This sample repository helps you to deploy a simple solution to watch for newly created accounts in your organization and submit a support case requesting the new account to have Enterprise Support enabled.
WARNING: This repository and its contents are only meant for Enterprise Support customers, as it is required to interact with AWS Support API and enable Enterprise Support to child accounts.
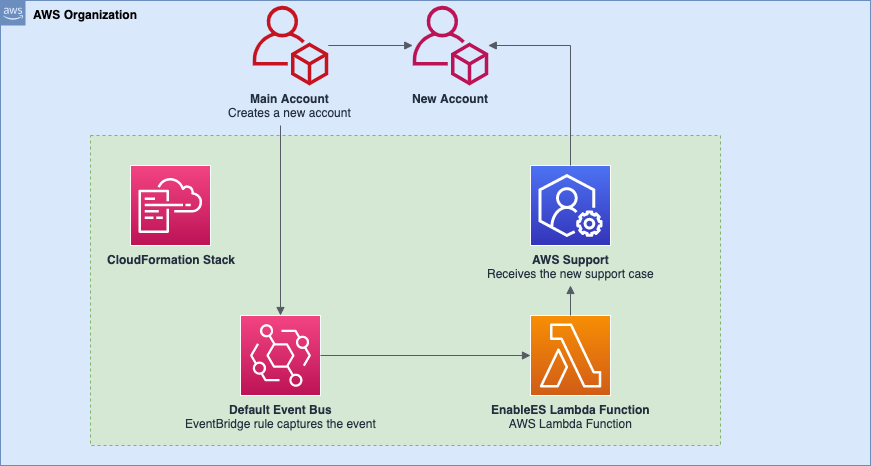
This solution should be deployed to your main account, where the new accounts are created.
This CloudFormation template will create in your account:
- An IAM role with permissions to execute your Lambda function, and interact with AWS Support API.
- AWS Lambda function, that will submit the support case requesting Enterprise Support to be enabled in the newly created account
- EventBridge Rule, which will be matching the event for
CreateAccountResultand passing this event to AWS Lambda - AWS Lambda Permission, which allows the event from EventBridge rule to trigger the AWS Lambda.
- When you create a new account in your organization, a new event
CreateAccountResultwill be generated in your CloudTrail. - The EventBridge rule will match this event if the creation state is
SUCCEEDEDand trigger the AWS Lambda function for processing, passing the whole Event body to the function. - The Lambda function will parse the Event body and look for the
Account IDof the newly created account. - Having the
Account ID, the function will connect to the AWS Support API and submit the support case, requesting Enterprise Support to be enabled on the newly created account. The support case will be created with aProduction System Impairedseverity.
To facilitate the implementation of this solution, you can simply deploy the CloudFormation template from this repository. You can also find the EventSample.json and rule.json used for this implementation on the samples directory and use this information to build the same manually if you prefer.
- Download or clone the repository
To start the deployment, clone this repository to the desired location, or download it as a ZIP file. On this example, I will be downloading it as a ZIP file.
- Extract files
Extract the files from the ZIP
- Open your AWS Managed Console
Using your preferred browser, open the AWS Managed Console.
- Navigate to the CloudFormation console
- Create a new Stack
On the top right corner of the page, click on Create stack -> With new resources (standard)
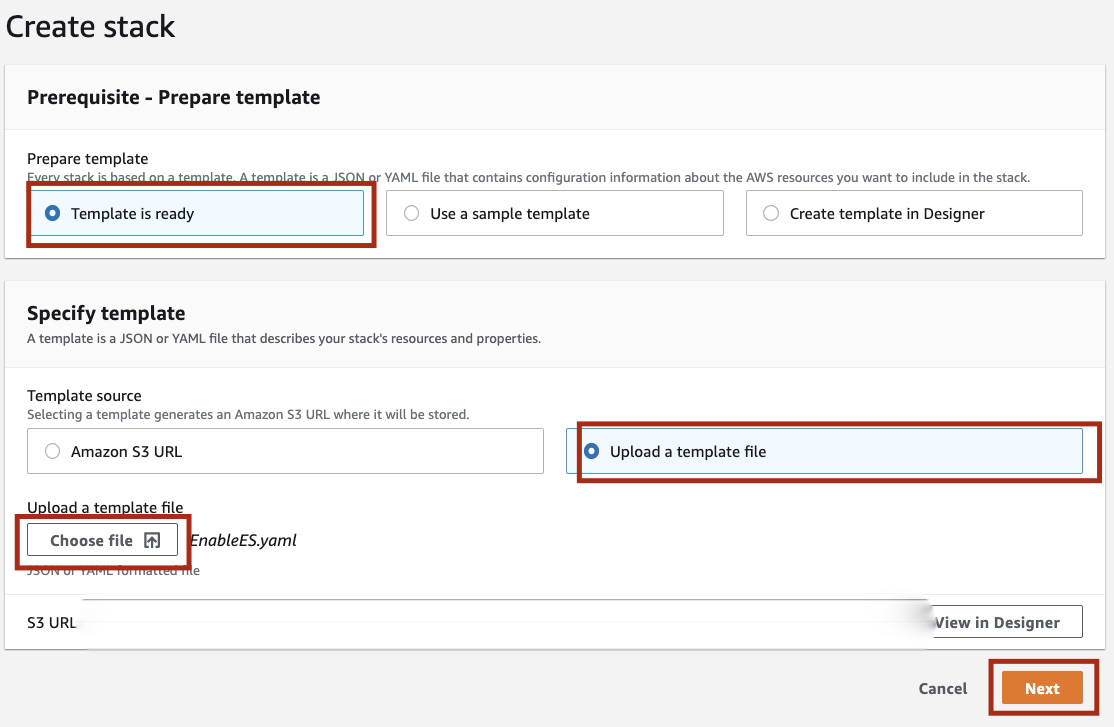
In the Prerequisite - Prepare template session, make sure the Template is ready option is selected.
For the Specify template, select Upload a template file and choose the template/EnableES.yaml file you downloaded from this repository.
Click in Next.
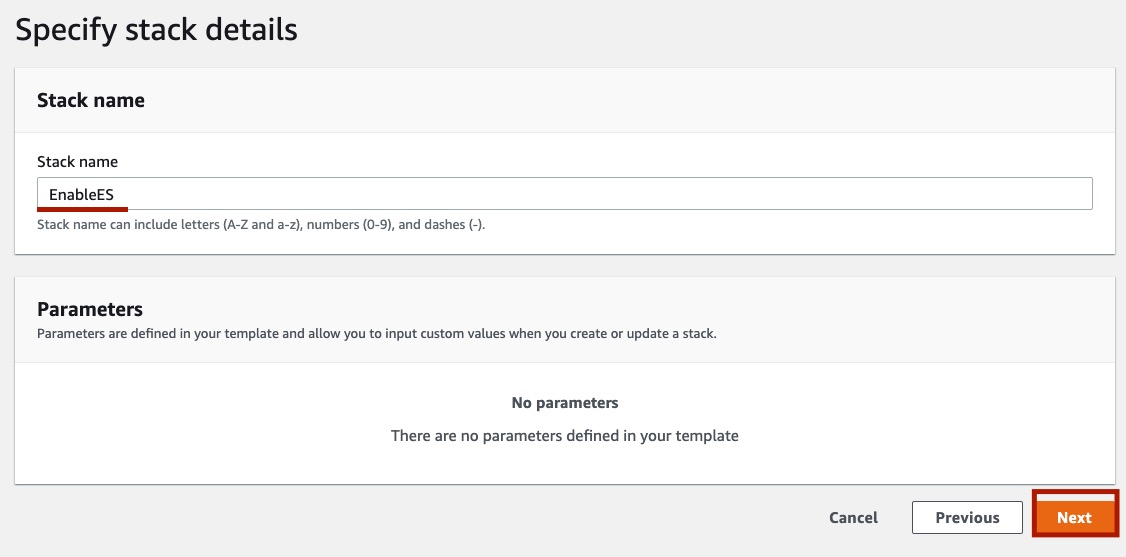
On the Specify stack details section, provide a name to your stack. This name will be added to the name of resources created on the stack. I will choose EnableES as stack name.
Click in Next.
On the Configure stack options section, you can provide Tags if you wish. Leave all the remaining fields as default.
On the bottom of the page, click Next.
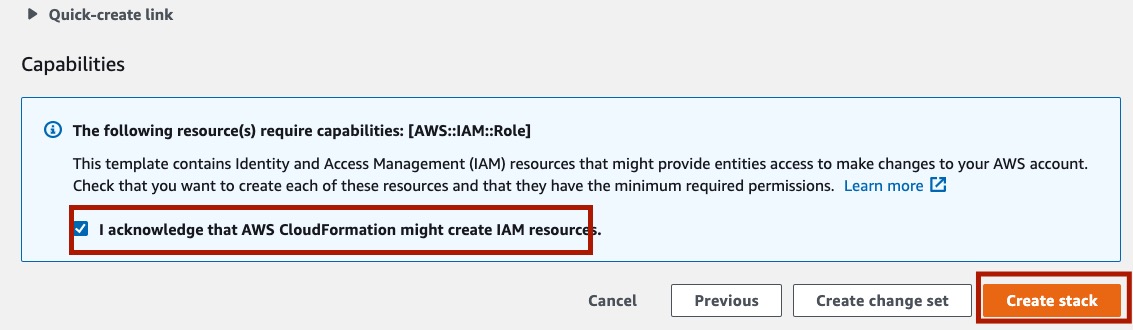
On the Review STACK_NAME page, scroll all the way down, make sure the check box I acknowledge that AWS CloudFormation might create IAM resources is checked, and click in Create stack.
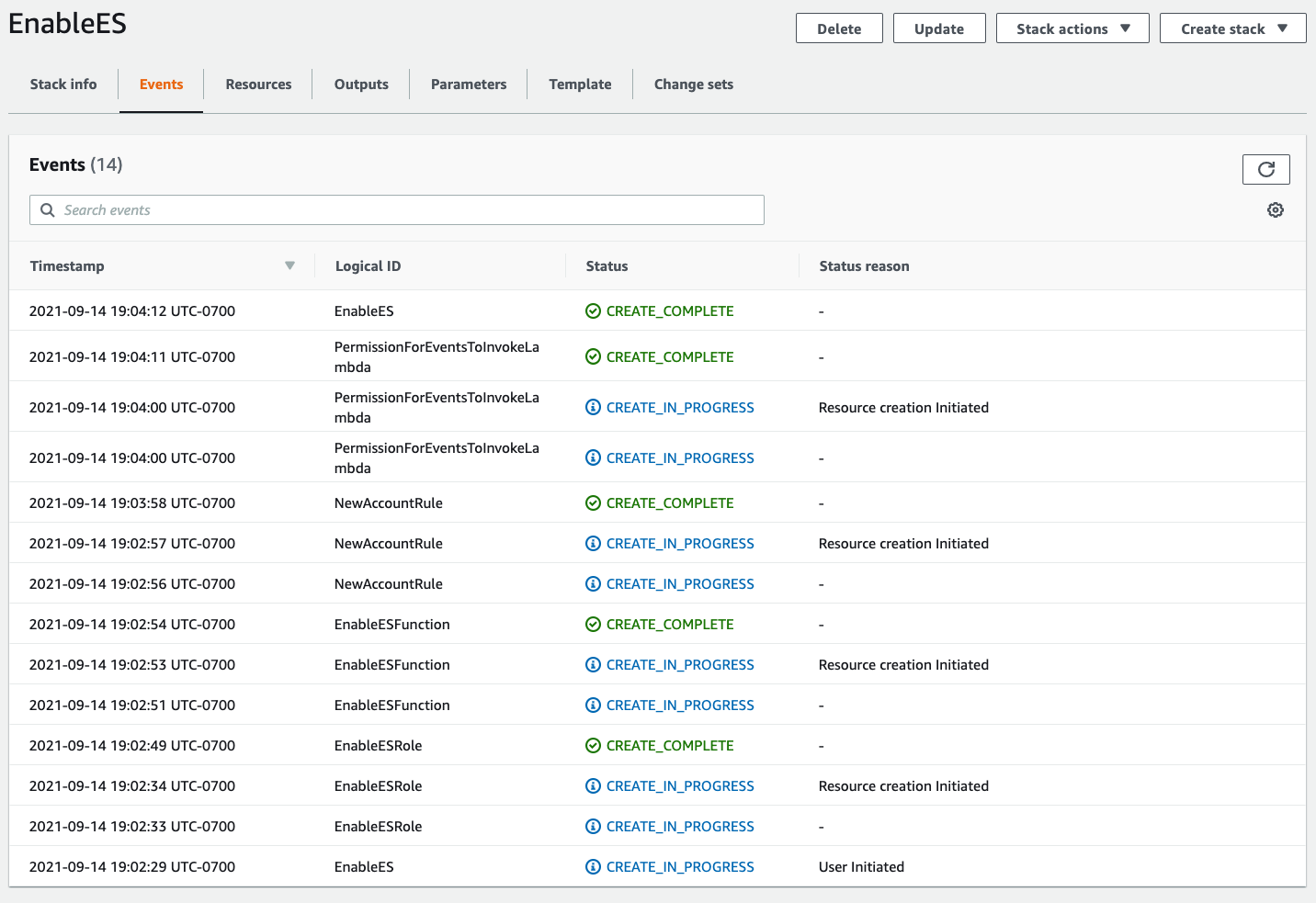
The setup process might take a few minutes to complete.
Click on the Refresh icon until you see CREATE_COMPLETE for the stack.
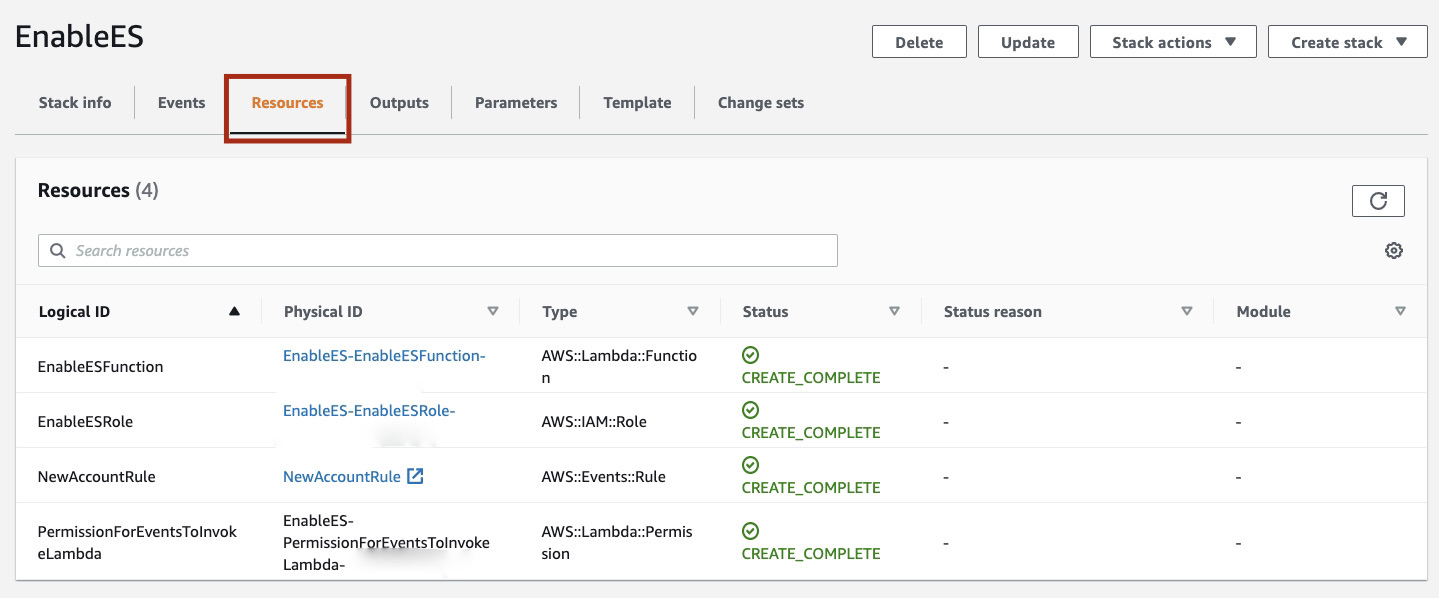
To validate the setup was completed successfully, check the Resources tab of your newly created Stack.
Click on the EnableESFunction Physical ID to open the AWS Lambda Function.
It will open the AWS Lambda Function in a new tab of your browser.
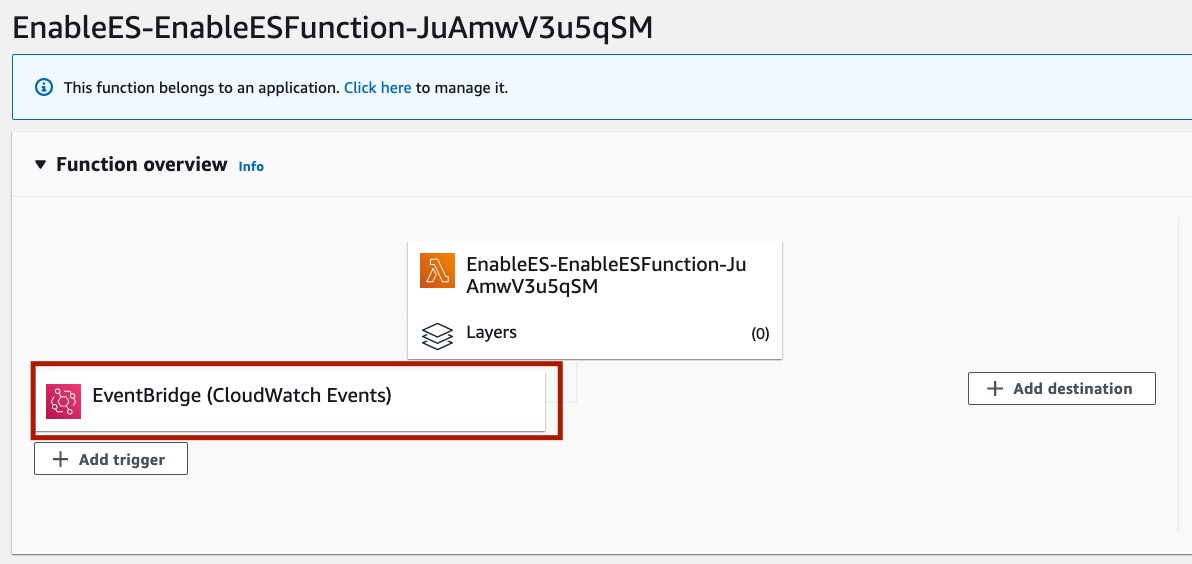
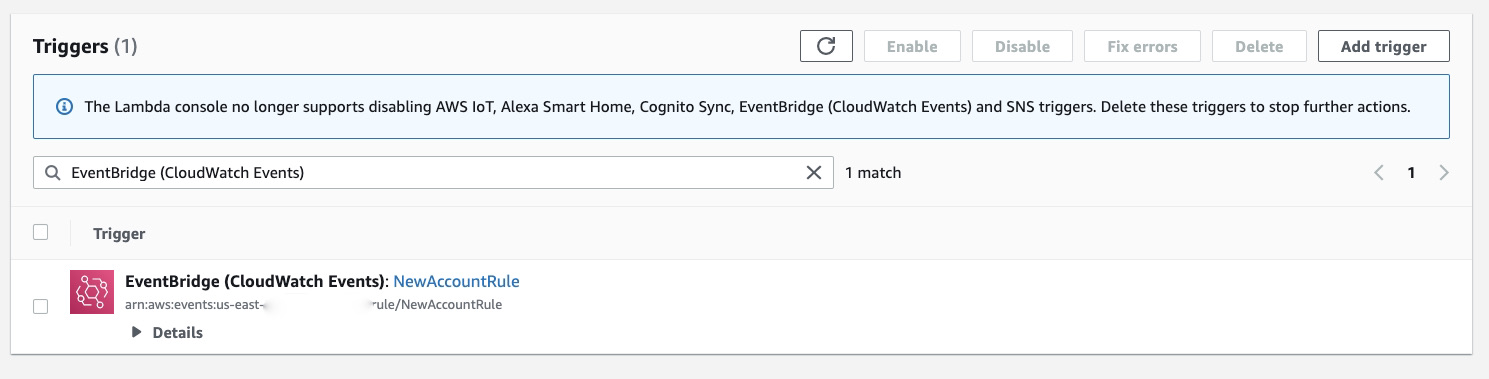
In the Lambda Function page, you should be able to see the EventBridge (CloudWatch) as a trigger for the code.
Seeing the EventBridge (CloudWatch) as the trigger for the code indicates the Lambda permissions are set correctly and EventBridge is able to invoke the function.
Click in the EventBridge (CloudWatch) to see available triggers for this function.
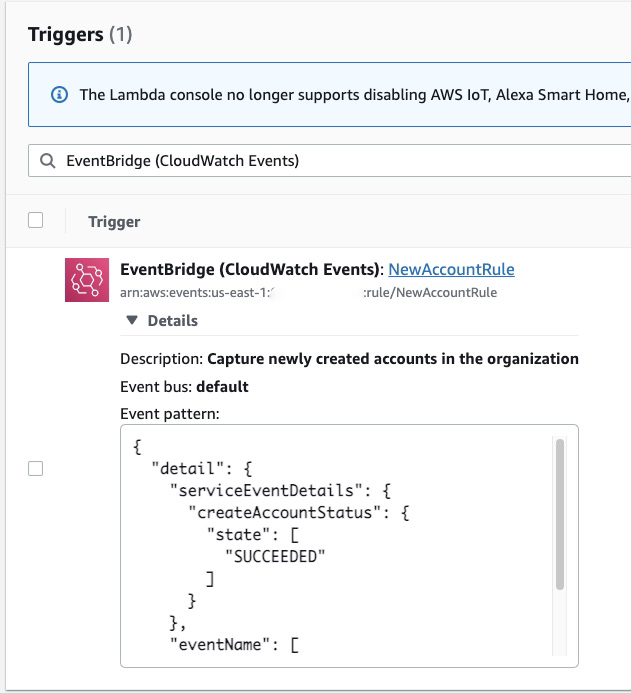
Only EventBridge (CloudWatch Events): NewAccountRule should be listed as a trigger.
You can click on Details to verify the Event pattern to match this rule.
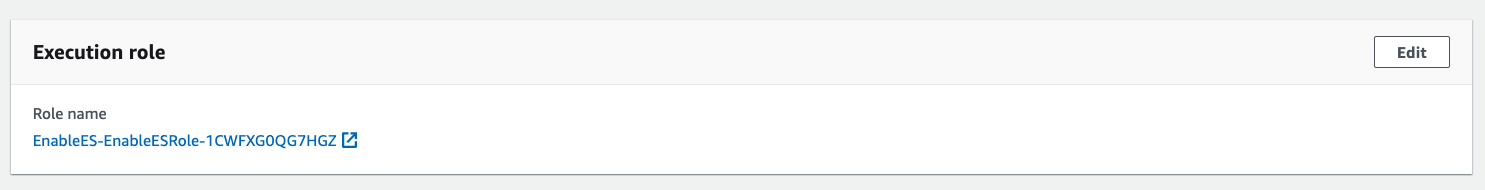
On the left panel for your Lambda function, click on Permissions to validate the IAM Role associated with the function.
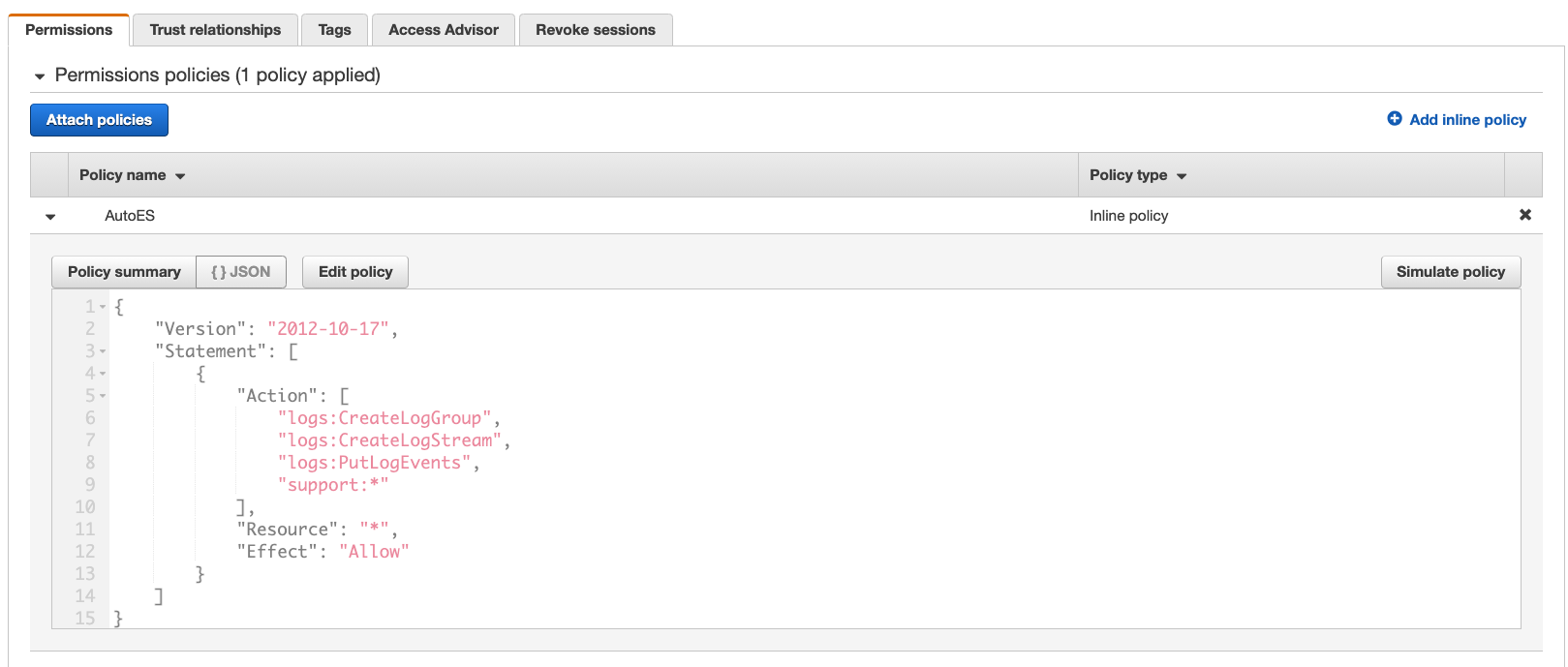
You will see there is a role associated with the function. This role name must start with EnableES-EnableESRole- and is the role that authorizes the function to be executed and to communicate with AWS Support API, submiting the support case to request enabling Enterprise Support on the newly created account.
If you click on the role name to see the details about the role, expand the AutoES policy to see the operations the role is allowed to perform.
If you confirm all the the steps of this document were executed as expected, the next you create a new account in your organization, it will automatically submit a support case requesting Enterprise Support to be enabled in the newly created account with a Production System Impaired severity.
Once you confirmed the automation to request enabling Enterprise Support on the newly created account works as exected, if you decide to delete all the associated resources:
- Navigate again to the CloudFormation console,
- List your stacks
- Select the
EnableESstack - Click on
Delete - Click on
Delete stackto confirm your action - Wait until the deletion is completed