Reflected Cross Site Scripting (XSS) in Intermesh BV Group-Office version 6.6.145, allows attackers to gain escalated privileges and gain sensitive information via the GO_LANGUAGE cookie
- Product: Group Office Application
- Version: 6.6.145
- Vulnerability Type: Reflected XSS
- Severity: Medium
- CVSS v3.1 Score: 6.1 (AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N)
The application is vulnerable to a reflected XSS attack via the “GO_LANGUAGE” cookie that injects malicious JavaScript into the application's response. The malicious script is executed in the context of the affected website, allowing an attacker to steal sensitive information such as session cookies, personal information, etc. The vulnerability exists in the cookie of the Group Office application. By sending a specially crafted cookie to the server, an attacker can inject malicious JavaScript code into the response, which is then executed in the context of the affected website. This can result in sensitive information being stolen from the user's browser, such as session cookies and personal information.
This vulnerability allows an attacker to steal sensitive information from the affected website and its users, such as session cookies, personal information, and more. An attacker can also use this vulnerability to inject further malicious code into the affected website, compromising its functionality and potentially exposing sensitive information.
- Filter input data to prevent malicious payloads from being included in the response.
- Use a Content Security Policy (CSP) to restrict the execution of untrusted JavaScript in the response.
- Escape or encode all user input before including it in the response.
- Upgrade to version 6.6.147 of the Group Office application.
- Go to the vulnerable instance of group-office.
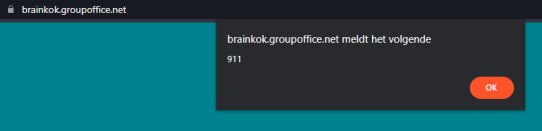
- Change the “GO_LANGUAGE” cookie with F12, to the following payload:
ar'"()&%<zzz><ScRiPt>alert(911)</ScRiPt>