| page_type | languages | products | description | urlFragment | ||
|---|---|---|---|---|---|---|
sample |
|
|
Script to run against Azure MFA NPS Extension servers to perform some basic checks to detect any issues. The output will be in HTML format. |
azure-mfa-nps-extension-health-check |
Script to run against Azure MFA NPS Extension servers to perform some basic checks to detect any issues.
Here's a quick summary about each available option when the script is run:
- To isolate the cause of the issue: if it's an NPS or MFA issue (Export MFA RegKeys, Restart NPS, Test, Import RegKeys, Restart NPS)
- To check a full set of tests, when not all users can use the MFA NPS Extension (Testing Access to Azure/Create HTML Report)
- To check a specific set of tests, when a specific user can't use the MFA NPS Extension (Test MFA for specific UPN)
- To collect logs to contact Microsoft support (Enable Logging/Restart NPS/Gather Logs). The output will be in HTML format.
The script needs to be run as a user with local admin privilege on the server, and will ask for global admin on the tenant to be run against.
To download and run the MFA_NPS_Troubleshooter.ps1 script from this GitHub repo, click Browse Code on top of this webpage, and from the green Code pull-down menu, select Download Zip.
When you run the script, select an option that meets your goal.
Based on each option selection, performs the following test against MFA Extension Server:
Option 1:
- Export the current registry keys for NPS Extension configuration
- Restarts NPS Extension with empty registry keys
- User performs simulation of current situation being checked
- Import to current registry keys for NPS Extension configuration from previous backed up information
- Restarts NPS Extension with configured registry keys
Option 2:
Based on each option selection, performs the following test against Azure cloud environment
Suboption 1:
- Check accessibility to https://login.microsoftonline.com
- Check accessibility to https://adnotifications.windowsazure.com
- Check accessibility to https://strongauthenticationservice.auth.microsoft.com
Suboption 2:
- Check accessibility to https://login.microsoftonline.us
- Check accessibility to https://adnotifications.windowsazure.us
- Check accessibility to https://strongauthenticationservice.auth.microsoft.us
Suboption 3:
- Check accessibility to https://login.chinacloudapi.cn
- Check accessibility to https://adnotifications.windowsazure.cn
- Check accessibility to https://strongauthenticationservice.auth.microsoft.cn
Common:
- Check accessibility to https://credentials.azure.com
- Check MFA version.
- Check if the NPS Service is Running.
- Check if the SPN for Azure MFA Exists and is Enabled.
- Check if Authorization and Extension registry keys have the right values.
- Check other Azure MFA related registry keys have the right values.
- Check if there is a valid certificated matched with the certificates stored in Azure AD.
Option 3:
- Check if user account Exists in Azure AD
- Check if use is synched to Azure AD from On premises
- Check if user is blocked on Azure AD or not
- Check if user status is healthy in Azure AD
- Check if user has completed MFA Proofup in Azure AD
- Check if user has a valid license for MFA
- Check user Dial-In status on local AD
Option 4:
- Enable logging for NPS Extension feature and dependent services
- Restart NPS Extension
- User performs simulation of current situation being checked
- When simulation ends, it will generate a ZIP file with all log files required
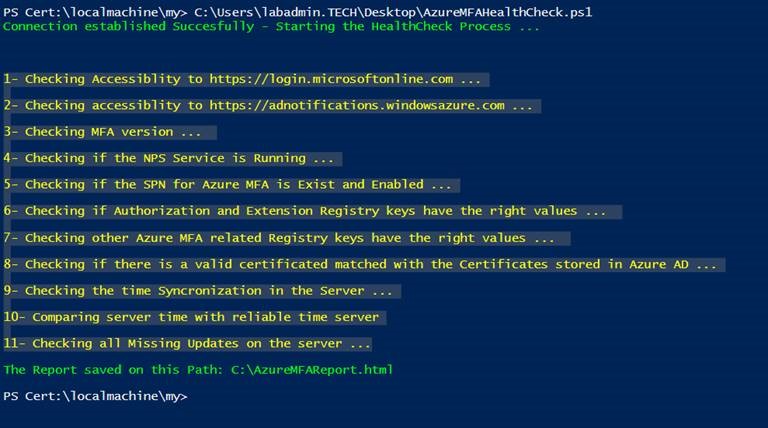
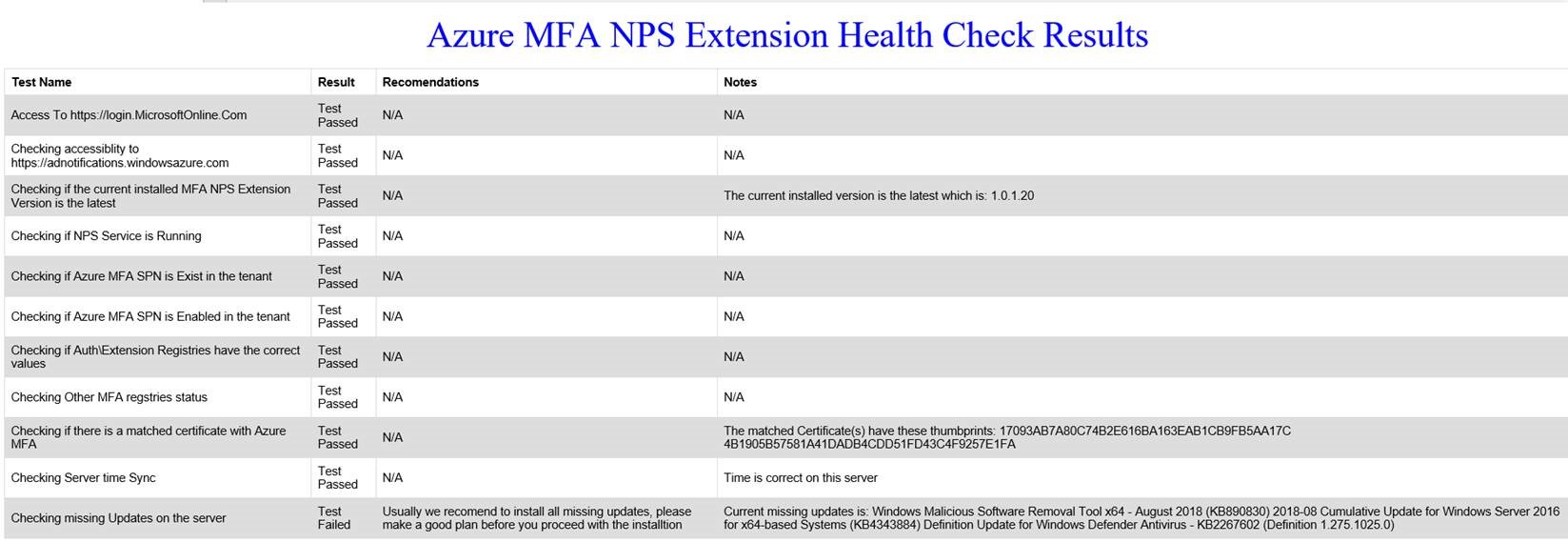
In PowerShell console it will only display the test name, then it will convert the result to HTML file located at C:\AzureMFAReport.html.
Example console output:
Example HTML output:
No, but the script will suggest some remediation steps, as shown in the previous example HTML output.
No, here I need your help! Feel free to share your ideas with me and we can work together to improve it. Open a GitHub issue or pull request in this repo.
No, help to make it better! Open a GitHub pull request in this repo with your improvements.
This project welcomes contributions and suggestions. Most contributions require you to agree to a Contributor License Agreement (CLA) declaring that you have the right to, and actually do, grant us the rights to use your contribution. For details, visit https://cla.opensource.microsoft.com.
When you submit a pull request, a CLA bot will automatically determine whether you need to provide a CLA and decorate the PR appropriately (e.g., status check, comment). Simply follow the instructions provided by the bot. You will only need to do this once across all repos using our CLA.
This project has adopted the Microsoft Open Source Code of Conduct. For more information see the Code of Conduct FAQ or contact opencode@microsoft.com with any additional questions or comments.