- Summary
- Install
- Usage
- Running reconFTW
- Sample Video
- Features
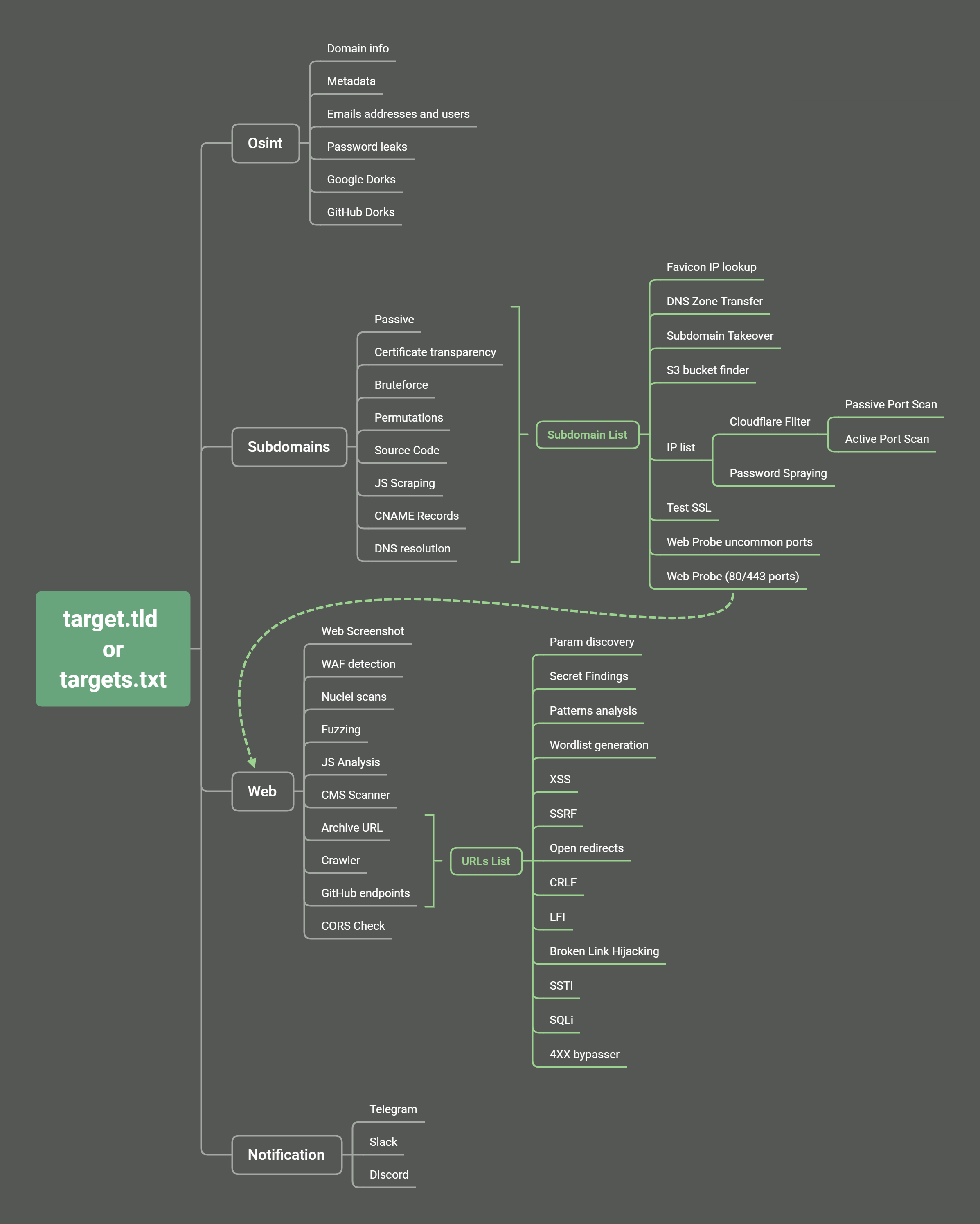
- Mindmap/Workflow
- Need help?
- Contribute
- Thanks
reconFTW is a tool designed to perform automated recon on a target domain by running the best set of tools to perform enumeration and finding out vulnerabilities.
- Installation Guide 📖
- Requires Golang > 1.14 installed and paths correctly set ($GOPATH, $GOROOT)
▶ git clone https://github.com/six2dez/reconftw
▶ cd reconftw
▶ chmod +x *.sh
▶ . ./install.sh
▶ ./reconftw.sh -d target.com -aFrom DockerHub
▶ docker pull six2dez/reconftw:main
▶ docker run -it six2dez/reconftw:main /bin/bash
# Exit the container and run this commands additionally if you want to gain persistence:
▶ docker start $(docker ps -a|grep six2dez/reconftw:main|cut -d' ' -f1)
▶ docker exec -it $(docker ps -a|grep six2dez/reconftw:main|cut -d' ' -f1) /bin/bash
# Now you can exit the container and run again this command without files loss:
▶ docker exec -it $(docker ps -a|grep six2dez/reconftw:main|cut -d' ' -f1) /bin/bash▶ git clone https://github.com/six2dez/reconftw
▶ cd reconftw/Docker
▶ docker build -t reconftw .
▶ docker run -it reconftw /bin/bash- Through
reconftw.configfile the whole execution of the tool can be controlled. - Hunters can set various scanning modes, execution preferences, tools config files, APIs/TOKENS, personalized wordlists
Click here to view default config file
#################################################################
# reconFTW config file #
#################################################################
# TERM COLOURS
bred='\033[1;31m'
bblue='\033[1;34m'
bgreen='\033[1;32m'
yellow='\033[0;33m'
red='\033[0;31m'
blue='\033[0;34m'
green='\033[0;32m'
reset='\033[0m'
# General values
tools=~/Tools
NPROC=$(nproc || echo -n 1)
SCRIPTPATH="$( cd "$(dirname "$0")" >/dev/null 2>&1 ; pwd -P )"
profile_shell=".$(basename $(echo $SHELL))rc"
#dir_output=/custom/output/path
# Golang Vars (Comment or change on your own)
export GOROOT=/usr/local/go
export GOPATH=$HOME/go
export PATH=$GOPATH/bin:$GOROOT/bin:$HOME/.local/bin:$PATH
# Tools config files
#NOTIFY_CONFIG=~/.config/notify/notify.conf # No need to define
#SUBFINDER_CONFIG=~/.config/subfinder/config.yaml # No need to define
AMASS_CONFIG=~/.config/amass/config.ini
GITHUB_TOKENS=${tools}/.github_tokens
# APIs/TOKENS - Uncomment the lines you set removing the '#' at the beginning of the line
SHODAN_API_KEY=XXXXXXXXXXXXX
XSS_SERVER=six2dez.xss.ht
COLLAB_SERVER=i0m1y4j3fu.canarytokens.com
findomain_virustotal_token=XXXXXXXXXXXXXXXXX
findomain_spyse_token=XXXXXXXXXXXXXXXXX
findomain_securitytrails_token=XXXXXXXXXXXXXXXXX
findomain_fb_token=XXXXXXXXXXXXXXXXX
# File descriptors
DEBUG_STD="&>/dev/null"
DEBUG_ERROR="2>/dev/null"
# Osint
GOOGLE_DORKS=true
GITHUB_DORKS=false
METADATA=true
EMAILS=true
DOMAIN_INFO=true
# Subdomains
SUBCRT=true
SUBBRUTE=true
SUBSCRAPING=true
SUBPERMUTE=true
SUBTAKEOVER=true
ZONETRANSFER=true
S3BUCKETS=true
# Web detection
WEBPROBESIMPLE=true
WEBPROBEFULL=true
WEBSCREENSHOT=true
# Host
FAVICON=true
PORTSCANNER=true
PORTSCAN_PASSIVE=true
PORTSCAN_ACTIVE=true
# Web analysis
WAF_DETECTION=true
NUCLEICHECK=true
URL_CHECK=true
URL_GF=true
JSCHECKS=true
PARAMS=true
FUZZ=true
CMS_SCANNER=true
WORDLIST=true
# Vulns
XSS=true
CORS=true
TEST_SSL=true
OPEN_REDIRECT=true
SSRF_CHECKS=true
CRLF_CHECKS=true
LFI=true
SSTI=true
SQLI=true
BROKENLINKS=true
SPRAY=true
BYPASSER4XX=true
# Extra features
NOTIFICATION=true
DEEP=false
DIFF=false
REMOVETMP=false
# HTTP options
COOKIE=""
HEADER="User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:72.0) Gecko/20100101 Firefox/72.0"
# Threads
FFUF_THREADS=40
HTTPX_THREADS=50
HTTPX_UNCOMMONPORTS_THREADS=150
SHUFFLEDNS_THREADS=5000
GOSPIDER_THREADS=50
GITDORKER_THREADS=5
XSSTRIKE_THREADS=30
BRUTESPRAY_THREADS=20
BRUTESPRAY_CONCURRENCE=10
# lists
fuzz_wordlist=${tools}/fuzz_wordlist.txt
lfi_wordlist=${tools}/lfi_wordlist.txt
subs_wordlist=${tools}/subdomains.txt
subs_wordlist_big=${tools}/subdomains_big.txt
resolvers=${tools}/resolvers.txtTARGET OPTIONS
| Flag | Description |
|---|---|
| -d | Target domain (example.com) |
| -m | Multiple domain target (companyName) |
| -l | Target list (one per line) |
| -x | Exclude subdomains list (Out Of Scope) |
MODE OPTIONS
| Flag | Description |
|---|---|
| -r | Recon - Full recon process (only recon without attacks) |
| -s | Subdomains - Search subdomains, check tko and web probe |
| -p | Passive - Performs only passive steps |
| -a | All - Perform all checks and exploitations |
| -w | Web - Just web checks from list provided |
| -v | Verbose - Prints everything including errors, for debug purposes |
| -h | Help - Show this help |
GENERAL OPTIONS
| Flag | Description |
|---|---|
| --deep | Deep scan (Enable some slow options for deeper scan) |
| -o | Output directory |
To perform a full recon on single target (may take a significant time)
▶ ./reconftw.sh -d example.com -rTo perfrom a full recon on a list of targets
▶ ./reconftw.sh -l sites.txt -r -o /output/directory/Perform all steps (recon + attacks)
▶ ./reconftw.sh -d example.com -aPerform full recon with more intense tasks (VPS intended)
▶ ./reconftw.sh -d example.com -r --deep -o /output/directory/Perform recon in a multi domain target
▶ ./reconftw.sh -m company -l domainsList.txt -rShow help section
▶ ./reconftw.sh -h- Domain information parser (domainbigdata)
- Emails addresses and users (theHarvester)
- Password leaks (pwndb and H8mail)
- Metadata finder (MetaFinder)
- Google Dorks (degoogle_hunter)
- Github Dorks (GitDorker)
- Multiple subdomain enumeration techniques (passive, bruteforce, permutations and scraping)
- Passive (subfinder, assetfinder, amass, findomain, crobat, waybackurls, github-subdomains, Anubis and mildew)
- Certificate transparency (crtfinder, tls.bufferover and dns.bufferover))
- Bruteforce (shuffledns)
- Permutations (dnsgen)
- Source Code Scraping (gospider)
- CNAME Records (dnsx)
- Nuclei Sub TKO templates (nuclei)
- Web Prober (httpx)
- Web screenshot (gowitness)
- Web templates scanner (nuclei)
- IP and subdomains WAF checker (cf-check and wafw00f)
- Port Scanner (Active with nmap and passive with shodan-cli)
- Url extraction (waybackurls, gau, gospider, github-endpoints)
- Pattern Search (gf and gf-patterns)
- Param discovery (paramspider and arjun)
- XSS (XSStrike)
- Open redirect (Openredirex)
- SSRF (headers asyncio_ssrf.py and param values with ffuf)
- CRLF (crlfuzz)
- Favicon Real IP (fav-up)
- Javascript analysis (LinkFinder, scripts from JSFScan)
- Fuzzing (ffuf)
- Cors (Corsy)
- LFI Checks (manual/ffuf)
- SQLi Check (SQLMap)
- SSTI (manual/ffuf)
- CMS Scanner (CMSeeK)
- SSL tests (testssl)
- Multithread in some steps (Interlace)
- Broken Links Checker (gospider)
- S3 bucket finder (S3Scanner)
- Password spraying (brutespray)
- 4xx bypasser (DirDar)
- Custom resolvers generated list (dnsvalidator)
- DNS Zone Transfer (dnsrecon)
- Docker container included and DockerHub integration
- Custom output folder
- Auto installer/updater compatible with most distros
- Diff support for continuous running (cron mode)
- Support for targets with multiple domains
- Update tools script
- RaspberryPi/ARM support
- 5 modes (recon, passive, subdomains, web and all)
- Out of Scope Support
- Notification support for Slack, Discord and Telegram (notify)
If you want to contribute to this project you can do it in multiple ways:
- Submitting an issue because you have found a bug or you have any suggestion or request.
- Making a Pull Request from dev branch because you want to improve the code or add something to the script.
- Take a look in the wiki
- Ask for help in the Telegram group
For their great feedback, support, help or for nothing special but well deserved: