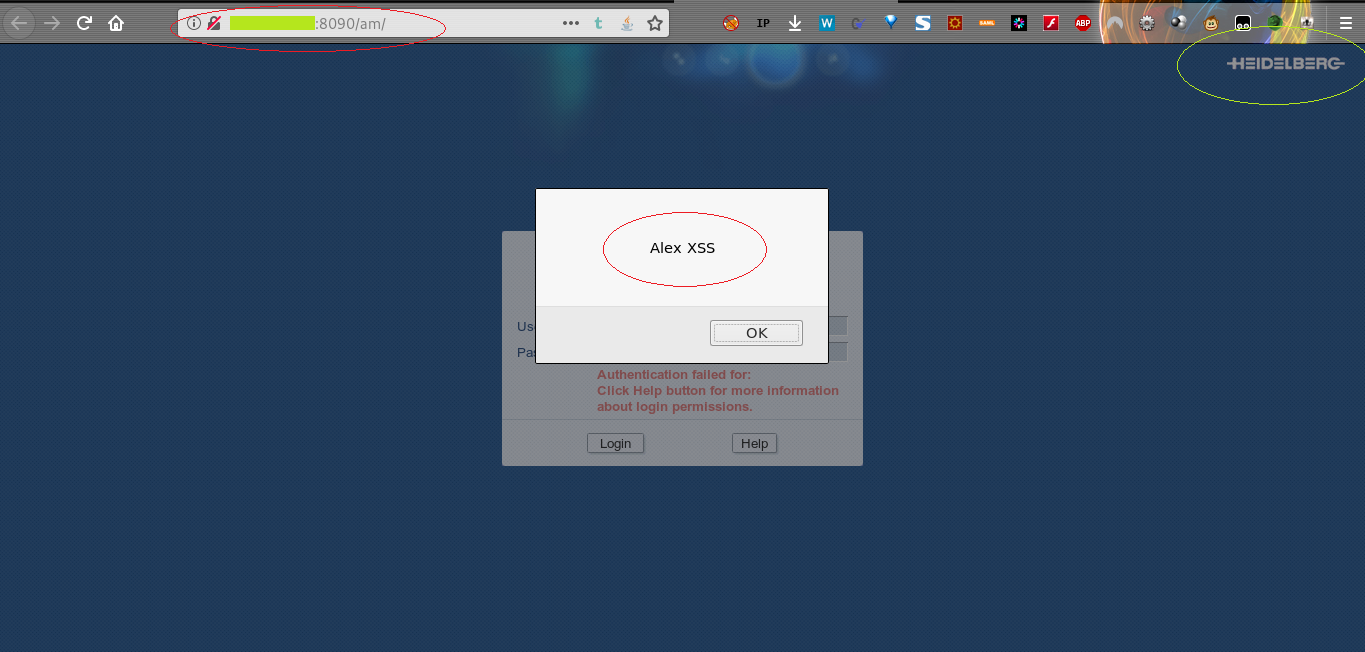
The user supplied input containing JavaScript is echoed back in JavaScript code in an HTML response via the "TextField" parameter.
Exploit-DB publication at https://www.exploit-db.com/exploits/46804
PacketStorm publication at https://packetstormsecurity.com/files/152727/Prinect-Archive-System-2015-Release-2.6-Cross-Site-Scripting.html
CVE: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-10685
================
2019-02-04: Discovered
2019-02-25: Retest PRO environment
2019-03-25: Retest on researcher's ecosystem
2019-04-02: Vendor notification
2019-04-03: Vendor feedback received
2019-04-08: Reminder sent
2019-04-08: 2nd reminder sent
2019-04-11: Internal communication
2019-04-26: No more feedback received from the vendor
2019-04-30: New issues found
2019-05-06: Public Disclosure
Alex Hernandez aka (@_alt3kx_)
My current exploit list @exploit-db:
https://www.exploit-db.com/author/?a=1074
https://www.exploit-db.com/author/?a=9576
CVE-2019-10685 with sexy screens here: https://medium.com/@alt3kx