🔐 🔪 Encrypted texts and perform Brute Force. Through Hash MD5, SHA1, SHA256, SHA512.. In all operating systems Gnu/Linux 🐧, Windows, MacOs 🍎
Font img: https://www.gta.ufrj.br
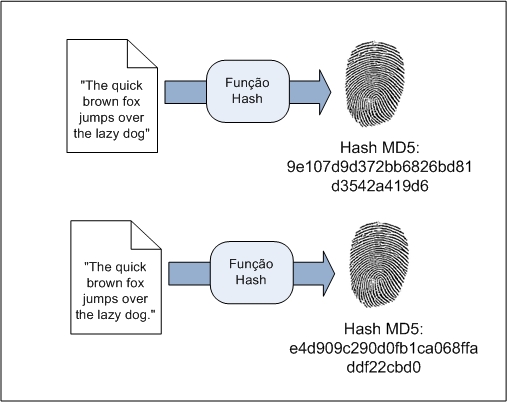
A hash function is an algorithm that maps variable-length data to fixed-length data. The values returned by a hash function are called hash values, hash codes, hash sums, checksums, or simply hashes.
MD5 is a 128-bit unidirectional cryptographic scatter function developed by RSA Data Security, Inc., described in RFC 1321, and widely used by point-to-point protocol software for file and log integrity checking.
Font img: https://upload.wikimedia.org
SHA1 implements a keyness hashed algorithm that takes a message up to 264 bits and produces a 160-bit message summary and is used for message integrity checking. It is based on the design principles of the MD4 and MD5 hash algorithms (Memory Digest 4 and 5).
Pseudo-collision attacks against up to 46 rounds of SHA-256. SHA-2 is a set of cryptographic hash functions designed by the NSA. SHA stands for secure hash algorithm.
Font img: https://upload.wikimedia.org
Hashblade is a multiplatform software (Gnu / Linux, MacOs, Windows) that performs text encryption for: MD5, SHA1, SHA256 and SHA512. However, the software also has the brute force functionality in the hashes previously mentioned.
"In computer science, brute force search or exhaustive search, also known as generate and test, is a trivial yet very general problem solving technique that consists of enumerating all possible candidates for the solution and checking each candidate to see if he or she satisfies the problem statement."
Ubuntu Gnu/Linux Operating System

The compilation process is basically the same in all operating systems, because it is a software written in c ++ language. While using 🐧 Gnu/Linux operating systems, just use the make command to compile and generate the binary ELF
make
or
g++ hashblade.cpp lib/md5.cpp lib/sha1.cpp lib/sha256.cpp lib/sha512.cpp lib/libhashblade.cpp -o hashblade
❗ In Windows, the process is the same, and only the extension of the final file that will be changed to hashblade.exe
hashblade -md5 "12345"
Ubuntu Gnu/Linux Operating System<

hashblade -sha1 "12345"
hashblade -sha256 "12345"
hashblade -sha512 "12345"
And if you want to get all the hashes just type:
hashblade.exe "12345"
hashblade.exe -list -sha1 mylist.txt
Ubuntu Gnu/Linux Operating System

✅ Subsequently after encrypting every word list, the software generates a new list with the name listHash.txt with encrypted hashes:
Ubuntu Gnu/Linux Operating System

The use of brute-force methods requires 3 parameters: In which type of hash the attack will apply, the list of possible passwords, and the hash itself:
hashblade -md5-brute wordlists/wordlistNumber.txt 827ccb0eea8a706c4c34a16891f84e7b
Ubuntu Gnu/Linux Operating System

The hash blade is open source software licensed under the MIT LICENSE