This repository contains a reference AWS Platform Configuration for use as a starting point in Upbound Cloud or Upbound Universal Crossplane (UXP) to build, run and operate your own internal cloud platform and offer a self-service console and API to your internal teams. It provides platform APIs to provision fully configured EKS clusters, with secure networking, and stateful cloud services (RDS) designed to securely connect to the nodes in each EKS cluster -- all composed using cloud service primitives from the Crossplane AWS Provider. App deployments can securely connect to the infrastructure they need using secrets distributed directly to the app namespace.
- Upbound Cloud
- Build Your Own Internal Cloud Platform
- Quick Start
- Platform Ops/SRE: Run your own internal cloud platform
- Customize for your Organization
- Learn More
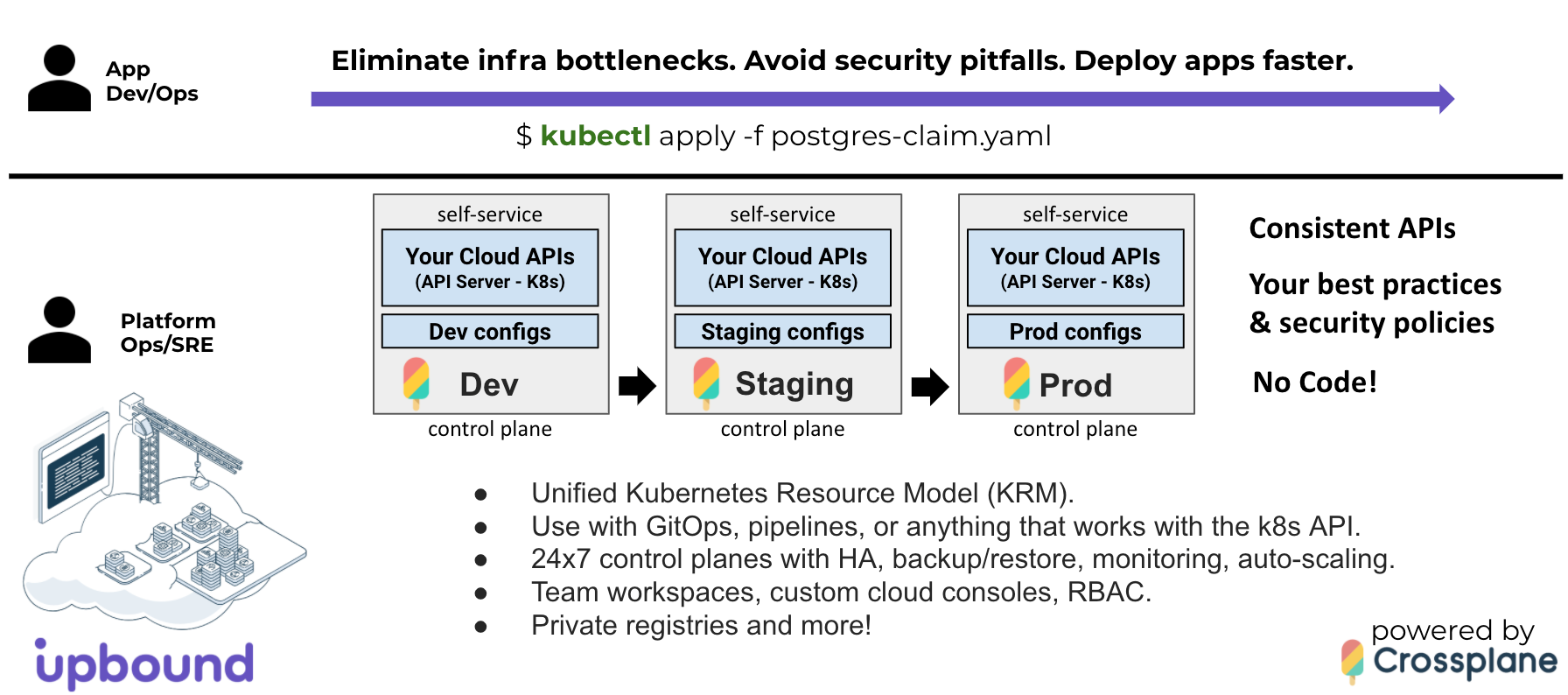
What if you could eliminate infrastructure bottlenecks, security pitfalls, and
deliver apps faster by providing your teams with self-service APIs that
encapsulate your best practices and security policies, so they can quickly
provision the infrastructure they need using a custom cloud console, kubectl,
or deployment pipelines and GitOps workflows -- all without writing code?
Upbound Cloud enables you to do just that, powered by the open source Upbound Universal Crossplane project.
Consistent self-service APIs can be provided across dev, staging, and production environments, making it easy for app teams to get the infrastructure they need using vetted infrastructure configurations that meet the standards of your organization.
App teams can provision the infrastructure they need with a single YAML file
alongside Deployments and Services using existing tools and workflows
including tools like kubectl and Flux to consume your platform's self-service
APIs.
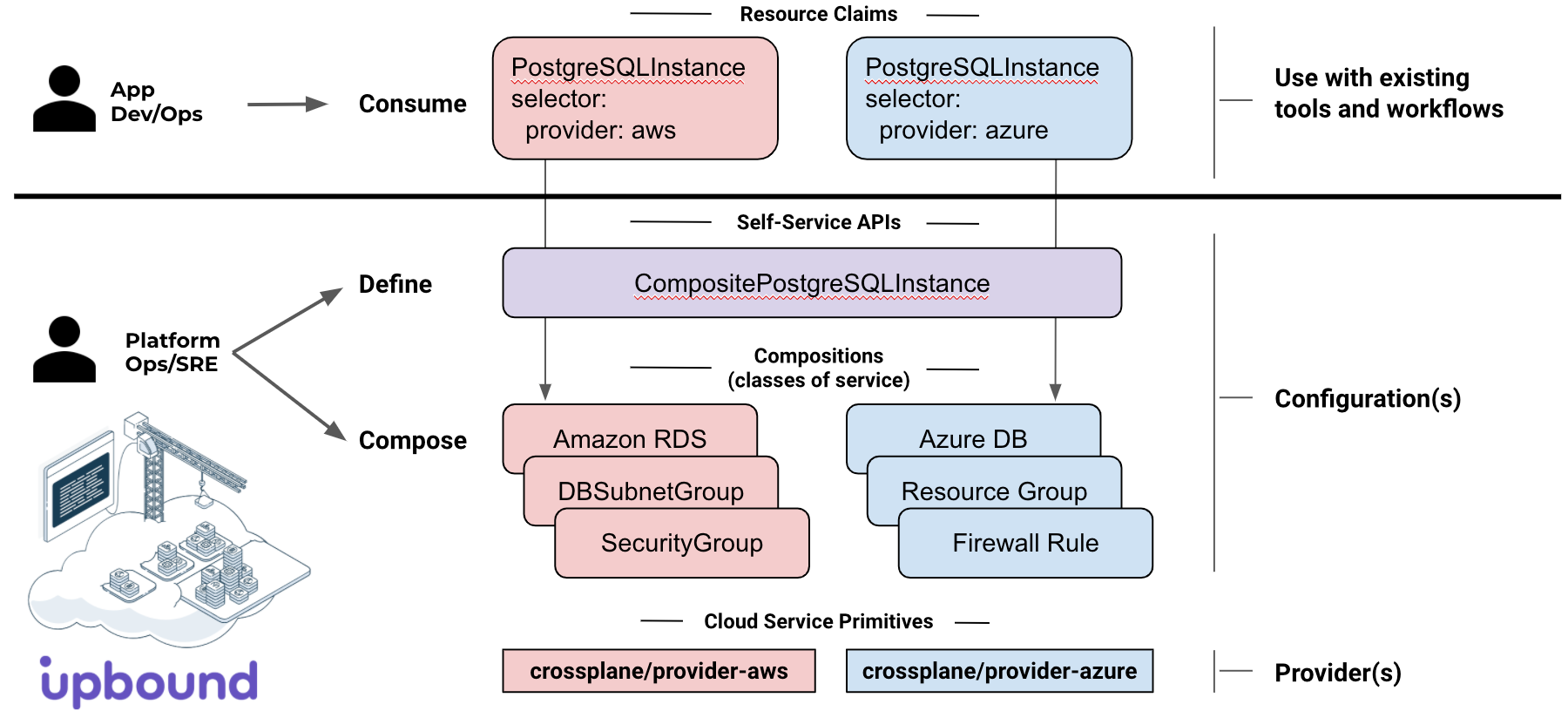
The Platform Configuration defines the self-service APIs and
classes-of-service for each API:
CompositeResourceDefinitions(XRDs) define the platform's self-service APIs - e.g.CompositePostgreSQLInstance.Compositionsoffer the classes-of-service supported for each self-service API - e.g.Standard,Performance,Replicated.
Crossplane Providers include the cloud service primitives (AWS, Azure, GCP,
Alibaba) used in a Composition.
Learn more about Composition in the Crossplane
Docs.
There are two ways to run Universal Crossplane:
- Hosted on Upbound Cloud
- Self-hosted on any Kubernetes cluster.
To provision the AWS Reference platform, you can pick the option that is best for you.
We'll go through each option in the next sections.
Hosted Control planes are run on Upbound's cloud infrastructure and provide a restricted
Kubernetes API endpoint that can be accessed via kubectl or CI/CD systems.
- Sign up for Upbound Cloud.
- When you first create an Upbound Account, you can create an Organization
- Create a
Control Planein Upbound Cloud (e.g. dev, staging, or prod). - Connect
kubectlto yourControl Planeinstance.- Click on your Control Plane
- Select the Connect Using CLI
- Paste the commands to configure your local
kubectlcontext - Test your connectivity by running
kubectl get pods -n upbound-system
The other option is installing UXP into a Kubernetes cluster you manage using up, which
is the official CLI for interacting with Upbound Cloud and Universal Crossplane (UXP).
There are multiple ways to install up, including Homebrew and Linux packages.
curl -sL https://cli.upbound.io | shEnsure that your kubectl context is pointing to the correct cluster:
kubectl config current-contextInstall UXP into the upbound-system namespace:
up uxp installValidate the install using the following command:
kubectl get all -n upbound-systemNow that your kubectl context is configured to connect to a UXP Control Plane, we can install this reference platform as a Crossplane package.
curl -sL https://raw.githubusercontent.com/crossplane/crossplane/master/install.sh | sh
cp kubectl-crossplane /usr/local/bin# Check the latest version available in https://cloud.upbound.io/registry/upbound/platform-ref-aws
PLATFORM_VERSION=v0.2.0
PLATFORM_CONFIG=registry.upbound.io/upbound/platform-ref-aws:${PLATFORM_VERSION}
kubectl crossplane install configuration ${PLATFORM_CONFIG}
kubectl get pkgA ProviderConfig is used to configure Cloud Provider API credentials. Multiple
ProviderConfigs can be created, each one pointing to a different credential.
The AWS provider expects a credential Secret in the named profile format:
[default]
aws_access_key_id = <your access key ID>
aws_secret_access_key = <your secret access key>This file can be crated manually or by using the aws CLI:
AWS_PROFILE=default && echo -e "[default]\naws_access_key_id = $(aws configure get aws_access_key_id --profile $AWS_PROFILE)\naws_secret_access_key = $(aws configure get aws_secret_access_key --profile $AWS_PROFILE)" > creds.confCreate the ProviderConfig and Secret using the credentials file:
kubectl create secret generic aws-creds -n upbound-system --from-file=key=./creds.conf
kubectl apply -f examples/aws-default-provider.yamlWe are now ready to provision resources.
The example network composition includes the creation of a VPC, Subnets, Route Tables and a Gateway:
kubectl apply -f examples/network.yamlVerify status:
kubectl get claim
kubectl get composite
kubectl get managed- Create a Team
team1. - Invite app team members and grant access to
Control PlanesandRepositories.
- Join your Upbound Cloud
Organization - Verify access to your team
Control Planesand Registries
- Browse the available self-service APIs (XRDs) Control Plane
- Provision a
CompositePostgreSQLInstanceusing the custom generated GUI for your PlatformConfiguration - View status / details in your
Control PlaneGUI console
- Connect
kubectlto aControl Planefrom the self-service GUI console.
kubectl apply -f examples/postgres-claim.yamlVerify status:
kubectl get claim
kubectl get composite
kubectl get managedDelete resources created through the Control Plane Configurations menu:
- From the
TeamsGUI using the ellipsis menu in the resource view. - Using
kubectl delete -n team1 <claim-name>.
Delete resources created using kubectl:
kubectl delete -f examples/postgres-claim.yaml
kubectl delete -f examples/network.yamlVerify all underlying resources have been cleanly deleted:
kubectl get managedkubectl delete configurations.pkg.crossplane.io platform-ref-aws
kubectl delete providers.pkg.crossplane.io provider-aws
kubectl delete providers.pkg.crossplane.io provider-helmrm /usr/local/bin/kubectl-crossplane*Cluster- provision a fully configured EKS cluster- definition.yaml
- composition.yaml includes (transitively):
EKSClusterNodeGroupIAMRoleIAMRolePolicyAttachmentOpenIDConnectProviderHelmReleasesfor Prometheus and other cluster services.
Network- fabric for aClusterto securely connect to Data Services and the Internet.- definition.yaml
- composition.yaml includes:
VPCSubnetInternetGatewayRouteTableSecurityGroup
PostgreSQLInstance- provision a PostgreSQL RDS instance that securely connects to aCluster- definition.yaml
- composition.yaml includes:
RDSInstanceDBSubnetGroup
Create a Repository called platform-ref-aws in your Upbound Cloud Organization:
Set these to match your settings:
UPBOUND_ORG=acme
UPBOUND_ACCOUNT_EMAIL=me@acme.io
REPO=platform-ref-aws
VERSION_TAG=v0.2.0
REGISTRY=registry.upbound.io
PLATFORM_CONFIG=${REGISTRY:+$REGISTRY/}${UPBOUND_ORG}/${REPO}:${VERSION_TAG}Clone the GitHub repo.
git clone https://github.com/upbound/platform-ref-aws.git
cd platform-ref-awsLogin to your container registry.
docker login ${REGISTRY} -u ${UPBOUND_ACCOUNT_EMAIL}Build package.
up xpkg build --name package.xpkg --ignore ".github/workflows/*,examples/*,hack/*" Push package to registry.
up xpkg push ${PLATFORM_CONFIG} -f package.xpkgInstall package into an Upbound Control Plane instance.
kubectl crossplane install configuration ${PLATFORM_CONFIG}The AWS cloud service primitives that can be used in a Composition today are
listed in the Crossplane AWS Provider
Docs.
To learn more see Configuration Packages.
If you're interested in building your own reference platform for your company, we'd love to hear from you and chat. You can setup some time with us at info@upbound.io.
For Crossplane questions, drop by slack.crossplane.io, and say hi!