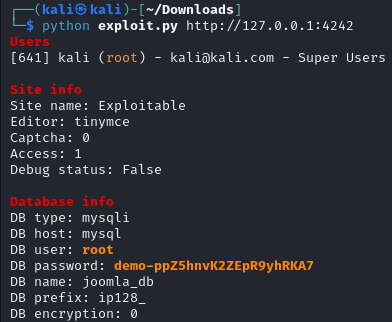
This Python implementation serves an educational purpose by illustrating the exploitation of CVE-2023-23752. The code offers insight into how the vulnerability can be exploited.
This project showcases a Python implementation aimed at demonstrating the CVE 2023 23752 Information Disclosure Vulnerability. It includes a docker-compose.yml file to streamline setup and execution, making it particularly useful for efficiently demonstrating or testing the Proof of Concept.
To properly run the exploit.py file, download the project files and execute the following code to install the necessary dependencies:
pip install -r requirements.txt
- termcolor version 1.1.0
- requests version 2.31.0
Utilizing the exploit.py file is simple—just execute it with the provided URL. Moreover, running it without color can be achieved by using the --no-color option.
python exploit.py http://target_url.com:port
Explain how others can contribute to your project. Whether it's bug reporting, feature requests, or code contributions, outline guidelines for potential contributors.
- Fork the repository
- Create a new branch (
git checkout -b feature) - Make changes, commit them, and push to the branch (
git push origin feature) - Create a pull request
v4.2.7
docker-compose up --build
Then reach the installation page http://127.0.0.1:4242/installation/index.php.
Complete the installation (db credentials are root / MYSQL_ROOT_PASSWORD (cf. docker-compose.yml) and host is mysql not localhost).
Warning: This setup is not suitable for production use.
- Noraj(Alexandre Zanni): This project drew inspiration from Noraj's implementation in Ruby, which served as a foundational reference for this project.
- Hacktricks: A lot of information about the possibilities of this vulnerability were researched in this website.
This project is licensed under the MIT License.
This software is intended for knowledge and awareness purposes only. I do not endorse, encourage, or support any illegal or unauthorized use of this software. Any actions taken by users with this software that violate the law or infringe upon the rights of others are strictly prohibited. Users are solely responsible for ensuring that their use of this software complies with all applicable laws and regulations. I shall not be held liable for any misuse or illegal activities carried out with this software.