Adhrit is an open source Android APK reversing and analysis tool that can help security researchers and CTF enthusiasts alike. The tool is an effort to cut down on the amount of time spent on reversing and basic reconnaissance of Android applications. The project is still under progress and will continually incorporate features with time. Feel free to report the issues. Feature requests and suggestions are always welcome!
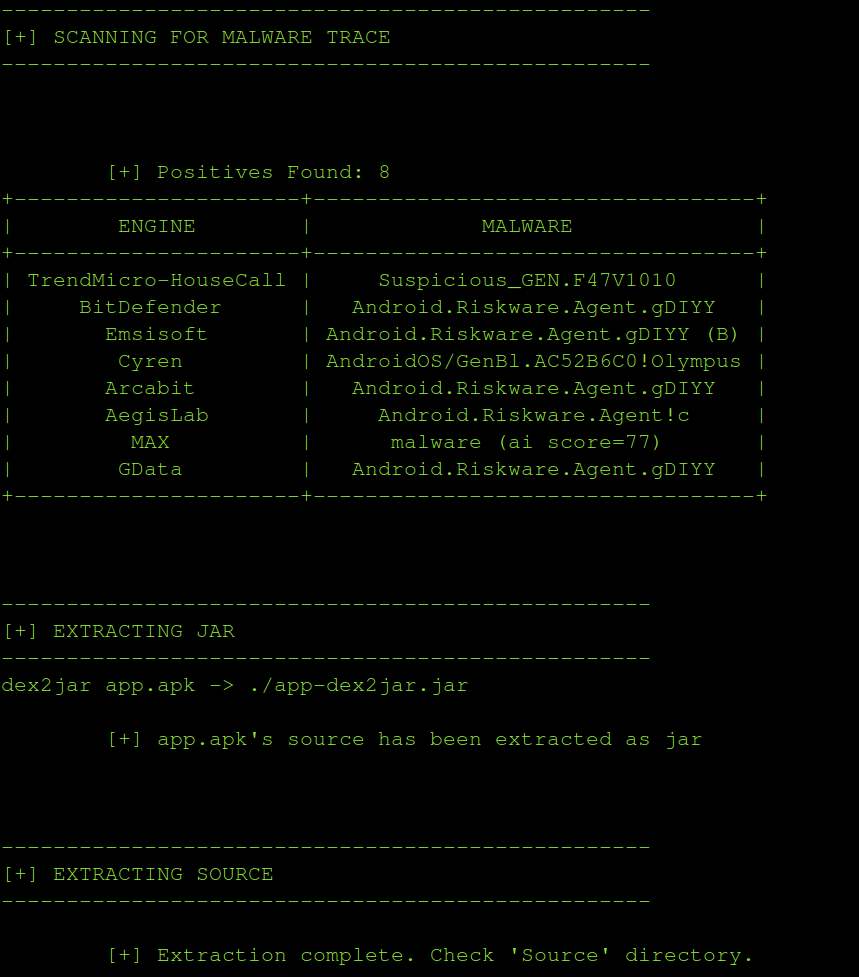
- Extracts the apk contents.
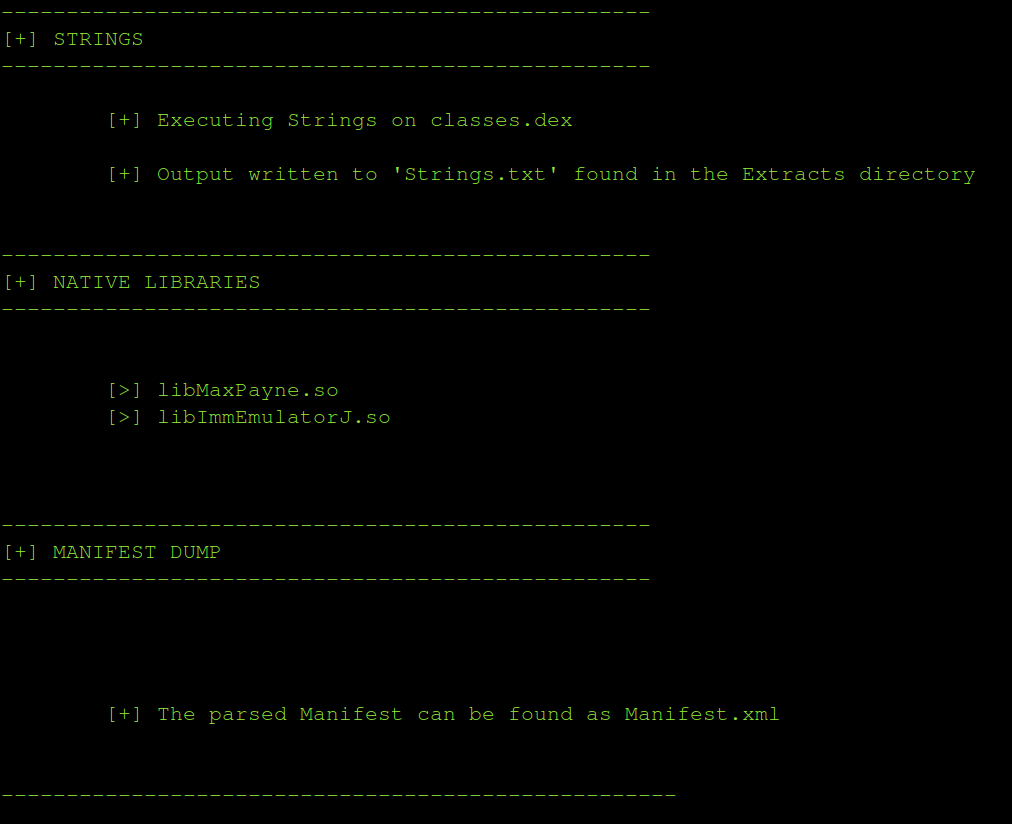
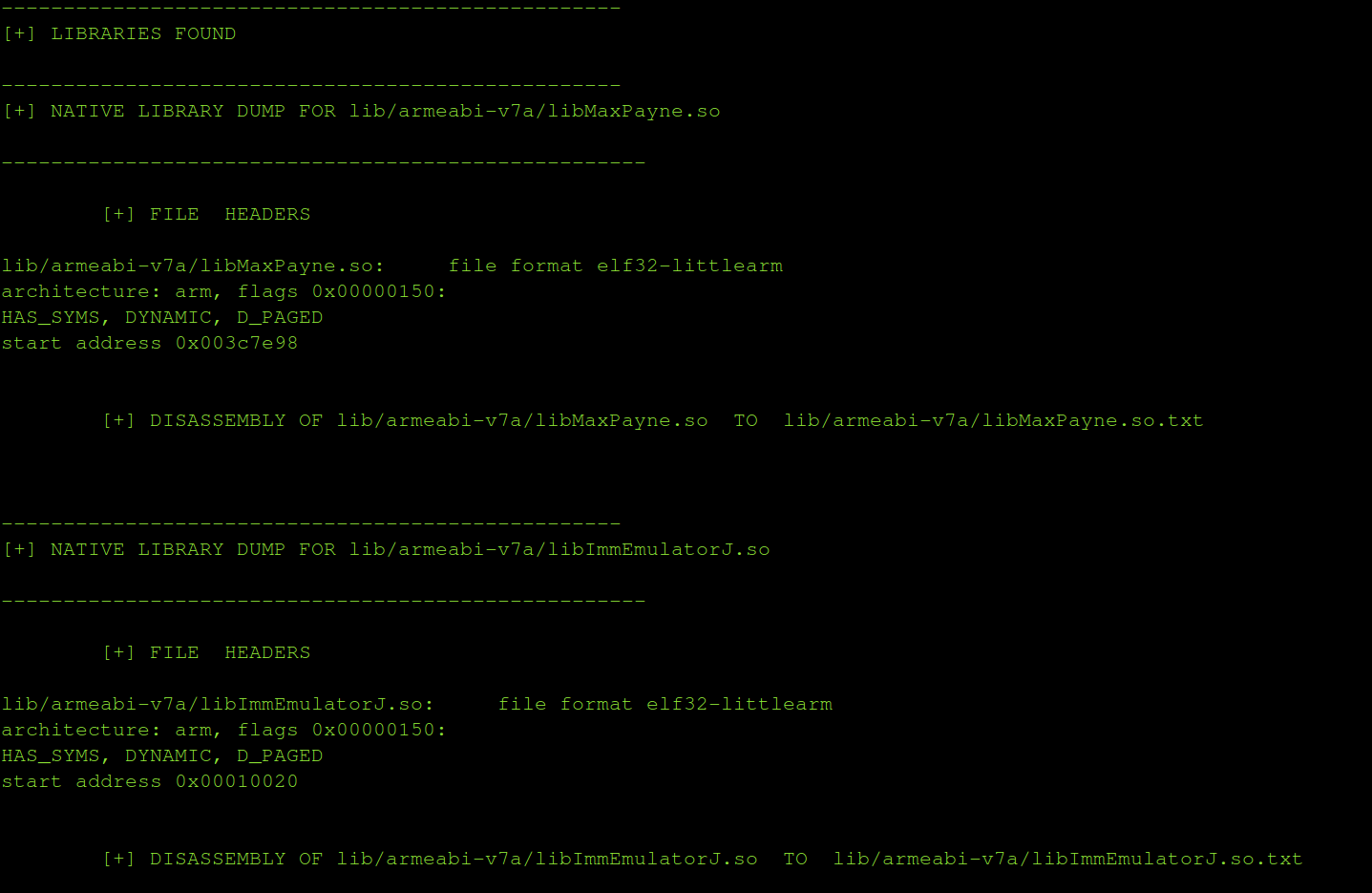
- Disassembles native libraries
- Extracts jar out of dex.
- Extracts source code in Java.
- Extracts source code in Smali.
- Recompiles smali into APK
- Signs the APK
- Checks for virtual apps/droppers
- Checks for bytecode injection points and write it to a file.
- Analyzes permissions used by the application.
- Dumps the Manifest.
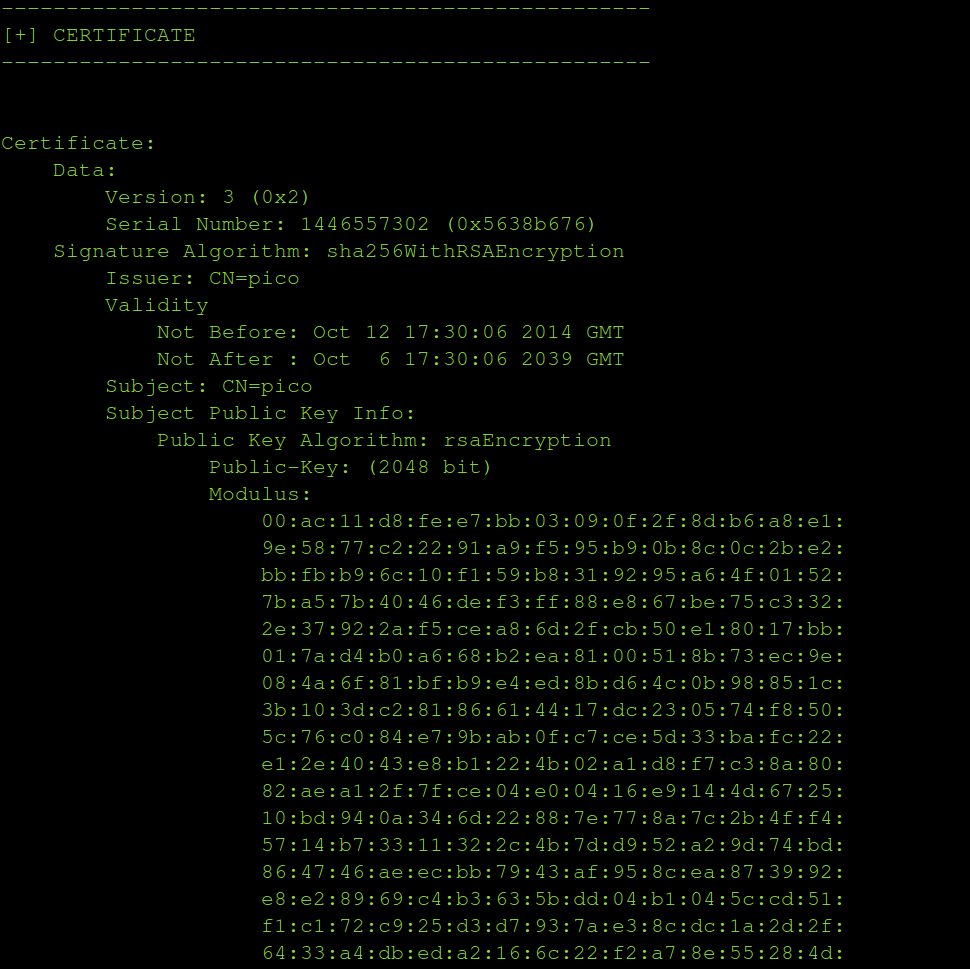
- Dumps the certificate details.
- Checks for malware footprints in the VirusTotal database.
- Linux or MAC
- Java JDK
- Dowload the zip or clone the package and extract the tool (
git clone https://github.com/abhi-r3v0/Adhrit.git). - Open
configand input your VirusTotal API key without any quotes. (Click here to know how to obtain your VT API key) - Open a terminal and cd into the directory.
- Run
python installer.pyfor installing the necessary tools.
- Place the application (apk file) in the tool directory.
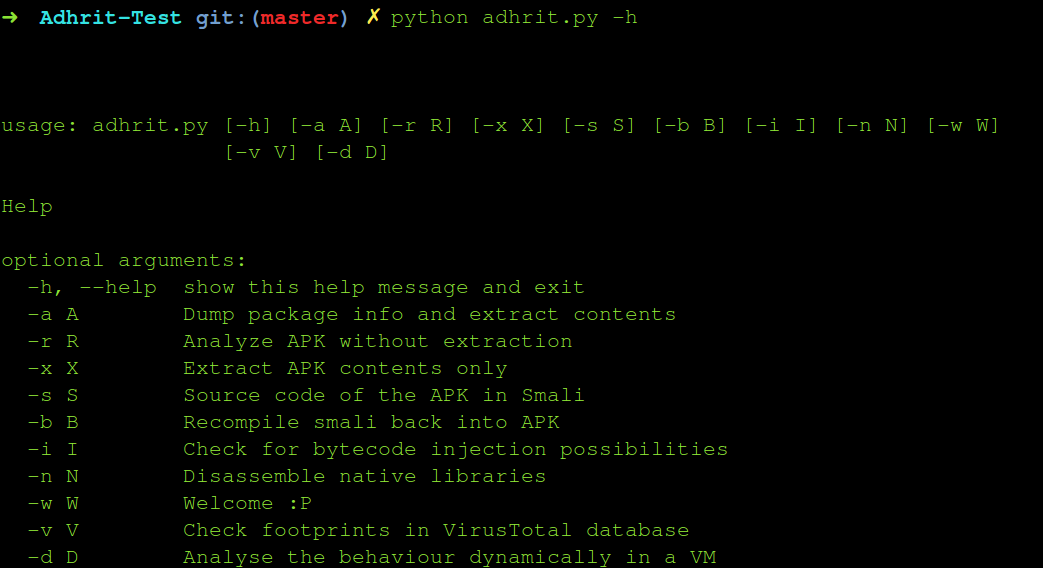
- Use
python adhrit.py -hfor usage help.
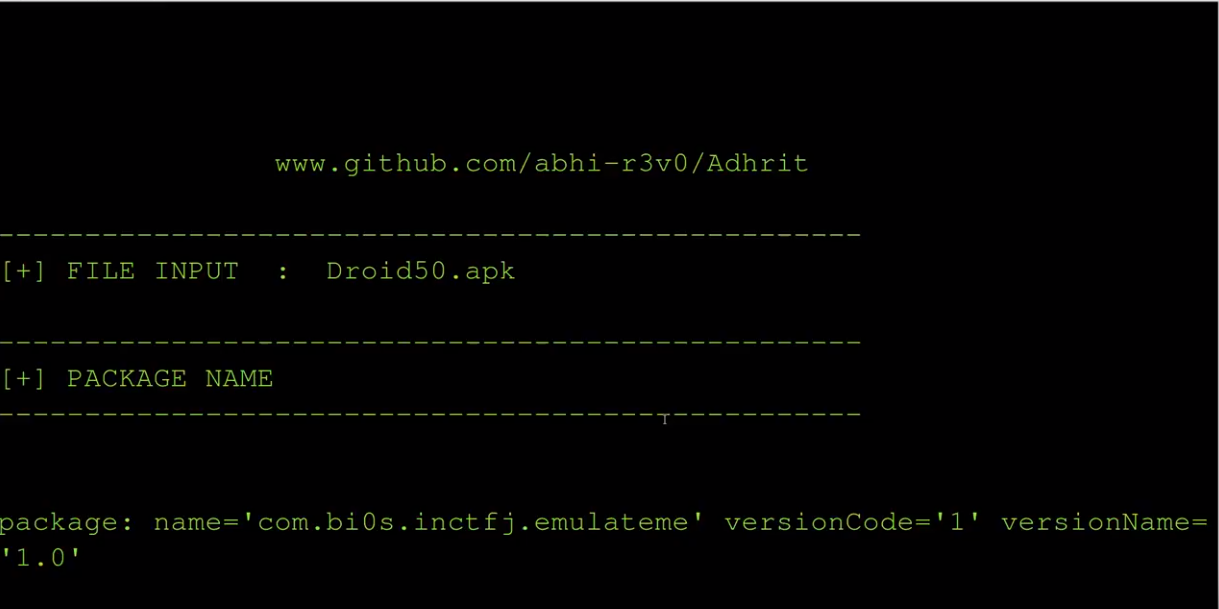
Example: python adhrit.py -a my_app.apk
- Abhishek J M (jmabhishek4@gmail.com, @abhi_r3v0)
- Akhil Mahendra (akhilmahendra7991@gmail.com, @Akhil_Mahendra)
- P S Narayanan (thepsnarayanan@gmail.com, @0xP5N_)
- Heeraj Nair (heeraj123@gmail.com, @heerajnair)
- Loyd Jayme (loydjayme1996@gmail.com, @loydjayme25)
- Neonix
- Troopers
- Seclist
- DedSec
- Howucan.gr
- HackerTor
- tuicool
- @androidtools on Twitter
- pcbbc
- Ethical Hacking Consultants
- Anonymoushacker
- Pax0r
- KitPloit
- NeOnSec
- ISEC
- Prodefence
- appscan.io
- Weixin
- blackhatsecdevteam
- 360doc
- Hackers Online Club
- Altervista
- Xaunwulab
- Prodefense
- Digital Munition
- Xenicom
- Filenames with two '.' may give an error. Please rename the apk in such cases.
For example, if your file name is
my.app.apk, rename it tomyapp.apk