- Include a vpc to enable future growth and scale
- Include private and public subnet - Public for Loadbalancer, Private for Instances
- Security Group to allow only minial ports
- Use latest AWS AMI
- Auto Scaling Group requirements: 2 separate volumes: 1- /, 2- /var/log, 3- Include a webserver of choice
- Design webservers to be logged in without root key
- Set Alarms to show if application is facing any issue
- Not to use any tertiaty Configuration Management Tool
- Automatically Add and Remove Nodes based on load metrics
- Manage growth and storage of logs
-
Place your AWS access key id and secret access key in a file named credentials housed in a folder named .aws. .aws should be placed in your home directory ideally at
/home/<user-name>/.
The syntax of credentials should be as follows:
[default]
aws_access_key_id=xxxxx
aws_secret_access_key=xxxxx -
Installation in Linux:
wget https://releases.hashicorp.com/terraform/0.14.0/terraform_0.14.0_darwin_amd64.zip
unzip ./ terraform_0.12.2_linux_amd64.zip –d /usr/local/bin -
Testing Installation:
terraform -v
- Change Directory to the Directory housing the terraform scirpt
- To Initialize:
terraform init
- To Deploy:
terraform apply -auto-approve
- To Destroy:
terraform destroy -auto-approve
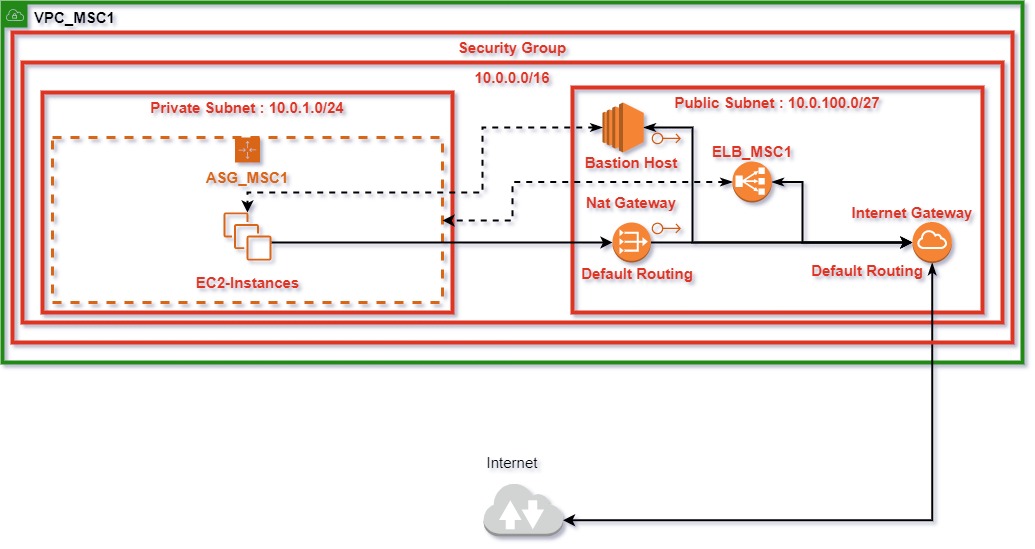
- VPC: To serve the entire Infrastructure
- Internet Gateway: To provide External Connectivity form VPC
- Nat Gateway: To provide Natted Connectivity to Private Instances
- Public Subnet: To serve Elastic LoadBalancer and EC2 Bastion Host
- Private Subnet: To serve private Instances
- Routing Table for Internet Gateway: To provide default route for Internet Gateway
- Routing Table for Nat Gateway: To provide default route for NAT Gateway
- Secutiry Group: To grant and restrict access to Instances
- Launch Configuration: To provide template for each EC2 spun up in Auto Scaling Group
- Auto Scaling Group: Provide Dynamic Host Allocation
- Auto Scaling Policy: To Provide Scale In/Out Policy for Auto Scaling Group
- Auto Scaling Notification: To trigger Topic in context to Auto Scaling Group
- SNS Topic - To provide notifications from Auto Scaling Notification
- Elastic LoadBalancer: To Serve the Auto Scaling Group
- EC2 Instance: To Serve as a Bastion Host to connect to Instances in Private Subnet,and the Instances in the Auto Scaling Group
- AWS Easltic IP: To serve the NAT Gateway and Bastion Host
- Elastic Block Storage: To Serve the Auto Scaling Group Instances and Bastion Host
The vpc contains two subnets, public to serve LoadBalancer and Bastion Host, and the private subnet to serve the instances of autoscaling group. The Security Group provides access to only icmp, port 80, port 22 essential for Connectivity, Hosting and manual health checks, 443 and 8080 are added in to provide for SSL Termination and replacement of webserver respectively.
The launch configuration contains the latest AWS HVM AMI for Amazon Linux for US-East-1(Virjinia). It also contains two separate ebs volumes, defined at appropriate capacities, one to be used for root volume, and the other to be used for '/var/log/'. The volume for /var/log is made to be persistent, which ensures retrieval of essential log data even if an instance is scrapped. The more important aspect of the Launch Configuration is that it provides user data script, which does a certain number of tasks:
- Installs, Starts and Enables Apache to run on boot
- Fetches the secondary volume, formats it as ext4(to enable journaling) and mounts it to /var/log, there by making the data persistent
- Enables Password Authentication, Root Login, and sets the default Password
PS - The User Data Script can be used as base64 encoded, plain text is used here to accertain the Logic
The Auto Scaling Group utilizes the Launch Configuration to deploy the instances as and when required (determined by the auto scaling policy)
The Auto Scaling Notification utilizes the sns topic to send across notifications as and when certain conditions are met, the conditions being self-explanatory
The Elastic Load Balancer acts as the single point of access to the webserver running off from the instances in the Auto Scaling Group. To facilitate that, the Elastic Load Balancer is associated with both the public and the private subnet. Listeners are set on the destination and source port of 80, the port served by Apache, by default.
The Bastion Host, acts as our point of entry into the private subnet serving the EC2 Instances in the Auto Scaling Group. To faciliate that, the Bastion Host is provided with an Easltic IP
PS: To provide Encryption at Rest SSL Termination would have been required at ELB, since the arn of the Certificate is tightly coupled with the Infrastructure, I have chosen not to use it here
Two Elastic IPs are used in the entire Infrastructure:
- Nat Gateway
- Bastion Host
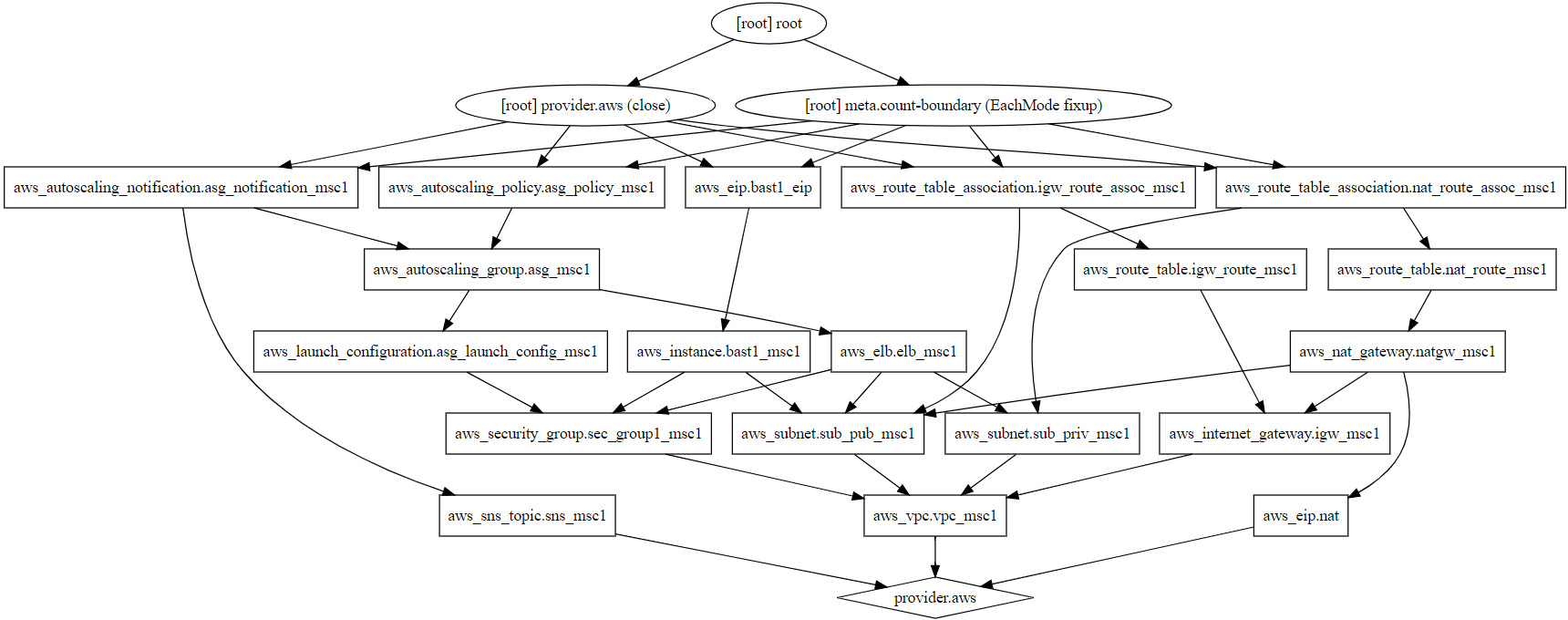
- Dot Graph showcases the build procedure followed by Terraform
- Author: Arnab Seal - arnabseal16@gmail.com