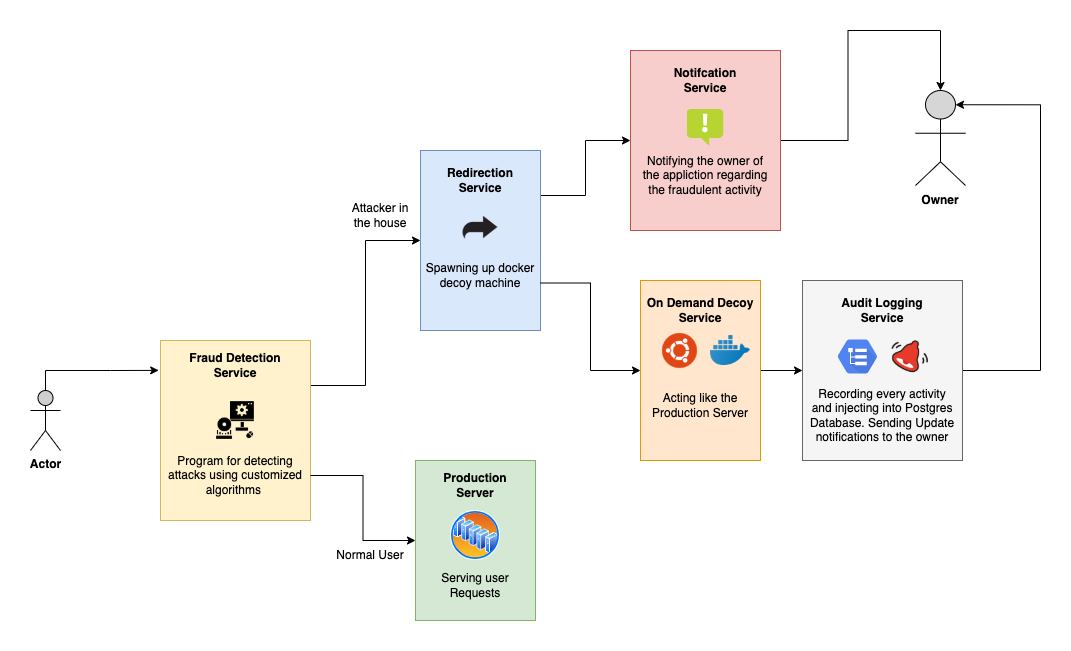
Spawning up Decoy Server in case of any fraudulent activity and directing the intruder towards the decoy. Auto Killing the decoy if it is idle for too long.
Here Decoy is Dockerised Golang API and the attack that is considered is Password Spray Attack
- Docker Hub Image - https://hub.docker.com/repository/docker/ankithans/securex_app
- Set up
.envfile according to the.env.samplefile - Email and Password should be a google account while turning on low secure apps
- Enter
go run server.goto run the golang server - Run
go run intruder/password_spray.goto start password spray simulation
Currently the detection of Password Spray Attack is done using its own properties. Attackers attempt the same password on many accounts before moving on to another and repeating the process
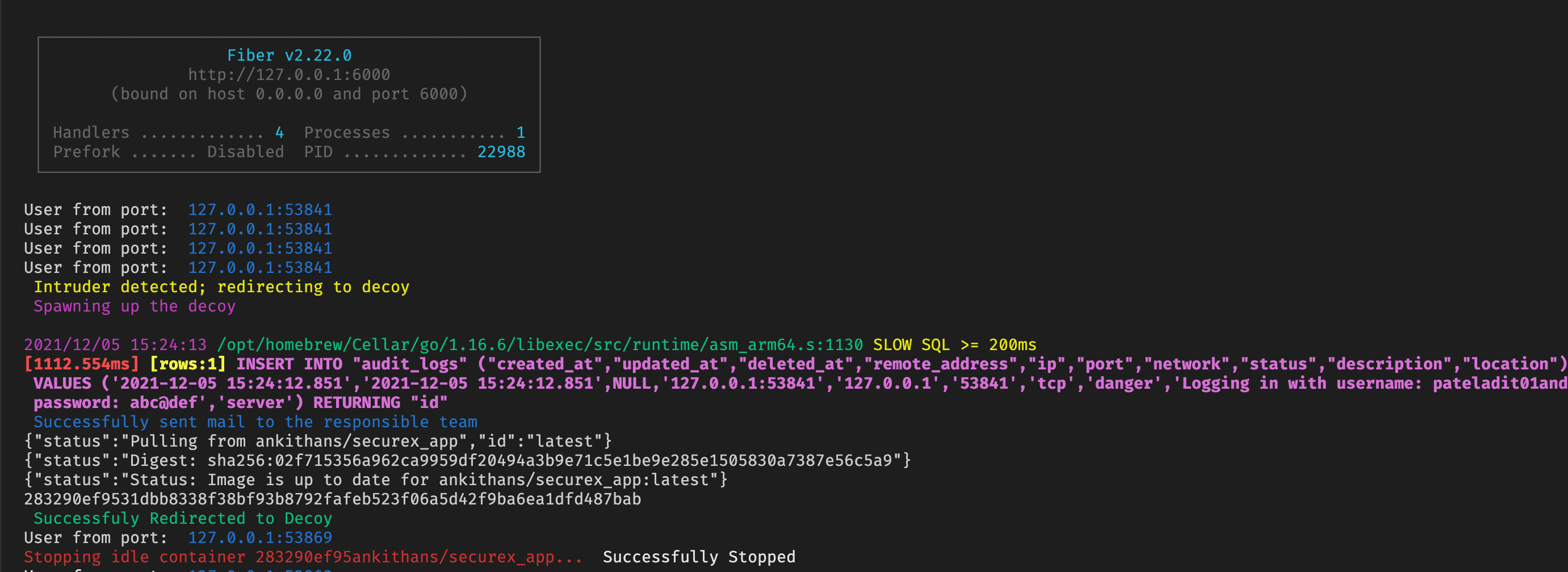
- Counting number of logins from the same Port which are done simultaneously
- If count is greater than a threshold then declare it as a Password Spray attack
In case of Fraud
- Spawning up of Decoy Machine
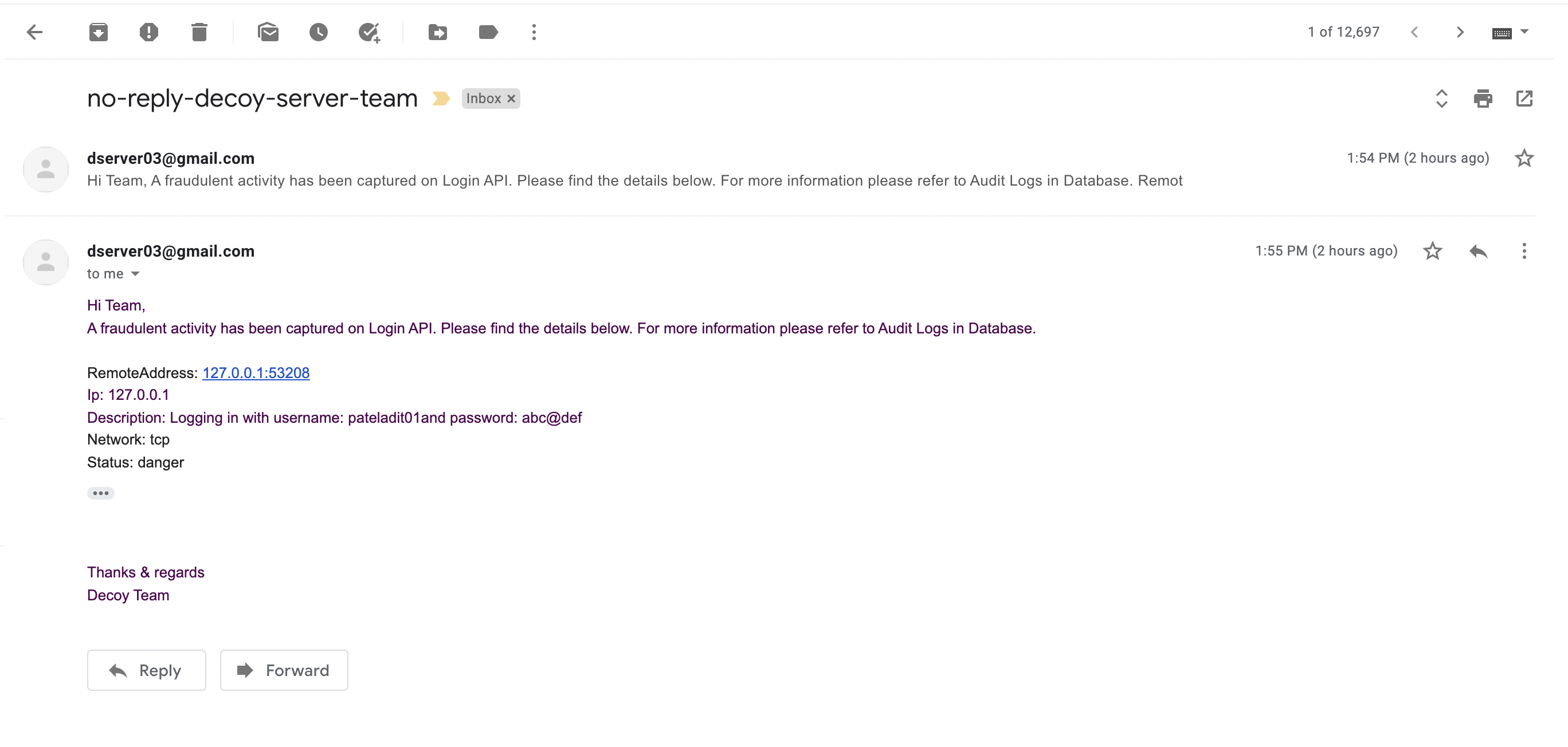
- Notifying on mailing list
- Redirecting the API call to Decoy Server
- Docker Container as a Decoy
- Fake Data and Configuration while ensuring similar experience as original server to the Intruder
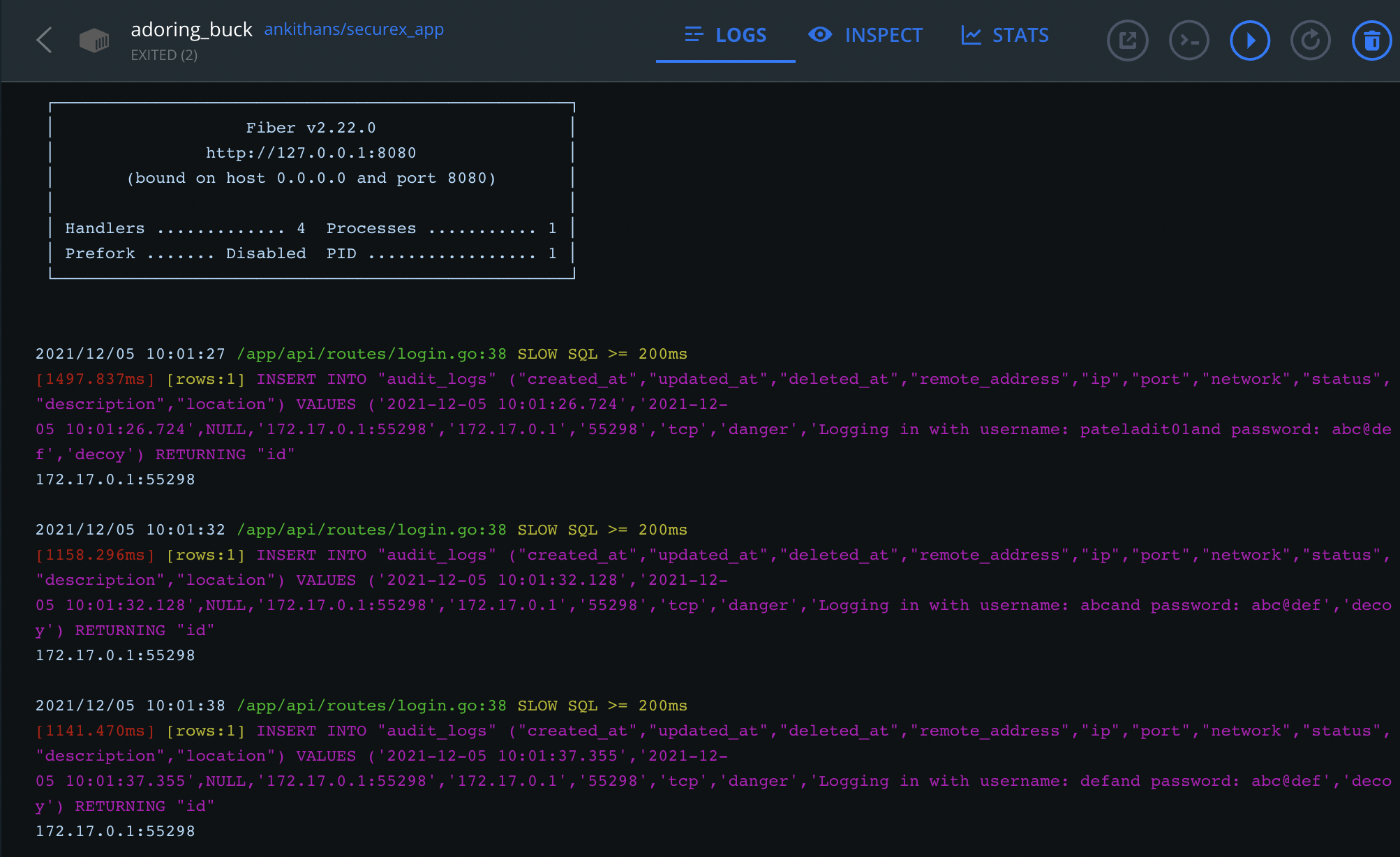
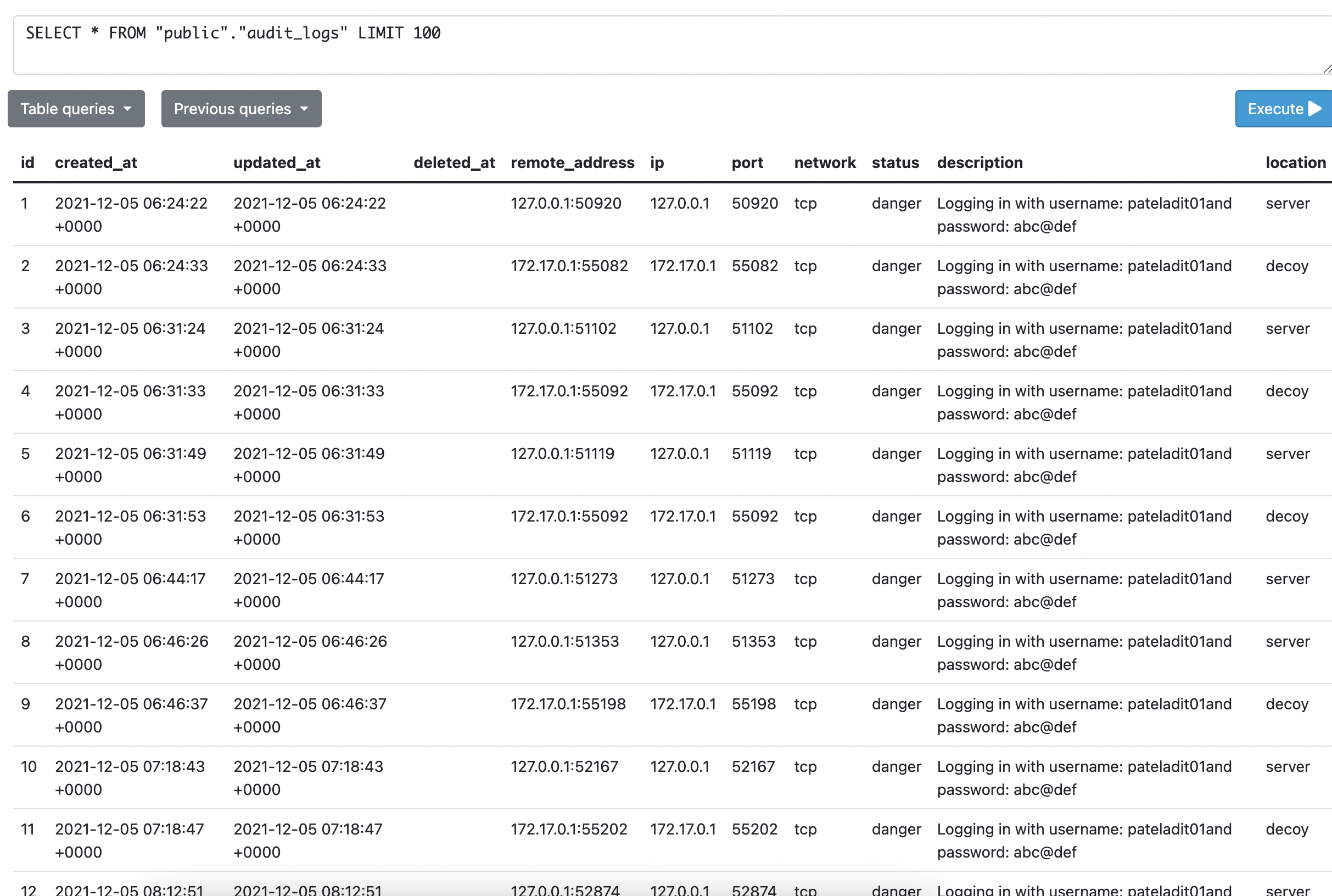
- All the Activities in Decoy are Recorded and Monitored as Audit Logs
- Auto Kill the Decoy if it is idle for more than a minute (using concurrency)
- Notifying the teams that are responsible for taking action against the fraudulent activity
- Using SMTP Email Services
- Recording all interactions of Intruder with Decoy
- Storing IP, Port, Network Type, Location, Description and status of the Activity
- Useful to Recreate the whole Process if required
Golang, Docker, SMTP, PostgreSQL, Scripting
Create a golang API for loginSystem to detect the port scan attack or password spray attackDocker container with the same Golang APISpawn the Docker container programmatically on a specific portRedirect the intruder to server created by docker containerShut down container if it is idleAudit Logging service in the container APINotification service in the container APIImprove dataset for logins
Made with love by Ankit Hans