Intune doesn't support installing .pkg files directly - instead requiring wrapping them using custom scripts.
It's much easier and more reliable to use a shell script to deploy Crowdstrike Falcon Protect to end-users.
Here's the steps I went through to get it working.
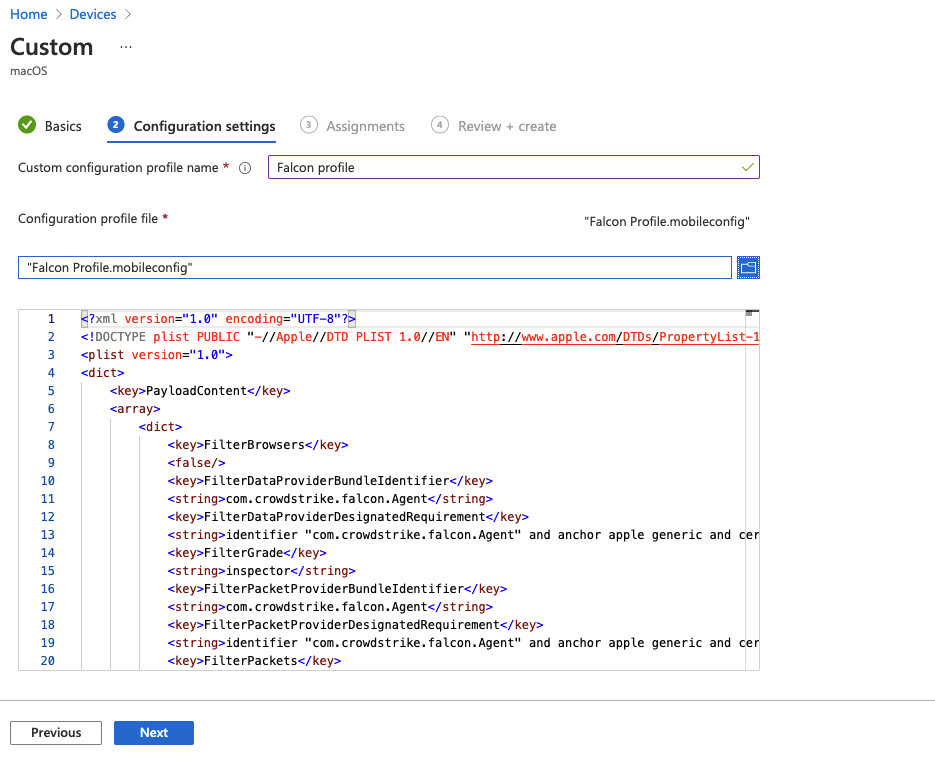
Crowdstrike provides a Configuration profile to enable KExts, System Extensions, Full Disk Access and Web Content Filtering that can be deployed by Intune. Unfortunately this profile does not work on Apple Silicon (M1) devices due to lack of support for KExts.
This would be an easy fix if there was a way to identify arm64 devices in intune for use in Dynamic Groups or the new Filters feature - but so far I haven't figured out a decent way to do this (If you find something, please submit an issue or PR on this repo!).
The closest thing to do to get this to work is to deploy two .mobileconfigs - one with the standalone kexts and one with the rest of the permissions - the kexts will still fail on Apple Silicon, but it doesn't cause any issues with the installation, since Crowdstrike doesn't try to use them on M1.
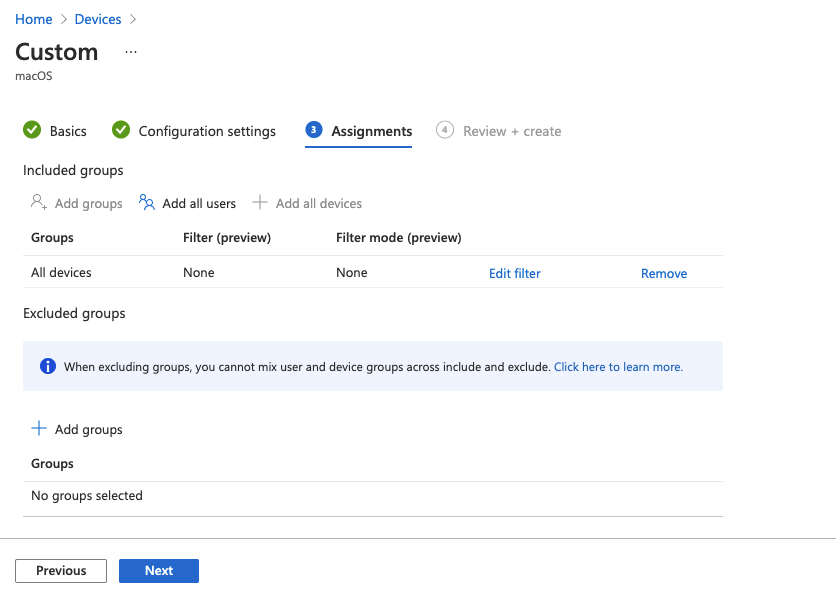
Deploy the .mobileconfig files in /MobileConfigs by doing the following:
-
Open open the Microsoft Endpoint Manager admin center
-
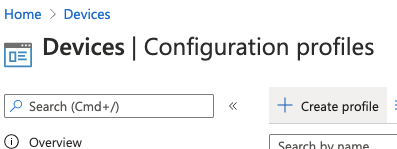
Select
Devices->Configuration Profiles -
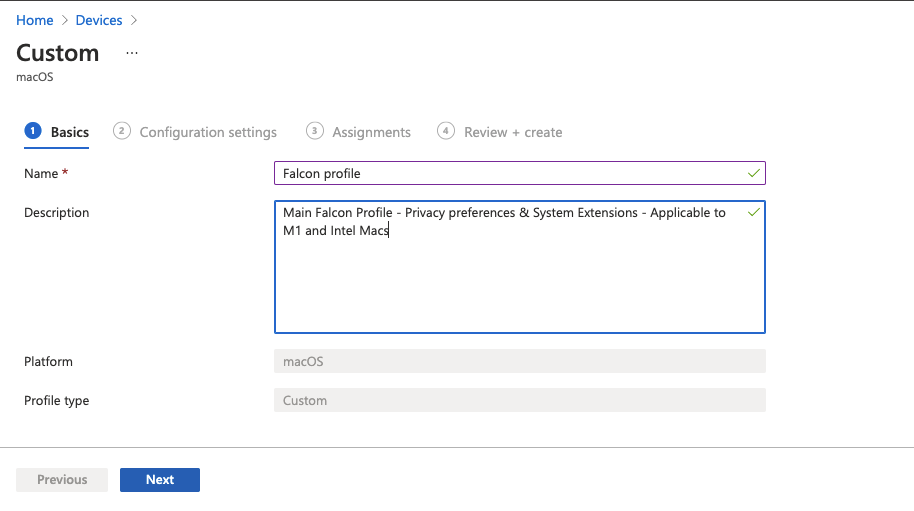
In the blade that opens on the right, select
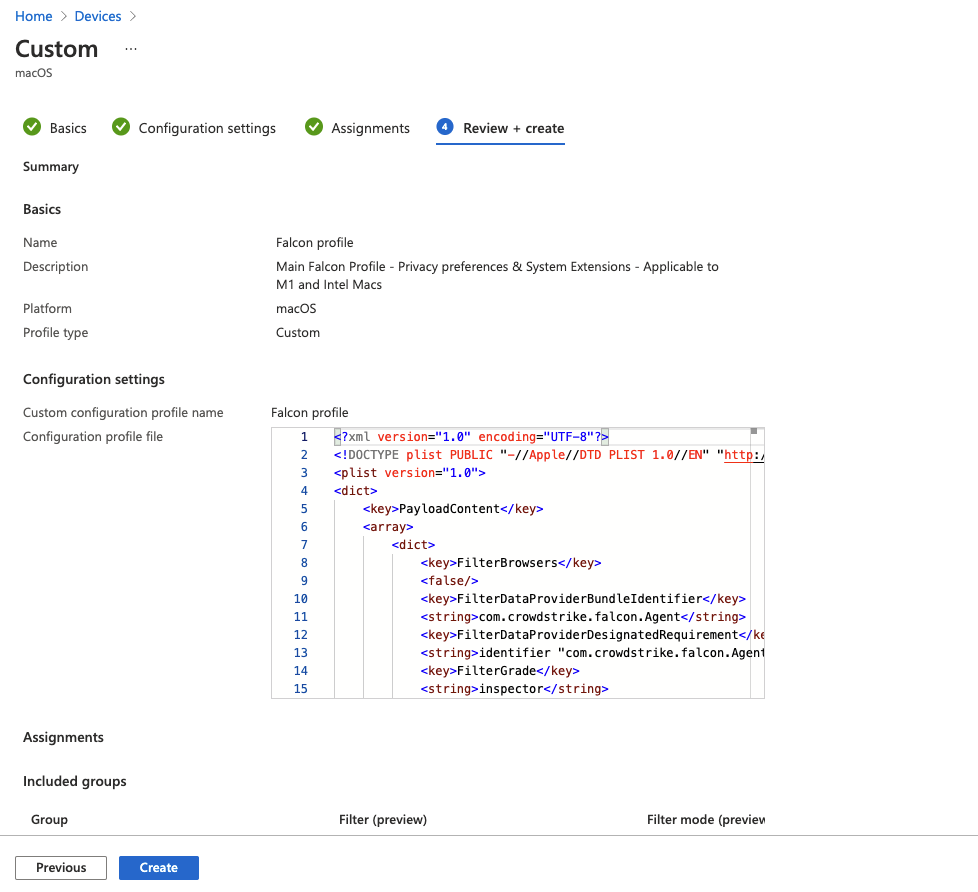
macOSfor platform,Templatesfor Profile type, andCustomfor template name. ClickCreate
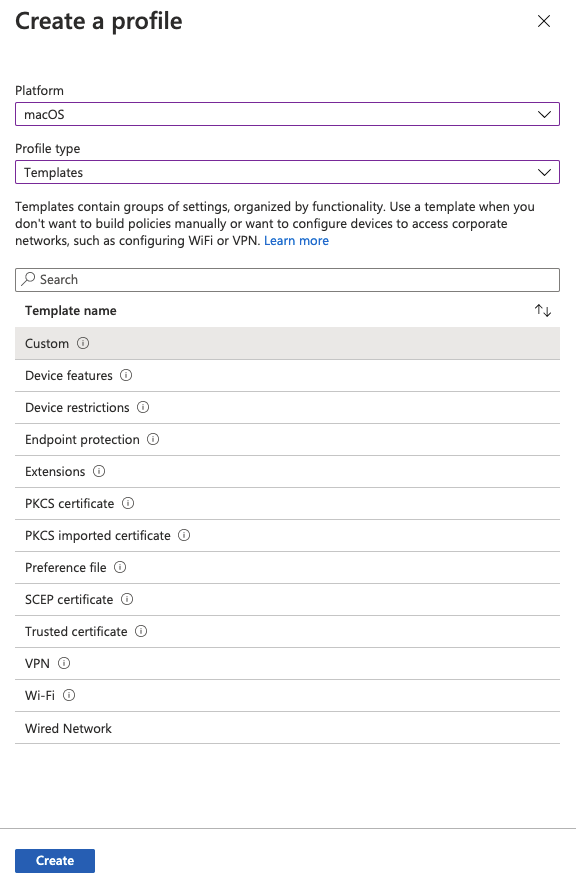
-
Repeat steps 3-8 for MobileConfigs/Falcon Profile - kexts.mobileconfig
Now the actual deployment of Crowdstrike - This should work on M1 and Intel with no additional dependencies.
This script uses JXA & Open Scripting Architecture to parse JSON (We used to use Python, but runtimes are being deprecated in MacOS). (Thanks to both https://www.macblog.org/posts/how-to-parse-json-macos-command-line/ and RhubarbBread on the MacAdmins slack for guidance on this)
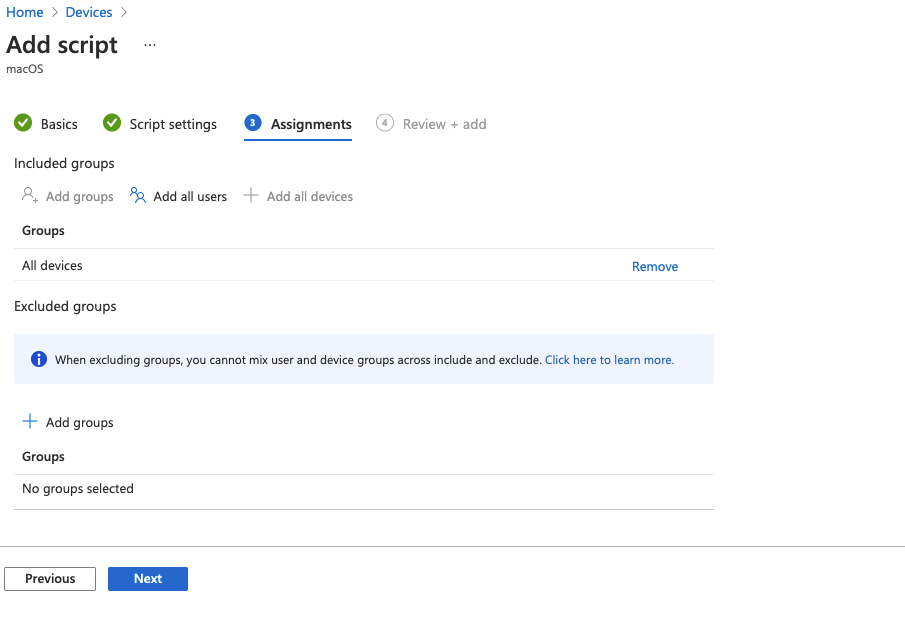
How to push the script via Intune:
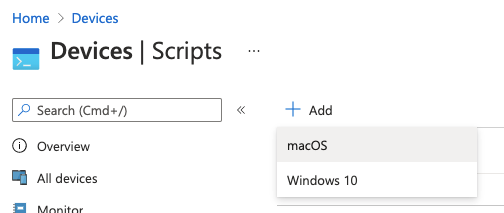
- Open open the Microsoft Endpoint Manager admin center
- Select
Devices->Scripts - Click
+ Add
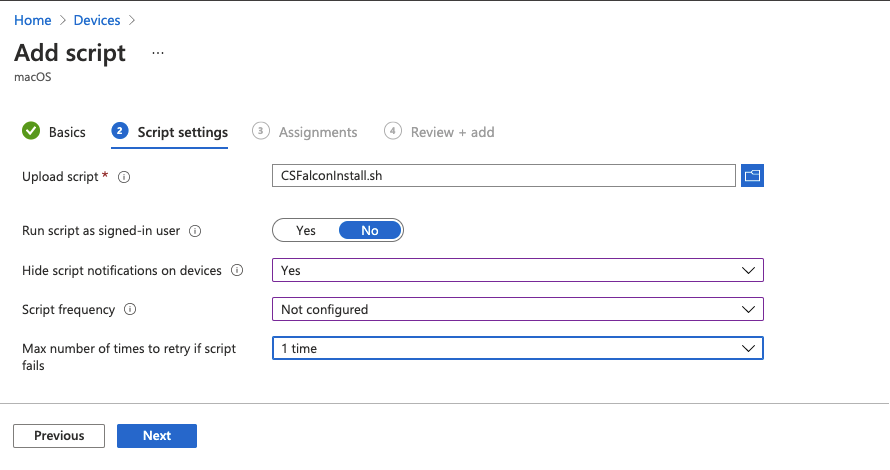
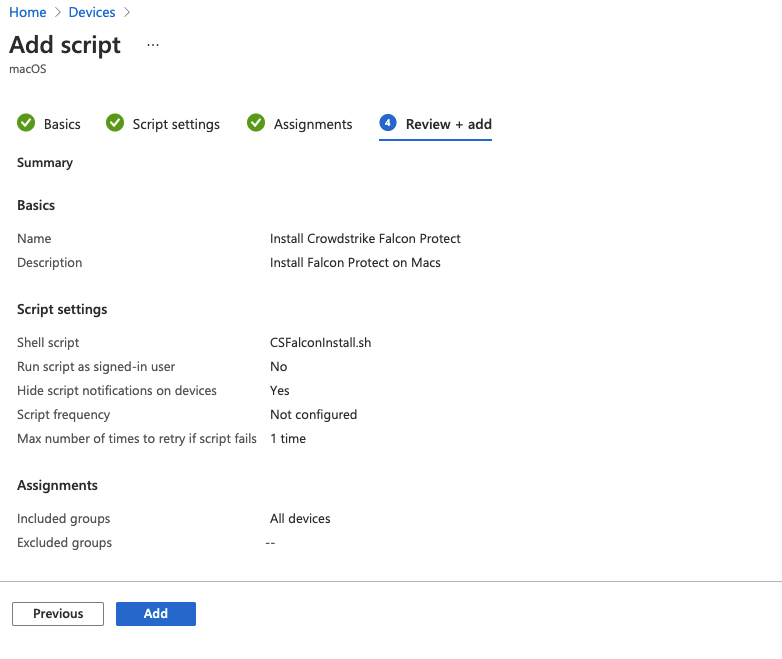
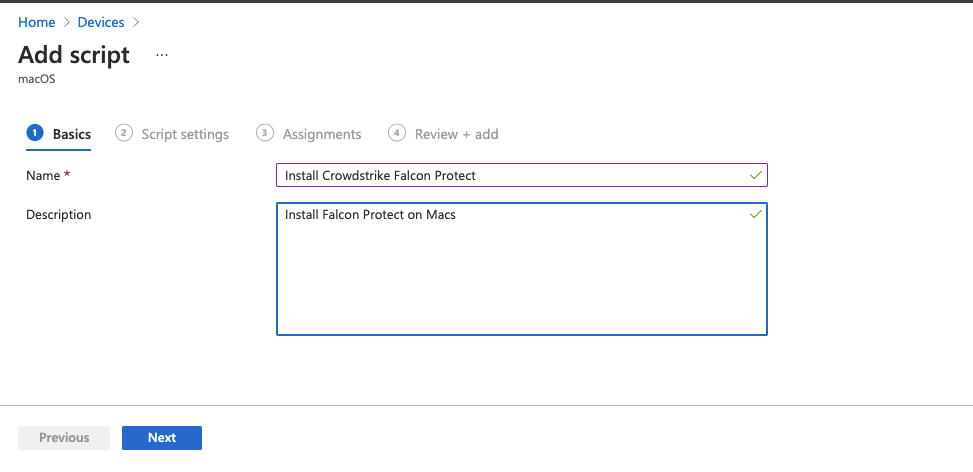
- Enter the basic details for the script
- Upload CSFalconInstall.sh
- Select "No" For
Run script as signed-in userso it runs as the superuser instead of the local user - Choose your preference for
Hide script notifications on devices - Setting
Not Configuredfor the Script Frequency will ensure it runs only once (Unless the script is updated or the user's cache is deleted) 1 timefor script retries should be plenty, but this setting is at your discretion.