This Terraform template target for AWS Security Lake service enablement on AWS Organizations. This repository have two module for the AWS services enabling and setup by each organization account. Let's look at below guide.
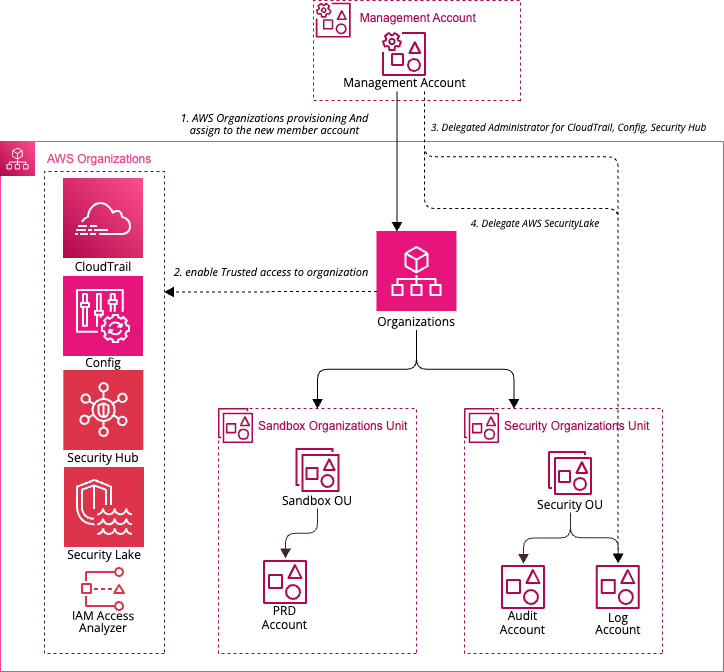
This Terraform code configures preconditions for activating the Security Lake service, and It must be set up in AWS Organization's management account. First, activate the AWS Organization service, create a OU, and create an account that has specific roles, such as a log archive role. Second, management account is enable trusted access with AWS Security Service ( AWS CloudTrail, AWS Config, AWS Security Hub, Amazon Security Lake) Third, the management account must specify an delegated Security Lake administrator account for the organization, which should be the Log Archive account.
Please refer to this README
module/org-management-securitylake-delegate/
├── terraform.tf
├── variables.auto.tfvars
├── variables.tf
├── datas.tf
├── locals.tf
├── resources
│ └── member_account.yml
├── aws-organizations.tf
├── aws-org-administrators-delegation.tf
├── HEAD.md
└── README.md
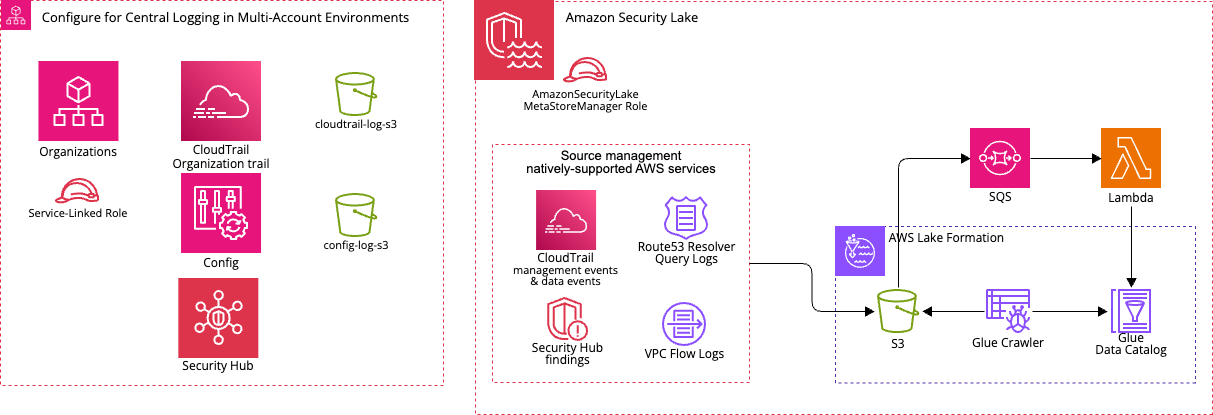
This module is set up in the Log Archive account. Set up AWS services by following natively-supported logging and event collection in Amazon Security Lake. such as a Cloudtrail, Security Hub, Config After that, create the required Role, enable Amazon Security Lake, and log source settings.
Please refer to this README
module/org-logarchive-securitylake-setup/
├── terraform.tf
├── variables.auto.tfvars
├── variables.tf
├── datas.tf
├── resources
│ ├── AmazonSecurityLakeS3ReplicationPolicy.json.tftpl
│ ├── EmptyStatement.json.tftpl
│ ├── S3BucketPermission_CloudTrail_append.json.tftpl
│ ├── S3BucketPermission_Config_append.json.tftpl
│ └── assume_role_policy.json.tftpl
├── cloudtrail_forOrg.tf
├── configService_forOrg.tf
├── securityhub_forOrg.tf
├── iam_roles.tf
├── main.tf
├── HEAD.md
└── README.md