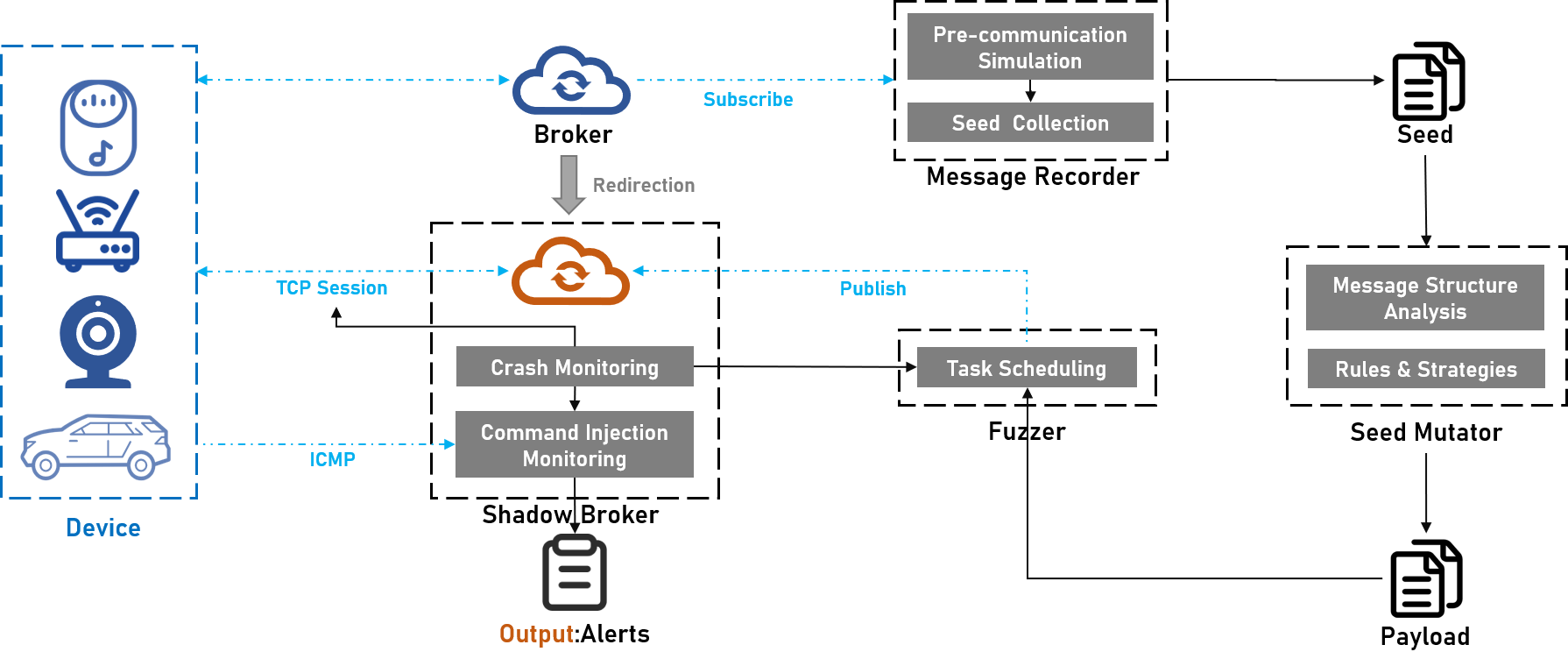
The ShadowFuzzer is a fuzzing framework to find client-side vulnerabilities when processing incoming MQTT messages.
Huikai Xu, Miao Yu, Yanhao Wang, Yue Liu, Qinsheng Hou, Zhenbang Ma, Haixin Duan, Jianwei Zhuge and Baojun Liu. Processdings of The 7th IEEE European Symposium on Security and Privacy, (EuroS&P) Genoa, June 6-10, 2022
The attack targets are the IoT devices communicating with the MQTT broker. The adversary aims to leverage the broker as a trampoline to transfer exploit messages to the target devices to trigger the vulnerabilities when processing the MQTT payload.
First build the ShadowBroker and make the device (subscriber) to connect to the ShadowBroker by DNS redirection or other tricks.
Boot the fuzzer