- Use Procmon to obtain a CSV file of potential DLL hijacks
- Modify
outputFilevariable withinwrite.cpp - Build the project for the appropriate architecture
- Open
powershell.exeand loadGet-PotentialDLLHijack.ps1into memory. .\Get-PotentialDLLHijack.ps1
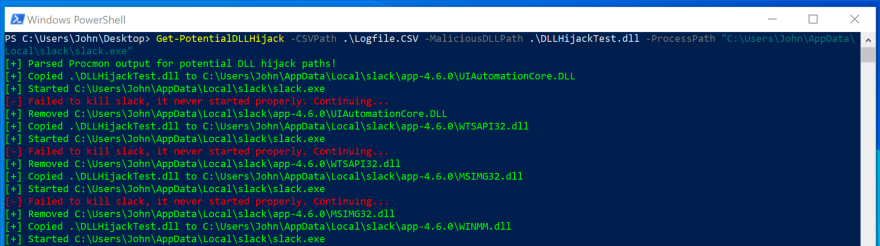
- Run
Get-PotentialDLLHijackwith the appropriate flags- Example:
Get-PotentialDLLHijack -CSVPath .\Logfile.CSV -MaliciousDLLPath .\DLLHijackTest.dll -ProcessPath "C:\Users\John\AppData\Local\Programs\Microsoft VS Code\Code.exe"
-CSVPathtakes in a path to a .csv file exported from Procmon-MaliciousDLLPathtakes in a path to your compiled hijack DLL-ProcessPathtakes in a path to the executable you want to run-ProcessArgumentstakes in commandline arguments you want to pass to the executeable
- Example:
- View the contents of
outputFilefor found DLL hijacks- Run
strings.exeon theoutputFileto clean up the output paths
- Run
- Party!!!