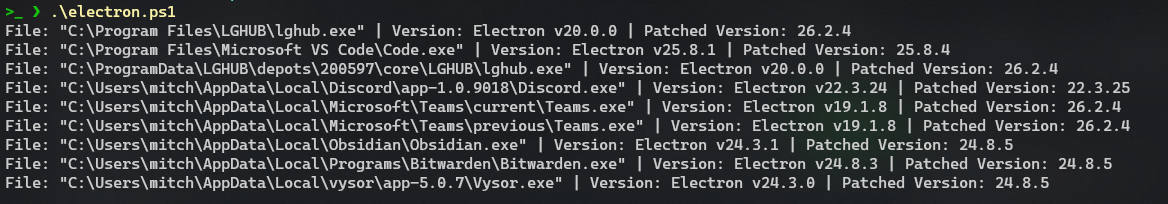
This PowerShell script downloads Sysinternals Strings, recursively searches for strings within all .exe files across all drives, and compares the Electron version found with known patched versions below to determine vulnerability to CVE-2023-4863 / CVE-2023-5129.
Note:
The script downloads
strings.ziptoC:\Windows\Tempand extractsstrings.exefrom it. The user running the script needs permissions for this folder. If you're using an RMM tool, there should be no issues since it runs as SYSTEM or an admin account. But if you're running it locally, you might need to open the folder in Explorer to grant necessary permissions..
The script generates a list each time it discovers a vulnerable file, including the found file, its vulnerable version, and the corresponding updated version that addresses the issue.