GoCheck a blazingly fast™ alternative to Matterpreter's DefenderCheck which identifies the exact bytes that Windows Defender AV by feeding byte slices to MpCmdRun.exe
I also wrote a blog post showcasing this project: Identifying Malicious Bytes in Malware
$ gocheck check --help
Usage:
gocheck check [flags]
Flags:
-a, --amsi Use AMSI to scan a file
-d, --defender Use Windows Defender to scan a binary
-f, --file string Binary to check
-h, --help help for checkThe check cobra flag is only used for ease of extensibility in the event that I finally decide to integrate Ghidra's Headless Analyzer with gocheck. For ease of use, you can actually completely omit the check flag and directly pass the file to gocheck as an argument.
$ gocheck <file> /optional:argsThis may be changed in the future.
gocheck [path_to_binary] /optional: --defendergocheck [path_to_file] /optional: --amsigocheck [path_to_file] /optional: --defender --amsiYou can install gocheck from go install
go install github.com/gatariee/gocheck@latestAlternatively, you can download the precompiled binaries from the releases or build it yourself.
git clone https://github.com/gatariee/gocheck
make [ windows / win64 / win32 ]You can use gocheck to identify bad bytes, and then pass the identified offset of bad bytes into ghidra (or, any other decompiler) to hopefully decompile the binary and locate the bad bytes in a function.
I'll be using ghidra to decompile the binary since I'm more familiar with it. (and, it's free)
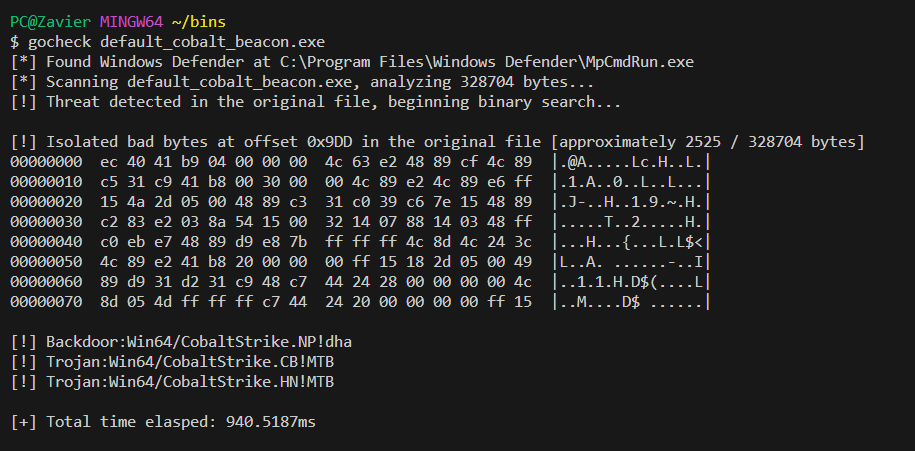
$ gocheck <file> /optional:args- Identified bad bytes at offset 0x9DD (from start of binary)
- 16 bytes before & after the bad bytes are also printed for context, but doesn't help much in this case.
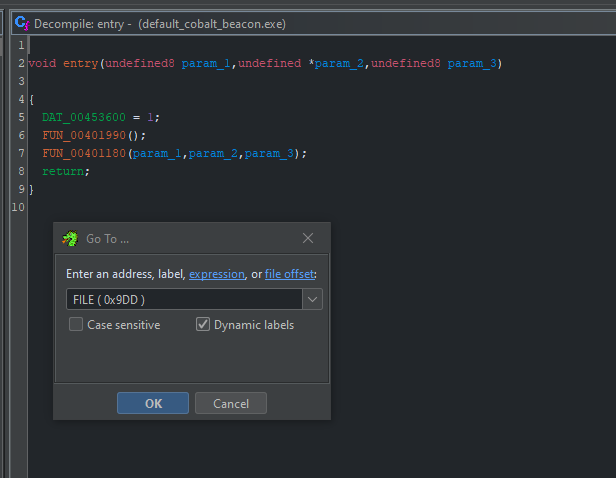
- Navigation -> Go To... -> FILE ( 0x9DD )
- Alternatively,
Galso brings up the same dialog.
- Alternatively,
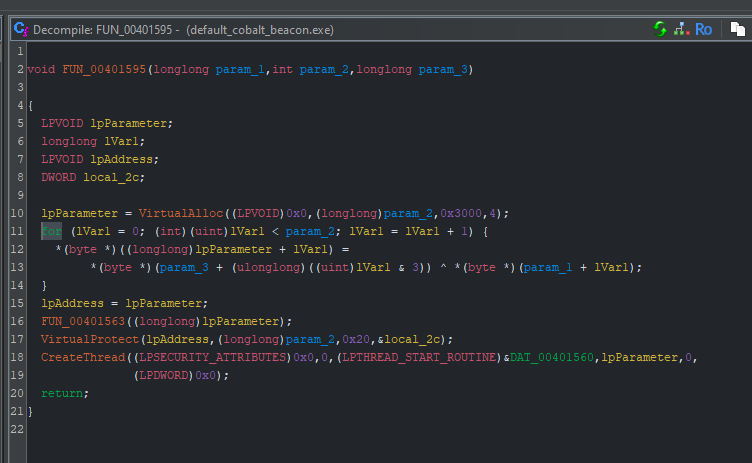
- The bad bytes are identified after a call to
VirtualAllocand before a call toVirtualProtectin this case, which should be easy to find in the artifact kit.
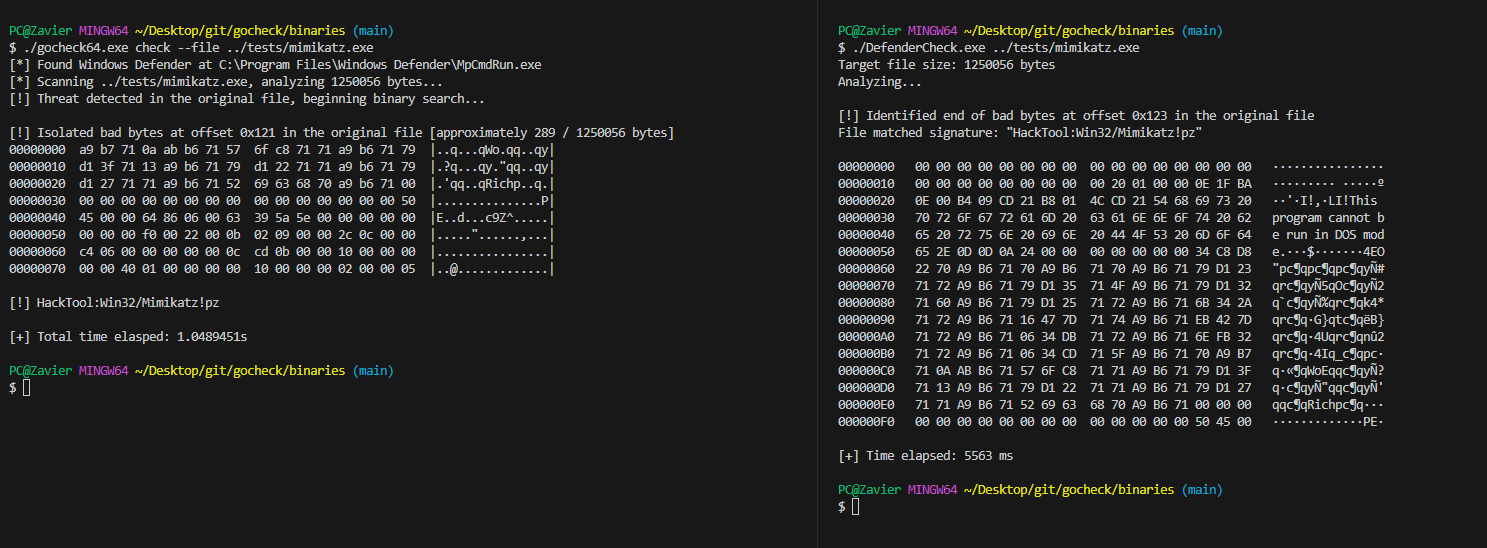
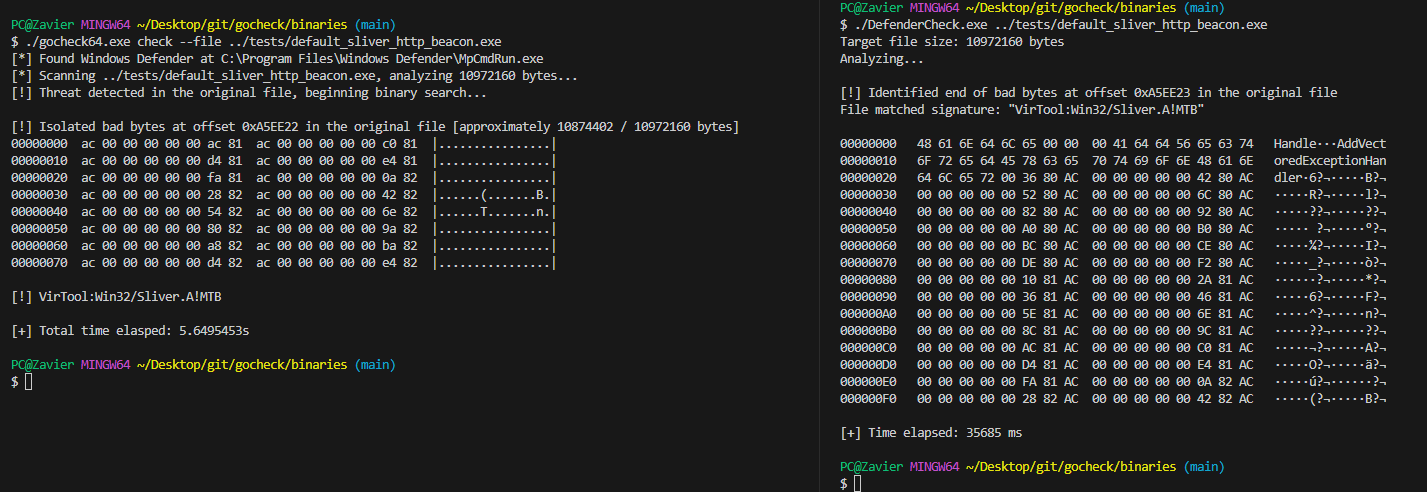
⚠️ I am not an expert in benchmarking, and the following benchmarks are conducted on a single machine, and the results may vary on different machines. The benchmarks are conducted on a single machine to provide a rough estimate of the performance difference betweengocheckandDefenderCheck.
The objective of gocheck was to implement a faster alternative to Matterpreter's DefenderCheck as I realized that it was painfully slow when scanning large binaries, which can be quite a headache for extremely large binaries such as those written in Golang.
The following benchmarks were conducted on the following specifications:
- OS: Windows 10 Pro
- CPU: AMD Ryzen™ 5 3600X
- RAM: 32 GB DDR4 3200 MHz
The I/O operations were conducted on a Samsung 870 EVO SATA 2.5" SSD (1 TB), 560/530 MB/s R/W, the temporary binaries are stored in the C:\Temp directory.
| Tool | Time |
|---|---|
| GoCheck | 1.05s |
| DefenderCheck | 5.56s |
| Tool | Time |
|---|---|
| GoCheck | 5.65s |
| DefenderCheck | 35.69s |
- Originally implemented by Matterpreter in DefenderCheck
- https://github.com/rasta-mouse/ThreatCheck