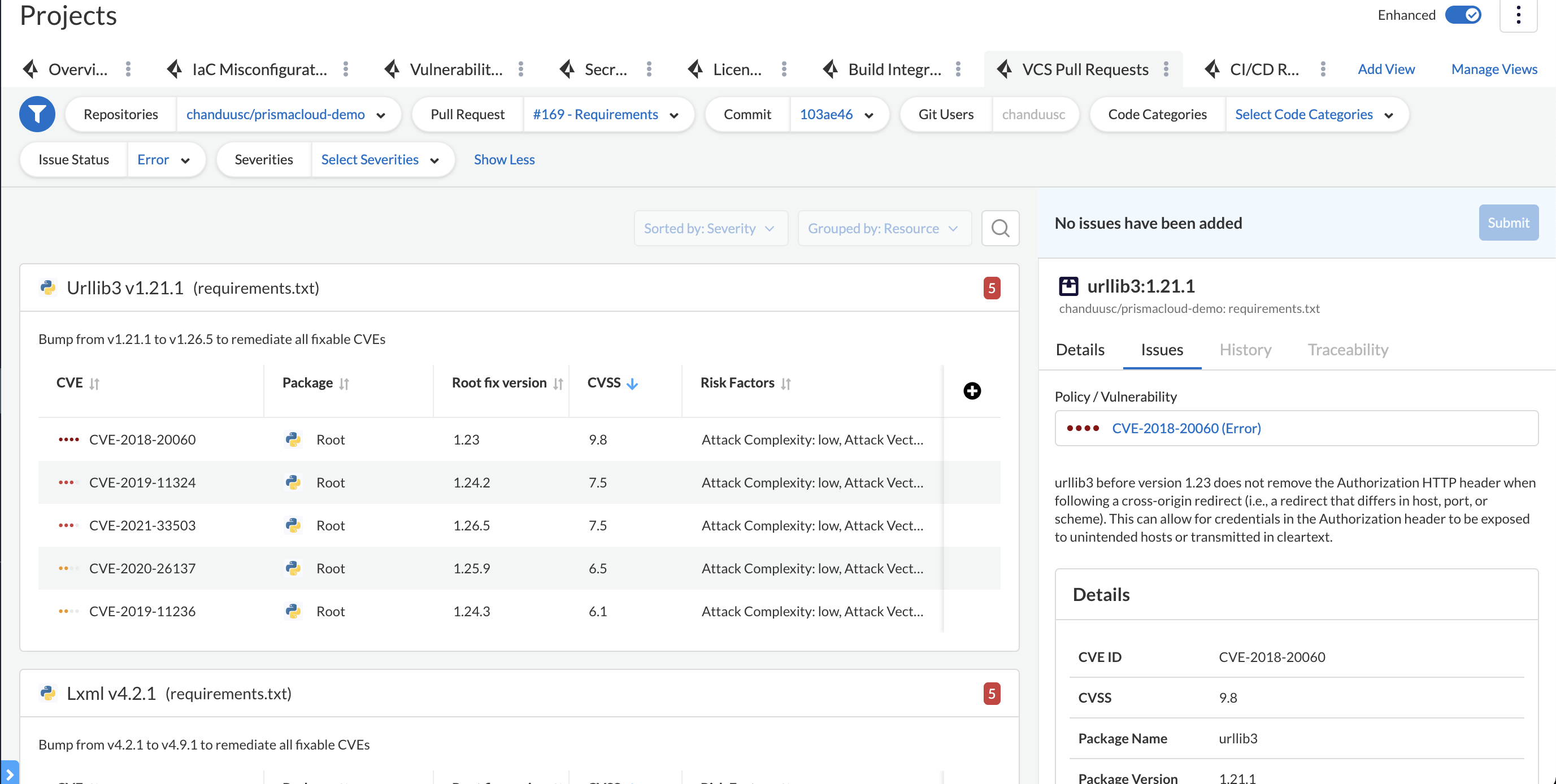
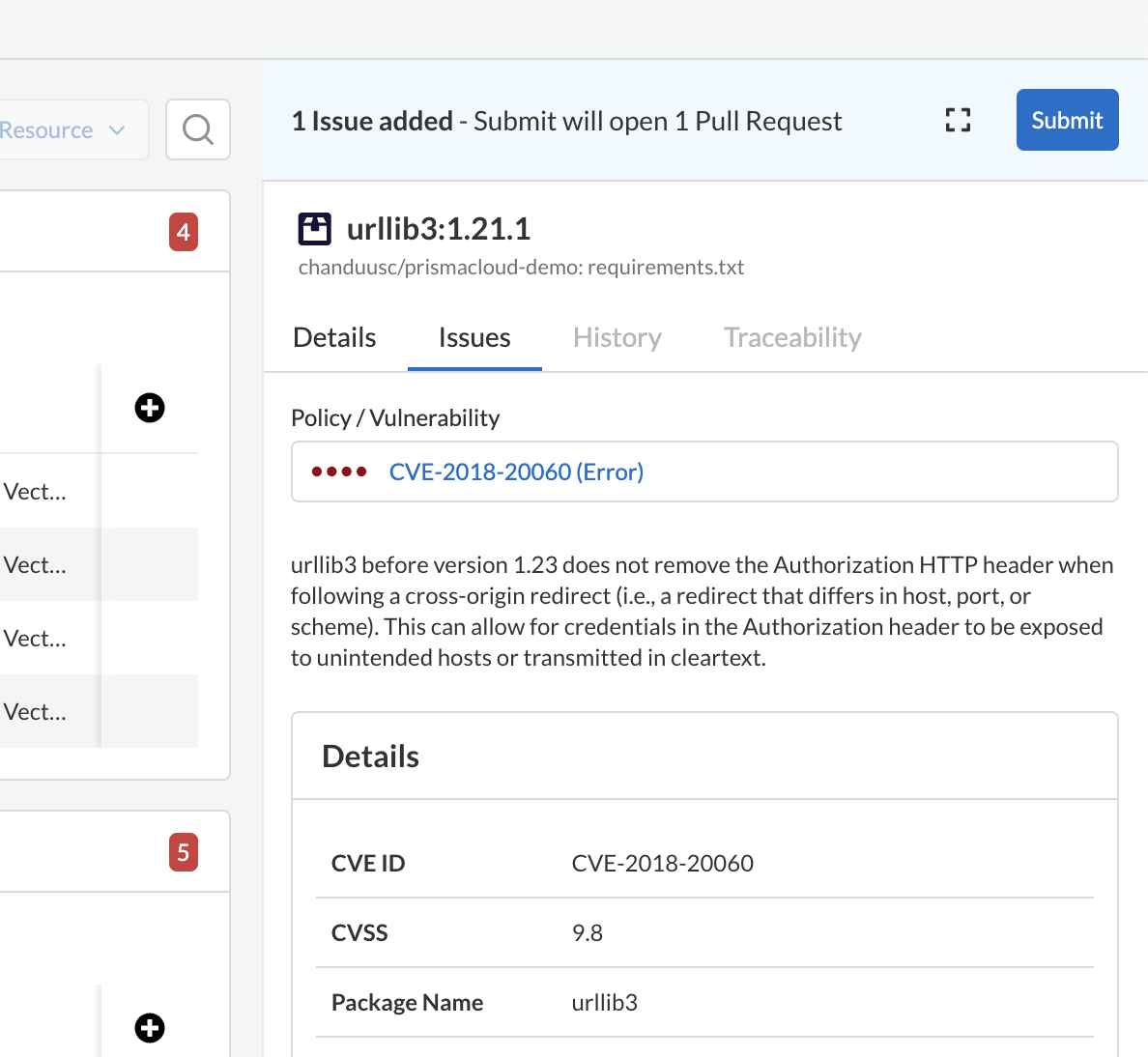
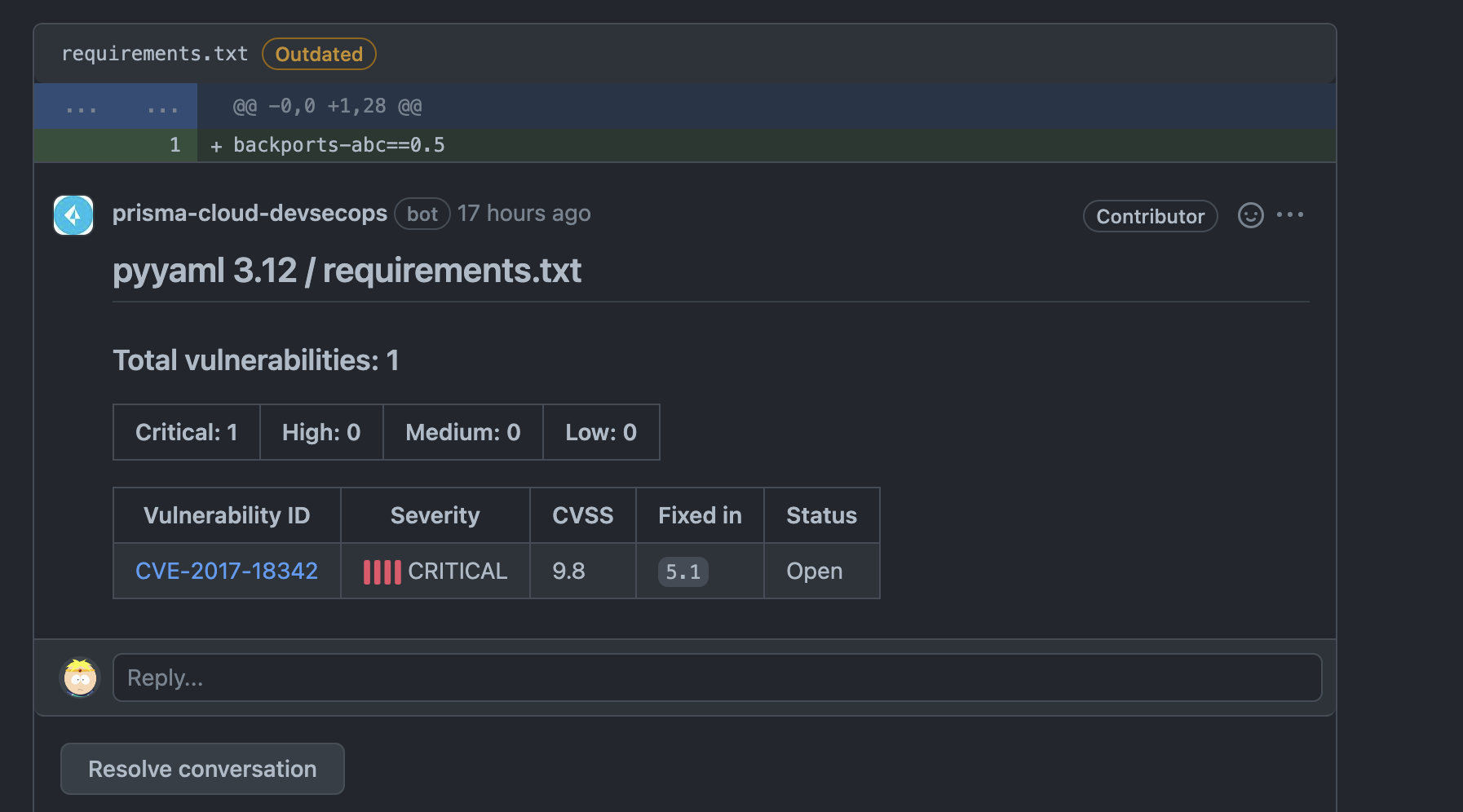
Please pay attention to docker file where apt is used against best practices

Cloud Workload Protection:
Vulnerability policies are used as example here. Can be used with compliance policies too
CD phase (Persona: Developer/Devops)
- Github actions trigger build and deploy jobs in EKS,GKE and AKS.
- Prisma Cloud image scan is inserted as part of github actions.
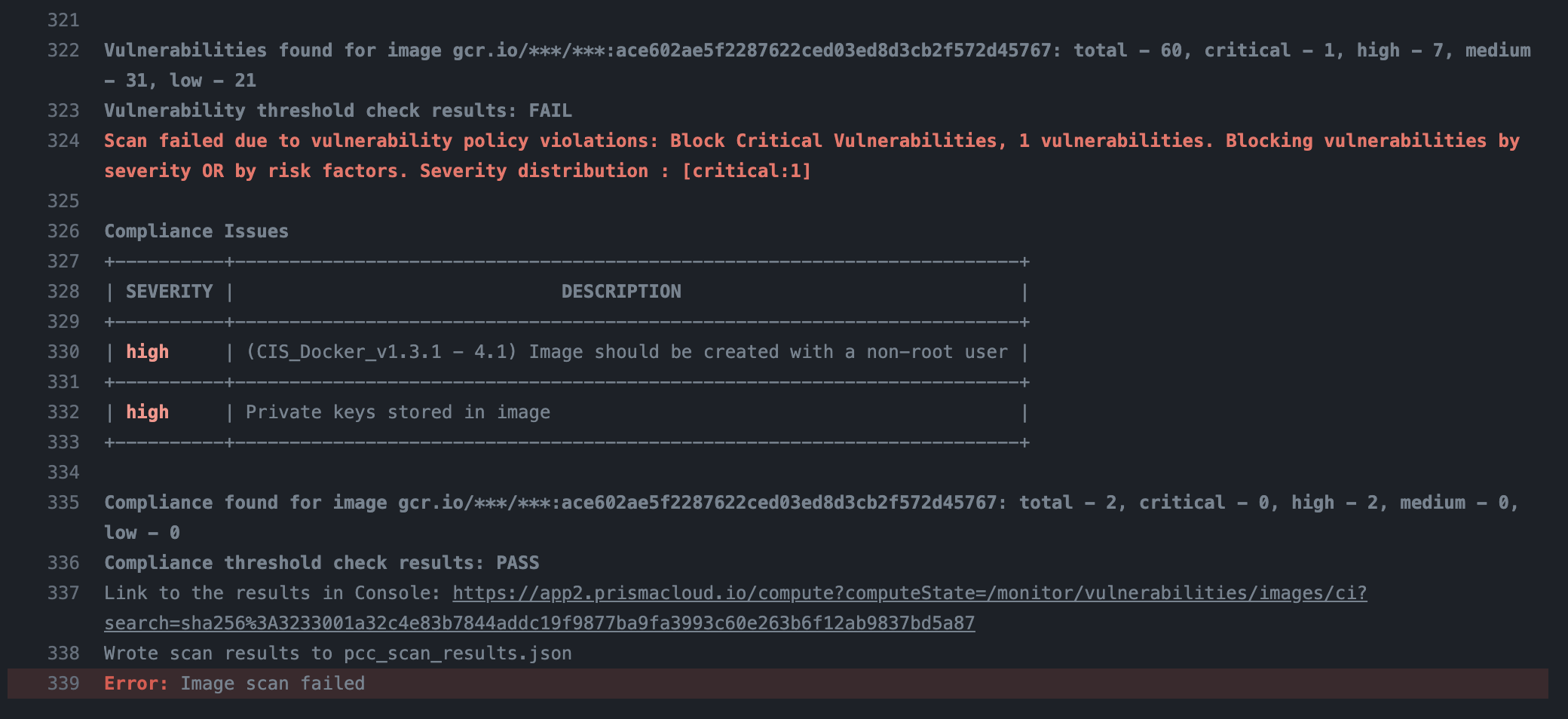
- Policies for vulnerabilites (or compliance) can be set from Prisma Cloud.
- Prisma Cloud will scan the image and fail the CD job hence the non-approved images are not pushed to registries.
Remember Code security warned you about APT :)
CD phase (Persona: Secops/Security Team)
- Sets the polices related to images being built on day to day basis within the tools/process which are already part of organization.
- Can view the real time status of builds in Prisma Cloud console.
- Can debug/know which layer of build introduced the vulnerabilities.
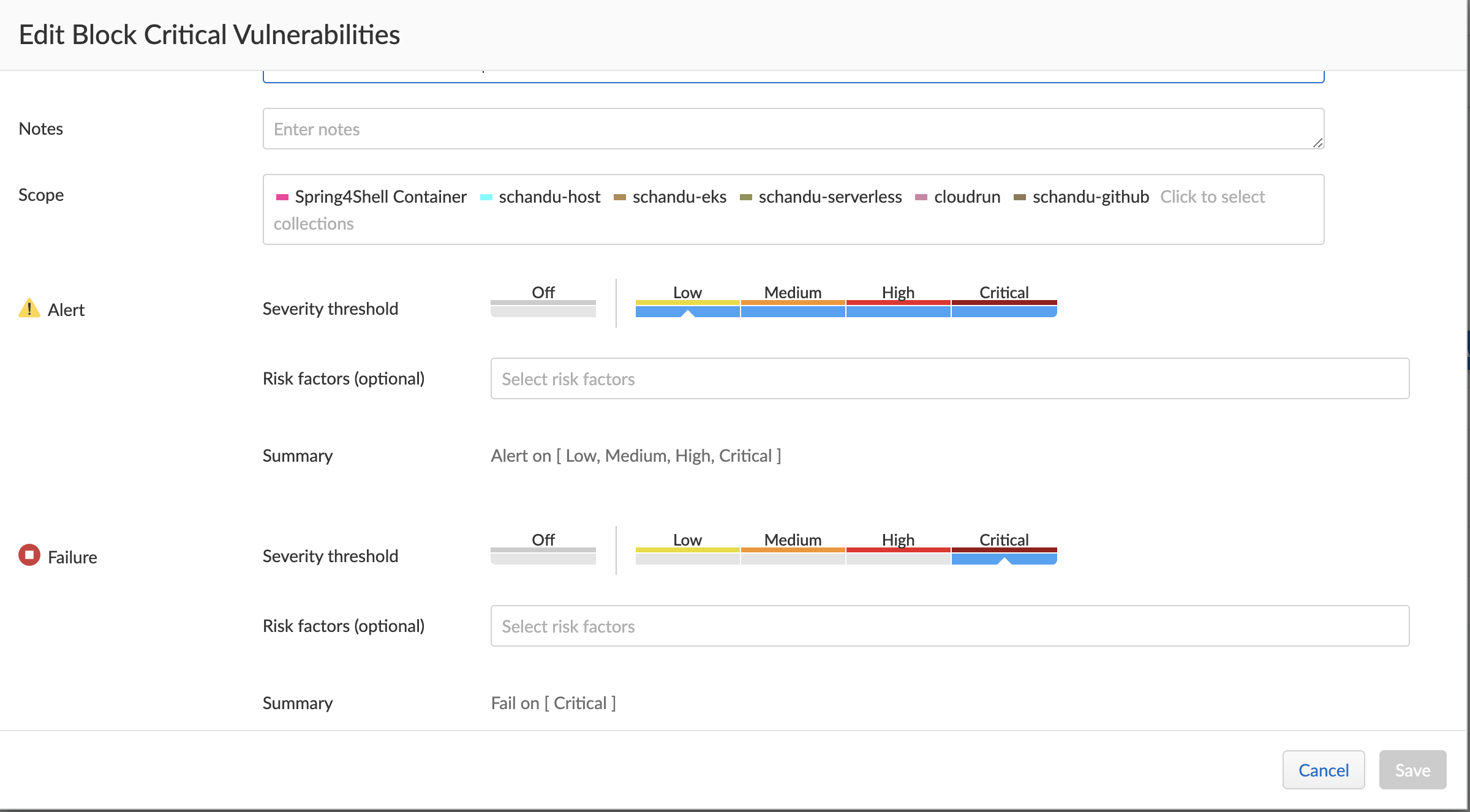
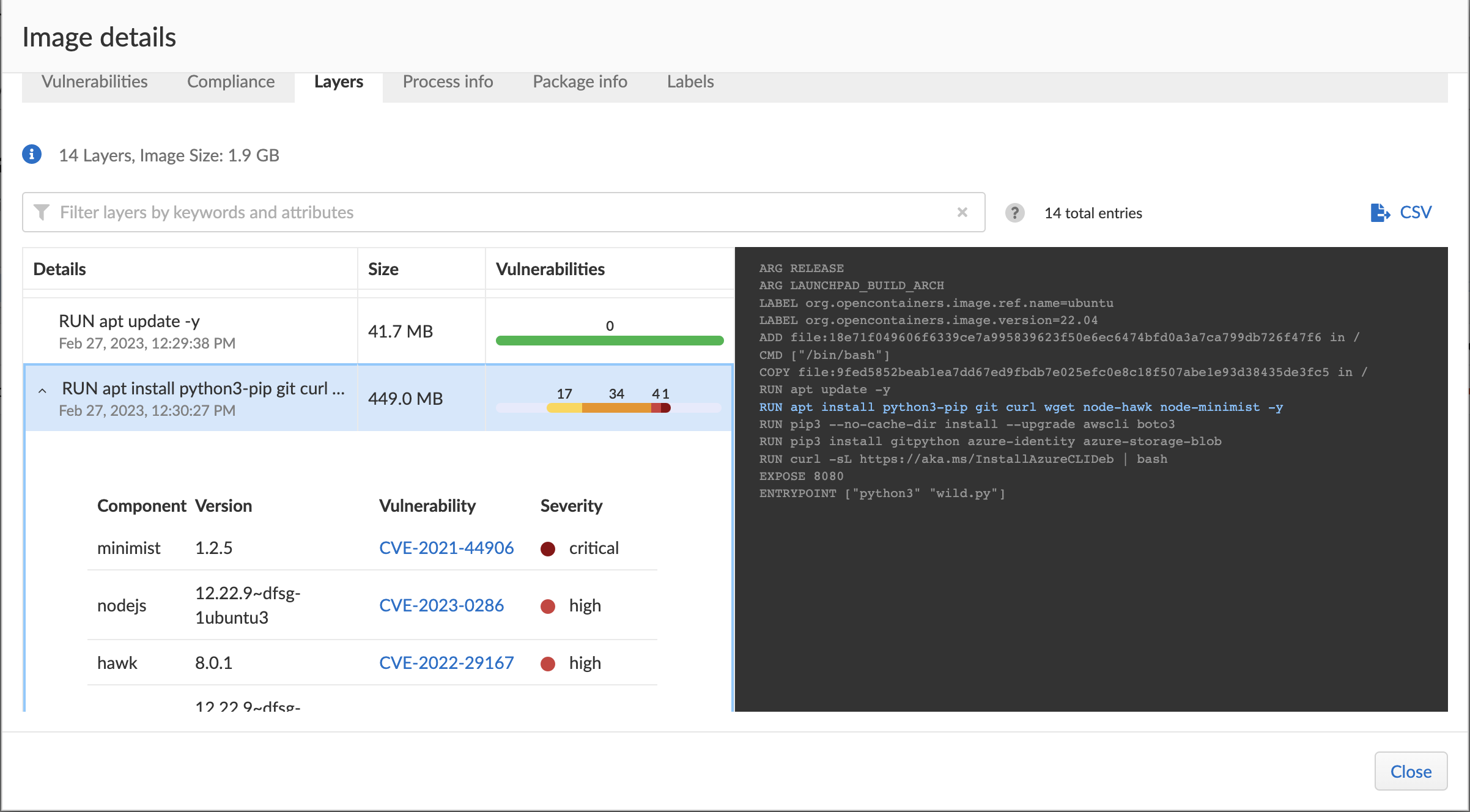
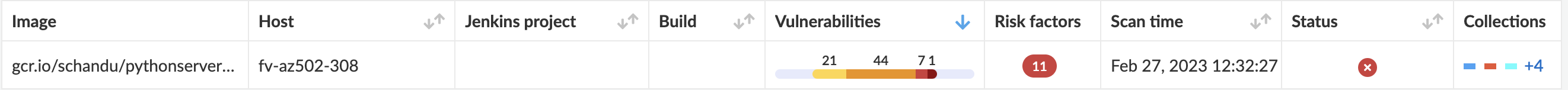
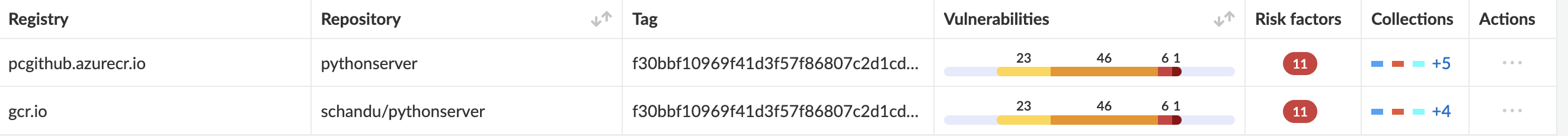
Image storage in registry (Persona: Secops/Security Team)
- Image scanning is important after image build and push to registry
- Vulnerabilites present in the image might be discovered after the image is built.
- The same applies to deployed images.

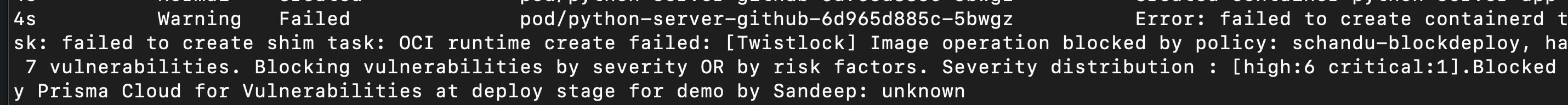
Deploy phase (Persona: Devops and Production Engineering)
- Devops team can see the vulnerable images not getting deployed.
- The reason of failure (policy) can be viewed in audit logs

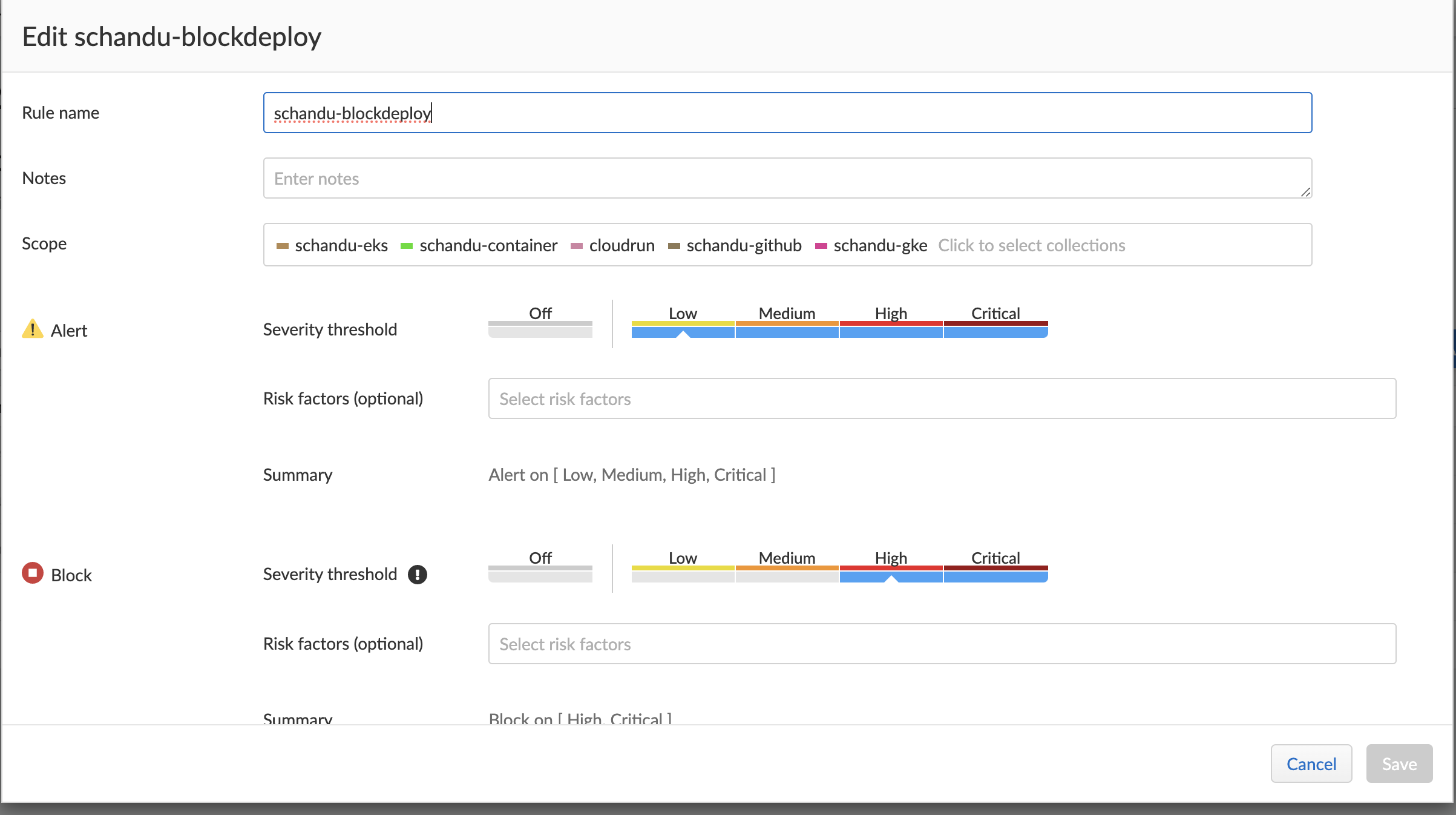
Deploy phase (Persona: Secops/Security Team)
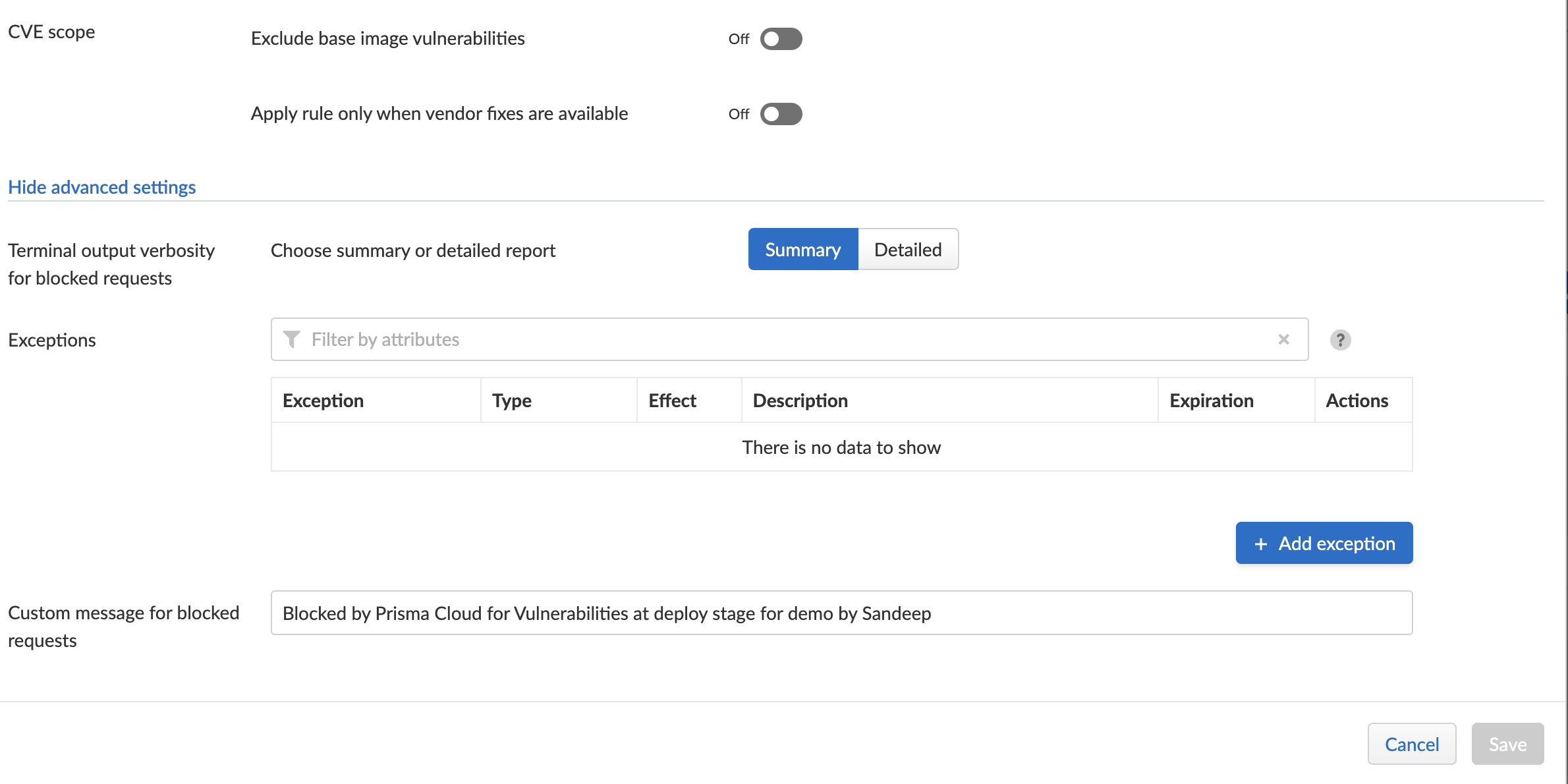
- Security team can set policies around deployment. Advanced features/exceptions can also be configured.
- A message can be set so deployment team can know the reason/next steps.
- Deployment failures are logged in PC Events tab.
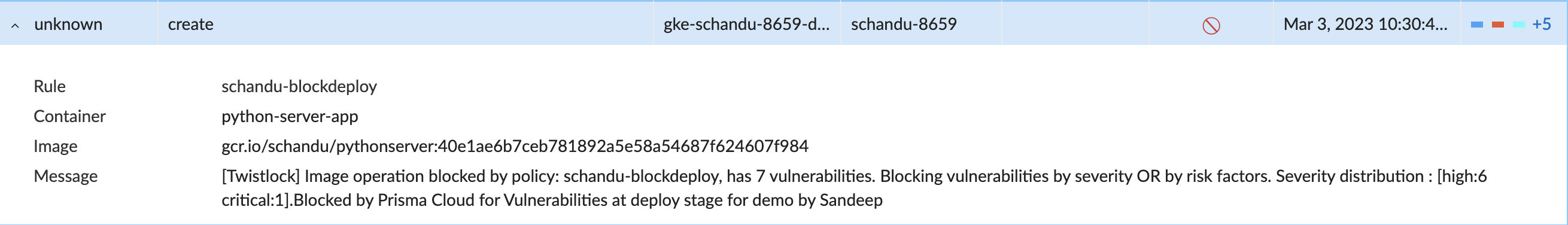
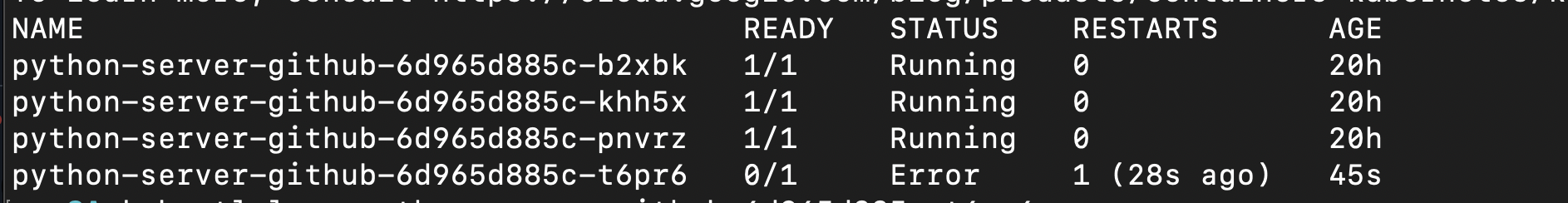
Notice that the message set in Prisma Cloud console is visible in k8s audit logs
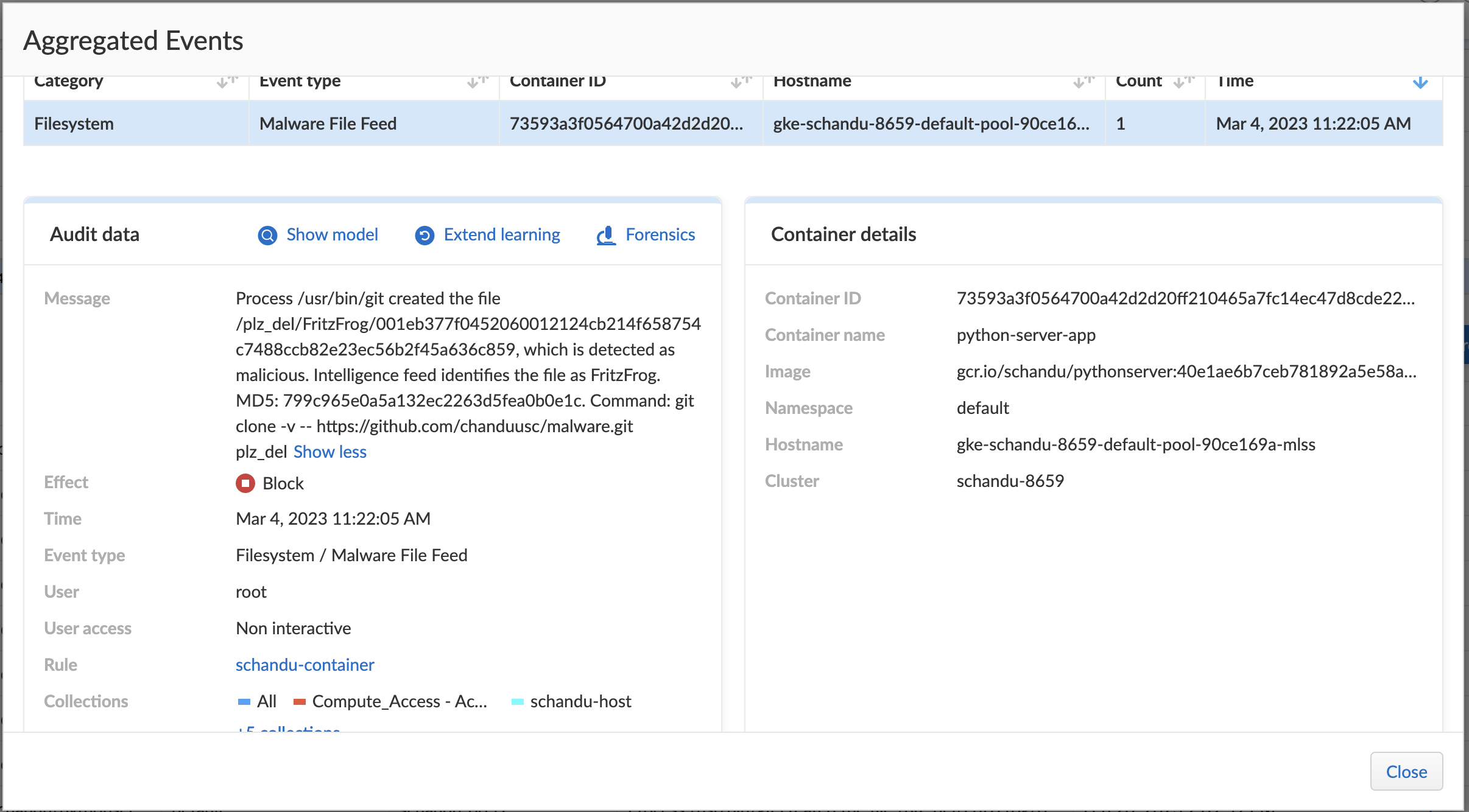
Runtime (Persona: Secops/Security team)
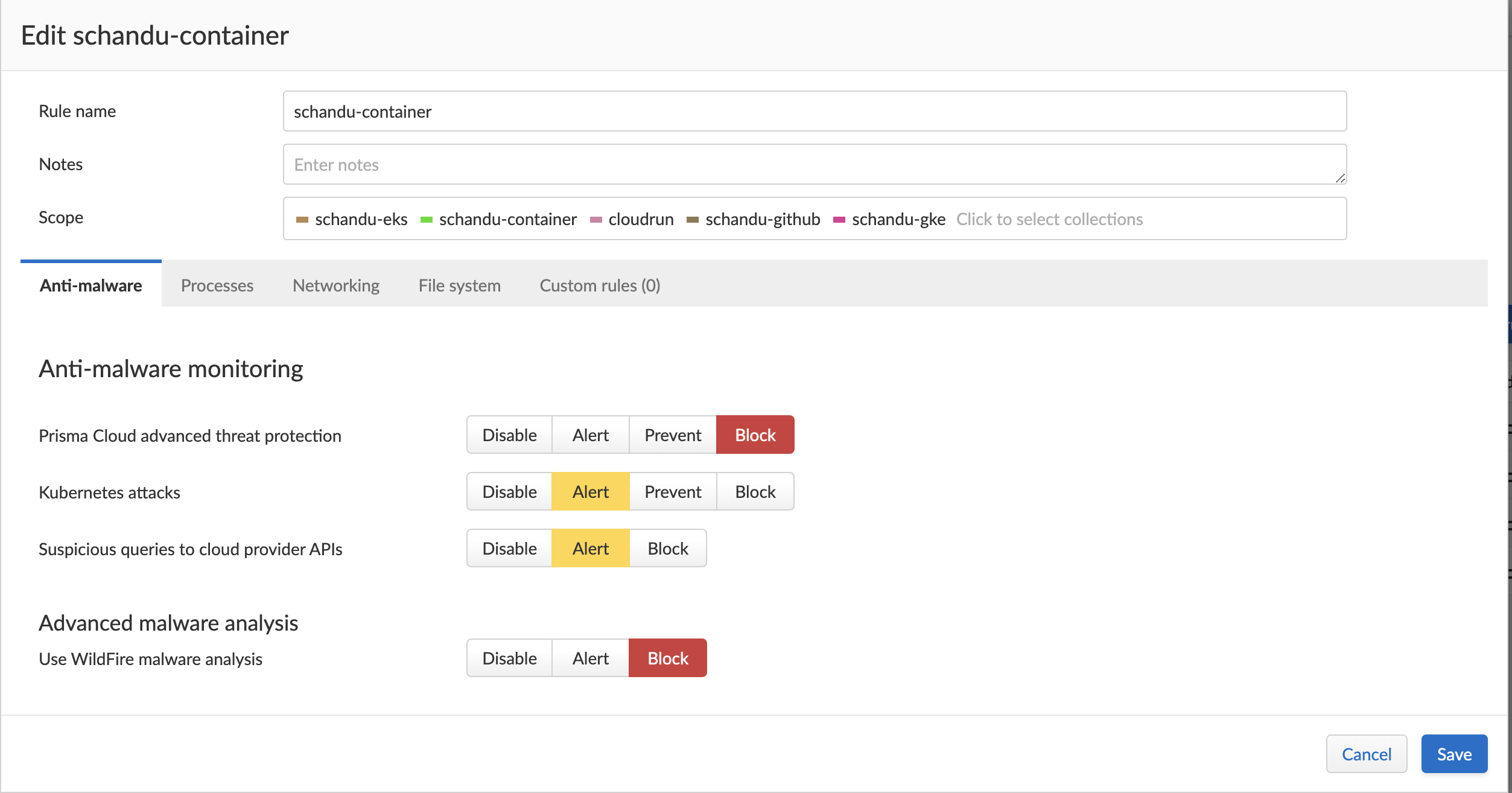
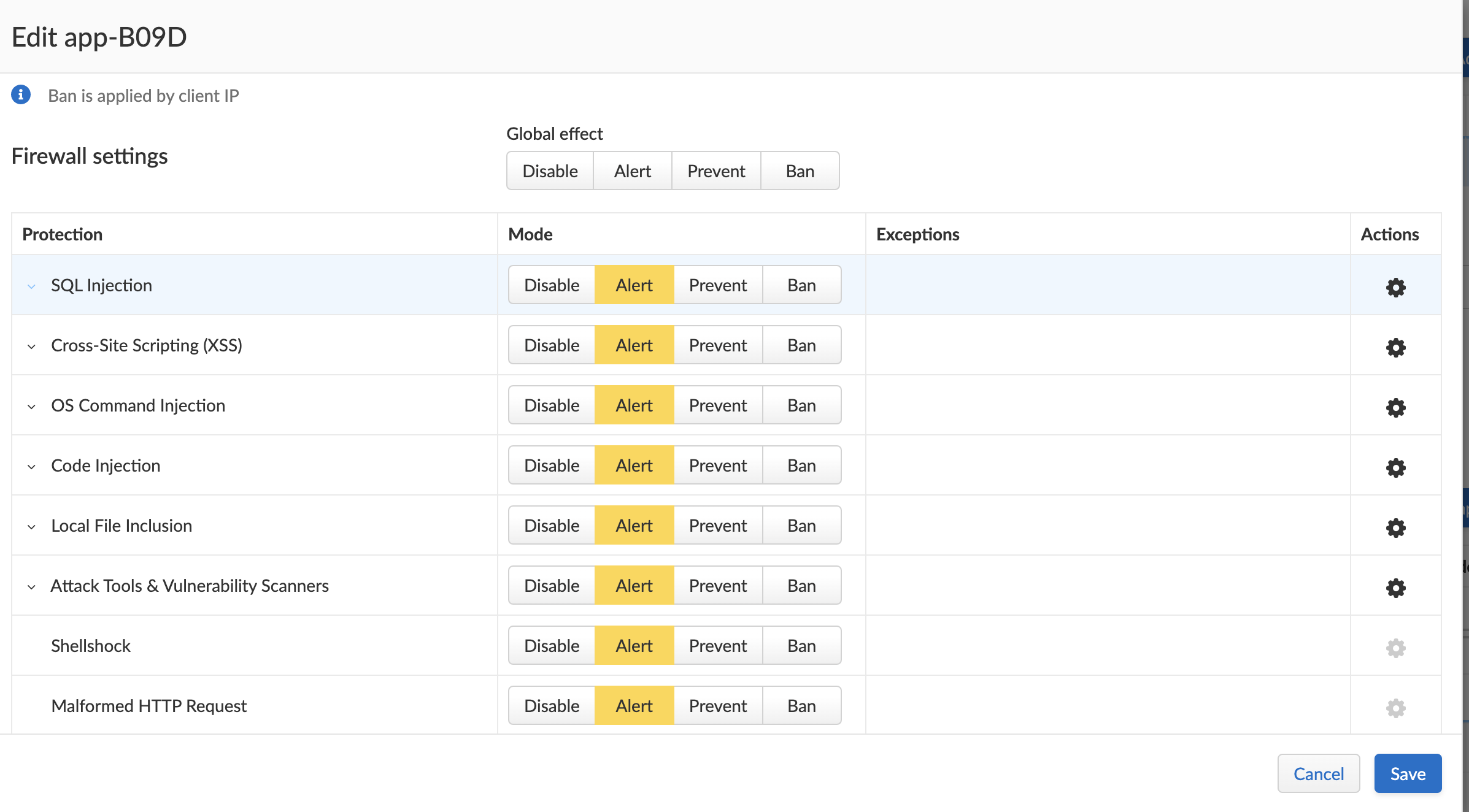
- Set runtime rules so that no malicious activities are happening during run time.
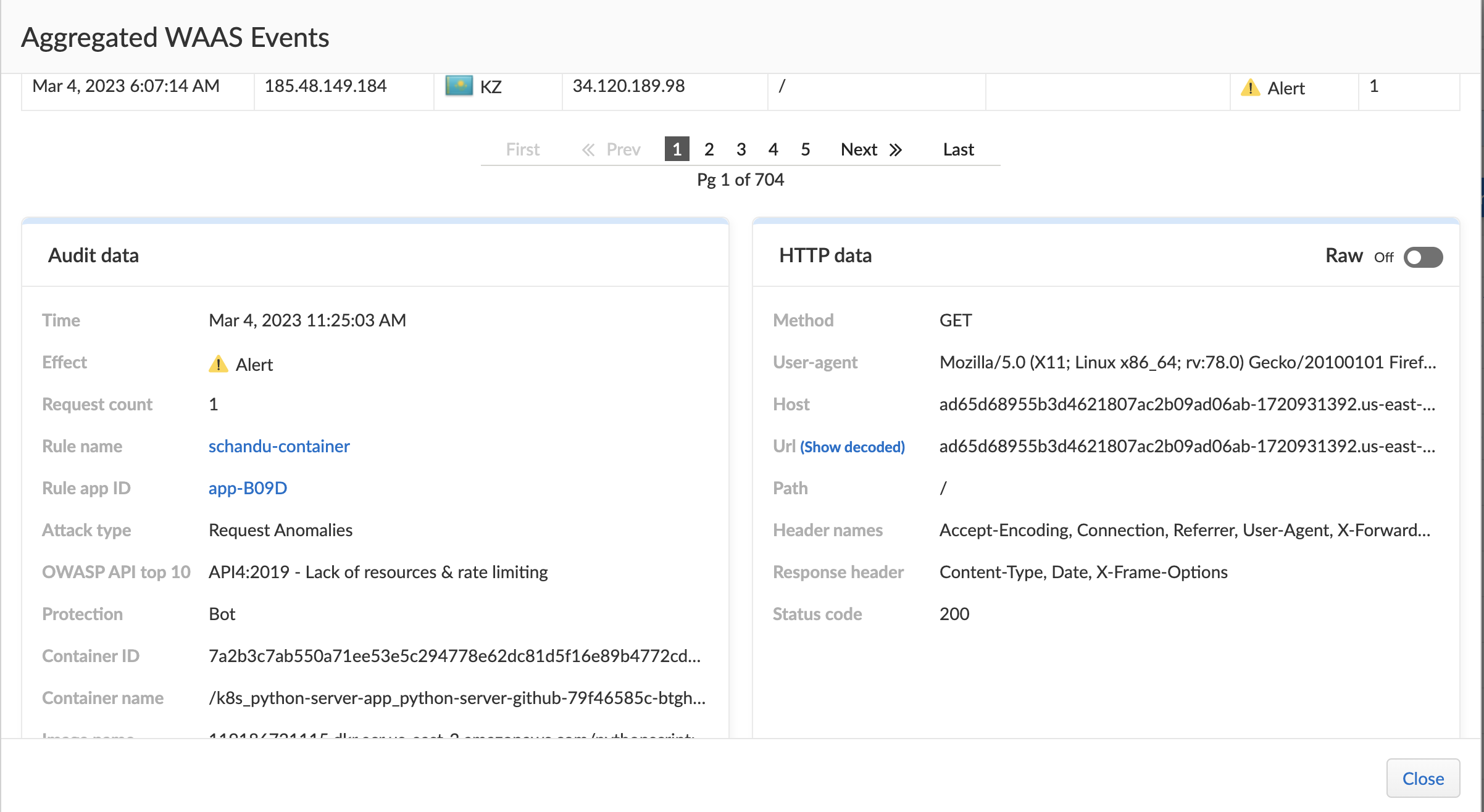
- Set WAAS rules to protect your applications from real time attacks.
We have unrealistic example in wild.py but any imported module can be the bad actor. Requirements.txt scan of code security should have caught it realistically.
- Observe the event and alerts to keep track on production application health.
Use tools like nuclei to simulate attacks --> nuclei -u http:/// -t nuclei-templates/f/ (more info : https://medium.com/@cyb_detective/using-nuclei-for-osint-5-minute-basic-guide-f8764424902b )
Runtime (Persona: Production Engineering)
- Work closely with dev and security teams based on the production runtime results.
- Provide continous feedback about app/api deployment pattern to security teams.
Cloud Infrastructure Entitlement Management:
Post Deployment (Production Engineering / Secops or Security team)
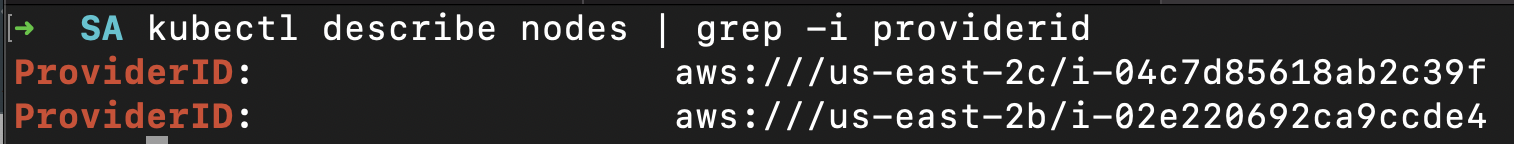
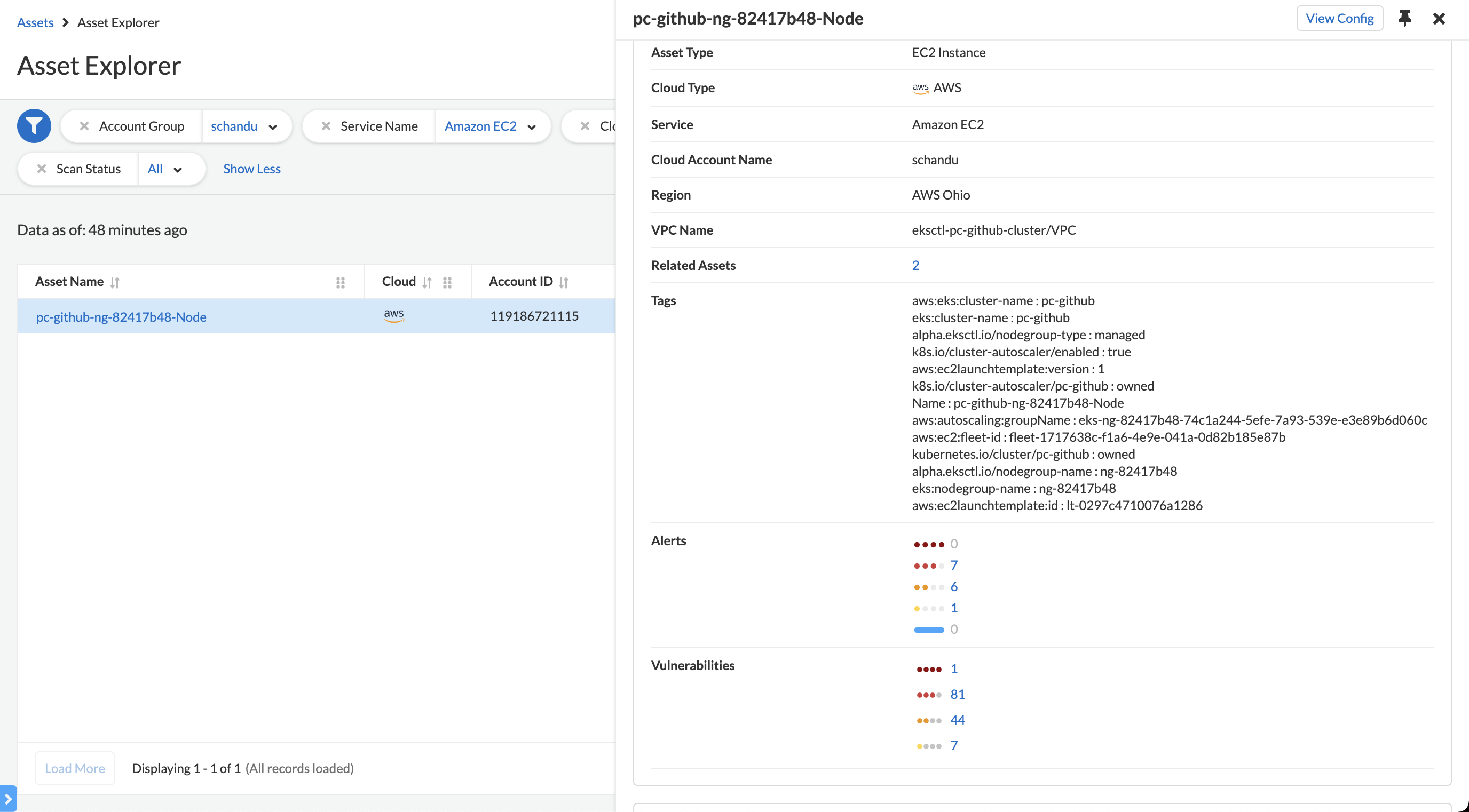
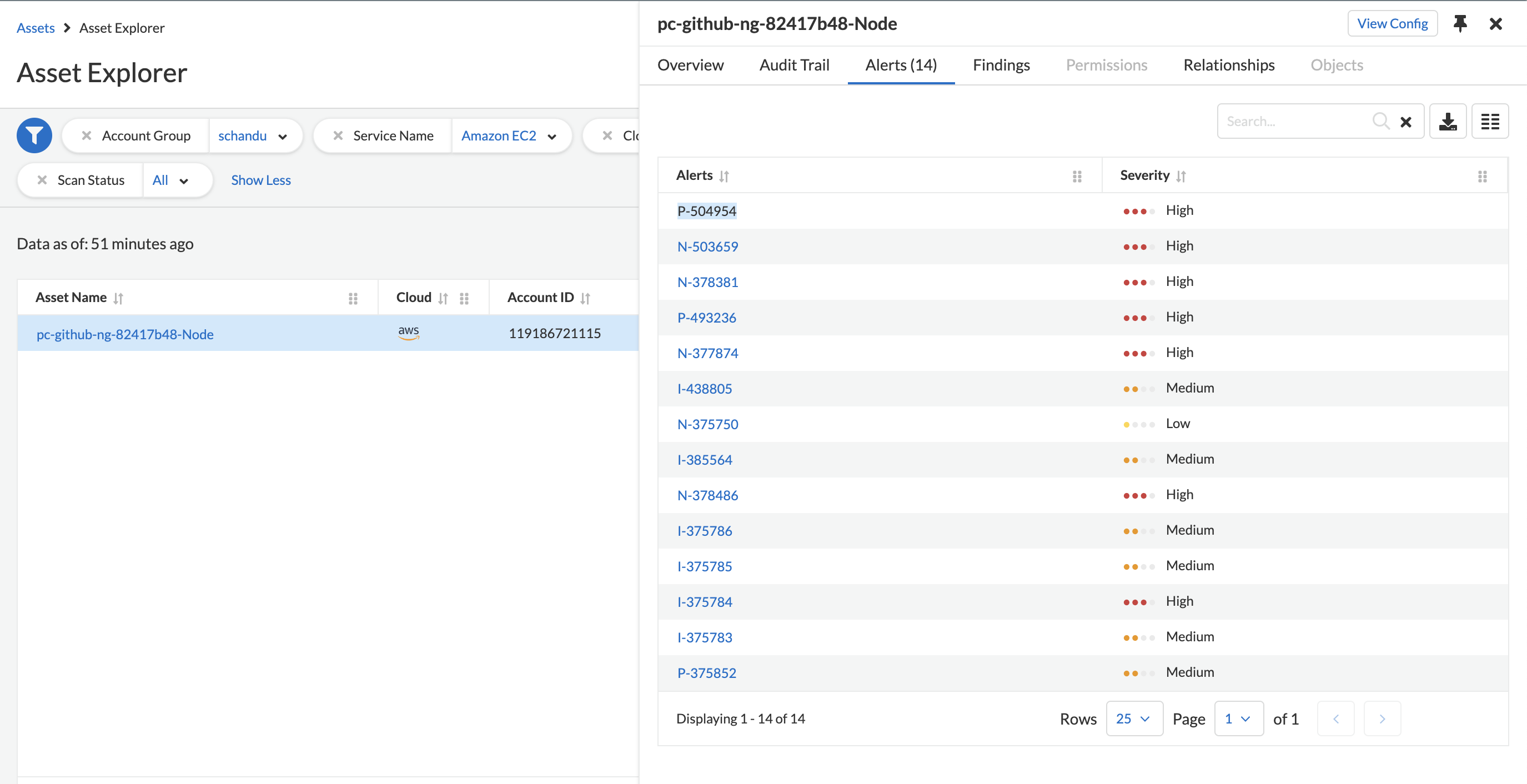
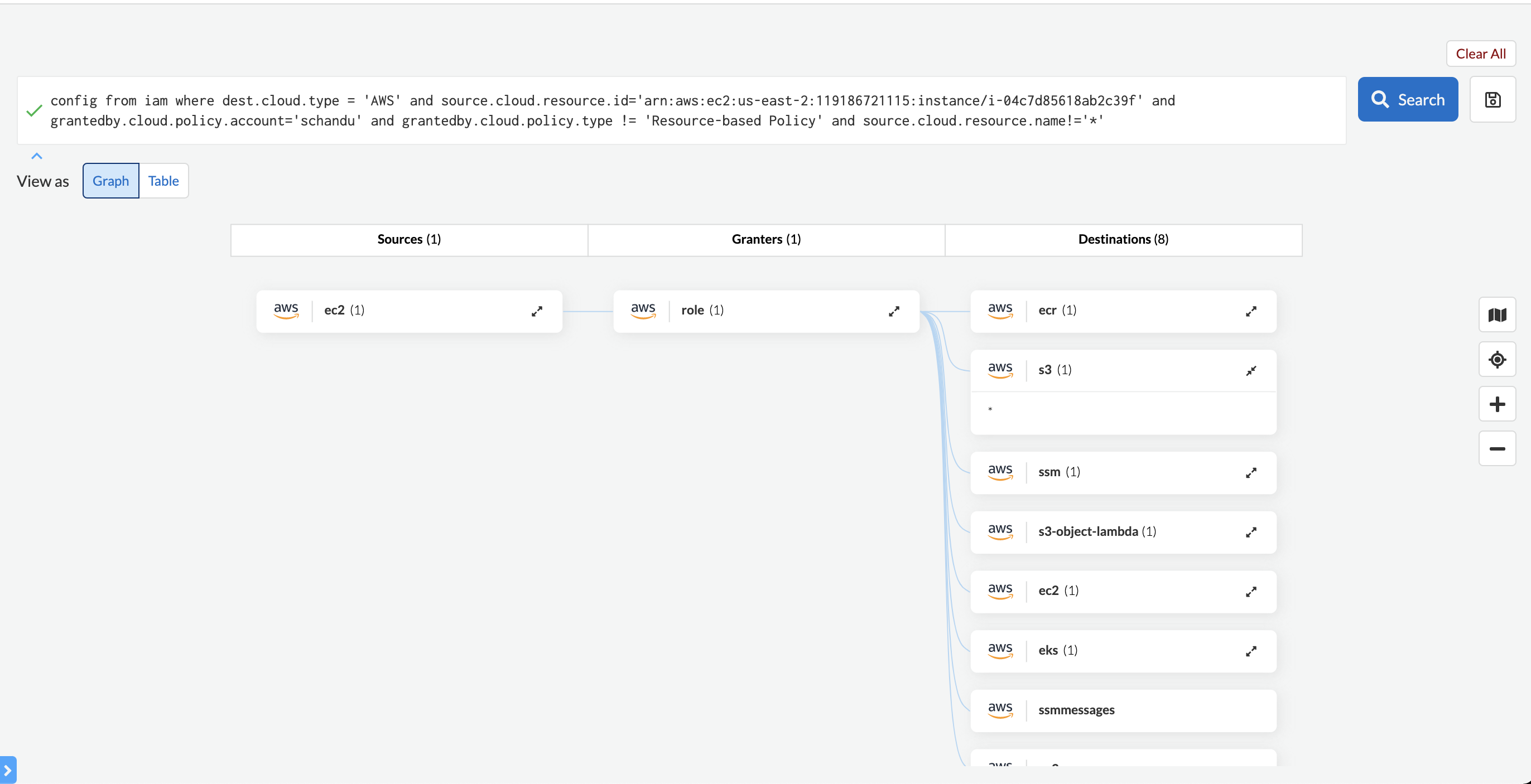
- CIEM module detects that one of the nodes have escalated permissions.
- The nodes has permission to perform any action(*) on s3 service. Hence those capabilities are inherited by pods.
Cloud Data Security:
Post Deployment (Production Engineering / Secops or Security team)
This is th only place where something is hardcoded in this entire project (Azure blobname and AWS s3 bucket needs to be changed)
- The script wild.py copies malware and sensitive files to S3 bucket (and azureblob) which are public.
- Again developers aren't educated about security and this is consequence of lack of security awareness.
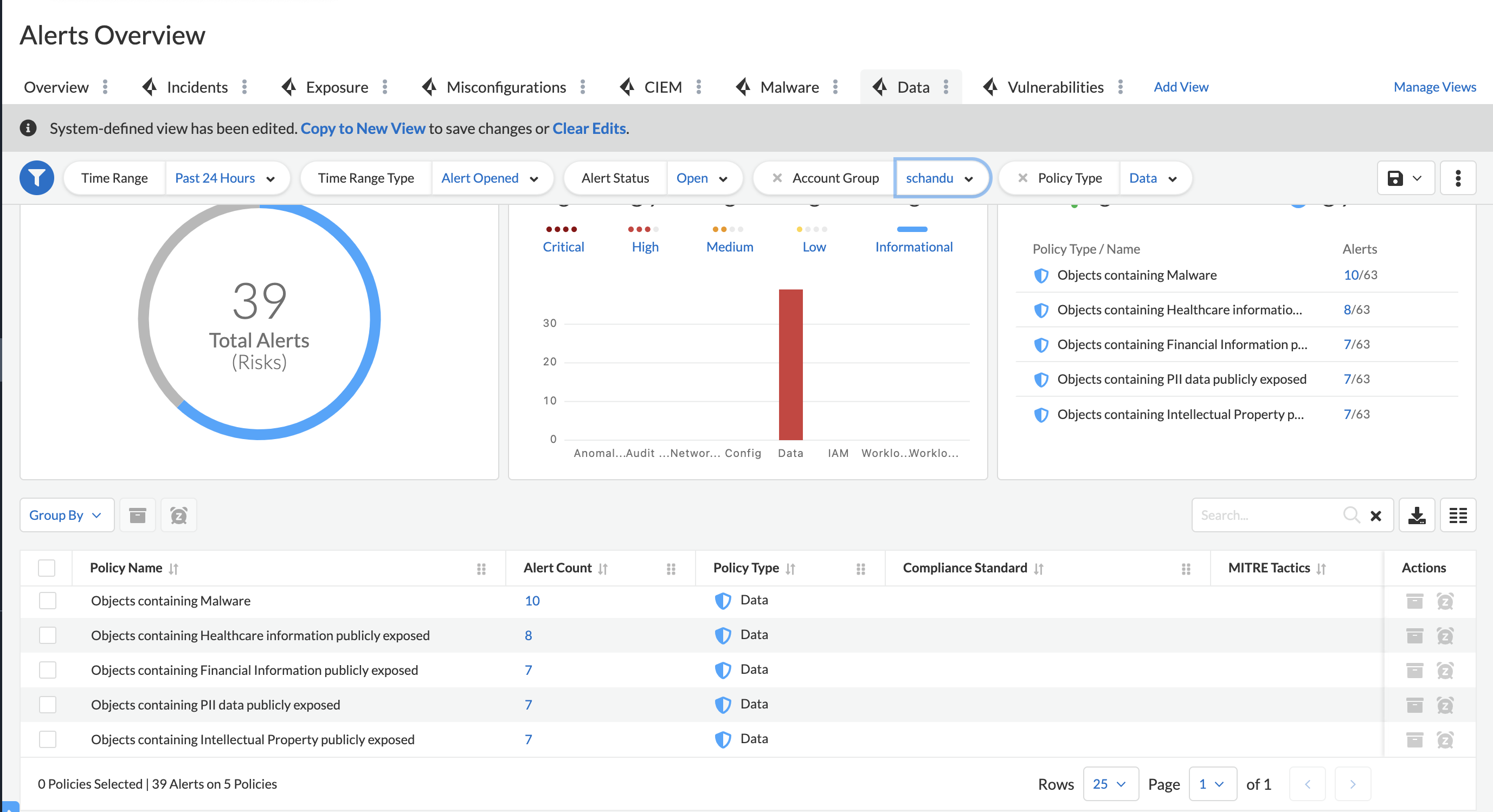
Cloud Security Posture Management:
Post Deployment (Production Engineering / Secops or Security team and compliance teams)
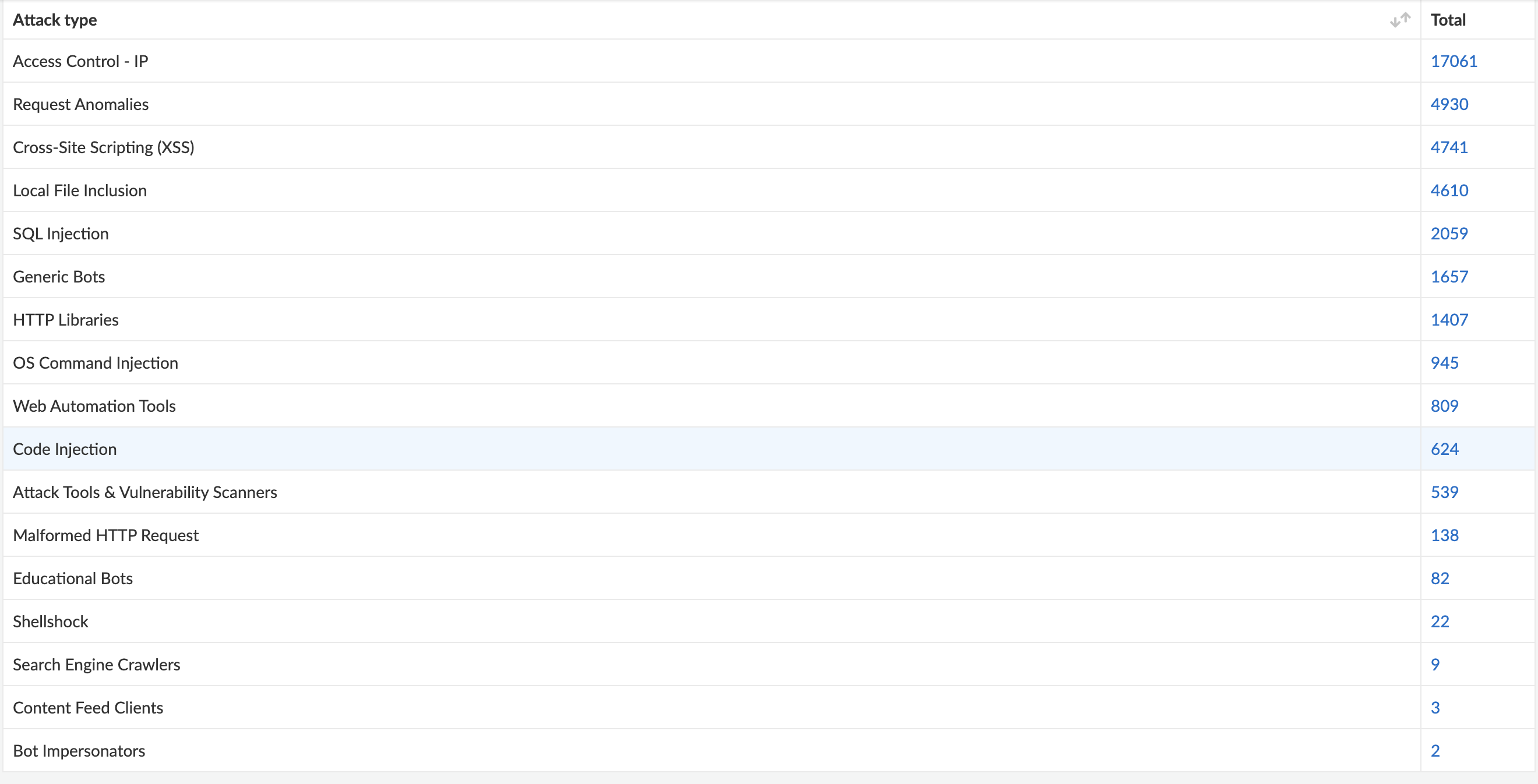
- Prisma Cloud ships with lot of out of box policies which provides visibility (or protection) across modules.
- Generate reports for compliance, business unit and cloud security assesment on regular basis.
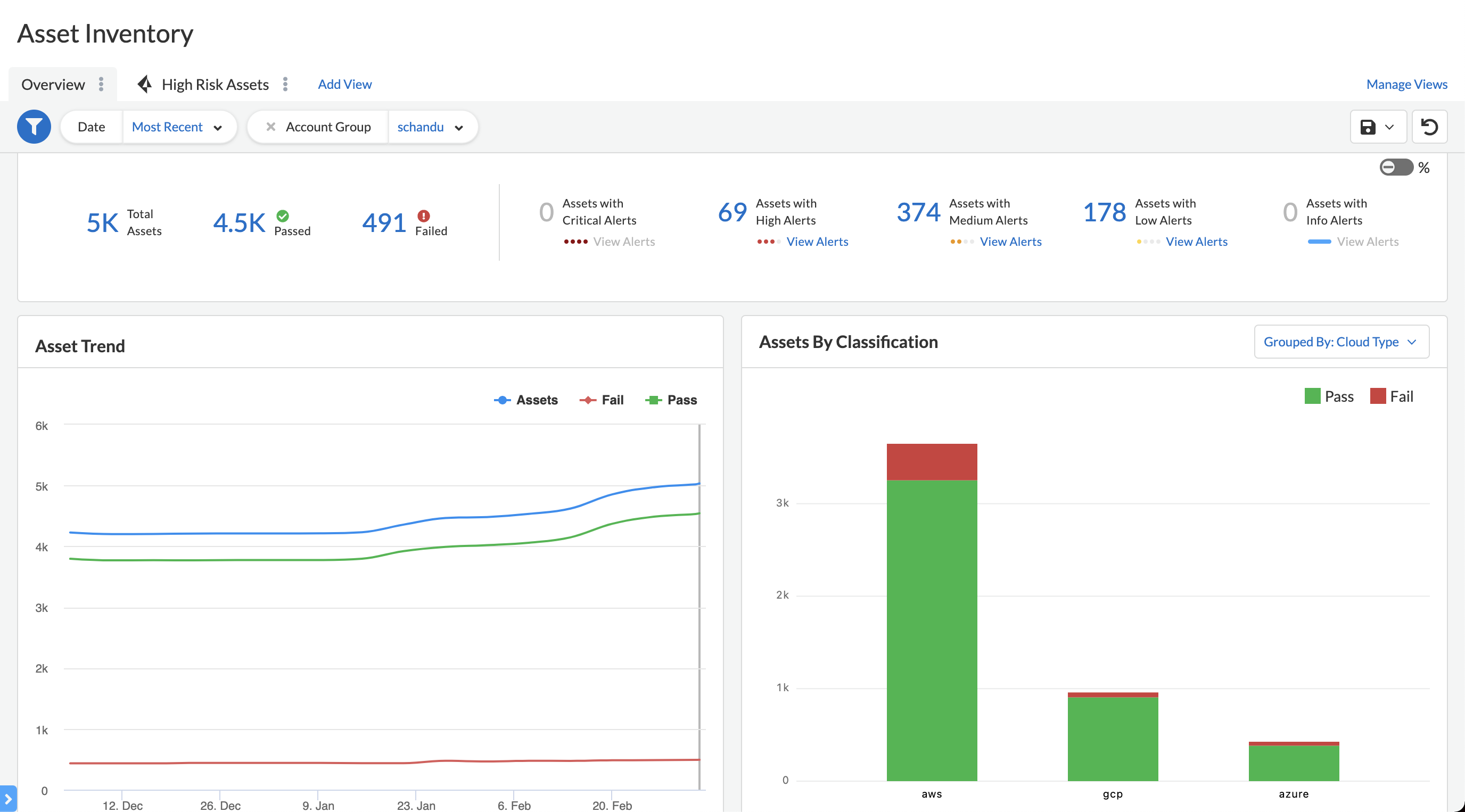
- Review your compliance and asset trend to check how your organization is doing against time.
- Setup alerts to be emailed to concerned people in your organization and audit them on regular basis.
- Make sure you integrate alerts with change management and/or incident reporting tools to track remidiation.Integrations link