faasd is built for everyone else, for those who have no desire to manage expensive infrastructure.
faasd is OpenFaaS reimagined, but without the cost and complexity of Kubernetes. It runs on a single host with very modest requirements, making it fast and easy to manage. Under the hood it uses containerd and Container Networking Interface (CNI) along with the same core OpenFaaS components from the main project.
- You have a cost sensitive project - run faasd on a 5-10 USD VPS or on your Raspberry Pi
- When you just need a few functions or microservices, without the cost of a cluster
- When you don't have the bandwidth to learn or manage Kubernetes
- To deploy embedded apps in IoT and edge use-cases
- To shrink-wrap applications for use with a customer or client
faasd does not create the same maintenance burden you'll find with maintaining, upgrading, and securing a Kubernetes cluster. You can deploy it and walk away, in the worst case, just deploy a new VM and deploy your functions again.
- is a single Golang binary
- uses the same core components and ecosystem of OpenFaaS
- is multi-arch, so works on Intel
x86_64and ARM out the box - can be set-up and left alone to run your applications
Demo of faasd running in KVM
If your IaaS supports user_data aka "cloud-init", then this guide is for you. If not, then checkout the approach and feel free to run each step manually.
You can run this tutorial on your Raspberry Pi, or adapt the steps for a regular Linux VM/VPS host.
Automate everything within < 60 seconds and get a public URL and IP address back. Customise as required, or adapt to your preferred cloud such as AWS EC2.
To use private image repos, ~/.docker/config.json needs to be copied to /var/lib/faasd/.docker/config.json.
If you'd like to set up your own private registry, see this tutorial.
Beware that running docker login on MacOS and Windows may create an empty file with your credentials stored in the system helper.
Alternatively, use you can use the registry-login command from the OpenFaaS Cloud bootstrap tool (ofc-bootstrap):
curl -sLSf https://raw.githubusercontent.com/openfaas-incubator/ofc-bootstrap/master/get.sh | sudo sh
ofc-bootstrap registry-login --username <your-registry-username> --password-stdin
# (the enter your password and hit return)The file will be created in ./credentials/
You can view the logs of functions using journalctl:
journalctl -t openfaas-fn:FUNCTION_NAME
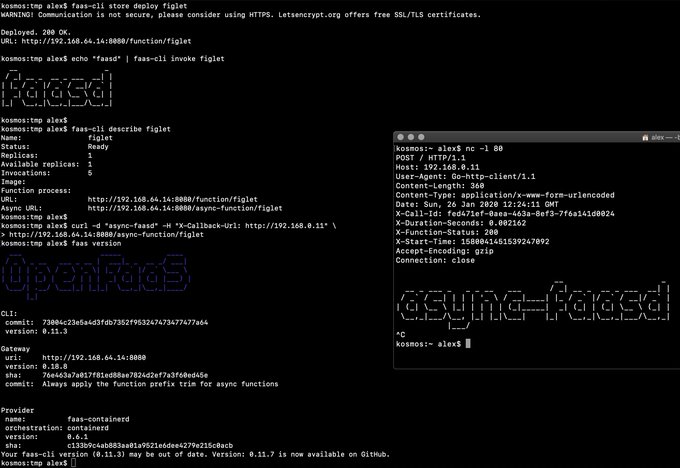
faas-cli store deploy figlet
journalctl -t openfaas-fn:figlet -f &
echo logs | faas-cli invoke figletCore services as defined in the docker-compose.yaml file are deployed as containers by faasd.
View the logs for a component by giving its NAME:
journalctl -t default:NAME
journalctl -t default:gateway
journalctl -t default:queue-workerYou can also use -f to follow the logs, or --lines to tail a number of lines, or --since to give a timeframe.
The OpenFaaS stack is made up of several core services including NATS and Prometheus. You can expose these through the docker-compose.yaml file located at /var/lib/faasd.
Expose the gateway to all adapters:
gateway:
ports:
- "8080:8080"Expose Prometheus only to 127.0.0.1:
prometheus:
ports:
- "127.0.0.1:9090:9090"To upgrade faasd either re-create your VM using Terraform, or simply replace the faasd binary with a newer one.
systemctl stop faasd-provider
systemctl stop faasd
# Replace /usr/local/bin/faasd with the desired release
# Replace /var/lib/faasd/docker-compose.yaml with the matching version for
# that release.
# Remember to keep any custom patches you make such as exposing additional
# ports, or updating timeout values
systemctl start faasd
systemctl start faasd-providerYou could also perform this task over SSH, or use a configuration management tool.
Note: if you are using Caddy or Let's Encrypt for free SSL certificates, that you may hit rate-limits for generating new certificates if you do this too often within a given week.
Memory limits for functions are supported. When the limit is exceeded the function will be killed.
Example:
functions:
figlet:
skip_build: true
image: functions/figlet:latest
limits:
memory: 20Mi- faasd - itself, and its faas-provider for containerd - CRUD for functions and services, implements the OpenFaaS REST API
- Prometheus - for monitoring of services, metrics, scaling and dashboards
- OpenFaaS Gateway - the UI portal, CLI, and other OpenFaaS tooling can talk to this.
- OpenFaaS queue-worker for NATS - run your invocations in the background without adding any code. See also: asynchronous invocations
- NATS for asynchronous processing and queues
You'll also need:
You can use the standard faas-cli along with pre-packaged functions from the Function Store, or build your own using any OpenFaaS template.
See here for manual / developer instructions
The OpenFaaS docs provide a wealth of information and are kept up to date with new features.
For community functions see faas-cli store --help
For templates built by the community see: faas-cli template store list, you can also use the dockerfile template if you just want to migrate an existing service without the benefits of using a template.
The founder of faasd and OpenFaaS has written a training course for the LinuxFoundation which also covers how to use OpenFaaS on Kubernetes. Much of the same concepts can be applied to faasd, and the course is free:
The OpenFaaS workshop is a set of 12 self-paced labs and provides a great starting point for learning the features of openfaas. Not all features will be available or usable with faasd.
An active community of almost 3000 users awaits you on Slack. Over 250 of those users are also contributors and help maintain the code.
faas loginfaas upfaas listfaas describefaas deploy --update=true --replace=falsefaas invoke --asyncfaas invokefaas rmfaas store list/deploy/inspectfaas versionfaas namespacefaas secretfaas logs
Scale from and to zero is also supported. On a Dell XPS with a small, pre-pulled image unpausing an existing task took 0.19s and starting a task for a killed function took 0.39s. There may be further optimizations to be gained.
Other operations are pending development in the provider such as:
faas auth- supported for Basic Authentication, but OAuth2 & OIDC require a patch
- Store and retrieve annotations in function spec - in progress
- Offer live rolling-updates, with zero downtime - requires moving to IDs vs. names for function containers
- An installer for faasd and dependencies - runc, containerd
- Monitor and restart any of the core components at runtime if the container stops
- Provide ufw rules / example for blocking access to everything but a reverse proxy to the gateway container
- Provide simple Caddyfile example in the README showing how to expose the faasd proxy on port 80/443 with TLS
- Provide a cloud-init configuration for faasd bootstrap
- Configure core services from a docker-compose.yaml file
- Store and fetch logs from the journal
- Add support for using container images in third-party public registries
- Add support for using container images in private third-party registries
- Provide a cloud-config.txt file for automated deployments of
faasd - Inject / manage IPs between core components for service to service communication - i.e. so Prometheus can scrape the OpenFaaS gateway - done via
/etc/hostsmount - Add queue-worker and NATS
- Create faasd.service and faasd-provider.service
- Self-install / create systemd service via
faasd install - Restart containers upon restart of faasd
- Clear / remove containers and tasks with SIGTERM / SIGINT
- Determine armhf/arm64 containers to run for gateway
- Configure
basic_authto protect the OpenFaaS gateway and faasd-provider HTTP API - Setup custom working directory for faasd
/var/lib/faasd/ - Use CNI to create network namespaces and adapters
- Optionally expose core services from the docker-compose.yaml file, locally or to all adapters.
WIP:
- Annotation support (PR ready)
- Hard memory limits for functions (PR ready)