Centralize and share all my custom scripts to be used with the PIPER Burp extension.
Documentation of the extension.
ℹ️ No external dependencies needed.
Python >= 3.7 needed and in PATH.
PS> python --version
Python 3.7.4This GitHub action workfow validate that all scripts are compatible with Python 3.7, 3.8, 3.9 on Windows, Mac and Linux OS.
This topic is pending on the PIPER's author side. Once ready, this repository will be merged.
Visual Studio Code with Python extension provided by Microsoft is used to develop the scripts.
Project workspace file has been configured to trigger the installation of required code analysis modules and analysis profile is defined in the workspace settings area.
Each script describes its goal in its header, for which PIPER tools is targeted to be used and instruction regarding if HTTP headers must be passed as well as filter to define:
"""
PIPER script to ...
Target tool: [PIPER_TOOL]
[INSTRUCTION_IF_HTTP_HEADERS_MUST_BE_PASSED]
[FILTER_NEEDED_TO_BE_DEFINED]
"""
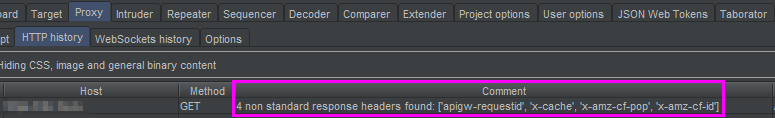
Add a comment to the matching line in the proxy tab for every response containing non-standart HTTP headers.
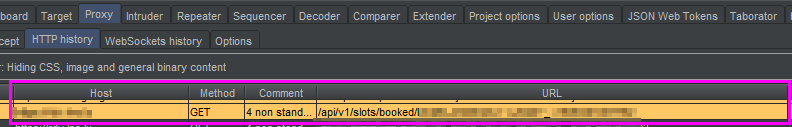
Highlight the matching line in the proxy tab for every request that is made to a web api.
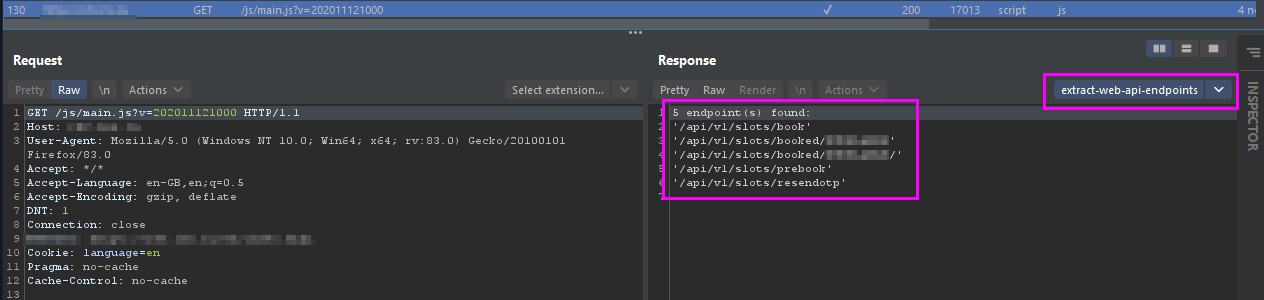
Extract all API endpoints (and URL like because it is hard to really identify if a URL is an API endpoint or not from a static point view) from a JS script content obtained from a HTTP response.
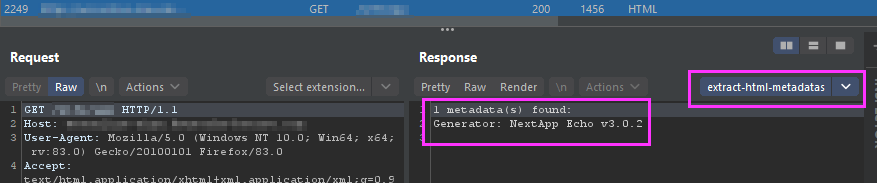
Extract interesting information from HTML META tags from a HTTP response. Mainly used to quickly identify which products/tools was used to build the site/application.
Detect HTTP responses containing a strack trace. Mainly used to quickly identify pages disclosing technical information via stack traces.
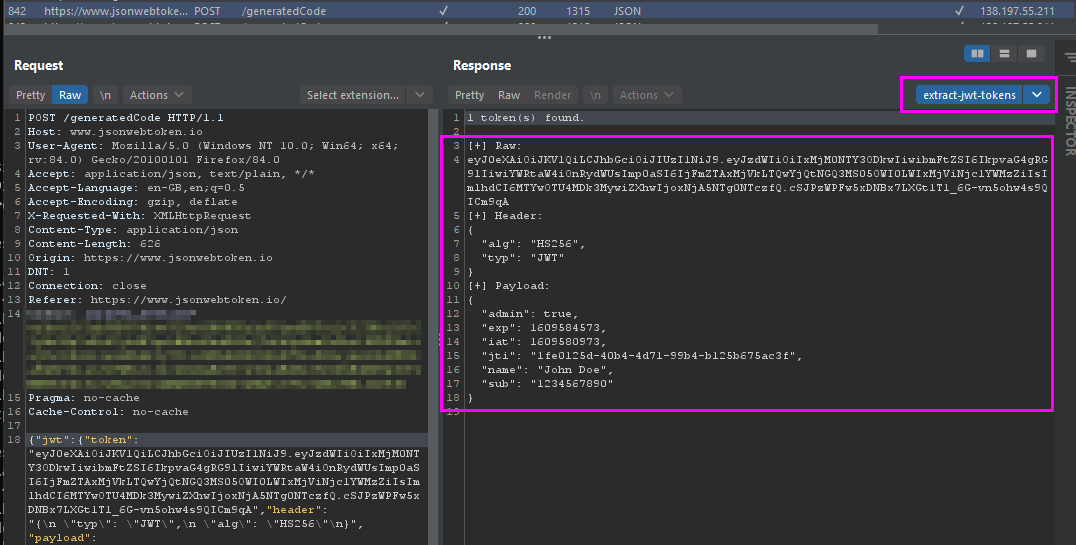
🎯 This script was created in order to avoid the need to use another extensions or the decoder to just see the content of the token.
Extract and pretty-display all JWT tokens present in an HTTP response.
⚠️ Change the script location path defined in prefix field for all custom scripts before to import the configuration.
After the import, do not forget to enable the scripts because they are all disabled by default by the import command.
For Highlighters, the color can be changed before the import by changing the color field to one constants supported by PIPER/BURP.
The file piper-config.yaml contains the complete configuration that I use for all my custom scripts.