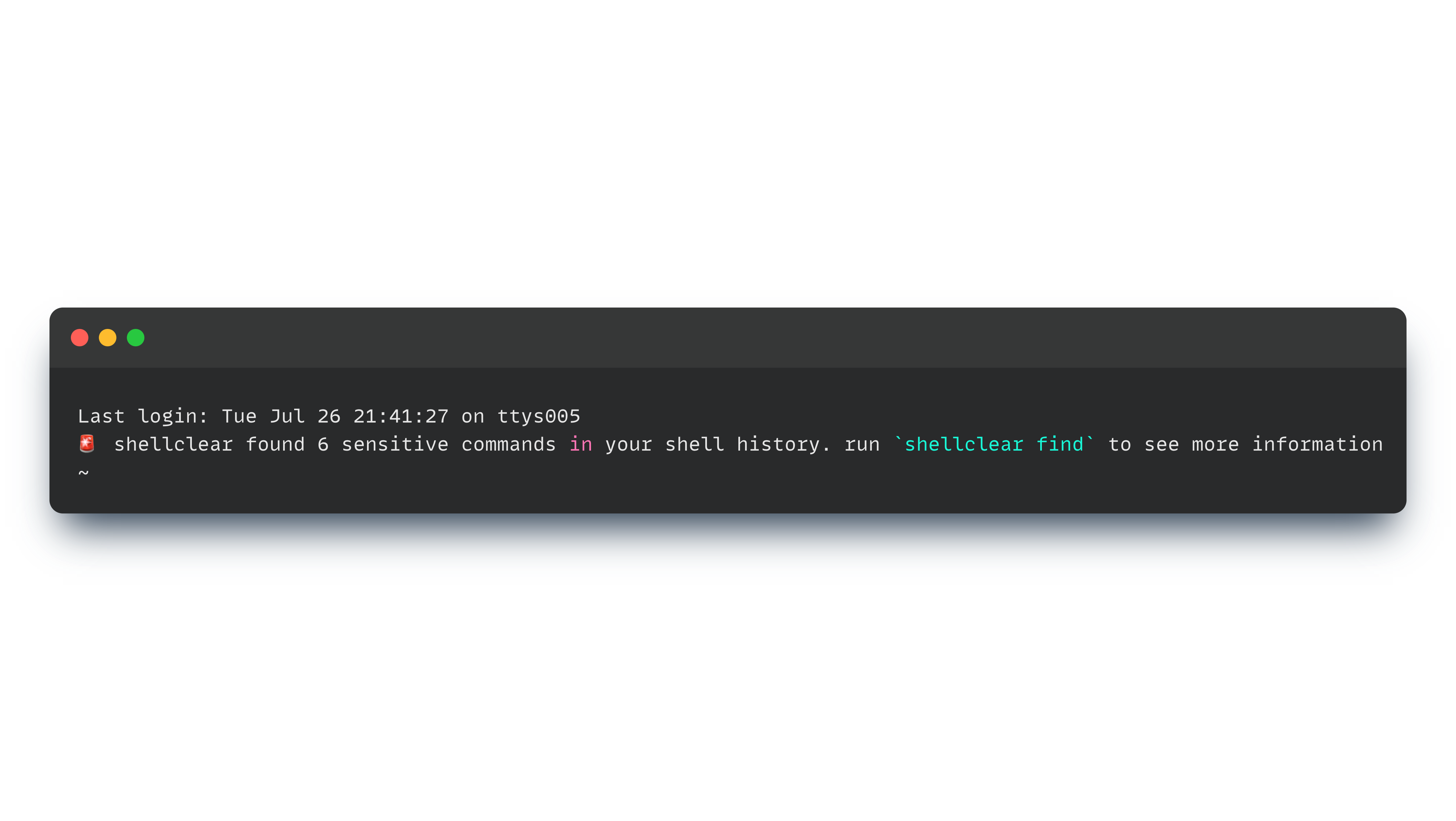
🚩 Show sensitive command summary when open a new terminal
👀 Clear sensitive commands from shell history
🙈 Stash your history command before presentations OR screen sharing
The idea behind shellclear is to provide a simple and fast way to secure you shell commands history
macOS
curl -sS https://raw.githubusercontent.com/rusty-ferris-club/shellclear/main/install/install.sh | shOr via brew
brew tap rusty-ferris-club/tap && brew install shellclearLinux
You need to make sure that apt install xz-utils is install. There is an open issue #52 to remove this dependencies.
curl -sS https://raw.githubusercontent.com/rusty-ferris-club/shellclear/main/install/install.sh | shWindows
iwr https://raw.githubusercontent.com/rusty-ferris-club/shellclear/main/install/install.ps1 -useb | iexOr download the binary file from releases page.
Bash
Add the following to the end of ~/.bashrc:eval $(shellclear --init-shell)Zsh
Add the following to the end of ~/.zshrc:eval $(shellclear --init-shell)PowerShell
Add the following to the end of your PowerShell configuration (find it by running $PROFILE):Invoke-Expression (&shellclear --init-shell)Fish
Add the following to the end of ~/.config/fish/config.fish:shellclear --init-shell | source$ shellclear --help
Secure shell commands
USAGE:
shellclear [OPTIONS] [SUBCOMMAND]
OPTIONS:
--config-dir <CFG_DIR_PATH> Set configuration directory path
-h, --help Print help information
--init-shell Show sensitive findings summary for MOTD
--log <LEVEL> Set logging level [default: INFO] [possible values: OFF,
TRACE, DEBUG, INFO, WARN, ERROR]
--no-banner Don't show the banner
-V, --version Print version information
SUBCOMMANDS:
config Create custom configuration
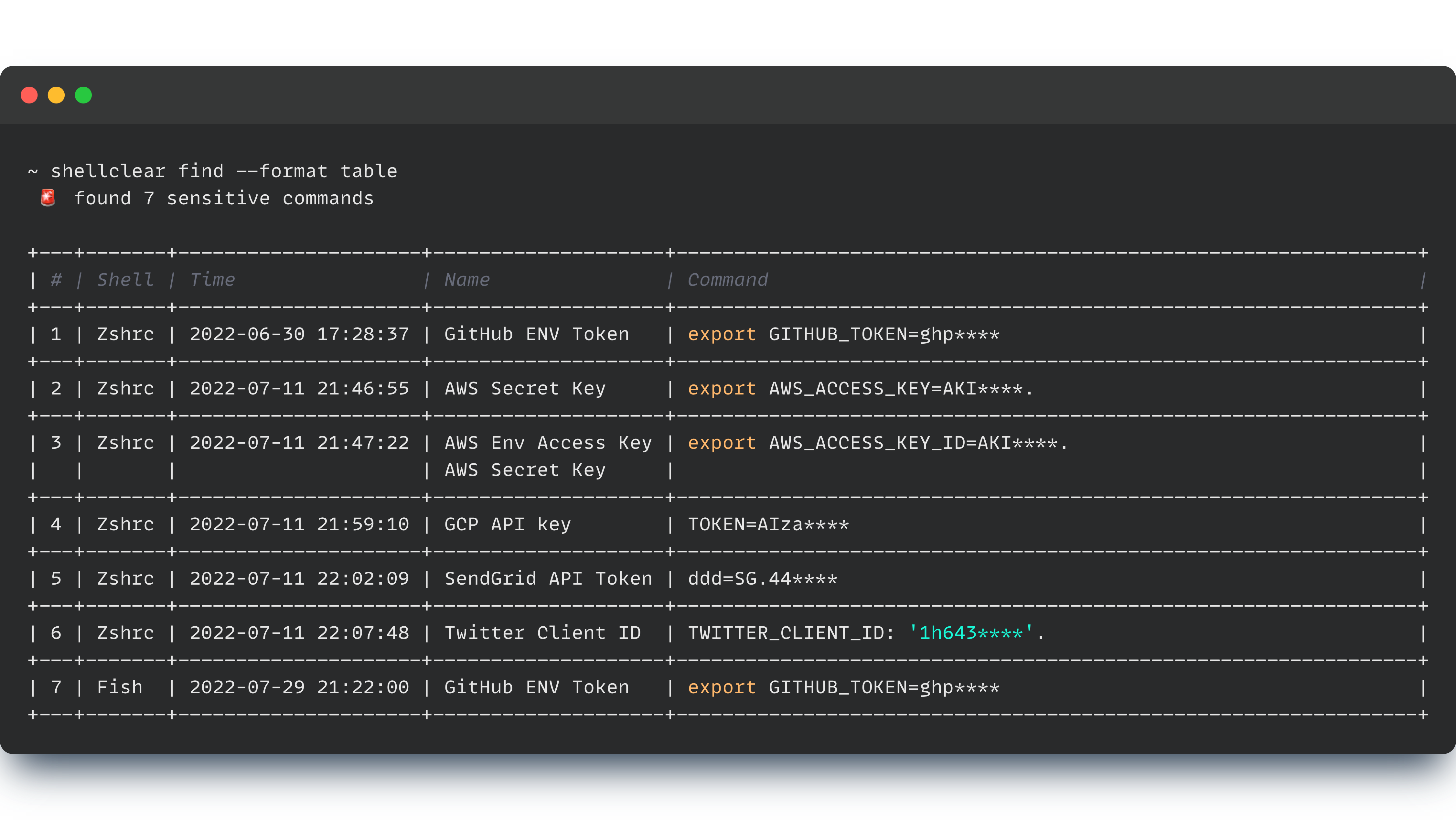
find Find sensitive commands
help Print this message or the help of the given subcommand(s)
restore Restore backup history file
stash Stash history fileSensitive data can be stored in your history file when export a token of something or running a script with token.
shellclear find --format tableshellclear clearshellclear clear --backupYou can stash your history shell by running the command:
shellclear stashNow your history shell is clear, to bring back your history run the command:
shellclear stash popYou can also restore your history backup file by running the command:
shellclear stash restoreCreate custom configuration by running the command
shellclear configConfig command will create:
- Custom pattern template for adding a custom risky patterns
- Ignore file to allows you ignore specific pattern
Validate syntax file
shellclear config validateValidate syntax file
shellclear config deleteManage pattern ignores
shellclear config ignoresAll the examples here - you make this happen, thanks!
To all Contributors - you make this happen, thanks!
Copyright (c) 2022 @kaplanelad. See LICENSE for further details.