Cryptography is the practise and study of techniques for secure communication in the presence of third parties The basic concept is that there are cases when we want to make sure a given message is read by the sender and the receiver exclusively.
There are several cases where cryptography can prove to be very important.
For example, during the second world war, the allies wanted to make sure that the messages can not be read by Germans So the Germans wanted to make sure that the messages can not be read by the allies So in these cases,both the allies and the Germans use cryptography in order to make sure that the message is read by the sender and the receiver exclusively.
Of course, it is important when transferring funds electronically It is quite intuitive that in these cases,usernames and passwords must be encrypted because we would like to make sure that the passwords are not going to be seen any third parties.
Cryptocurrency and blockchain are quite new technologies, but there are rely heavily on cryptographhy as well Or, for example, storing users' information in a database such as credit card passwords. Again, we have to encrypt these information in order to make sure that these information are not going to be public for anyone.
Some Important Terms
👉PLAINTEXT : It is the message thats we want to encrypt.
👉CIPHERTEXT : The encryted message.
👉ENCRYPTION :The process of encoding a given message in a way that only the authorized people can access it.
👉DECRYPTION:The process of decoding the message.
👉KEY:This is the sequences that is needed for both encryption and decryptions.
Basically encryption and decryption are mathematical functions
Encryption: cipher_text=(plain_text,key);Decryption: plain_text=f-1(cipher_text,key);
Symmetric Encryption
PRIVATE KEY CRYPTOGRAPHY
This type of cryptography uses just a single key. So the same key is used both for encryption and decryption as well this is why it also called symmetric encryption
⚠THE MAIN PROBLEM IS THAT THE KEY MUST BE EXCHANGED⚠Asymmetric Encryption:
PUBLIC KEY CRYPTOGRAPHY
This type of cryptography uses a public key and a private key as well. for this is why it is also called asymmetric encryption 👉We should keep the private key secret 👉if Durjoy wants to send a message to Rupkotha then Durjoy will encrypt it with Rupkotha's public key and Rupkotha can decrypt the message with its private key
Symmentric Cryptography Algorithms
👉 [Caesar-Cipher](https://en.wikipedia.org/wiki/Caesar_cipher)
Caesar-Cipher
Encryption
Formula behind the scane
En(x)=(x+n) mod 26
👉We have to consider all the characters in the plaintext👉E(x) is the encrypted letter of the original x letter
👉We have to shift the given letter with n (where n is the key)
⚠Why to use 26 ?
✅The size of alphabet is 27 which means there are 26 letter in the english alphabet
✅We want to make sure the encrypted letter is within the range[0,SIZE_ALPHABET-1] so this is why to use mod 26 here.
Decryption
Formula behind the scene
En(x)=(x-n) mod 26
👉 We have to consider all the characters in the ciphertext
👉 D(x) is the decrypted letter(x is the letter in the ciphertext)
👉 We have to shift the given letter with -n (where n is the key)
Cracking Caesar-cipher
The main problem with Caesar-cipher is that there are few possible key values ~the keyspace is small: it contains 26 keys only!!
NUMBER OF KEYS=SIZE OF THE ALPHABET
👉 there are 26 letters in the alphabet so the number of possible keys is as well
👉 intuition:let's use Caesar-encryption several times (brute-force approach)
CAESAR-CIPHER WILL NOT BE MORE SECURE IF WE REPEAT THE OPERATION
>For example: using Caesar-encryption with key 2 and then with key 3 is the same as using key 5 In our implementation we use 26 letters as the english alphabet We Can use brute force attack in order to find the key for the Caesar-cipher
There are 2 types of approaches to crack Caesar-cipher
1. Brute-force attack:because the number of possible key is 26 thats why we can consider all these cases (so check all the possible key values)
👉 we use all the posssible key values within the range[0,SIZE_ALPHABET-1] and check whether the decrypted message makes sense or not ~it may be important to be able to detect english language
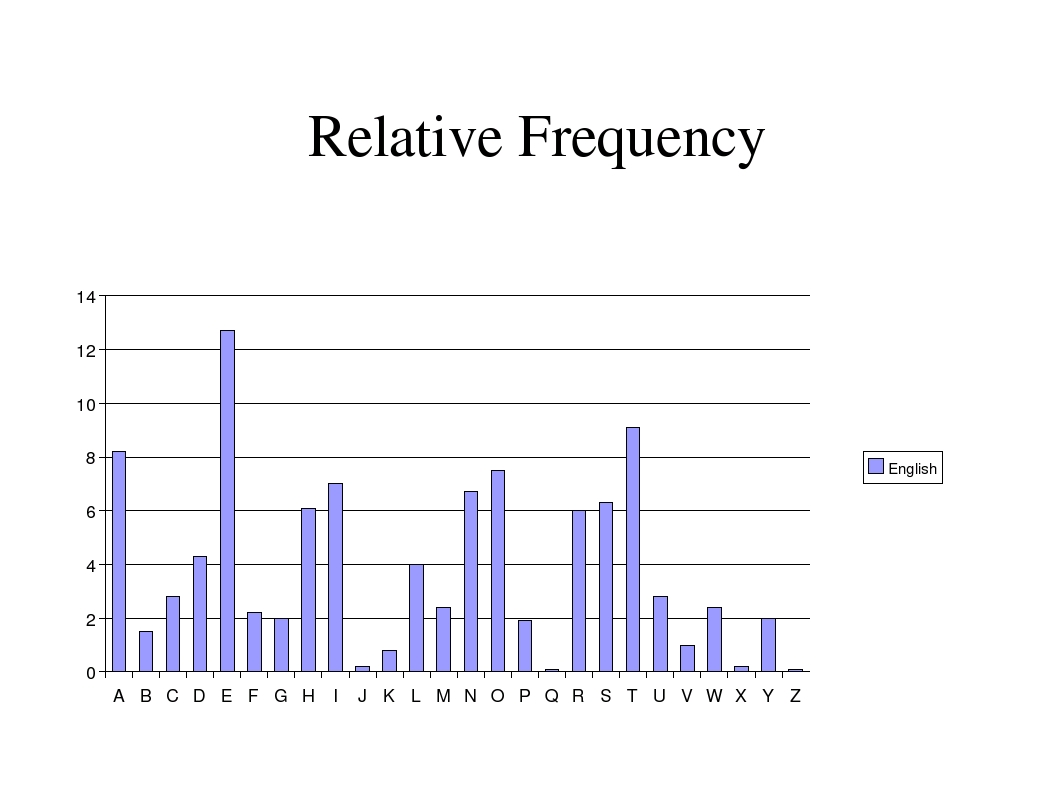
2. Frequency-analysis: we can analyse the frequency distribution of the letters For example in an english language text some letters are more frequent then others(E,A,O,I and T)
👉 we can analyse the ciphertext and based on the most frequent letter in the ciphertext we can predict the key(so the number of shift)
Relative frequency distribution of letters in an english text
Frequency analysis cracking
We are able to crack Caesar-cipher because some imformation is revealed about the cryptosystem1. calculate the relative frequency distribution of the ciphertext's letters
2. get the most frequent letter in the ciphertext (or the second because the most frequent one may be white-spaces)
3. we can get the key based on a simple formula
key=value of ciphertext's most frequent letter-value of E
THIS IS CALLED INFORMATION LEAKING!!!
👉Because of the information leaking we can analyise cipertexts and crack the given cipher
👉Information leaking can be avoid by using random numbers this is why one-time-pad(OTP) came to be