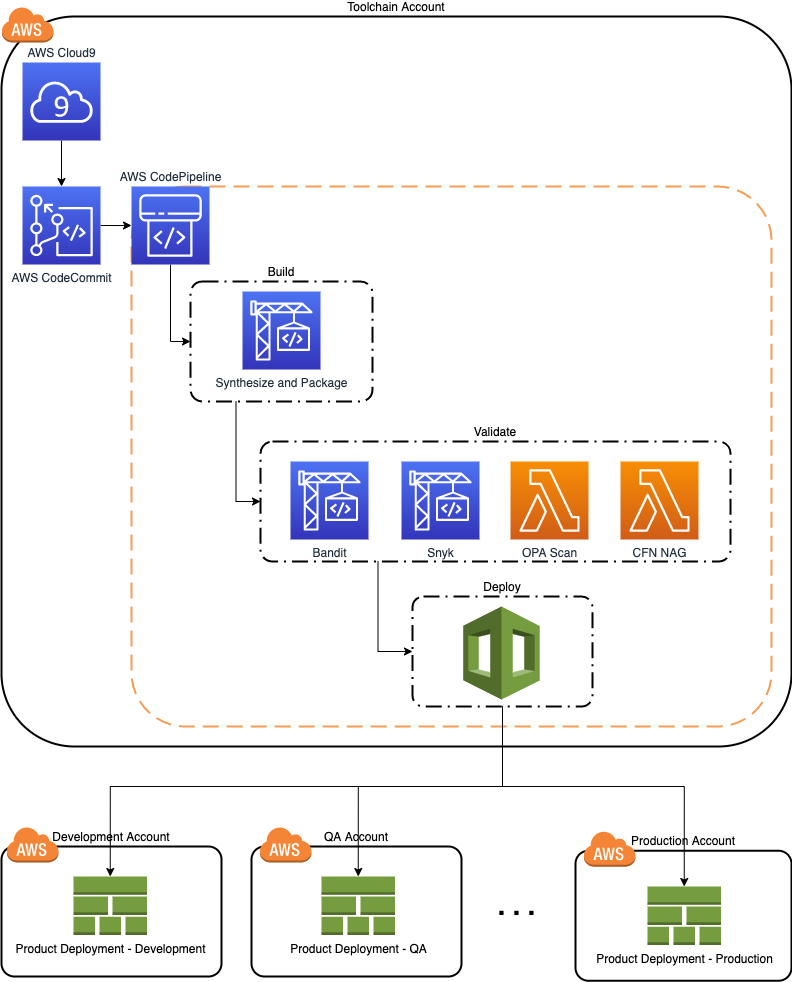
This artefact helps development teams to quickly set up a ready to use environment integrated with a multi-account CI/CD pipeline following security and DevOps best practices.
Upon successful deployment, you will have:
- an AWS CodeCommit Git repository
- an AWS Cloud9 development environment integrated with the code repository
- a multi-stage, multi-account CI/CD pipeline integrated with the code repository
- pipeline integration with Bandit for finding common security issues in Python code
- pipeline integration with Snyk for continuously monitoring for vulnerabilities in your dependencies
- pipeline integration with CFN NAG to look for patterns in CloudFormation templates that may indicate insecure infrastructure
- pipeline integration with Open Policy Agent (OPA) that enables you define and enforce policies on infrastructure resources at development time
- An AWS Account to be used as
Toolchainaccount - One or more AWS Account(s) to be used as deployment target accounts (e.g.
Dev,QA,Prod, etc.)
NOTE: Separating toolchain and deployment target accounts is technically not required, but is considered as best practice. We encourage you to start with a toolchain and a development account. You can easilty add new target environments to the pipeline in the future, if and when needed.
This project's code repository contains Git Submodules. If cloning for the first time, make sure to use
--recurse-submodules flag to automatically initialize and update submodules:
git clone --recurse-submodules https://github.com/aws-samples/devsecops-quickstart.git
If the repository is already cloned without the --recurse-submodules flag,
initialize and update submodules by running the following command:
git submodule update --init --recursive
For more information on working with Git repositories with submodules, refere to Git-Tools-Submodules documentation.
Locate cdk.json file on project's root folder. This is the project's configuration file.
Update cdk.json with account number and region values to be used for toolchain, and deployment target accounts.
The default setting has three deployment target accounts for Dev, QA, and Prod. This is just for demonstration purposes.
Feel free to add/remove deployment targets according to your requirements. You can for example start with a
single development account and keep adding more stages in the future as requierd.
NOTE: Make sure to commit your changes.
This project is set up like a standard Python project. The initialization
process also creates a virtualenv within this project, stored under the .venv
directory.
Use the following command to create a virtualenv on the project's root folder:
NOTE: Use
pythoninstead ofpython3on Windows.
python3 -m venv .venv
After the virtualenv is created, use the following step to activate your virtualenv.
source .venv/bin/activate
If you are a Windows platform, you would activate the virtualenv like this:
.venv\Scripts\activate.bat
Once the virtualenv is activated, install the required dependencies.
pip install -r requirements.txt
This is a one-time setup known as Bootstrapping, which you need to do for the toolchain and each deployment target account separately.
Do the following steps for toolchain account+region, that you configured in cdk.json in
step 2. Configure accounts and regions:
4. Configure AWS CLI to point to the account and region
NOTE: This can be quickly done as described in Quick configuration with aws configure section. Alternatively, you can use AWS CLI Profiles, which is more convenient when switching back and forth between multiple accounts.
NOTE: If you are using AWS CLI profiles, make sure to provide the
--profile <profile_name>option for every command interacting with AWS accounts below.
NOTE: Make sure to replace
toolchain_accountandtoolchain_regionplaceholders.
cdk bootstrap \
--cloudformation-execution-policies arn:aws:iam::aws:policy/AdministratorAccess \
aws://<toolchain_account>/<toolchain_region>
Repeat the following steps for each deployment target account+region that you configured in cdk.json in
step 2. Configure accounts and regions:
6. Configure AWS CLI to point to the account and rgion
NOTE: Make sure to replace
<toolchain_account>,<deployment_target_account>, and<deployment_target_region>placeholders.
cdk bootstrap \
--trust <toolchain_account> \
--cloudformation-execution-policies arn:aws:iam::aws:policy/AdministratorAccess \
aws://<deployment_target_account>/<deployment_target_region>
For Snyk integration, you need to provide authentication token with a Snyk profile account. You can sign up for a free Snyk account here. After sign up, you can get your Auth Token from the Account Settings section in your profile.
NOTE: When signing up for a new account on Snyk, the whizzard routes you to a final step to select a Git repository and provide integration for Snyk to monitor that repository. This step is not mandatory for creating Snyk accounts and is not required for our setup, either. Simply skip that by choosing
Select from other repositorieswhich will bring you directly to your profile.
With the Snyk authentication token retrieved, use create_secret_helper utility to securely store
the token in AWS Secret Manager in toolchain account.
It will be automatically used by the pipeline to interact with Snyk during the pipeline execution.
8. Configure AWS CLI to point to the account and rgion
TODO: Pass profile to CLI commands
./create_secret_helper.sh snyk-auth-token <snyk-auth-token-value> <toolchain_profile_name>
9. Configure AWS CLI to point to the account and region
Create a new Git repository in the toolchain account. This will become the main repository used by the pipeline for deployments, where you will be developing your application.
aws codecommit create-repository --repository-name devsecops-quickstart
Take note of cloneUrlHttp value in the command output.
If this is the first time you are using AWS CodeCommit, you need to configure a Git Credential Helper to be able to access CodeCommit repositories using HTTPS. Follow AWS CodeCommit documentation to set up a credential helper on Linux, macOS, or Unix or Windows.
NOTE: Make sure to replace
<codecommit_repository_url>placeholder withcloneUrlHttpvalue from step 9. Create Git repository.
git remote add codecommit <codecommit_repository_url>
git checkout -b main
git add .
git commit -m "initial commit"
git push --set-upstream codecommit main
13. Configure AWS CLI to point to the account and region
Run CDK deploy command to build and deploy the CI/CD pipeline.
cdk deploy devsecops-quickstart-cicd
Login to the toolchain account in AWS Console. Select the same region you used for the deployment.
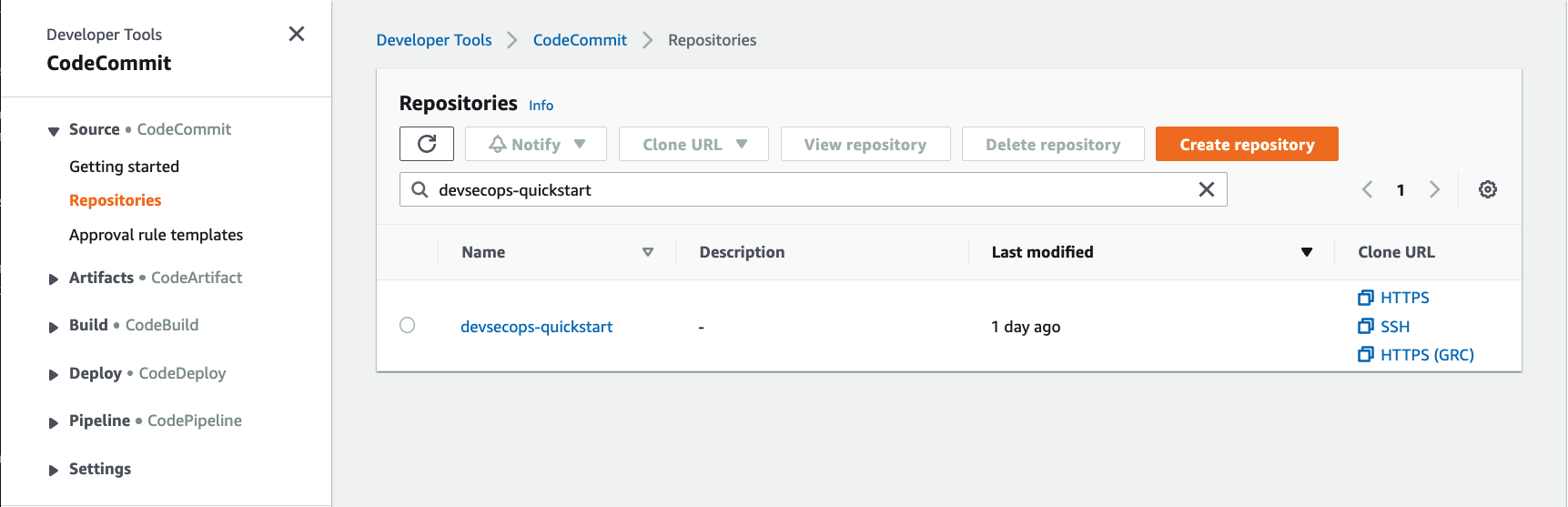
Navigate to AWS CodeCommit service, select Source/Repositories from the left navigation bar, and verify that a new repository has been created.
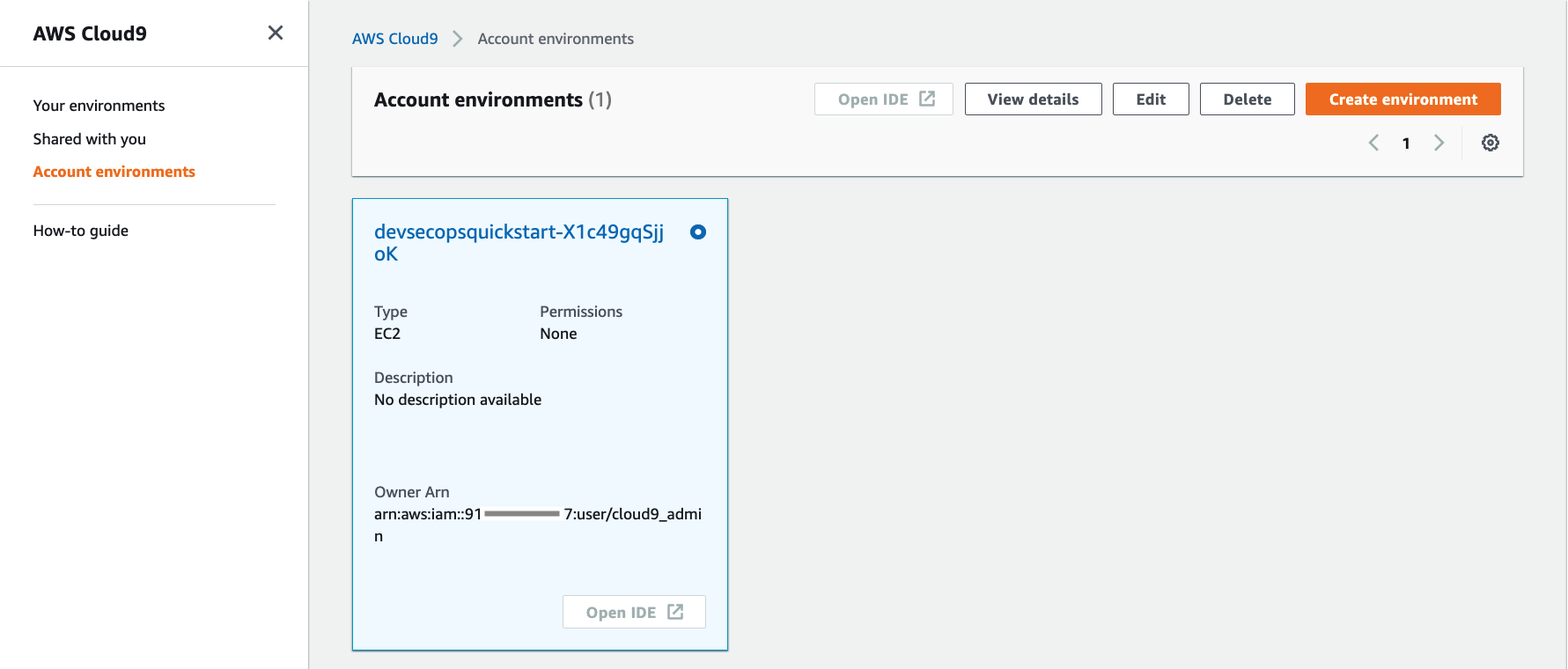
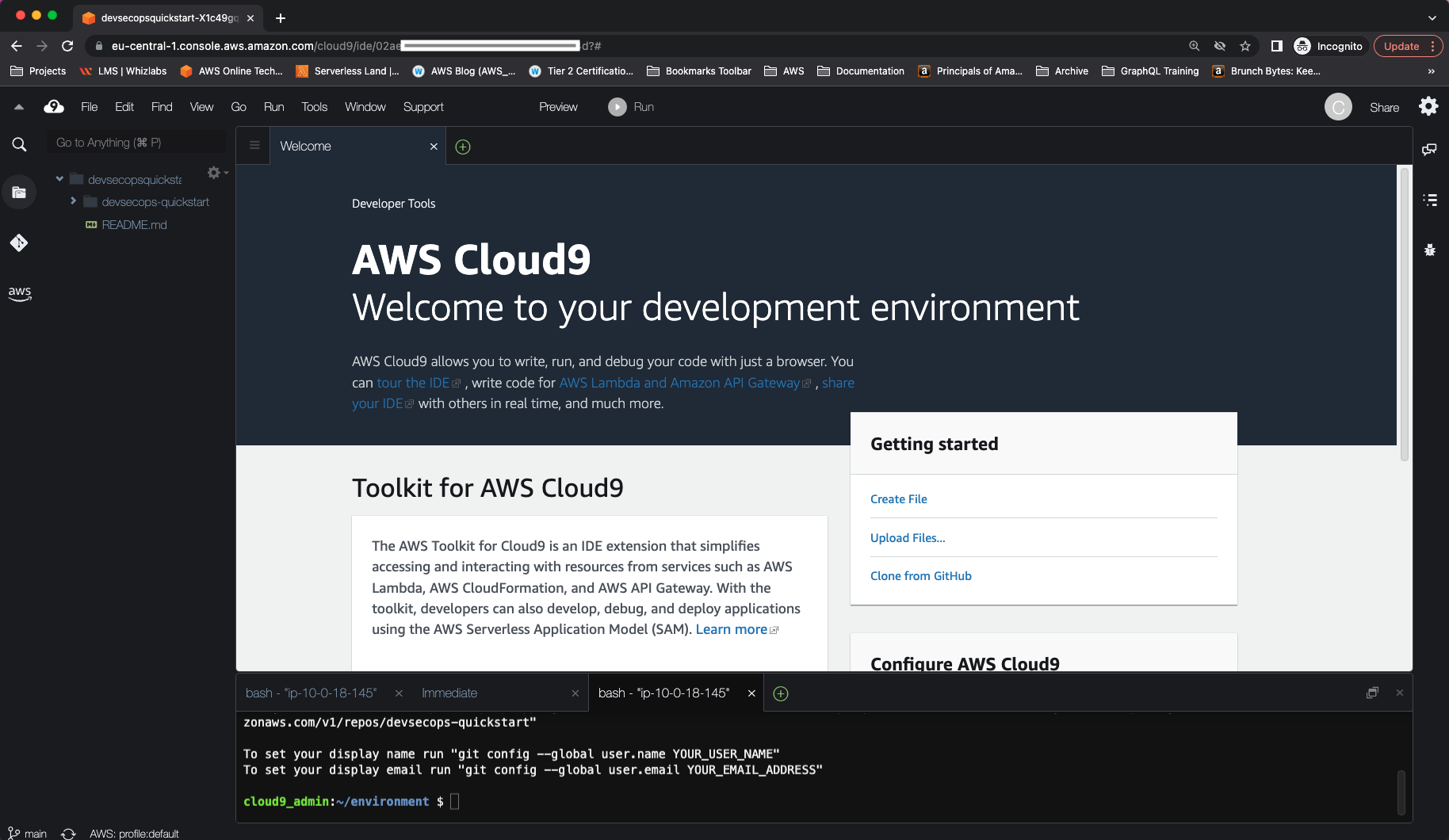
Navigate to AWS Cloud9 service, select Account Environments from the left navigation bar, and verify that a new Cloud9 environment has been created.
Note that cloud9_admin is the owner of the environment and Open IDE buttion is disabled. To access the
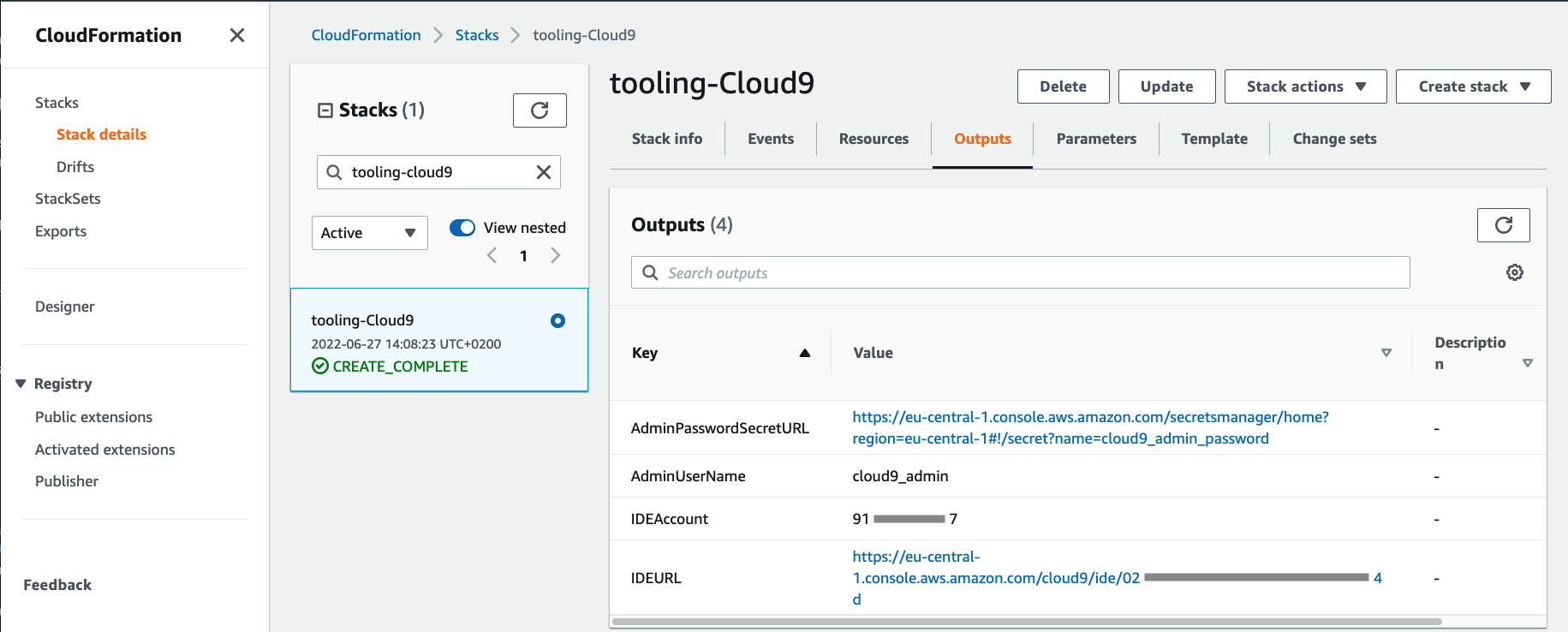
Cloud9 environment, go to CloudFormation service, open tooling-cloud9 stack, and select Outputs section from the top navigation bar.
Copy the IDEURL link and open it in a new incognito browser tab. For Sign In select IAM User. For Account number use the IDEAccount value from stack outputs, and for IAM user use AdminUserName. The Password needs to be retrieved from AWS Secret Manager by following the link in AdminPasswordSecretURL and selecting Retrieve Secret Value under Secret Value section. After successful login, you get access to the Cloud9 environment.
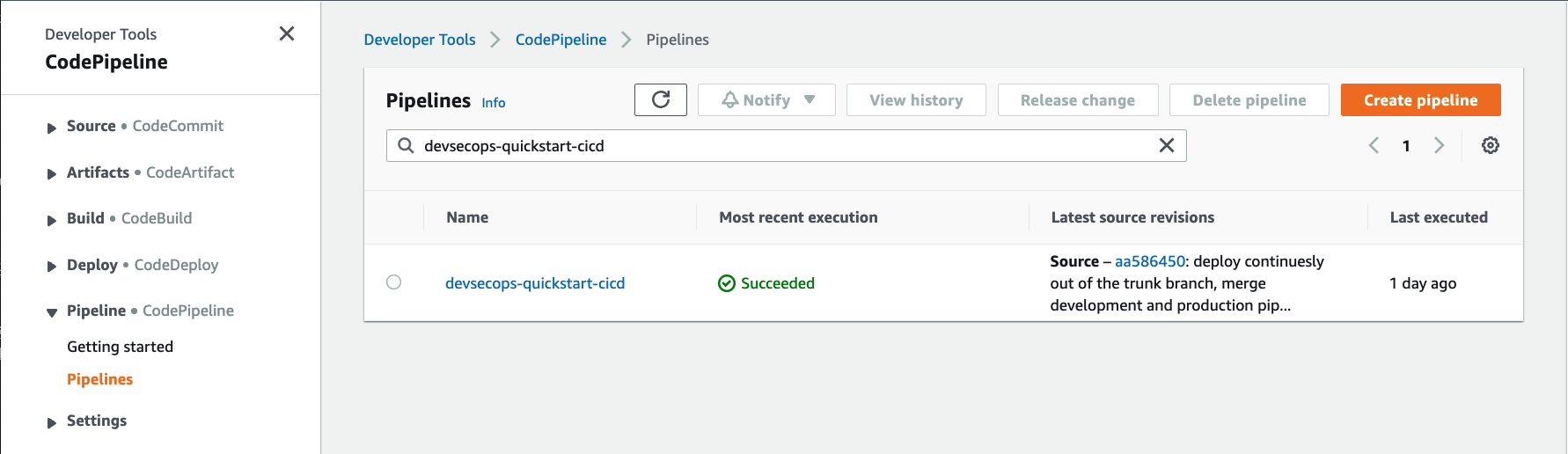
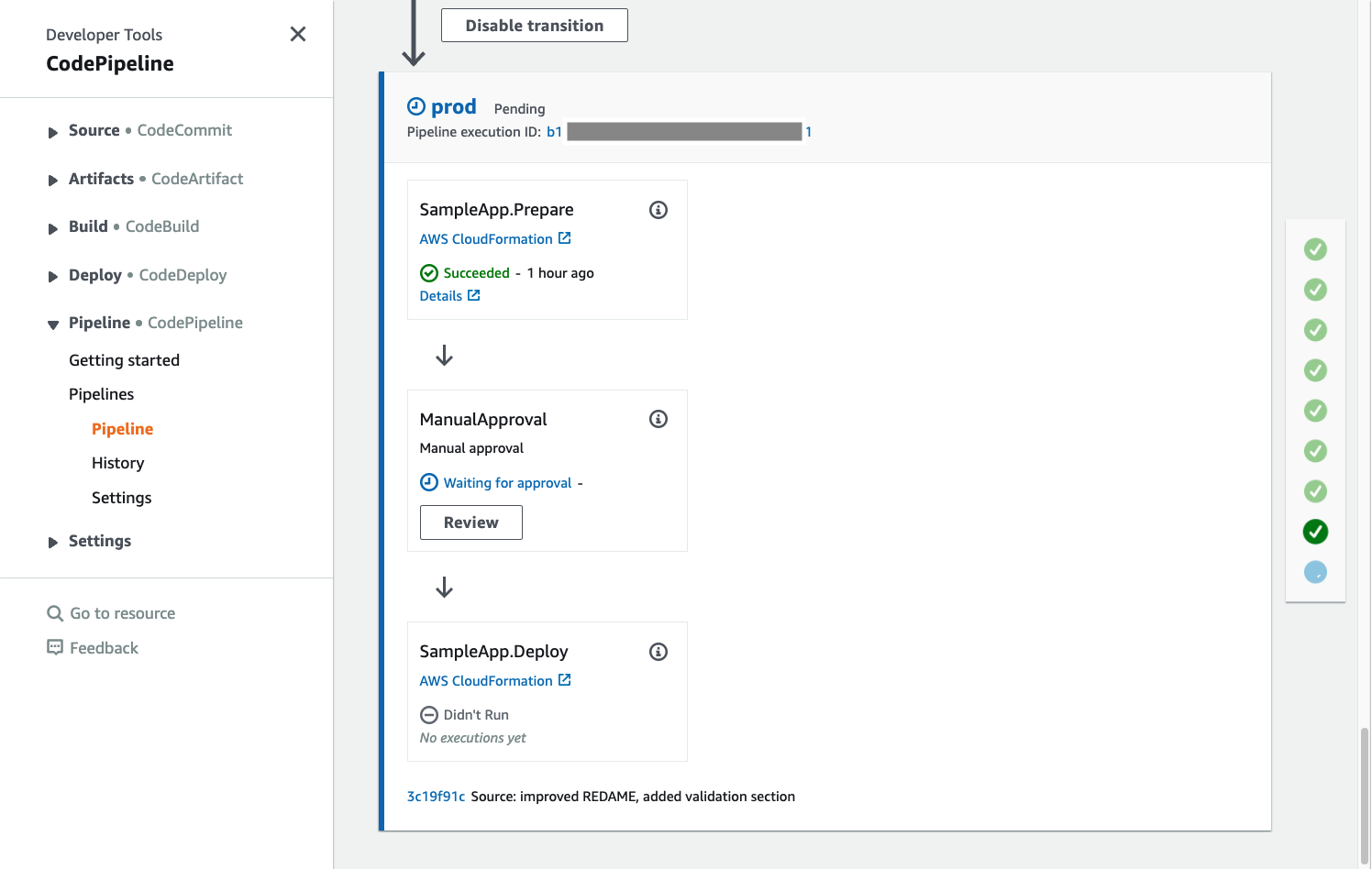
Navigate to AWS CodePipeline service, select Pipeline/Pipelines from the left navigation bar, and verify that a new pipeline has been created.
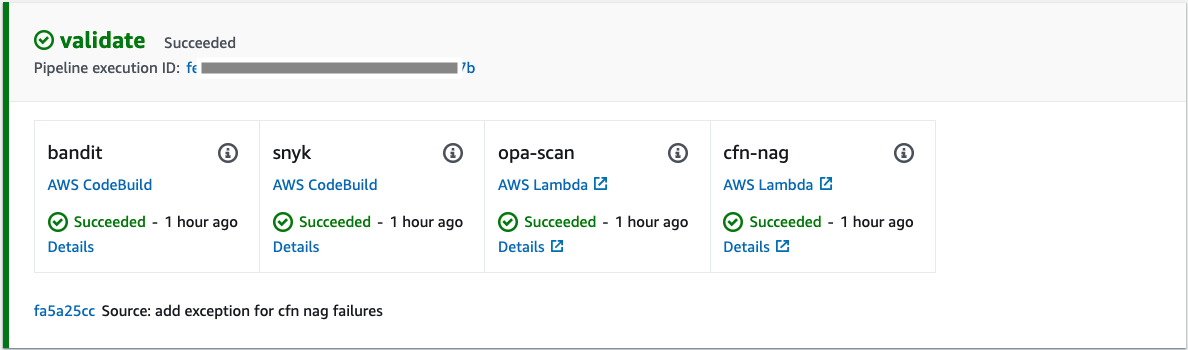
Open the pipeline and scroll down to validate stage. This is the stage where all the validation steps will be run.
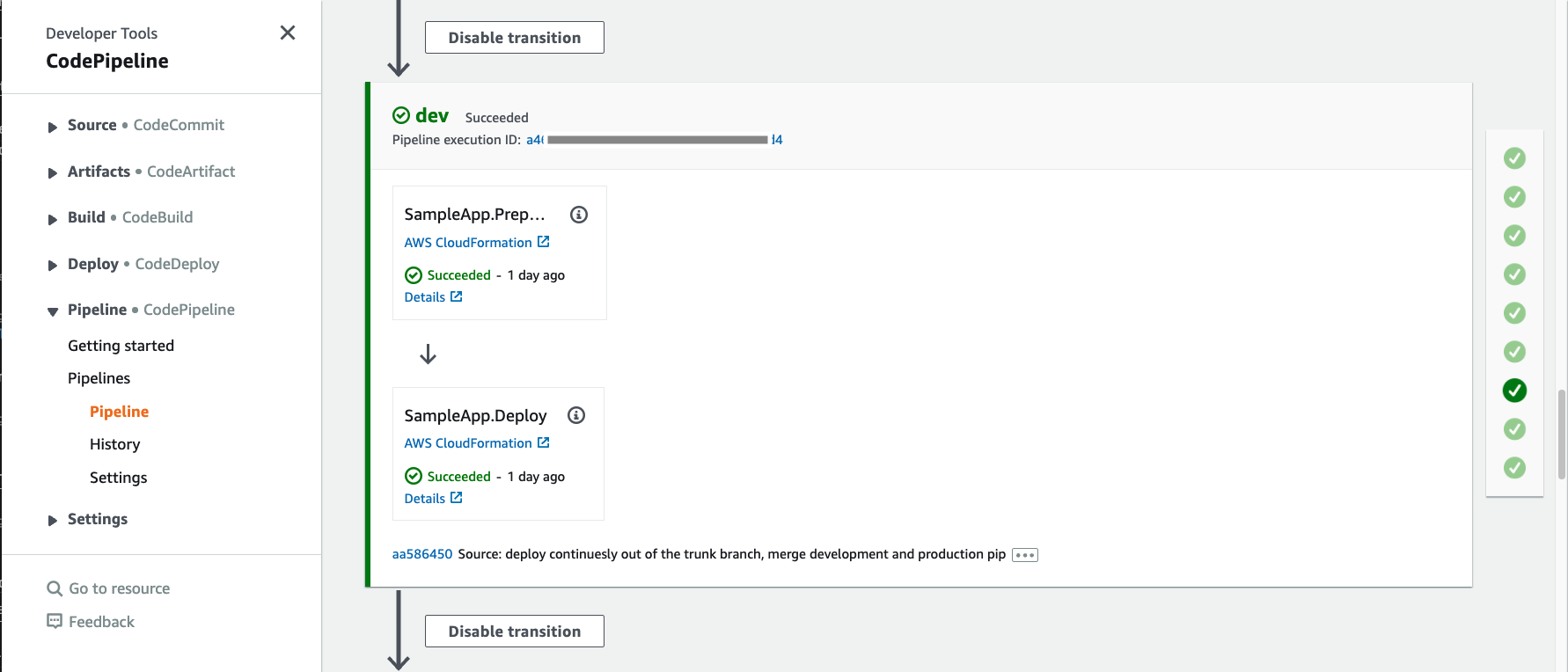
After validation you can see the deployment stage(s). The number of the stages correspond to the number of target accounts you have configured in the cdk.json file as described in the Deploy section.
If you have enabled manual approvals in the stage configuration in cdk.json, the corresponding pipeline stage will have a mandatory manual approval before deploying to that environment.
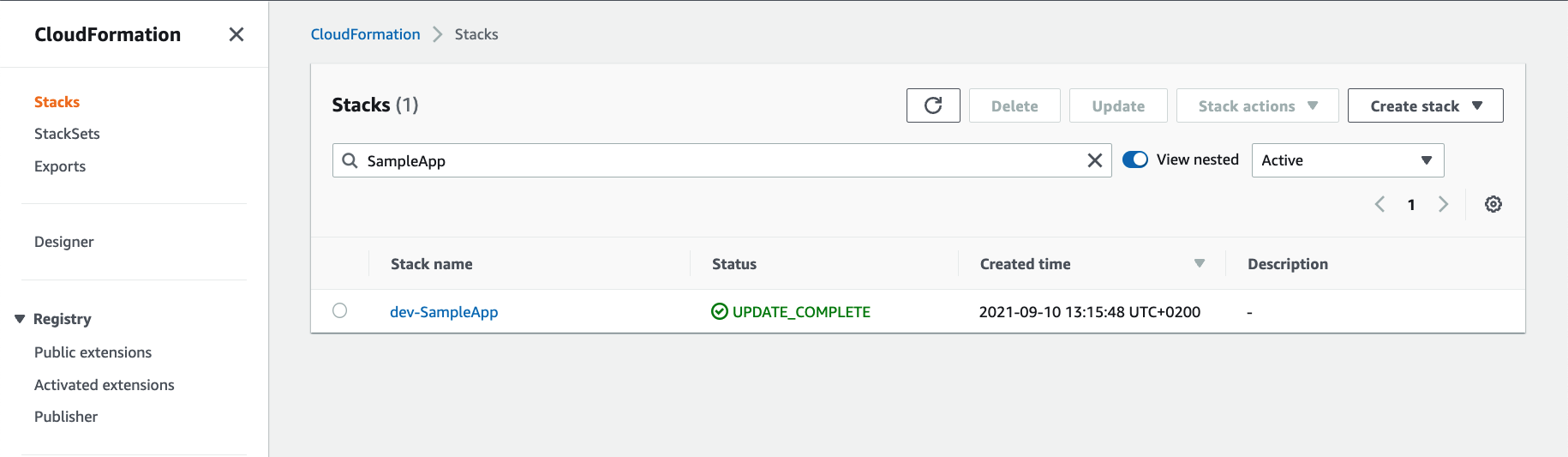
For each target account, login to the account in AWS Console. Make sure you are in the same region as you used for the deployment. Navigate to CloudFormation service and search for the application stack that is deployed by the pipeline. This pipeline comes with a sample application called SampleApp which is deployed for demonstration purposes. You can add your application stacks following the same approach and the pipeline will take care of deploying them into your target environments.
The pipeline you just created is deploying a dummy application stack called SampleApp. The stack is defined in
devsecops_quickstart/sample_app/sample_app.py and is integrated into the pipeline definition in
devsecops_quickstart/pipeline.py.
It is now your turn to roll up the sleeves and develop your application stack(s). Follow the same approach as in
the SampleApp to define you application stage and integrate it into the pipeline.
Have fun!
A: Check the CloudFormation Outputs section of the stack called tooling-Cloud9. There you can find output parameters
for the environment URL, admin user, and the AWS Secret Manager secret containing the admin password.
A: Deployment targets are configured in cdk.json file under context.config.stage variable. You can add as many stages
to the pipeline as required, both now or in the future. Simply give your new stage a name and provide values for account, region, and wheather
manual approval is required. Then commit and push the changes to trigger the pipeline. The pipeline is capable of mutating
itself to dynamically adjust to your configuration.
See CONTRIBUTING for more information.
This library is licensed under the MIT-0 License. See the LICENSE file.