Invoke-LSAParse
PowerShell implementation for parsing LSA (Local Security Authority) memory dumps.
This PowerShell script can be used to extract user credentials (currently only NT hashes) from LSA memory dump files. Its only dependency is the executable of the Microsoft Console Debugger (cdb.exe) which is integrated into the PowerShell code by using the corresponding build script.
A tech blog article titled Extracting Secrets from LSA by Use of PowerShell about the problem of parsing LSA process memory dumps can be found on the SySS Tech Blog.
Installation
- Download Invoke-LSAParse
- Download the Microsoft Console Debugger and copy the executable file
cdb.exeto theInvoke-LSAParsedirectory - Call the PowerShell build script
.\build.ps1to create the actualInvoke-LSAParse.ps1PowerShell script
Usage
Load the module Invoke-LSAParse in a PowerShell session, e.g. via Import-Module .\Invoke-LSAParse.ps1, and execute it using the two parameters PathToDMP (absolute path of LSA dump file) and verbose (show additional information).
Mode of operation
Invoke-LSAParse writes the executable cdb.exe of the Microsoft Console Debugger in the temporary directory of the current user. The Microsoft Console Debugger is used for retrieving the exact memory addresses within dump files.
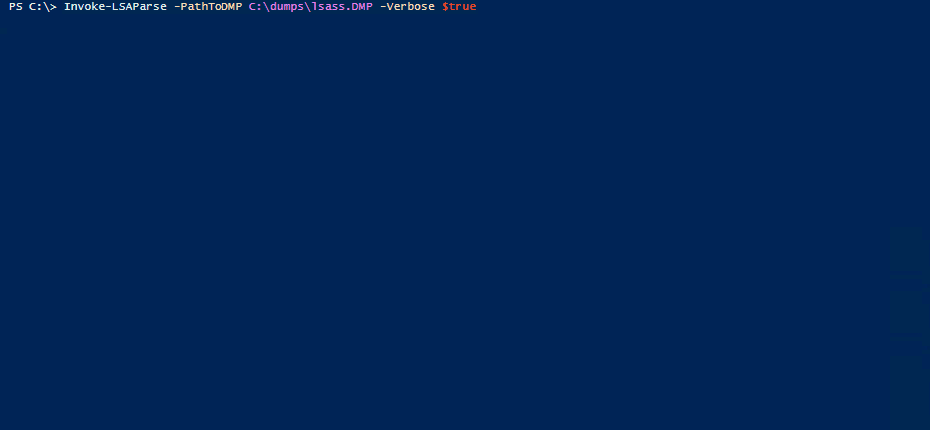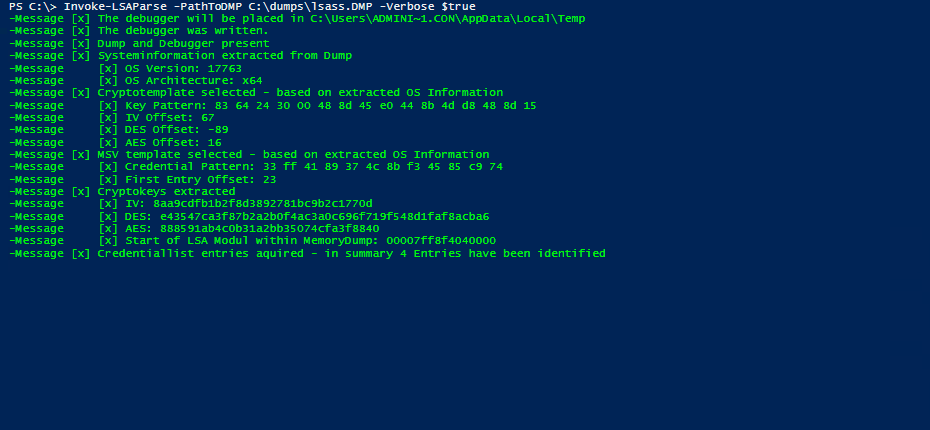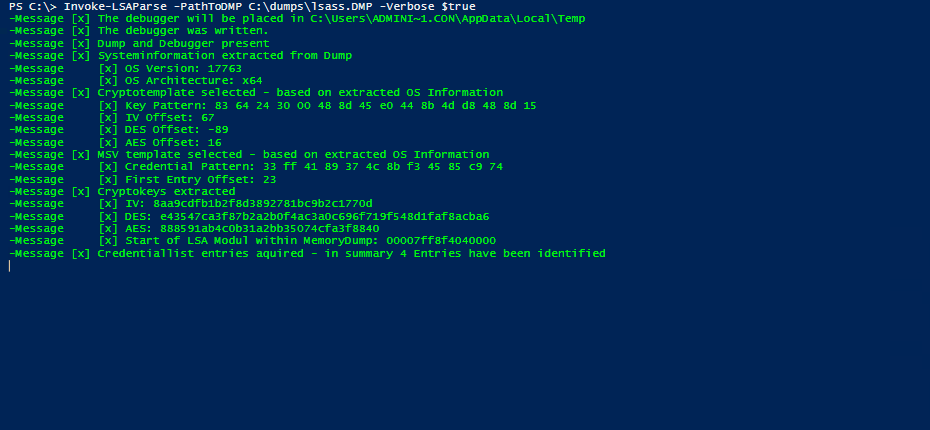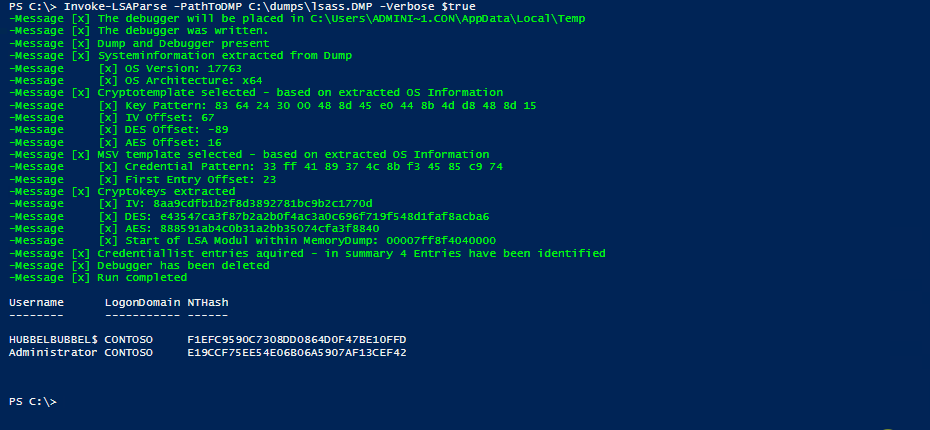
After those memory addresses are known, the data structures containing cryptographic data and encrypted user credentials are parsed using PowerShell code.
Currently, Invoke-LSAParse only outputs the NT hashes of logged-in users or identities.
Limitations
The current version of Invoke-LSAParse has the following limitations:
- Only Windows 10 LSASS process memory dumps are reliably supported.
- Extracting cleartext passwords is currently not supported.
Author
Sebastian Hölzle, SySS GmbH, 2021
Disclaimer
Use at your own risk. Do not use without full consent of everyone involved. For educational purposes only.