- AzurePolicyWorkshop
- Agenda
- Setup the local tools & environment
- Variables
- Labs
- Deployment of Azure resources - Bicep
- Deployment of Azure Built-In Policies - Bicep
- Deployment of Azure Custom Policies - JSON
- Testing Azure Policies - Bicep
- Deployment of Azure Resource Exemptions - Bicep
- Testing Azure Resource Exemptions - Bicep
- Deployment of Guest Config VM Extension - JSON
- Deployment of Guest Config Policies - JSON
-
Tooling
We install all the tools needed for successful policy configuration & deployment
-
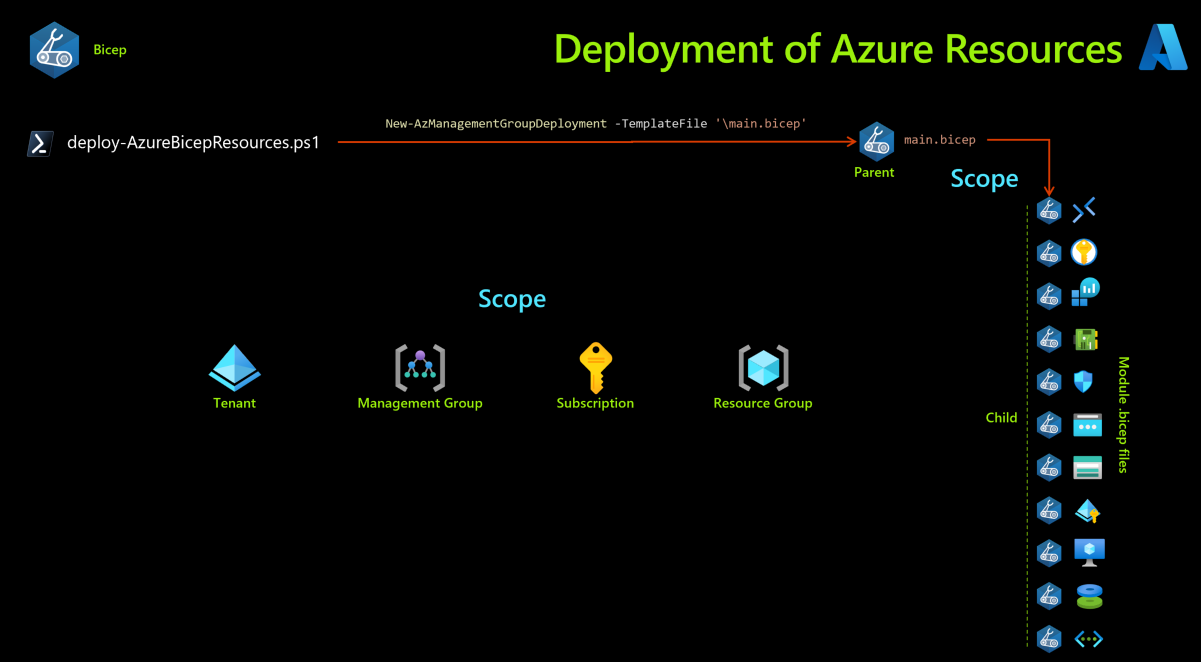
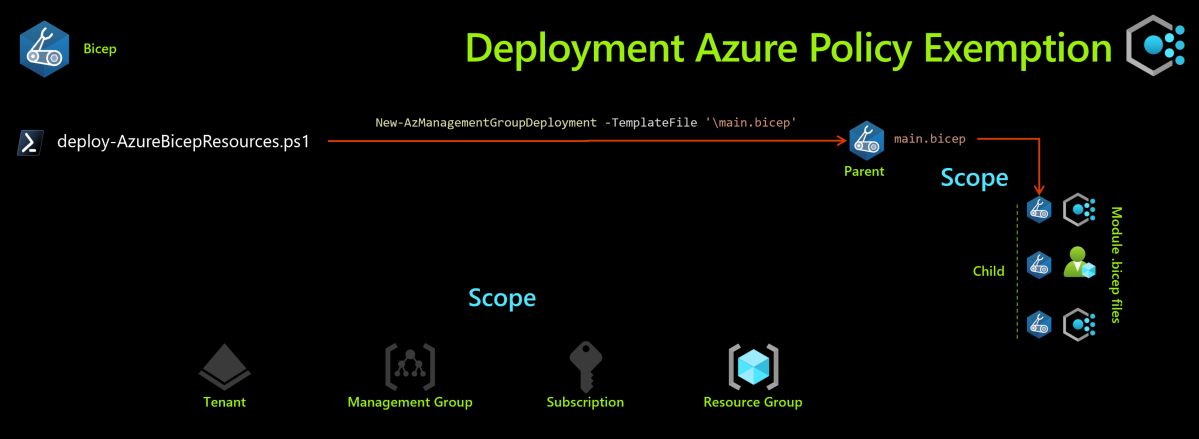
Scope
We look at two types of scope here. Deployment scope and Policy scope
-
Deployment of test Azure resources (Lab)
In this lab, we use Bicep templates to deploy test Azure resources in order to test Azure Policy against. We use pre-written Bicep templates in order to deploy what we need
- This is a lab exercise
-
Effects
Each policy definition in Azure Policy has a single effect. That effect determines what happens when the policy rule is evaluated to match. The effects behave differently if they are for a new resource, an updated resource, or an existing resource.
-
Policy Functions
All resource Manager template functions are available to use within a policy rule, except certain functions and user-defined functions.
-
Policy Definitions
Policy Definitions define a Policy. We look at both options for built-in Policy Definitions and Custom Policy Definitions. We understand the best practice of where custom Policy Definitions live in an Azure subscription and the structure of Policy Definitions.
-
Policy Initiatives
A Policy Initiatives are the new name for Policy Set Definitions and is like a group of Policy Definitions.
-
Policy Assignments
We can assign both Policy Initiatives and Policy Definitions to scope, either a scope comprising of a Management Group, subscription or resource group
-
Deployment of built-in Azure Policy Assignments (Lab)
In this lab, we use BICEP templates to deploy built-in Azure policy definitions, then assign these definitions. This demonstrates how to govern the Azure resources
As some policies are either DeployIfNotExists or Modify, we also assign some built-in roles to the policy service principals
This is a lab exercise
-
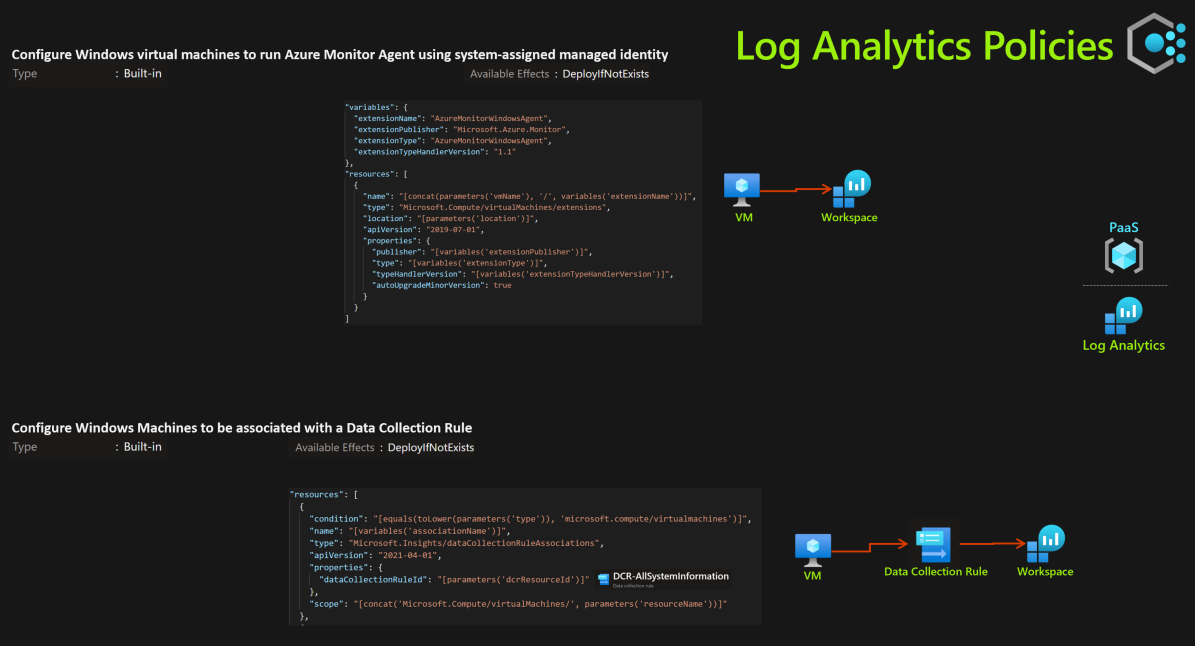
Configure Windows machines to run Azure Monitor Agent and associate them to a Data Collection Rule
Policy Type Initiative Assignment Scope Resource Group Definitions Configure Windows Machines to be associated with a Data Collection Rule Configure Windows virtual machines to run Azure Monitor Agent using system-assigned managed identity
-
Allowed_Locations
Policy Type Definition Assignment Scope Subscription
-
-
Deployment of custom Azure Policies (Lab)
In this lab, we use JSON templates to deploy custom Azure policy definitions, then assign these definitions. This demonstrates how to govern the Azure resources
As some policies are either DeployIfNotExists or Modify, we also assign some built-in roles to the policy service principals
This is a lab exercise
-
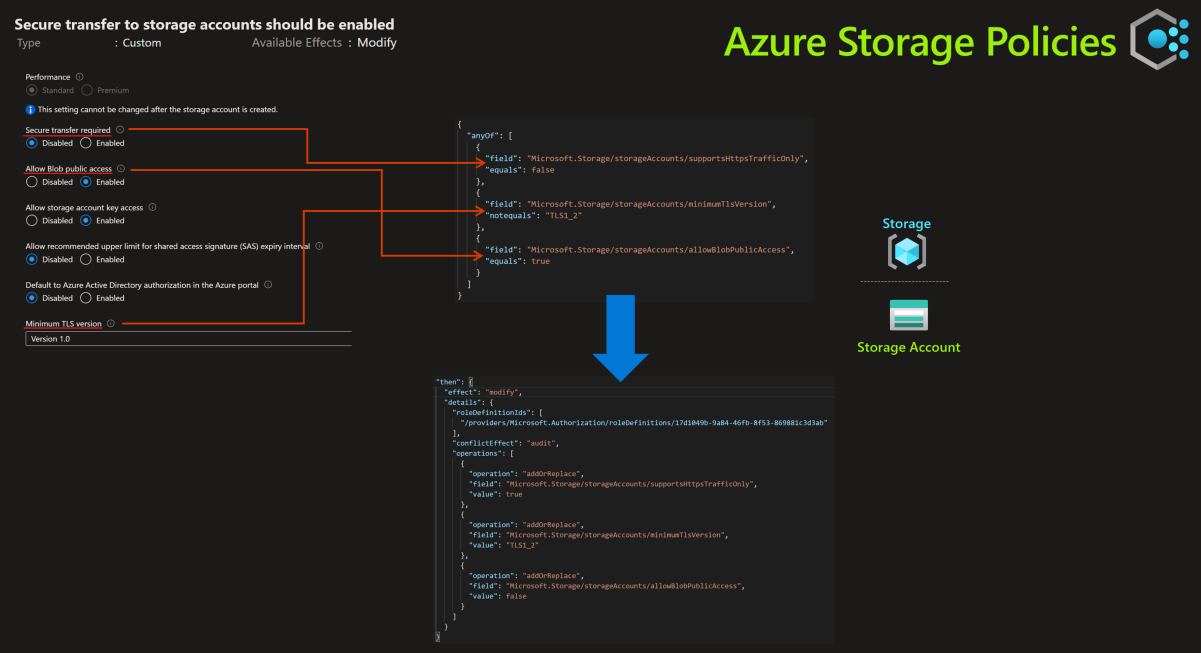
Secure transfer to storage accounts should be enabled
Policy Type Definition Assignment Scope Subscription
-
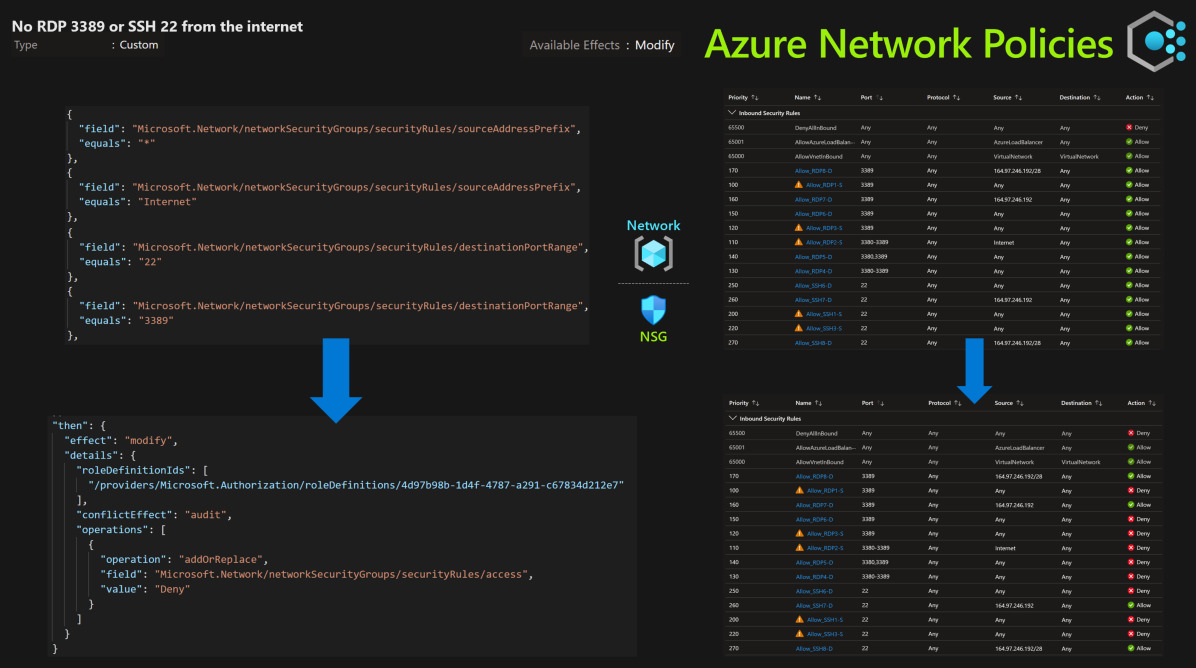
No RDP 3389 or SSH 22 from the internet
Policy Type Definition Assignment Scope Subscription
-
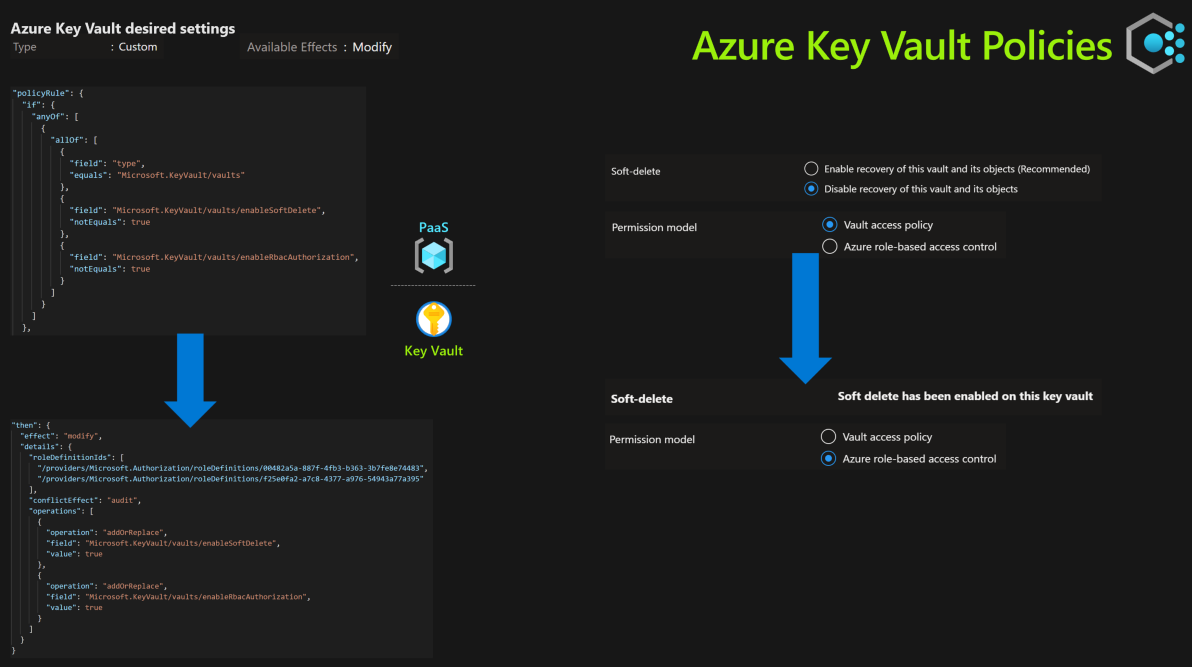
Azure KeyVault desired settings
Policy Type Definition Assignment Scope Subscription
-
Deny deployment of a custom role which has the same permissions as the built-in owner role
Policy Type Definition Assignment Scope Subscription -
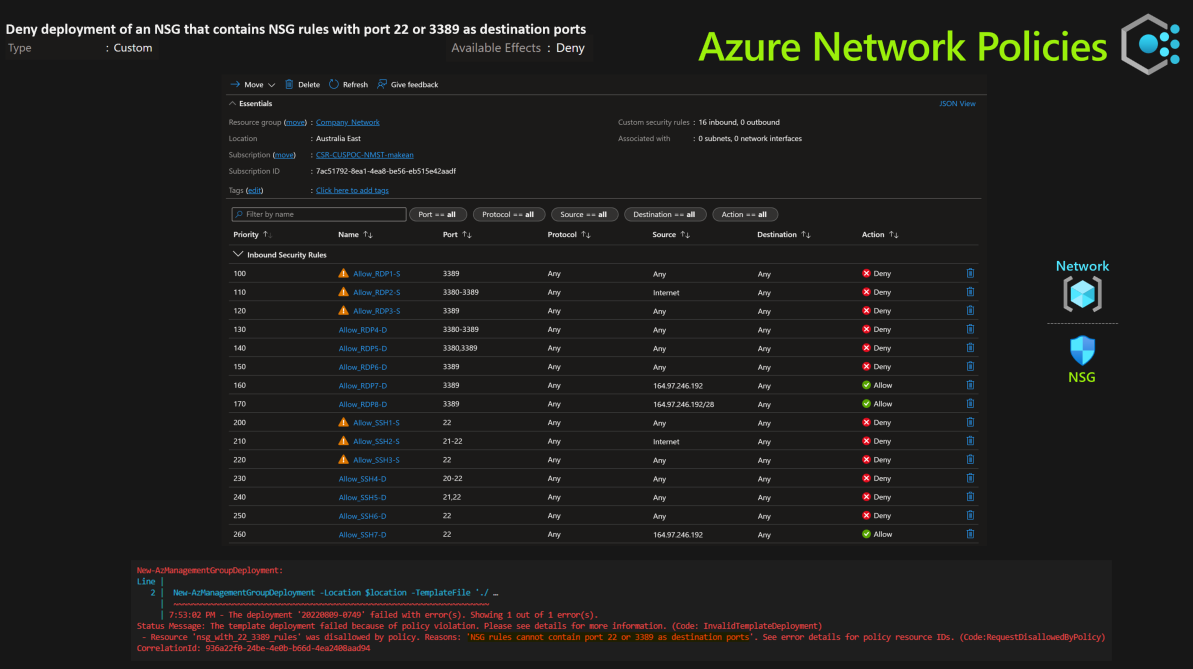
Deny deployment of an NSG that contains NSG rules with port 22 or 3389 as destination ports
Policy Type Definition Assignment Scope Subscription
-
-
Testing Azure Policies (Lab)
- We test the Azure Policies we have deployed in the previous lab exercise
- For this test we will use Bicep to deploy NSGs with ports opened from the internet on port 3389, 322 443 so see the effect that Azure Policy has on the resources being deployed.
-
Exemptions
The Azure Policy exemptions feature is used to exempt a resource hierarchy or an individual resource from evaluation of initiatives or definitions. Resources that are exempt count toward overall compliance, but can't be evaluated or have a temporary waiver.
-
Exemptions (Lab)
- In this lab we deploy a policy exemption, to ensure that a particular resource group Company_Open is exempt from the Allowed_Locations Policy.
- We also test deploy some simple Azure resources using BICEP to test this Policy Exemption and to watch the effects of the exemption.
- We deploy public IP addresses in different Azure regions to both Company_Network and Company_Open resource groups to watch the effects of the exemption.
-
Compliance
Look at compliance Vs non-compliance and the Policy compliance checker.
-
Remediation
Looking at Remediation, remediation of non-compliant resources. Resources that are non-compliant to policies with deployIfNotExists or modify effects can be put into a compliant state through Remediation.
-
Remediation (Lab)
In this lab we use the Azure portal and work with the previously deployed Azure test resources and Azure policies to remediate non-compliant resources.
-
Managed Identities
We understand what are managed identities and how that are used in conjunction with the two effects, deployIfNotExists or Modify.
-
Regulatory Compliance in Azure Policy
Regulatory Compliance in Azure Policy provides built-in initiative definitions to view a list of the controls and compliance domains based on responsibility (Customer, Microsoft, Shared).
-
Policy Testing
We look at ways to test Azure Policy without initiating the policy effect or triggering entries in the Azure Activity log.
-
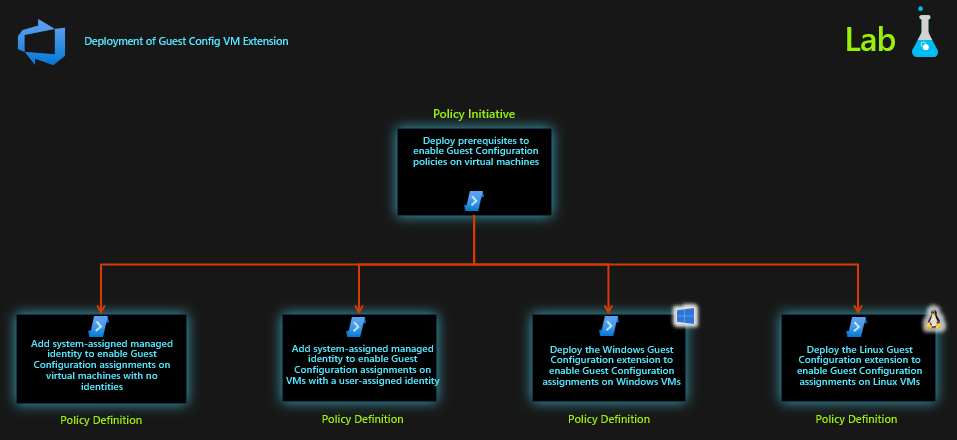
Guest Configuration/Azure Automanage Machine Configuration (Lab)
There are two labs here, one is for the Guest Config VM extension deployment, the other one is for the Guest Config Policies themselves.
We deploy a Policy Initiative that installs the Guest Configuration extension on all Windows and Linux virtual machines in a Resource Group.
- Deploy prerequisites to enable Guest Configuration policies on virtual machines
Policy Type Initiative Assignment Scope Resource Group -
Guest Configuration/Azure Automanage Machine Configuration
Azure Policy's guest configuration feature provides native capability to audit or configure operating system settings as code, both for machines running in Azure and hybrid Arc-enabled machines. The feature can be used directly per-machine, or at-scale orchestrated by Azure Policy.
We run some tests on Virtual Machines running in Azure
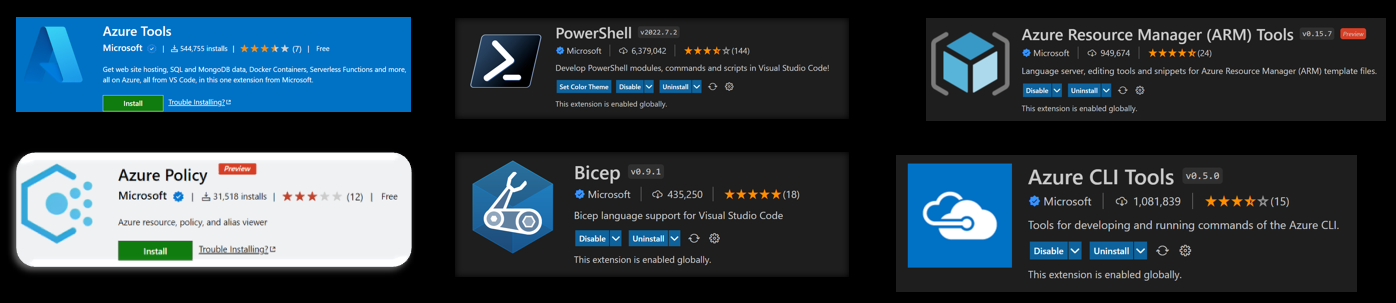
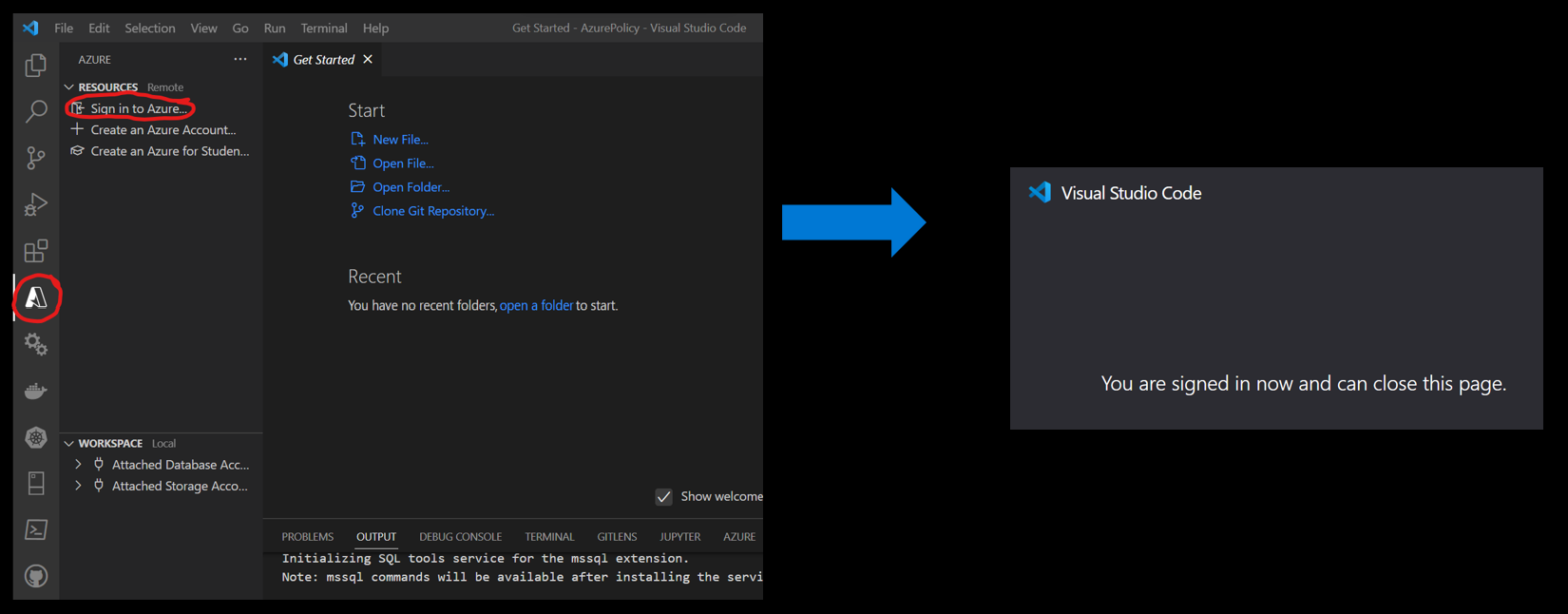
- Install all the following extensions in VS Code
Then sign into Azure.
Install PowerShell v7 on Windows if you’re a non-admin
You must have Azure CLI version 2.20.0 or later installed. Azure CLI automatically installs the Bicep CLI when a command is executed that needs it.
You can install the Bicep CLI and add it to your PATH. Or, you must manually install Bicep for any use other than Azure CLI, as this adds Bicep to the PATH for you.
Supported OS’s are Linux, MacOS, Windows
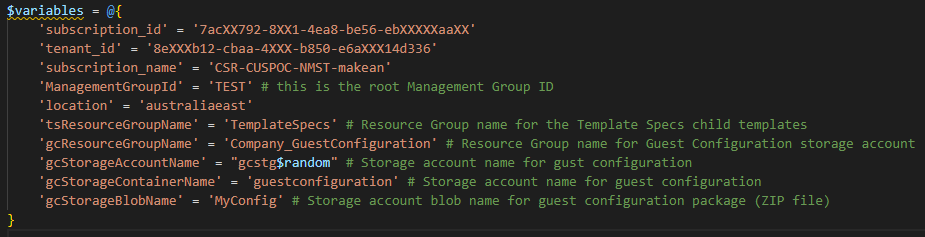
The variables to use in all the files in this workshop are contained in the one single file, so you only need to enter once. You can find the variables file here.
Below are the labs in which you deploy with code. Note, one lab remediation is an interactive lab which is done in the Azure Portal.
Run the deploy-AzureBicepResources.ps1 file in the 02 Deployment of Azure resources folder.
Run the deploy-AzureBicepResources.ps1 file in the 03.1 Deployment of Azure Resource Policies (BICEP) folder.
Run the deploy-AzureBicepResources.ps1 file in the 03.2 Deployment of Azure Resource Policies (JSON) folder.
Run the deploy-AzureBicepResources.ps1 file in the 03.3 Testing Azure Policies folder.
Run the deploy-AzureBicepResources.ps1 file in the 04.1 Deployment of Azure Policy Exemption (BICEP) folder.
Run the deploy-guestConfigurationPolicies.ps1 file in the 04.2 Testing Azure Resource Exemptions (BICEP) folder.
Run the deploy-guestConfigurationPolicies.ps1 file in the 05 Deployment of Guest Config VM Extension folder.
Run the deploy-guestConfigurationPolicies.ps1 file in the 06 Deployment of Guest Config Policies folder.