Elliptic curve analogue ElGamal encryption scheme requires encoding of the plain message onto elliptic curve coordinate using Koblitz encoding technique before encryption operation. The paper proposes a medical image encryption scheme using improved ElGamal encryption technique. A new finding has been made in the proposed method where separate calculations for encoding plain message to elliptic curve coordinate are removed. The algorithm in the improved version of ElGamal encryption scheme is designed to encrypt medical image where data expansion issue is resolved and execution speed is enhanced. The strength of the proposed method is insured through various statistical and security analyses and comparison with other existing encryption schemes.
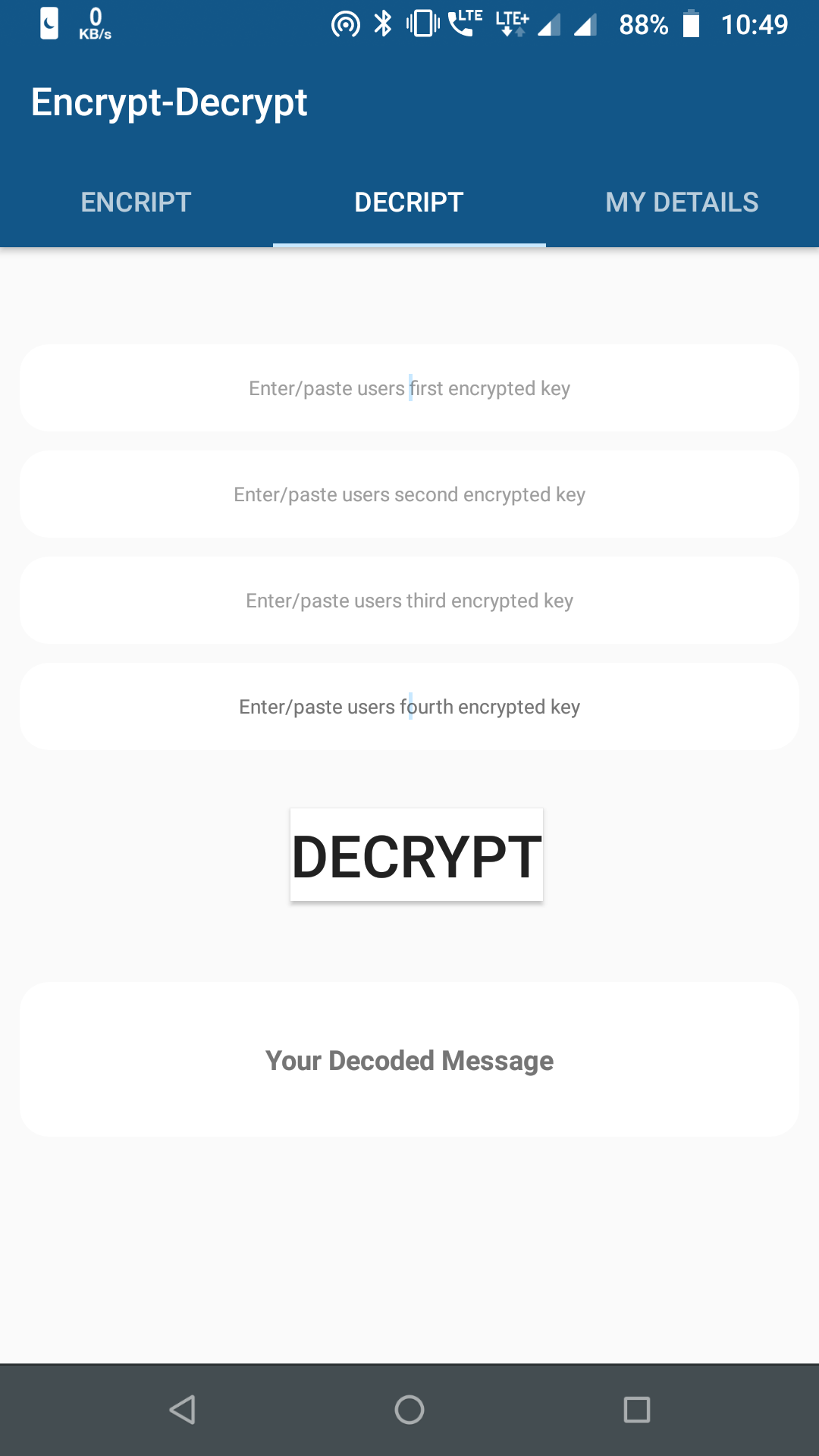
An android application is made to encrypt and decrypt texts and numbers using the Elliptic curve analogue ElGamal encryption scheme. There are more applications of it as mentioned in paper and so the further works will also be done on image and audio encryption.
Let Ep be an elliptic curve equation over a finite field
Ep : y2 = x3 + ax + b mod p (1)
where,
a and b are constant with 4a3 + 27b2 != 0.
p: prime number.
Coordinates (x, y) ∈ Ep follows certain additive abelian properties.
A point P(x, y) on addition with a point at infinity ∞ is the point itself.
P + ∞ = ∞ + P = P∀P ∈ Ep (2)
Negative of a point P = (x, y) is given as −P = (x, −y).
Two points P(x1, y1) and Q(x2, y2) ∈ Ep, adds up to produce a third point R(x3, y3) ∈ Ep.
Mathematically the coordinate of R is computed as:
If x1 , x2,
x3 = {λ2 − x1 − x2} mod p (3)
y3 = {λ(x1 − x3) − y1} mod p (4)
where,
λ =y2 − y1 / x2 − x1 mod p (5)
A point P(x1, y1) ∈ Ep upon addition to itself, generates a point R(x3, y3) ∈ Ep.
If x1 == x2 and y1 == y2 != 0,
x3 = {λ2 − 2x1} mod p (6)
y3 = {λ(x1 − x3) − y1} mod p (7)
where,
λ =3x12+ a/2y1 mod p (8)
If x1 = x2 but y1 , y2 in point addition case, the two point is said to meet at infinity.
P + Q = ∞ (9)
If the y coordinate is 0 in point doubling case, the point doubling operation is said to meet at
infinity.
P + P = ∞ (10)
Point subtraction is computed as point addition after negating the y2 coordinate.
P(x1, y1) − Q(x2, y2) = P(x1, y1) + Q(x2, −y2) (11)
Multiple times a point is computed as repeated addition
k × P = P + P + ...k times. (12)
Point multiplication operation can be reduced by a combination of point addition and point doubling. To compute k × P with the reduced operation, the following steps are performed.
- Begin a = k, B = ∞,C = P.
- If a is even, a = a/2, B = B and C = 2C.
- If a is odd, a = a − 1, B = B + C and C = C.
- If a , 0, go back to Step 2.
After completion B = k × P.
The strength of Elliptic curve analogue ElGamal encryption scheme (ECAEES) depends on
Elliptic curve discrete logarithmic problem (ECDLP) [19] which is an exponentially difficult
problem with raise in key size. Performing encryption and decryption operation using ECAEES
over a finite field requires computation for encoding plain data to the coordinate of the elliptic
curve.
Pc = {kG, (Pm + kPb)} (13)
Pc = {kG, (xc, yc)} (14)
where,
Pc: Cipher text.
G: Generator.
k: Random integer between 1(one) and n − 1 where n is the cyclic order[24] of an elliptic
curve over finite field.
Pm: Plain message represented as elliptic curve coordinate using Koblitz encoding technique.
Pb: Public key of the receiver.
(xc, yc): One of the point in elliptic curve after point addition of Pm and kPb.
All the points {kG, Pm, kPb, (xc, yc)} ∈ Ep
Pm = (xc, yc) − nbkG (15)
where,
nb: Receiver’s private key.
Given an elliptic curve over a finite field Ep : y2 = x3 + ax + b mod p. Represent the plain
message as an integer m where 0 ≤ m < p/1000 − 1.
For 0 ≤ j < 1000, compute xj = 1000m + j
and sj = xj3 + axj + b mod p. If sj(</supp−1)/2 ≡ 1 mod p, then sj is a square mod p. For p ≡ 3 mod 4, yj ≡ sj ^ (p+1)/4 mod p.
The message m is embedded as Pm = (xj, yj). m can be recovered by a division operation on x coordinate of Pm and taking the floor value [19]. m = [bxj/1000c].