MANDO-GURU: Vulnerability Detection for Smart Contract Source Code By Heterogeneous Graph Embeddings - API Services
This project was created to bring out the APIs of vulnerability detection for smart contracts based on heterogeneous graph embeddings.
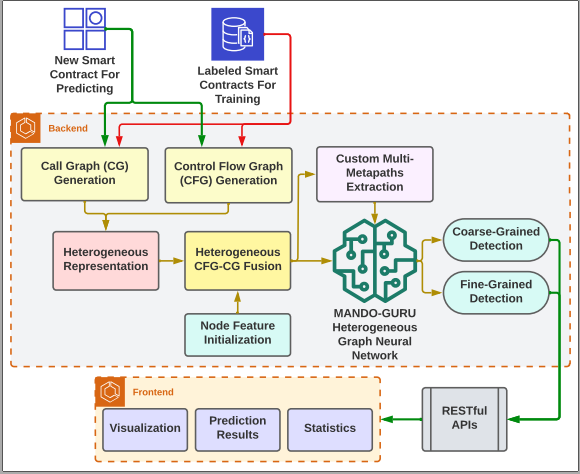
- Backend plays a vital role with several core sub-components such as heterogeneous presentation for the generated graphs from input smart contract files, heterogeneous graph fusion, custom multi-metapaths extraction, heterogeneous graph neural network, and vulnerability detections in coarse-grained and fine-grained levels.
- Frontend component services are used to visualize the prediction results and the statistics of the analyzed smart contracts.
- RESTful APIs are implemented as a bridge to communicate between the Backend and the Frontend.
Nguyen, H. H., Nguyen, N. M., Doan, H. P., Ahmadi, Z., Doan, T. N., & Jiang, L. (2022, November). MANDO-GURU: vulnerability detection for smart contract source code by heterogeneous graph embeddings. In Proceedings of the 30th ACM Joint European Software Engineering Conference and Symposium on the Foundations of Software Engineering (pp. 1736-1740). Preprint
@inproceedings{nguyen2022fse,
author = {Nguyen, Hoang H. and Nguyen, Nhat-Minh and Doan, Hong-Phuc and Ahmadi, Zahra and Doan, Thanh-Nam and Jiang, Lingxiao},
title = {MANDO-GURU: Vulnerability Detection for Smart Contract Source Code By Heterogeneous Graph Embeddings},
year = {2022},
month = {11},
isbn = {9781450394130},
publisher = {Association for Computing Machinery},
address = {New York, NY, USA},
url = {https://doi.org/10.1145/3540250.3558927},
doi = {10.1145/3540250.3558927},
booktitle = {Proceedings of the 30th ACM Joint European Software Engineering Conference and Symposium on the Foundations of Software Engineering},
pages = {1736-1740},
numpages = {5},
keywords = {Ethereum blockchain, graph neural networks, heterogeneous graphs, smart contracts, vulnerability detection},
location = {Singapore, Singapore},
series = {ESEC/FSE 2022}
}
- You can upload a solidity smart contract from local or select an available one in the drop-down box.
- We supported 7 kind of bugs. Due to limits of computation resources, the scanning process might take 1-2 minutes to get the results, depending on the complexity of the input source file. We recommend users use the Chrome browser for the best experience.
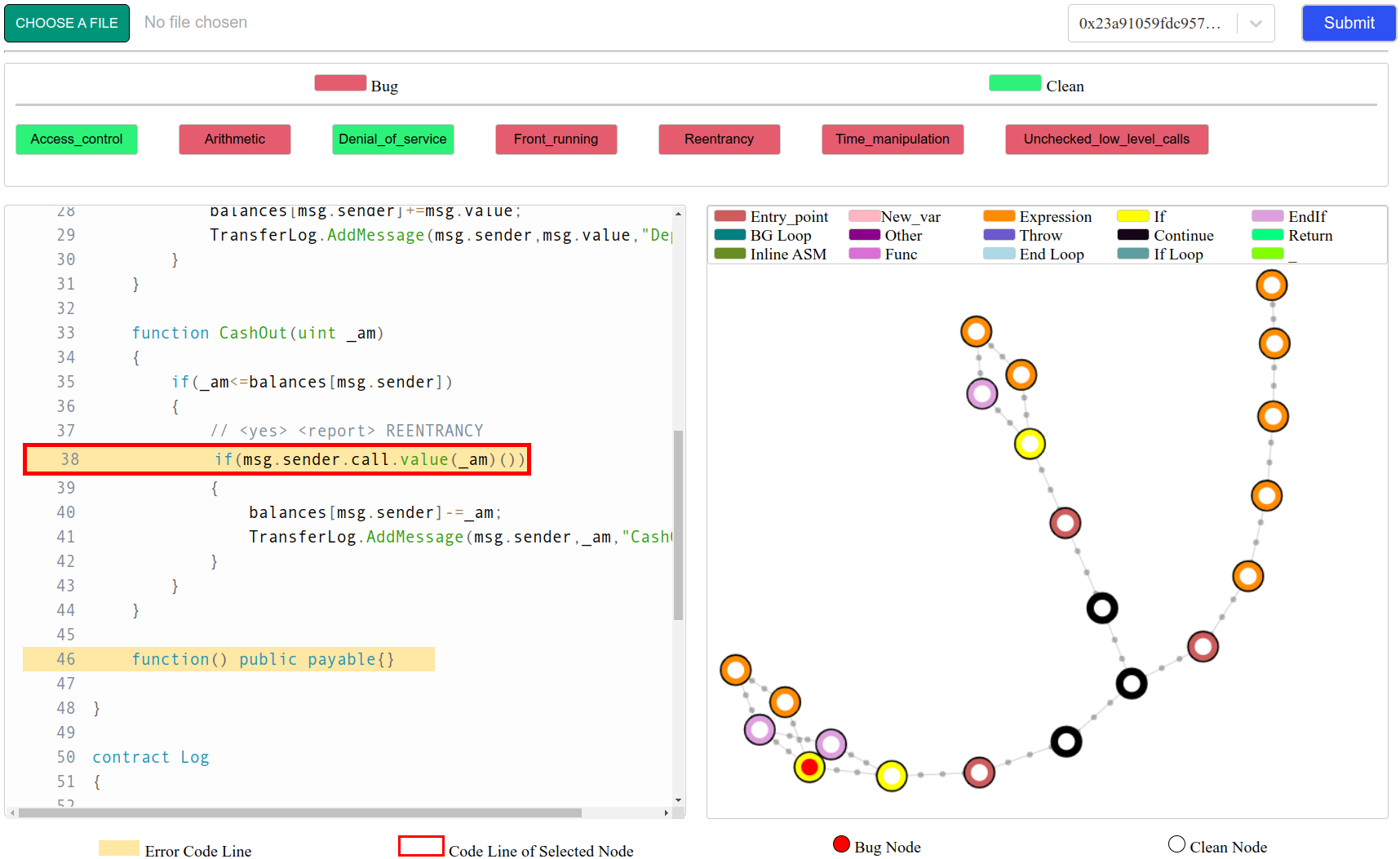
- When the process finished:
- Red Button: Smart contract contains this type of bug.
- Green Button: Smart contract does not contain this type of bug.
- When you click a button which was result of Coaser-Grained phase, the tool would show the source code and graph of the smart contract
- Source Code
- Buggy Code Line : The line of code has the background color of yellow.
- Graph
- Red Node: Bug Node.
- White Node : Clean Node.
- Border of Node : Node Type.
- If you click a node in the graph, the lines of code equivalent to that node will be bounded by a red border.
- Bar Chart
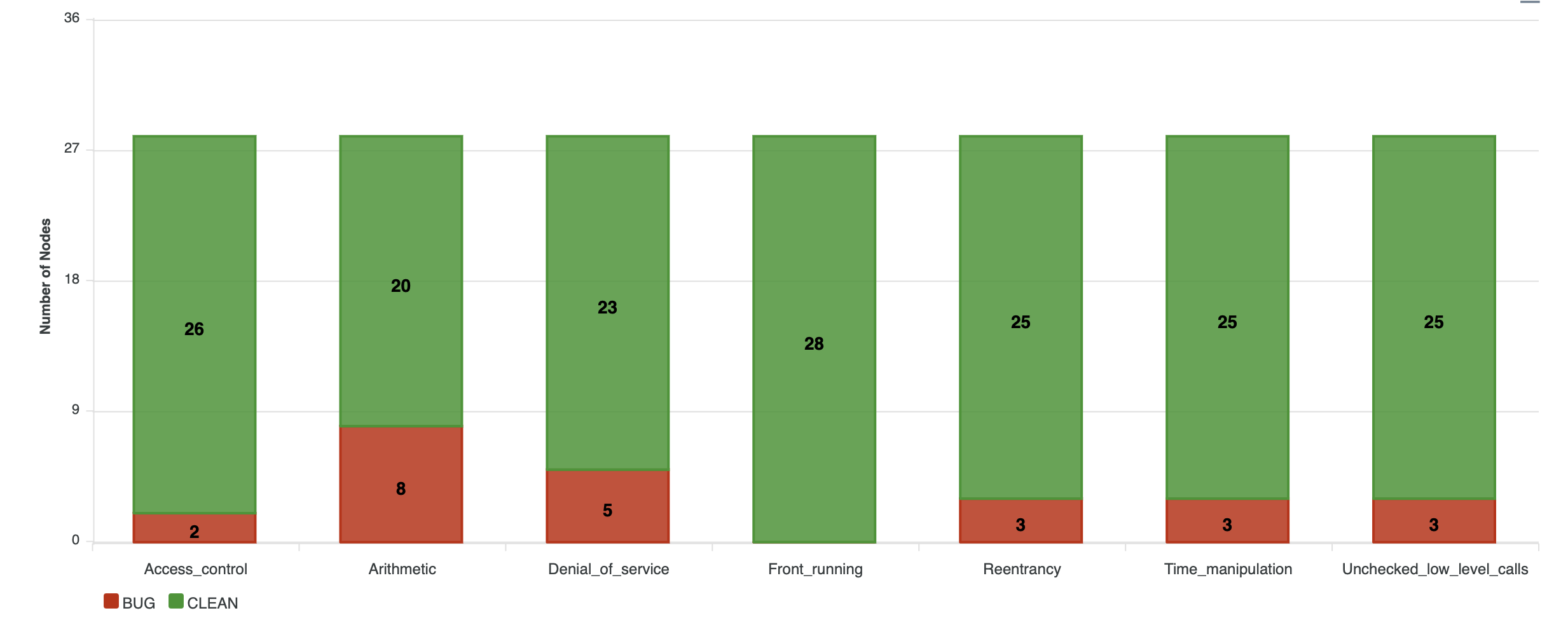
- Number of bug nodes and Number of clean nodes for each type of bug.
- Detection Time
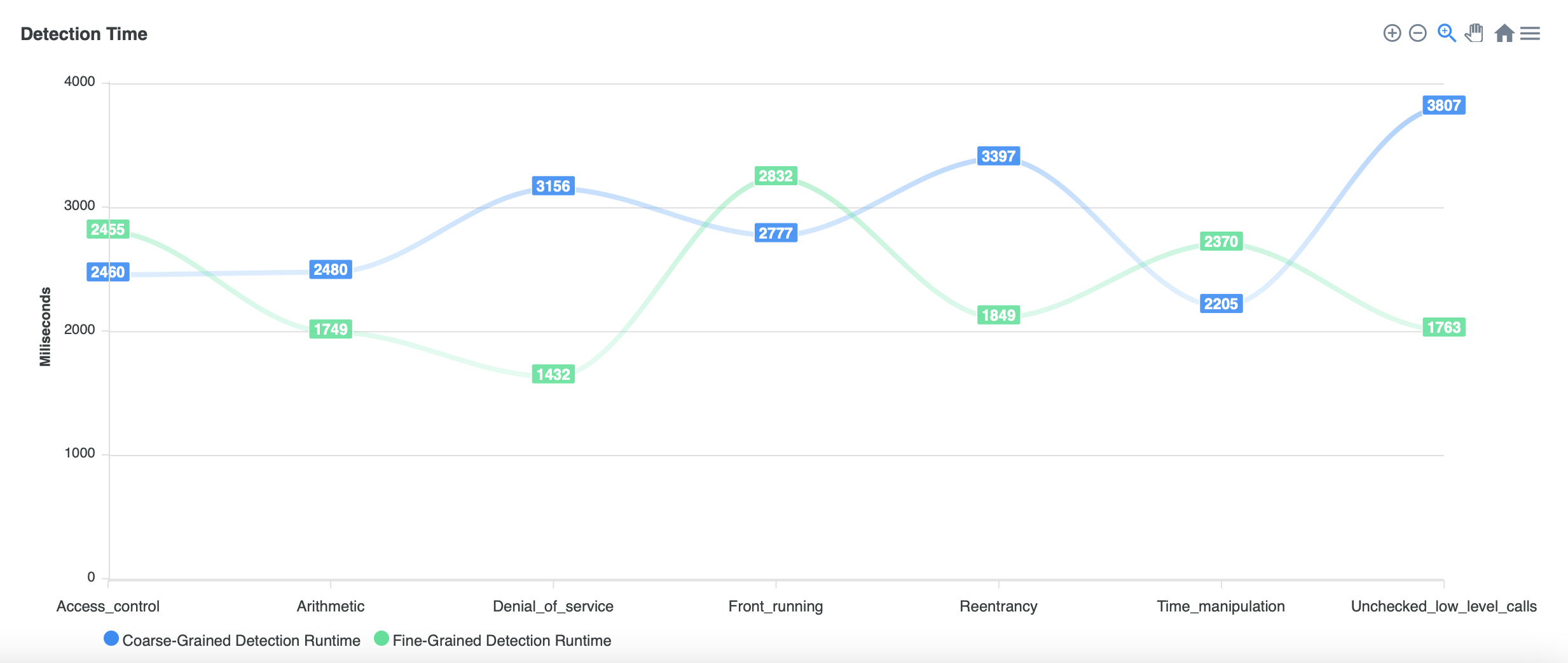
- DetectionTime for each type of bug.
- Bug Density
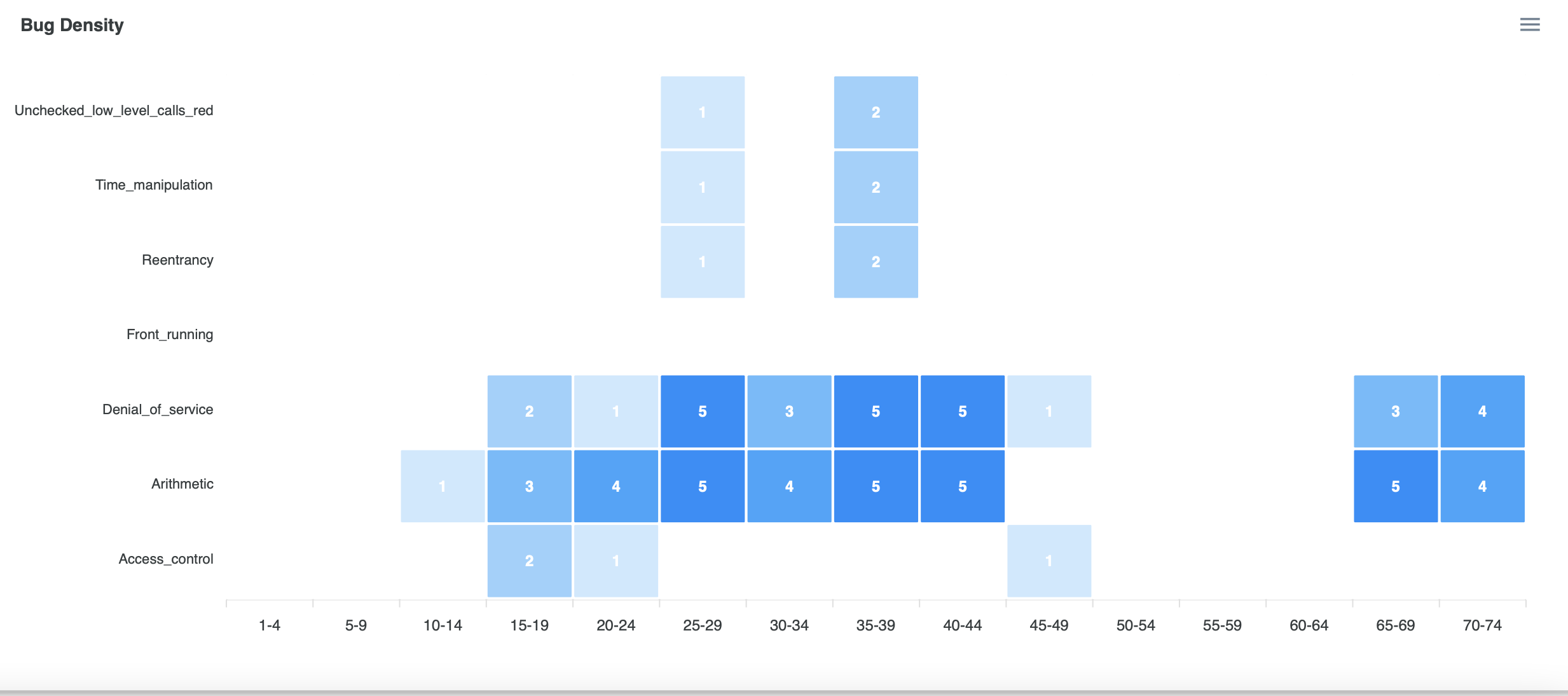
- We divided the line number which had bugs into 15 categories in order.
- The portion with darker color shows that the areas of source code have more bug lines.
- APIs documents: mandoguru.com/docs
- We also published APIs documents for user can directly request to MandoGuru services.
- There are 2 main APIs:
- Coarse-grained detection.
- Fine-grained detection.
- The document page were built based on Swagger which help you request directly.
- When making a request, you have to authorize by the public token fisrt.
- To call an API step by step, please refer to demo video.
MqQVfJ6Fq1umZnUI7ZuaycciCjxi3gM0
Please visit this link to see the demo video.
- If you want to launch our tool yourselves, please meet the prerequisites prior to follow the steps bellow:
-
We published docker image for launching backend service.
-
Pull docker image from docker hub.
docker pull nguyenminh1807/sco:latest
- Run container and map port 5555:xxxx to any port you want to public (we used the same port over here).
docker run -it -d --rm --name sco_app -p 5555:5555 nguyenminh1807/sco:latest
- You need to navigate to frontend directory first.
cd sco_frontend
- Install required package with legacy peer dependencies option.
npm install --legacy-peer-deps
- Launch app from local.
npm start