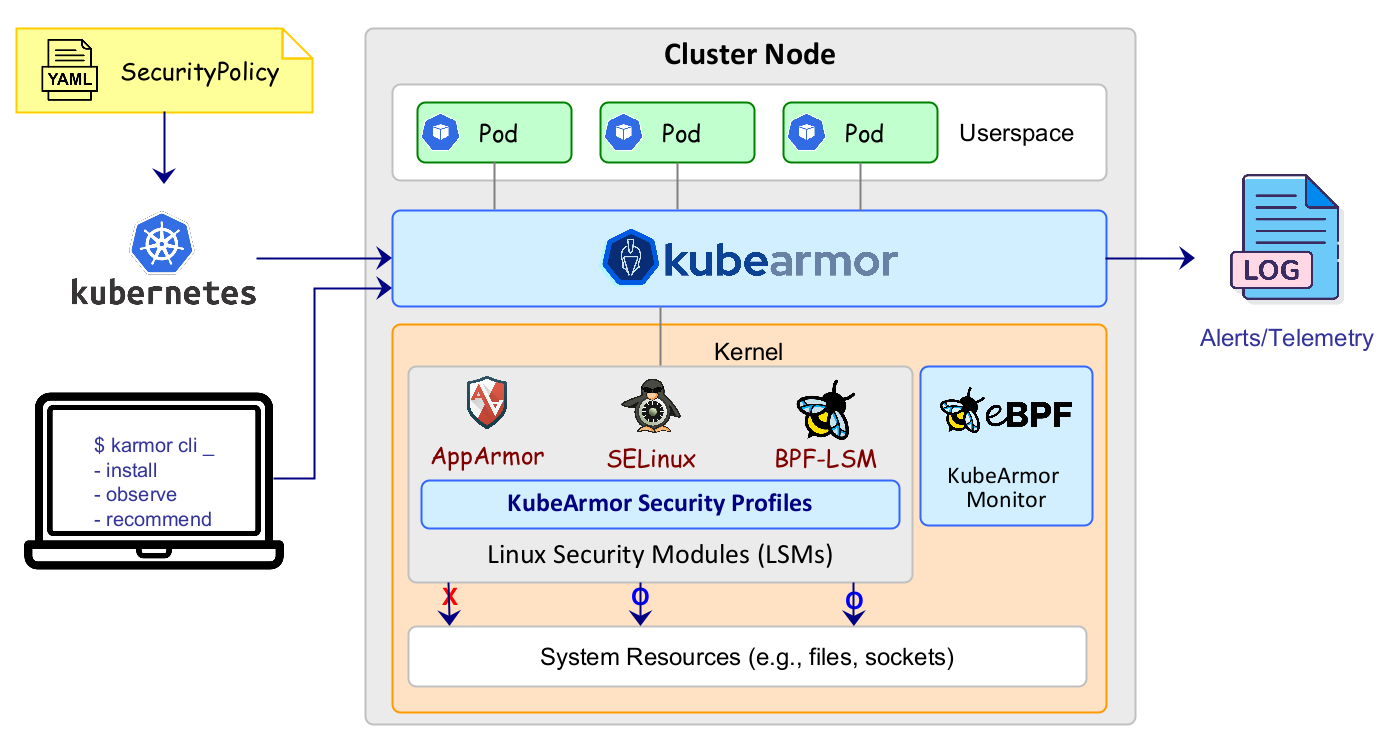
KubeArmor is a cloud-native runtime security enforcement system that restricts the behavior (such as process execution, file access, and networking operations) of pods, containers, and nodes (VMs) at the system level.
KubeArmor leverages Linux security modules (LSMs) such as AppArmor, SELinux, or BPF-LSM to enforce the user-specified policies. KubeArmor generates rich alerts/telemetry events with container/pod/namespace identities by leveraging eBPF.
Architecture Overview
Documentation 📓
👉 Getting Started🎯 Use Cases✔️ KubeArmor Support Matrix🏅 How is KubeArmor different?📜 Security Policy for Pods/Containers [Spec] [Examples]📜 Security Policy for Hosts/Nodes [Spec] [Examples]
Contributors 👥
Biweekly Meetup
🗣️ Zoom Link📄 Minutes: Document📆 Calendar invite: Google Calendar, ICS file
Notice/Credits 🤝
- KubeArmor uses Tracee's system call utility functions.
CNCF
KubeArmor is Sandbox Project of the Cloud Native Computing Foundation.