SGXRay is an automated reasoning tool based on the SMACK verification toolchain that automatically detects SGX enclave bugs rooting from violations of trusted boundaries. It recompiles a given enclave code and starts the analysis from a user-specified enclave function entry. After the analysis, it either finds an invalid pointer handling inside an SGX software stack such as deferencing unchecked pointer inside an enclave, invalid memory deallocation, and time-of-check to time-of-use bugs, or prove the absense of such bugs up to a user-specified loop and recursion bound.
Currently, SGXRay SGX applications built on two SGX SDKs: Intel SGX SDK and Open Enclave SDK. Users can opt in SDK code for a more thorough analysis.
For a quick start, please follow a step-by-step tutorial on using SGXRay over one of the demo examples here.
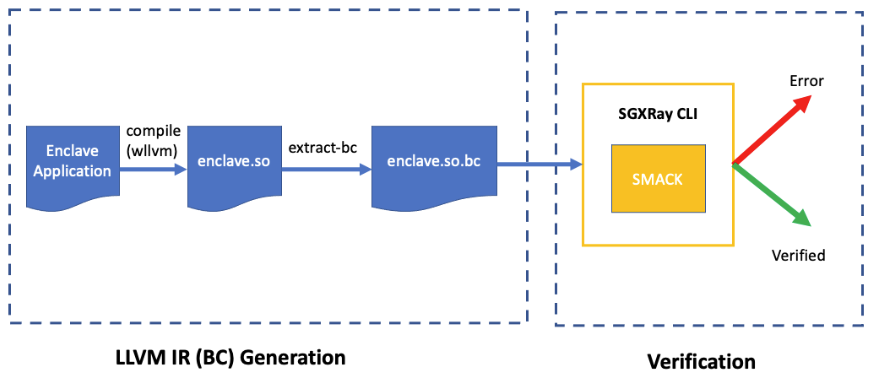
The following figure demonstrates the workflow of SGXRay.
Running SGXRay is a two-step process. The first step is to obtain an LLVM IR file for the application. The second step is to invoke the SGXRay CLI for verification.
For the first step, we provide two Docker images for each SDK, respectively.
docker pull baiduxlab/sgx-ray-frontend-intel
docker pull baiduxlab/sgx-ray-frontend-oeThe detailed instructions to run the first step can be found here.
For the second step, we also provide a Docker image.
docker pull baiduxlab/sgx-ray-distro:latestThe detailed instructions to run the second step can be found here.
We provide a script install.sh that installs SGXRay and its dependencies. Note that Clang-11 is required to get the bc
files of SGX applications so it is not included in this script. Installation of Clang-11 can be done via Debian packages or simply downloading it from LLVM's website.
To install SGXRay from scratch, simply clone this repo and run sudo ./install.sh from its root directory. SGXRay will be installed at the /opt/sgxray directory. For a rootless installation, please use ./install.sh --prefix <installation-path>.
We provide a Dockerfile that builds a image for the verification step.
git clone https://github.com/baidu/sgxray.git && cd sgxray
docker build . -t sgxray-localSuccesful installation using install.sh should produce an environment file sgx.environment at the installed path.
Source this file and the SGXRay CLI (sgx-ray) should in the path. The -h option provides an overview
of SGXRay CLI's option.
For a typical Intel SGX-based application, SGXRay CLI can be invoked as,
sgx-ray --intel --ecall-name <ecall> <enclave.so.bc>For a typical openenclave-based application, SGXRay CLI can be invoked as,
sgx-ray --oe --ecall-name <ecall> <enc.bc>We also provide detailed description of this step here.
The test cases are placed in the tests directory. To run them, please refer to the README file.
SGXRay is maintained by Shaobo He (shaobohe@baidu.com). Please submit issues if you have any feature requests or questions about SGXRay. Please create pull requests if you would like to contribute to SGXRay. Similar to SMACK, we adopt the following two simple guidelines for contributors.
- We use this git branching
model. Please avoid
working directly on the
masterbranch. - We follow guidelines for good git commit practice
A simple design documentation of SGXRay is here. Pelase refer to this file first if you would like to contribute.
SGXRay is Apache V2-licensed. Please refer to LICENSE for details.