Rahul Sharma
ELTROPY DEVOPS ASSESSMENT
18th NOV 2020
GOALS
-
Create a VPC
-
Create EC2 instance using Ubuntu Linux
-
Enable and configure Security Group
-
Server Hardening
-
Research and execute server hardening on this instance
-
For example (but not limited to the following, implement more if possible)
- SSH on a nonstandard port
- Disabled Password-based Sign in
- Configure UFW (Ubuntu Firewall)
- Disable root access
-
-
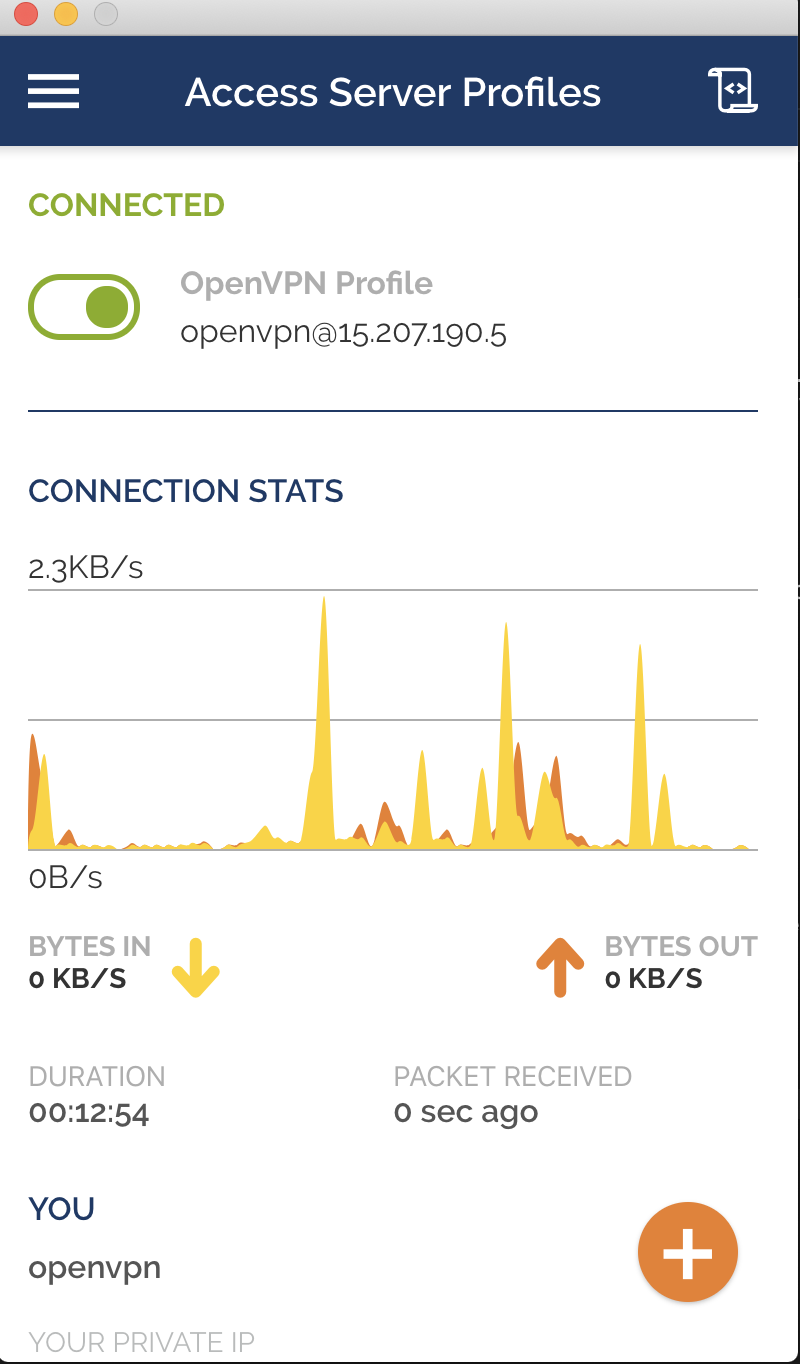
VPN - Enable Access only through OpenVPN to this instance
-
CloudWatch - Setup CloudWatch for Disk size and CPU
- Enable Email alerts for alerts
-
Enable ClamAV - Free AntiVirus for Linux
-
Backup
- Enable backup for instances
REQUIREMENTS
- Ansible 2.9.x
- Terraform 0.13.x
- AWS Console account with EC2, VPC, Cloudwatch, SNS CRUDs. (default provide should be accessible by aws-cli on ~/.aws/credentials)
This is a**complete Automated Setup** using Terraform and ansible. We just need to connect with the VPN manually from the system. Everything will be taken care of on its own.
Terraform Tasks Brief
Deploying VPN.
-
Selecting Region from available 14 region
-
Creating VPC for OpenVPN.
- Internet Gateway
- Public Subnet
- Route tables
- Security Groups ( Port 1194 open for connecting purposes.)
-
Auto Deploy Provided SSH Key Pairs.
-
Creating Instance for EC2
- User-data (For setting some initial VPN setting like username, password)
- Static EIP for OpenVPN.
At this stage, you should connect with OpenVPN as further steps only work with VPN.
Connecting VPN
To be able to connect with OpenVPN you need the following:
- VPN Server IP (You will get it from terraform output once, Deployed.)
- Username/Password (You will get it from terraform output once, Deployed.)
Deploying Webapp
Isolated environment (Only Accessible from deployed VPN)
-
Selecting Region from available 14 region
-
Searching Latest Ubuntu LTS from AMI Repo.
-
Creating VPC for OpenVPN.
- Internet Gateway.
- Private Subnet.
- Route tables.
- Security Groups ( Port 2224 open for VPN, 80/443 world open.)
- Creating Iam Role and policies for Cloudwatch access.
-
Auto Deploy Provided SSH Key Pairs.
-
Creating Instance for EC2
- User-data (For setting some initial VPN setting like username, password)
- Static EIP for web-app.
Ansible Configurations.
These configurations will automate triggered from Terraform.
-
Configuring Cloudwatch to use an ec2 attached role.
-
Firewall
- Installing Iptables
- Block OS level traffic. (Port 2224 open for VPN, 80/443 world open.)
-
Nginx Web Server
- Installing Nginx
- Setting a Vhost (eltropydemo.rvsharma.com) as well as other settings for root directories, error/access logs.
-
OS Level Security(Hardening).
-
Install software to monitor badSSH access and Nginx DDOS (fail2ban)
- IP will block for 10 Minutes on 3 Bad SSH attempts.
- IP will get blocked for 120 Minutes on 10 error entries in Nginx error logs.
-
Configure SSH to be more secure (disabling root login, requiring key-based authentication, and allowing a custom SSH port 2224)
-
Set up automatic updates.
-
-
Securing Nginx (Hardening).
- Nginx_client_body_buffer_size Default: 1k Description: Sets buffer size for reading client request body. In case the request body is larger than the buffer, the whole body or only its part is written to a temporary file.
- Nginx_remove_default_site Default: true Description: Disables the default site. Set to false to enable the default site in Nginx.
- Nginx_client_max_body_size Default: 1k Description: Sets the maximum allowed size of the client request body, specified in the “Content-Length” request header field. If the size in a request exceeds the configured value, the 41 3 (Request Entity Too Large) error is returned to the client.
- Nginx_keepalive_timeout Default: 5 5 Description: The first parameter sets a timeout during which a keep-alive client connection will stay open on the server-side. The zero value disables keep-alive client connections. The optional second parameter sets a value in the “Keep-Alive: timeout=time” response header field.
- Nginx_server_tokens Default: off Description: Disables emitting the Nginx version in error messages and the "Server" response header field. Set to on to enable the Nginx version in error messages and "Server" response header.
- Nginx_client_header_buffer_size Default: 1k Description: Sets buffer size for reading client request header. For most requests, a buffer of 1K bytes is enough.
- Nginx_large_client_header_buffers Default: 2 1k Description: Sets the maximum number and size of buffers used for reading large client request headers.
- Nginx_client_body_timeout Default: 10 Description: Defines a timeout for reading client request body.
- Nginx_client_header_timeout Default: 10 Description: Defines a timeout for reading the client request header.
- Nginx_send_timeout Default: 10 Description: Sets a timeout for transmitting a response to the client.
- Nginx_limit_conn_zone Default: $binary_remote_addr zone=default:10m Description: Sets parameters for a shared memory zone that will keep states for various keys.
- Nginx_limit_conn Default: default 5 Description: Sets the shared memory zone and the maximum allowed number of connections for a given key value.
- Nginx_add_header Default: [ "X-Frame-Options SAMEORIGIN", "X-Content-Type-Options nosniff", "X-XSS-Protection \"1; mode=block\"" ] Description: Adds the specified field to a response header provided that the response code equals 200, 201, 204, 206, 301, 302, 303, 304, or 307.
- Nginx_ssl_protocols Default: TLSv1.2 Description: Specifies the SSL protocol which should be used.
- Nginx_ssl_ciphers Default: see defaults.yml Description: Specifies the TLS ciphers which should be used.
- Nginx_ssl_prefer_server_ciphers Default: on Description: Specifies that server ciphers should be preferred over client ciphers when using the TLS protocols. Set to false to disable it.
- Nginx_dh_size Default: 2048 Description: Specifies the length of DH parameters for EDH ciphers.
-
ClamAV installation and onboot startup.
-
AWS Backup Plans
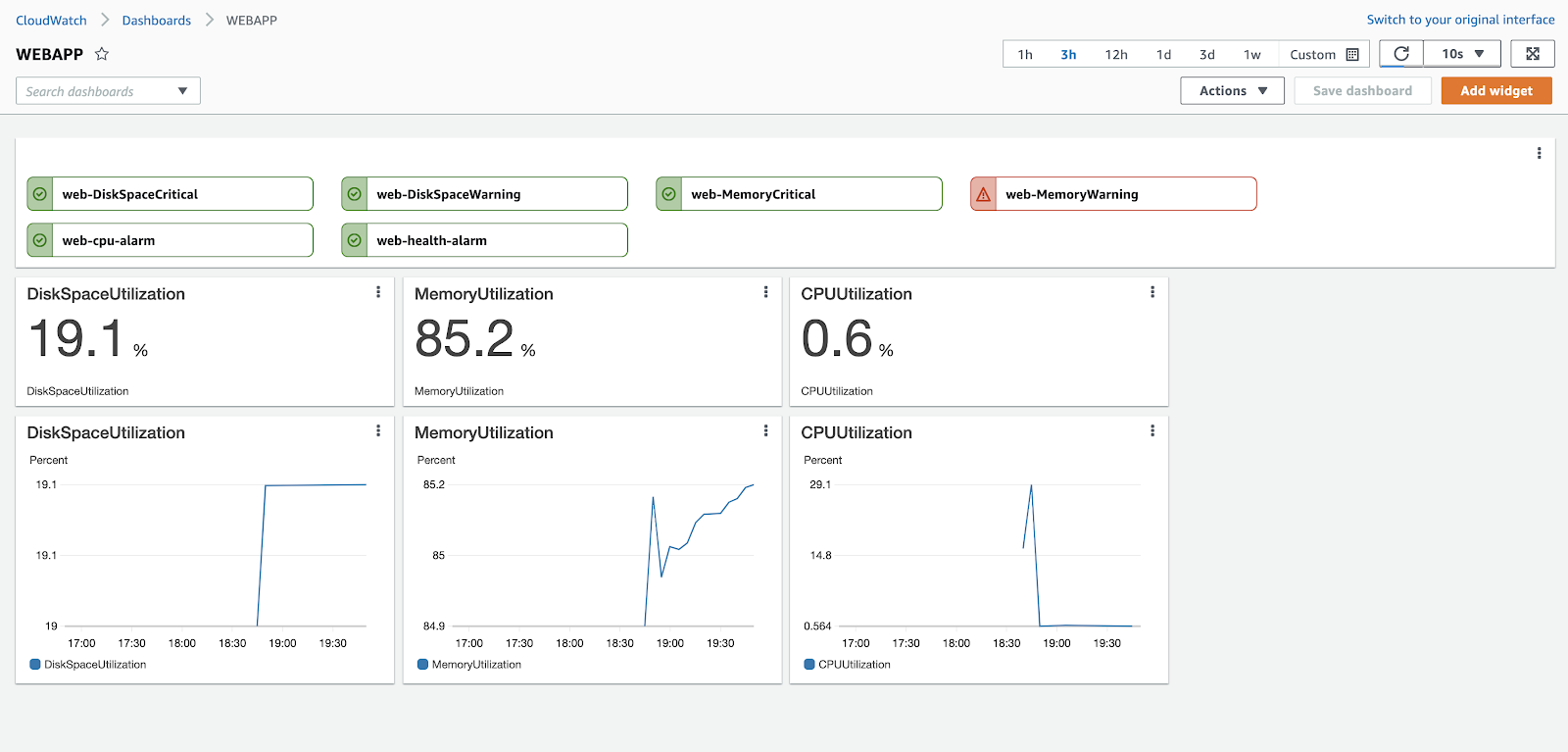
CloudWatch Monitoring
Automated Deployment of alert policies and centralized Dashboard.
-
SNS Topic with Email Subscription.
-
Metrics Alarms.
- DiskSpaceUtilization >= 70 for 1 datapoints within 2 minutes (Warning)
- DiskSpaceUtilization >= 90 for 1 datapoints within 2 minutes (Critical)
- MemoryUtilization >= 70 for 1 datapoints within 2 minutes (Warning)
- MemoryUtilization >= 90 for 1 datapoints within 2 minutes (Critical)
- StatusCheckFailed >= 1 for 1 datapoints within 2 minutes
- CPUUtilization >= 80 for 2 datapoints within 4 minutes
-
All in one Dashboard.