We have included the OWASP SSVS - Mapping file to show the mappings between the different standards and baselines used in the project.
The CBAS - SAP Security Verification Standard (SSVS) project allows organizations to determine their SAP security posture based on controls used to define a standard security baseline that organizations can maintain and adopt. This enables organizations to plan and enhance their security mechanisms when protecting SAP resources.
The project intends to be used by different professionals:
- SAP Security Experts
- non-SAP Security Experts
- Consultants
- Auditors
- Advisors
- The project helps operations, security, and audit teams assess, plan, and verify security controls that affect SAP implementations in their organizations.
- Helps organizations determine their maturity in protecting their SAP applications.
- Enables and supports organizations with implementing security controls that are required to protect their SAP applications.
In our initial release, we want to create a security baseline every organization must maintain to secure SAP applications.
The initial release is derived from the below standards:
- SAP Security Baseline Template V2.4
- German Federal Office for Information Security - BSI 4.2 SAP ERP System
- German Federal Office for Information Security - BSI 4.6 SAP ABAP Programming
- SAP security white papers - used for critical areas missing in the security baseline template and BSI standards
- OWASP Application Security Verification Standard ASVS 2.0
- NO MONKEY Security Matrix
We aim to create controls in a structured, easy, and understandable way.
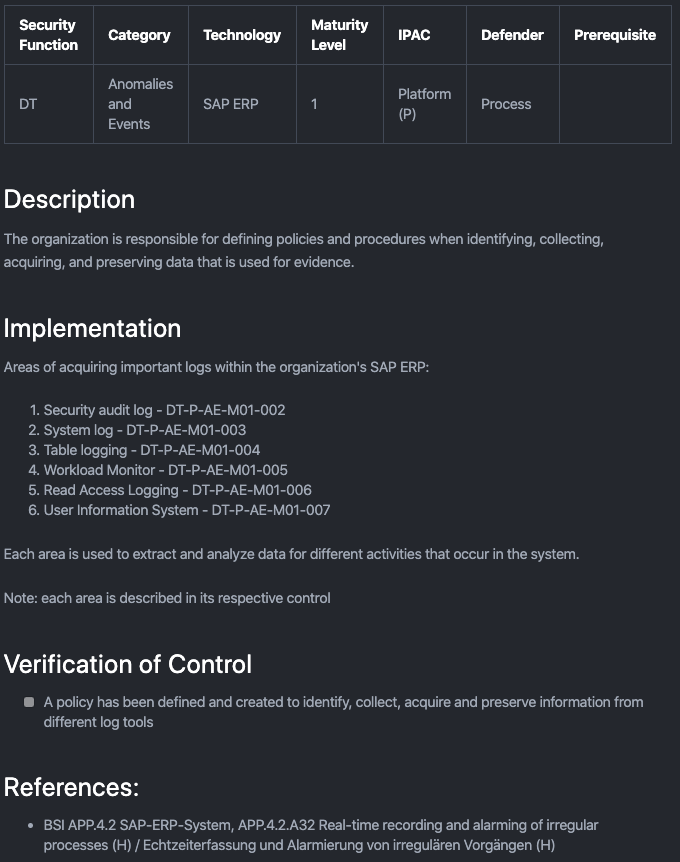
- Every control follows the same identification schema and structure
- Markdown language used for presenting the controls
- Excel tool to present maturity levels, risk areas represented by the NO MONKEY Security Matrix, and implementation status
Check our current released controls here.
We are continuously adding controls to cover the different maturity levels defined in the project. You can check our projects page to stay updated for upcoming controls.
- NIST Security Function
- NIST Category
- SAP Operational Areas
- SAP Technology
- Maturity Level (will be removed in the next release)
- Defender (People, Process, Technology)
- Control Prerequisite
Appendix A lists the acronyms used in either the control header or the naming convention for controls.
- Description of the control
- Implementing the control
- Verification of the control
- References
Anyone interested in supporting, contributing or giving feedback join us in our discord channel.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.