kfp-secret-scanner
Scan for Kubeflow pipelines secrets.
How to use it
- Push the
appto$REGISTRY/kfp-secret-scanner:$VERSION - Configure the
chart/values.yamlfile accordingly - Create the
elastic-credssecret usingcreate-elk-secret.sh(it will prompt you) - Deploy the helm chart as you please, adding the
imagePullSecretand namespace, probably. - If you want, trigger a manual run with
./manual-run.sh -n $NAMESPACE
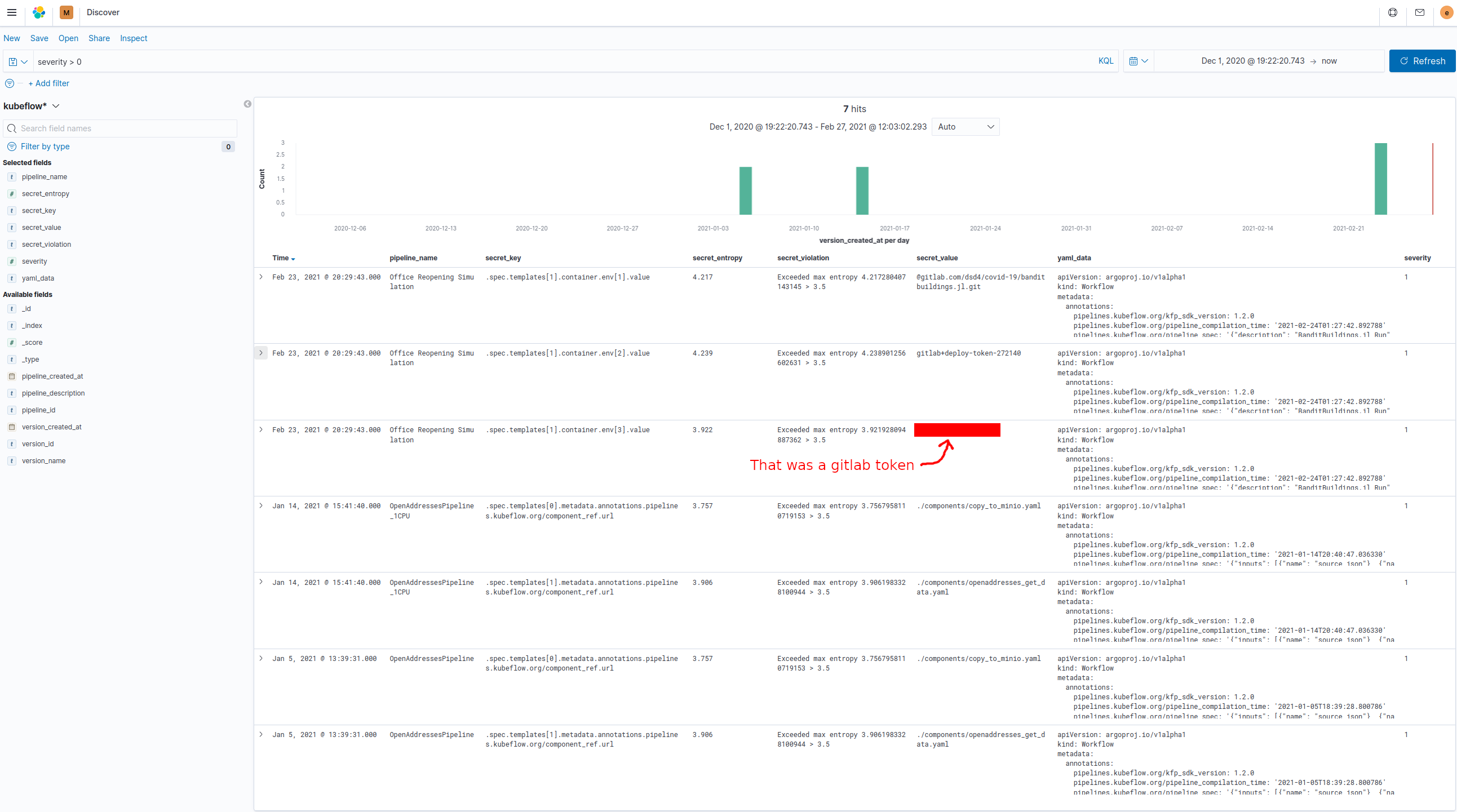
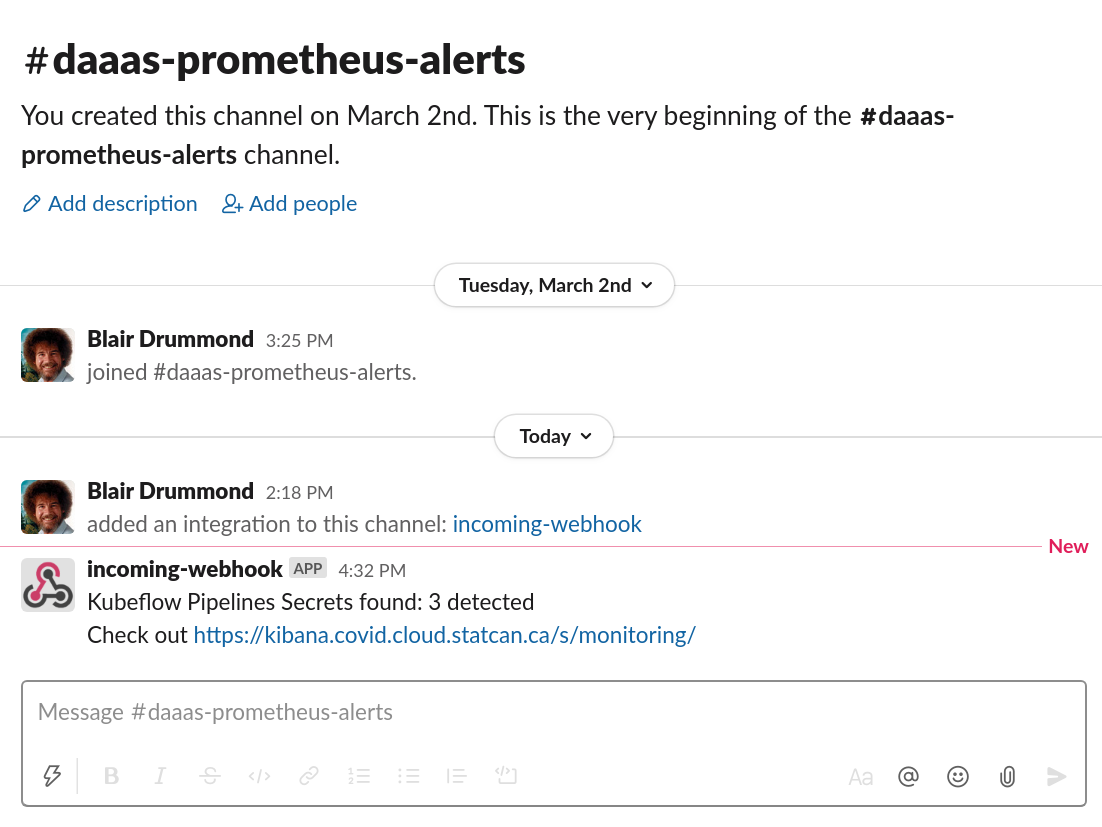
Then voila! Check kibana.
Attribution
The secret scanner borrows from Trufflehog, and the code and inspiration for scraping the kubeflow pipelines API came from @wg102's repo.