This is a repository that makes databases and database roles.
- snowflake_database.this
- snowflake_database_grant.create
- snowflake_database_grant.grant
- snowflake_role.read
- snowflake_role.write
- snowflake_schema_grant.all
- snowflake_schema_grant.create
- snowflake_schema_grant.read
- snowflake_table_grant.read
- snowflake_table_grant.write
- snowflake_view_grant.read
In general this repository is a module that can be used for making databases via a digestable module. The module in question creates two roles:
- snowflake_role.read
- snowflake_role.write
The roles are consecutive to RO for read permissions and RW for read/write permissions.
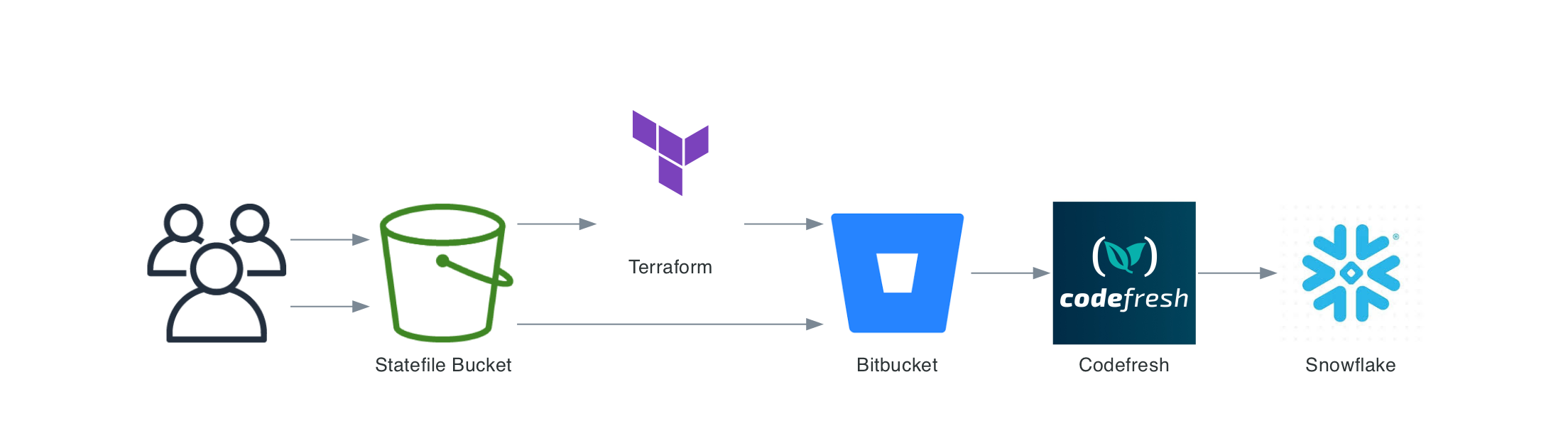
Example CICD with BitBucket and Codefresh:
To use the module you will need to use the following:
module "snowflake_database_consumption" {
source = "https://github.com/Richard-Barrett/terraform-snowflake-scim-integration"
version = "0.0.1"
database_name = "CONSUMPTION"
comment = "CONSUMPTION Database"
}There may be times where you want to specify more than what is needed and forloop through a bunch of roles or what not. This is particularly useful if you are using SCIM Provisioning to control your roles. As such you could see about controlling the roles via some form of mapping and iterating through each role that is created by the IDP to create databases for each role:
module "snowflake_database" {
for_each = toset(local.okta_role_databases)
source = "https://github.com/Richard-Barrett/terraform-snowflake-scim-integration"
version = "0.0.1"
database_name = "TEAM_${each.value}"
comment = "Database for ${each.value} Team"
}The above shows the use case, whereby you would want a locals.tf with some mapping for the okta_role_databases.
locals {
okta_roles = {
OKTA_SNOWFLAKE_TEAMNAME_READ = ["TEAM_TEAMNAME_DB_RO"]
OKTA_SNOWFLAKE_TEAMNAME_MODIFY = ["TEAM_TEAMNAME_DB_RW"]
}
okta_role_databases = distinct(flatten([
for role in keys(local.okta_roles) : [
replace(replace(replace(role, "OKTA_SNOWFLAKE_USPROD_", ""), "_MODIFY", ""), "_READ", "")
]
]))
}As you can see this module is very good at baking on the databases, database_roles, and database_grants.
The only required values are database_name and comment.
| Name | Version |
|---|---|
| terraform | >= 1.3.6 |
| snowflake | ~> 0.89.0 |
| Name | Version |
|---|---|
| snowflake | 0.75.0 |
No modules.
| Name | Type |
|---|---|
| snowflake_database.this | resource |
| snowflake_database_grant.create | resource |
| snowflake_database_grant.grant | resource |
| snowflake_role.read | resource |
| snowflake_role.write | resource |
| snowflake_schema_grant.all | resource |
| snowflake_schema_grant.create | resource |
| snowflake_schema_grant.read | resource |
| snowflake_table_grant.read | resource |
| snowflake_table_grant.write | resource |
| snowflake_view_grant.read | resource |
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| account_shares | Snowflake Account Shares that for Database Shares Across Accounts | set(string) |
[] |
no |
| comment | Database Comments | string |
n/a | yes |
| data_retention_time_in_days | Snowflake Database data retention time in days | string |
"7" |
no |
| database_name | Name of the database | string |
n/a | yes |
| enable_multiple_grants | (Boolean) When this is set to true, multiple grants of the same type can be created. This will cause Terraform to not revoke grants applied to roles and objects outside Terraform. | bool |
true |
no |
| read_permissions | Read Permissions for RBAC | set(string) |
[ |
no |
| schema_object_types | n/a | set(string) |
[ |
no |
| schema_read_privileges | Schema Privileges | set(string) |
[ |
no |
| schema_write_privileges | Schema Privileges | set(string) |
[ |
no |
| with_grant_option | Ignore Edition Check | bool |
true |
no |
| write_permissions | Read Permissions for RBAC | set(string) |
[ |
no |
| Name | Description |
|---|---|
| read_access | Read access granted to the database on selected warehouse on snowflake_role.name |
| write_access | Write access granted to the database on selected warehouse snowflake_role.name |