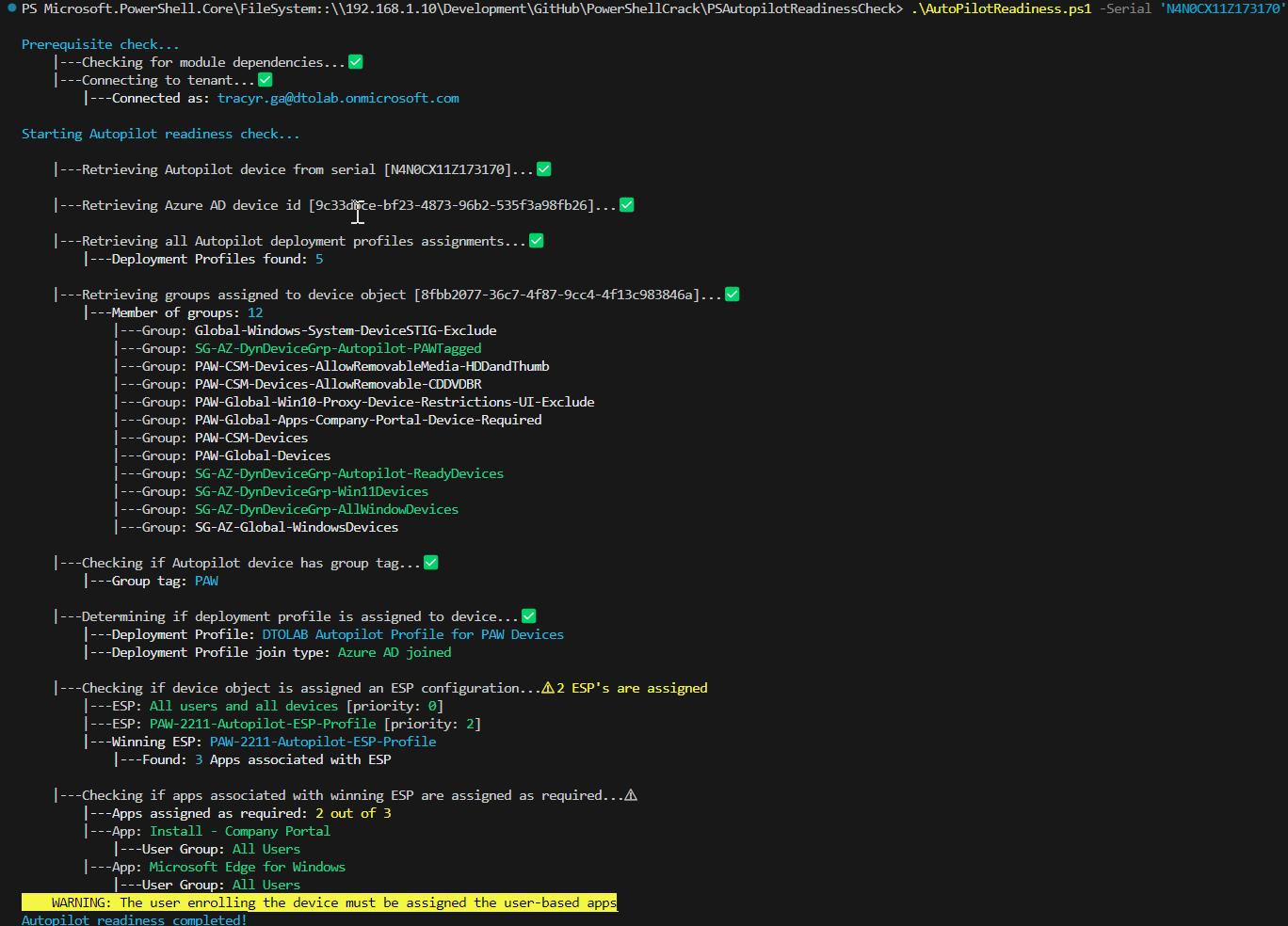
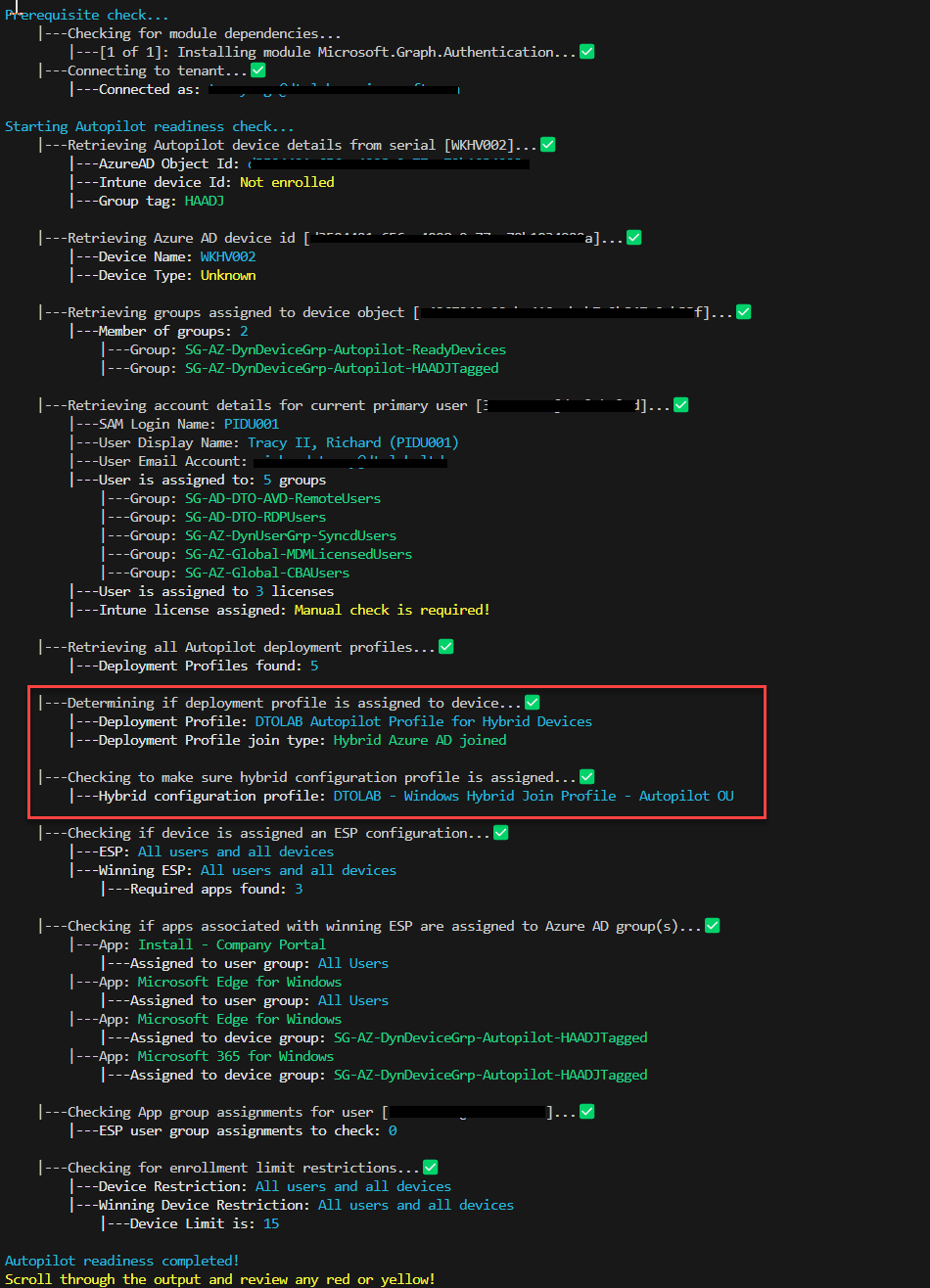
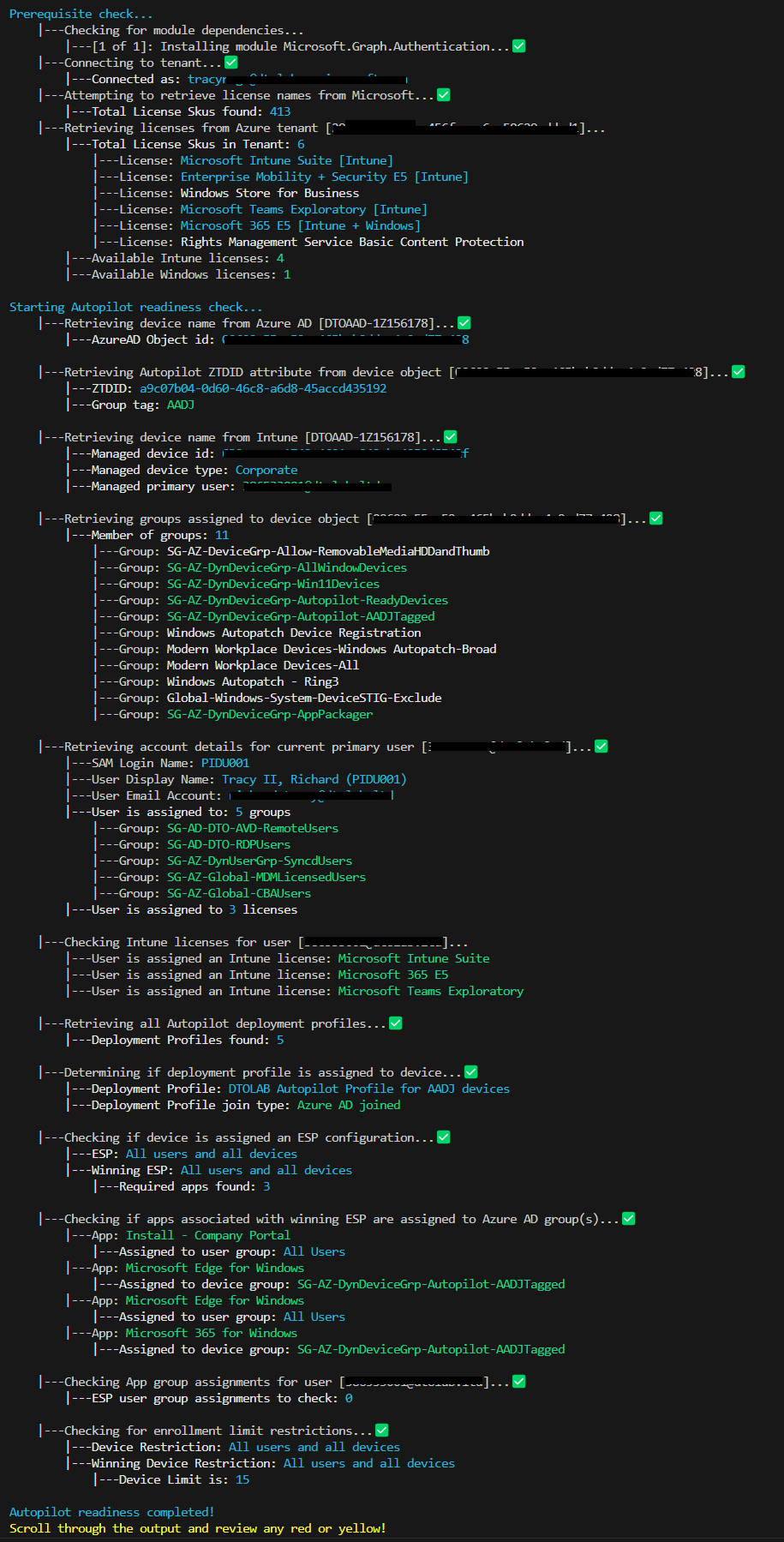
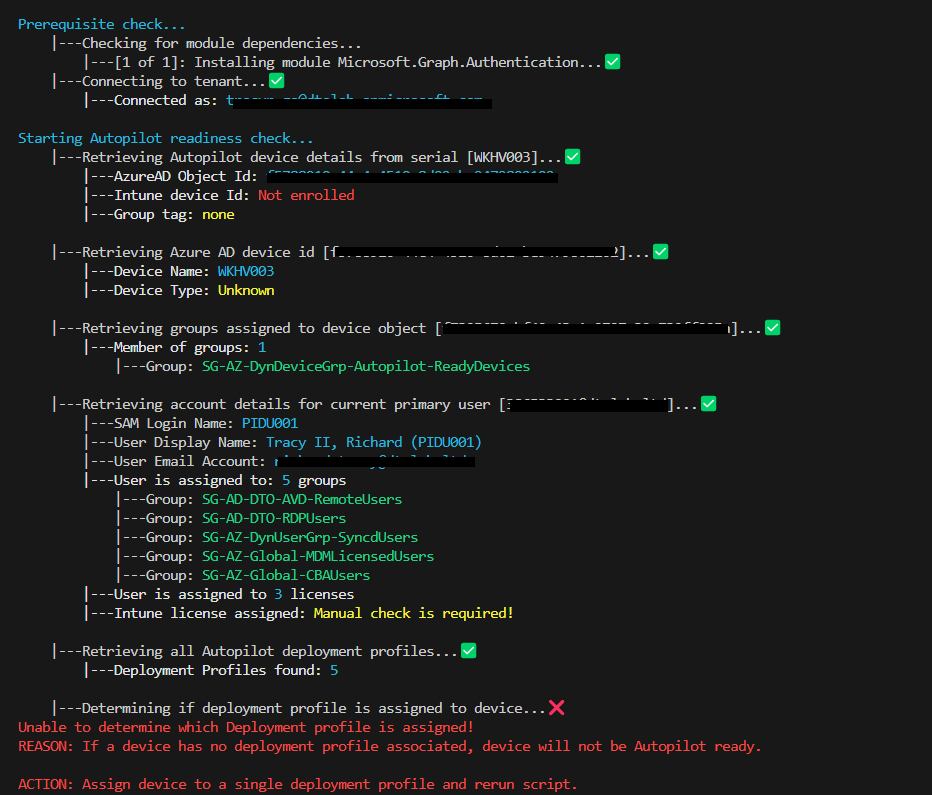
This script is designed to check to ensure a device is Autopilot Ready
This code only uses get cmdlets. There are no sets
- Microsoft.Graph.Authentication
NOTE: This script uses beta graph API requests
- Powershell 5.1 or higher (Tested with Posh 7.3.5)
- Check if device is enrolled as Autopilot Device
- Check if the device is assigned a deployment profile and how (group tag, Azure AD group)
- Check if device is assigned an ESP and what are the apps assigned to it
- Check to see what groups the device is assigned to
- Check to see if device groups are assigned to the apps as required.
- Check to see if user groups are assigned to the apps as required.
- Check type of DeploymentProfile is assigned to device (hybrid vs Azure AD)
- If Hybrid, check to make sure only one domain join profile is assigned to device
- Check if device is assigned a user profile
- Check if user is assigned to MDM enrollment group and Intune license
- Check if user is part of "allow user to Azure AD device" join group
NOTE: All graph calls are read only!
Run it against a serial number
.\AutoPilotReadiness.ps1 -Serial 'N4N0CX11Z173170'Run it against a device name
.\AutoPilotReadiness.ps1 -DeviceName 'DTOPAW-1Z173170'Run it against a device name and check licenses if primary user is assigned
.\AutoPilotReadiness.ps1 -DeviceName 'DTOAAD-1Z156178' -CheckUserLicenseRun it against a serial and check licenses for enrolling user
.\AutoPilotReadiness.ps1 -Serial 'N4N0CX11Z173170' -UserPrincipalName 'tracyr@contoso.com' -CheckUserLicenseRun it against a serial, check licenses for enrolling user, and check Azure settings
.\AutoPilotReadiness.ps1 -Serial 'N4N0CX11Z173170' -UserPrincipalName 'tracyr@contoso.com' -CheckUserLicense -CheckAzureAdvSettingsTest against a potential azure ad device
Test against a potential hybrid device
Test against an existing device
Failed test
- If apps or configuration has assignment filters; this may cause the output to be wrong; this is because the tool doesn't currently check if the device is in a filter.
- WPF UI
- Make it modular (Json controlled)
- Logging (cmtrace format)
- Support assignment filters
- Check if device is assigned at least one compliance policy (to ensure device will be compliant)
- Check if device is part of a device filter
- Check if device is assigned a device category
- Check Device restrictions against device
- Check Device limitation against user profile
- Check if device has supporting OS (using WINRM)
- Check if user is part of CBA Stage Rollout
- Check for Organization branding
- Check if user is assigned a Windows license.
- Check if device is assigned a post script (eg. rename script, complete script, etc)
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.