This is a repository that makes a saml+scim integration based on the ms_azure or okta integrations for Snowflake. The following resources are made depended on what you choose:
- snowflake_account_grant.provisioner_create_role
- snowflake_account_grant.provisioner_create_user
- snowflake_role.provisioner
- snowflake_role_grants.provisioner_grants
- snowflake_saml_integration.saml_integration
- snowflake_scim_integration.scim_integration
Example CICD with BitBucket and Codefresh:
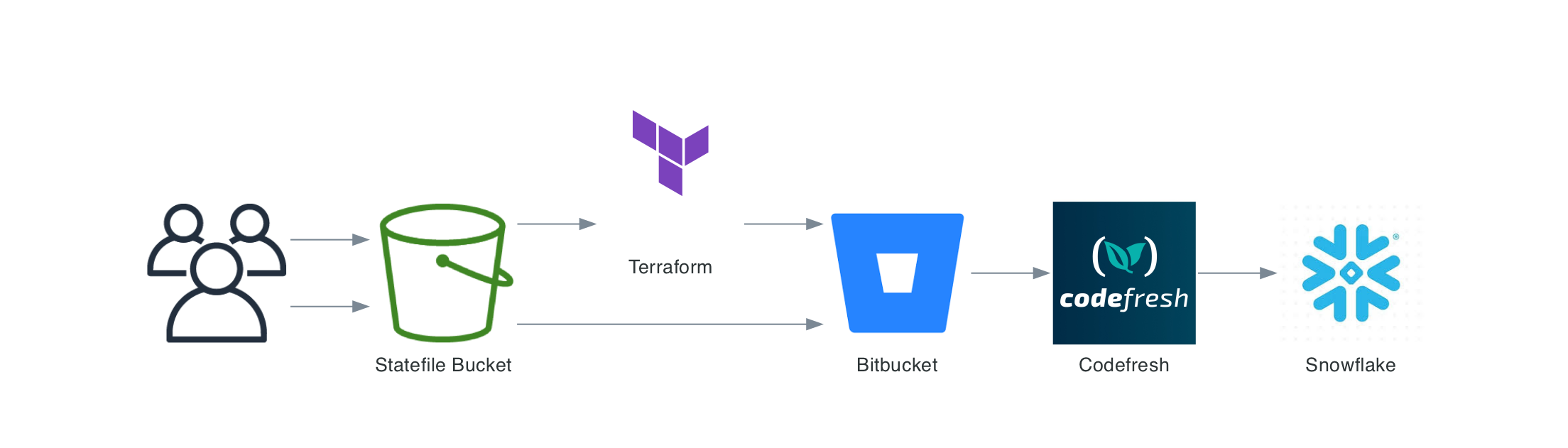
For further documentation on how this works, please read the following:
Essentially this module simplifies the ability to onboard new accounts and enables the IDP of choice to:
- Manage the user lifecycle (i.e. create, update, and delete) in Snowflake.
- Manage the role lifecycle (i.e. create, update, and delete) in Snowflake.
- Manage user to role assignments in Snowflake.
NOTES:
- THIS MODULE ASSUMES YOU HAVE AN IDP OF OKTA OR MS_AZURE
- THIS MODULE ASSUMES THAT YOU HAVE SET UP YOUR IDP AND THAT IT IS CONFIGURED
- THIS MODULE ASSUMES YOU HAVE SNOWFLAKE
WARNINGS:
- DO NOT HARDCODE THE
saml2_x509_certTHIS IS A SENSITIVE VALUE, YOU SHOULD USE SOME OTHER METHOD TO GRAB THIS DATA, I SIMPLY SHOW WHAT THE DATA MUST LOOK LIKE. IT IS A SECURITY RISK TO HARDCODE YOURsaml2_x509_certAND IS MARKED SENSITIVE BY DEFAULT - THE
scim_tokenIS DIRECTED TORWARDS SYSTEM OUTPUT ON INITAL CREATION AND WILL LOG TO YOUR TERMINAL ON CREATION FOR YOU TO USE. THIS WILL ONLY HAPPEN ONCE AND IT WILL NOT APPEAR IN SYSTEM LOGS AS IT IS MARKED SENSITIVE BY DEFAULT
To use the module you will need to use the following:
module "snowflake_samlscim_usdevelopment" {
source = "https://github.com/Richard-Barrett/terraform-snowflake-scim-integration"
version = "0.0.1"
idp = "okta"
saml2_issuer = "http://www.okta.com/<OKTA_ENTITY_ID>"
saml2_sso_url = "https://<YOURDOMAIN>.okta.com/app/snowflake/<OKTA_ENTITY_ID>/sso/saml"
saml2_provider = "OKTA"
saml2_x509_cert = "MIIDnjCCAoa...IGA..."
saml2_snowflake_issuer_url = "https://<URI>.<AWS_REGION>.aws.snowflakecomputing.com"
saml2_snowflake_acs_url = "https://<FQDN>.snowflakecomputing.com/fed/login"
}Required Values:
| Values |
|---|
| idp |
| saml2_issuer |
| saml2_sso_url |
| saml2_provider |
| saml2_x509_cert |
| saml2_snowflake_issuer_url |
| saml2_snowflake_acs_url |
Once you run the following:
terraform init
terraform validate
terraform plan
terraform apply
You should see something similar to the following:
Apply complete! Resources: 2 added, 0 changed, 0 destroyed.
Outputs:
scim_token = <sensitive>Take the scim_token and update your IDP with the API integration, afterwards, make sure you check what you want controlled by the provisioner:
- NOTE: ORDER MATTERS, CREATE THE API TOKEN AND TEST PROVISIONING FIRST BEFORE YOU SELECT WHAT THE PROVISIONING DOES IN THE IDP.
What if you want to manage the SCIM Access for ms_azure?
module "snowflake_samlscim_usdevelopment" {
source = "https://github.com/Richard-Barrett/terraform-snowflake-scim-integration"
version = "0.0.1"
idp = "aad"
saml2_issuer = "http://www.okta.com/<OKTA_ENTITY_ID>"
saml2_sso_url = "https://<YOURDOMAIN>.okta.com/app/snowflake/<OKTA_ENTITY_ID>/sso/saml"
saml2_provider = "AAD"
saml2_x509_cert = "MIIDnjCCAoa...IGA..."
saml2_snowflake_issuer_url = "https://<URI>.<AWS_REGION>.aws.snowflakecomputing.com"
saml2_snowflake_acs_url = "https://<FQDN>.snowflakecomputing.com/fed/login"
}If you want to keep the saml2_x509_cert secret pull it in as a data value from a secure datastore using your backend.
In overview, this repository acts as a digestible module that allows you to create a warehouse, the warehouse role, and the warehouse grant.
| Name | Version |
|---|---|
| terraform | >= 1.3.6 |
| snowflake | ~> 0.89.0 |
| Name | Version |
|---|---|
| snowflake | 0.89.0 |
No modules.
| Name | Type |
|---|---|
| snowflake_account_grant.provisioner_create_role | resource |
| snowflake_account_grant.provisioner_create_user | resource |
| snowflake_role.provisioner | resource |
| snowflake_role_grants.provisioner_grants | resource |
| snowflake_saml_integration.saml_integration | resource |
| snowflake_scim_integration.scim_integration | resource |
| snowflake_system_generate_scim_access_token.scim | data source |
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| enabled | value to enable or disable the SAML integration | bool |
true |
no |
| idp | The identity provider. Can be 'okta' or 'ms_azure' | string |
n/a | yes |
| saml2_issuer | value to enable or disable the SAML integration | string |
"your_default_value_here" |
no |
| saml2_provider | value to enable or disable the SAML integration | string |
"default_saml2_provider" |
no |
| saml2_snowflake_acs_url | value to enable or disable the SAML integration | string |
"https://example.com/saml2/acs" |
no |
| saml2_snowflake_issuer_url | value to enable or disable the SAML integration | string |
"https://example.com/snowflake/issuer" |
no |
| saml2_sso_url | value to enable or disable the SAML integration | string |
"https://example.com/saml2/sso" |
no |
| saml2_x509_cert | value to enable or disable the SAML integration | string |
"default_value" |
no |
| Name | Description |
|---|---|
| scim_access_token | The SCIM access token |
