Terraform module for deploying Kubernetes AWS Controllers for Kubernetes (ACK), lets you define and use AWS service resources directly from Kubernetes.
With ACK, you can take advantage of AWS managed services for your Kubernetes applications without needing to define resources outside of the cluster or run services that provide supporting capabilities like databases or message queues within the cluster.
module "ack" {
source = "git::https://github.com/DNXLabs/terraform-aws-eks-ack.git?ref=0.1.1"
enabled = true
cluster_name = module.eks_cluster.cluster_id
cluster_identity_oidc_issuer = module.eks_cluster.cluster_oidc_issuer_url
cluster_identity_oidc_issuer_arn = module.eks_cluster.oidc_provider_arn
aws_region = data.aws_region.current.name
helm_services = [
{
name = "s3"
policy_arn = "arn:aws:iam::aws:policy/AmazonS3FullAccess"
settings = {}
},
{
name = "sns"
policy_arn = "arn:aws:iam::aws:policy/AmazonSNSFullAccess"
settings = {}
},
{
name = "sfn"
policy_arn = "arn:aws:iam::aws:policy/AWSStepFunctionsFullAccess"
settings = {}
},
{
name = "elasticache"
policy_arn = "arn:aws:iam::aws:policy/AmazonElastiCacheFullAccess"
settings = {}
},
{
name = "ecr"
policy_arn = "arn:aws:iam::aws:policy/AdministratorAccess"
settings = {}
},
{
name = "dynamodb"
policy_arn = "arn:aws:iam::aws:policy/AmazonDynamoDBFullAccess"
settings = {}
},
{
name = "apigatewayv2"
policy_arn = "arn:aws:iam::aws:policy/AmazonAPIGatewayAdministrator"
settings = {}
}
]
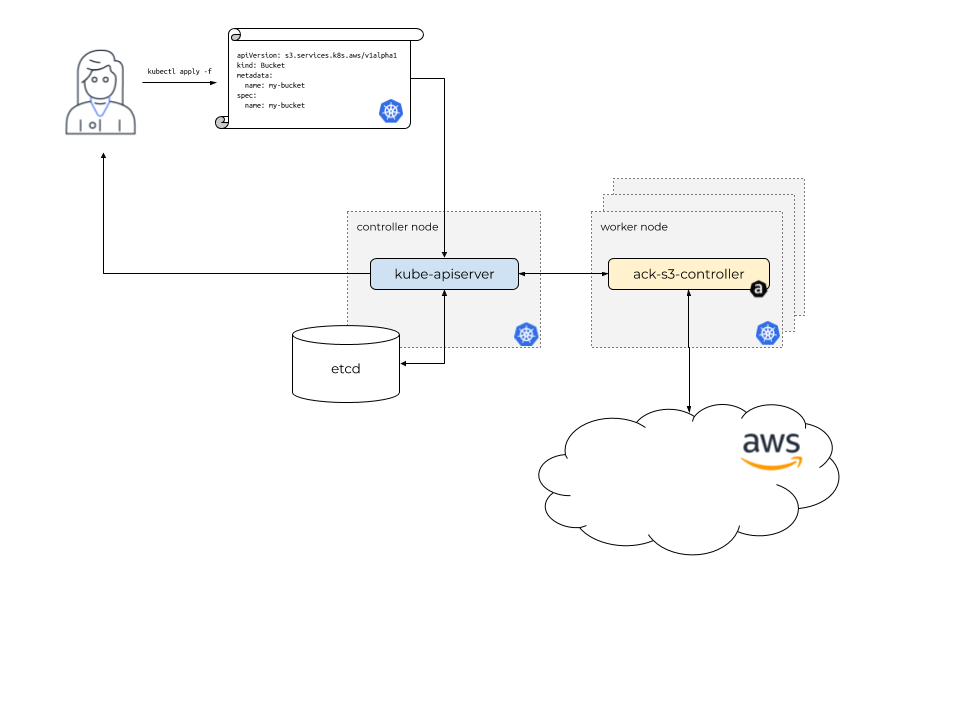
}ACK is a collection of Kubernetes Custom Resource Definitions (CRDs) and controllers which work together to extend the Kubernetes API and create AWS resources on your cluster’s behalf.
ACK comprises a set of Kubernetes custom controllers. Each controller manages custom resources representing API resources of a single AWS service API. For example, the ACK service controller for AWS Simple Storage Service (S3) manages custom resources that represent AWS S3 buckets.
Instead of logging into the AWS console or using the aws CLI tool to interact with the AWS service API, Kubernetes users can install a controller for an AWS service and then create, update, read and delete AWS resources using the Kubernetes API.
This means they can use the Kubernetes API and configuration language to fully describe both their containerized applications, using Kubernetes resources like Deployment and Service, as well as any AWS service resources upon which those applications depend.
apiVersion: s3.services.k8s.aws/v1alpha1
kind: Bucket
metadata:
name: "<redact>"
namespace: default
spec:
name: "<redact>"apiVersion: "ecr.services.k8s.aws/v1alpha1"
kind: Repository
metadata:
name: "<redact>"
spec:
repositoryName: <redact>
encryptionConfiguration:
encryptionType: AES256
tags:
- key: "is-encrypted"
value: "true"| Name | Version |
|---|---|
| terraform | >= 0.13 |
| aws | >= 3.13, < 4.0 |
| helm | >= 1.0, < 3.0 |
| kubernetes | >= 1.10.0, < 3.0.0 |
| Name | Version |
|---|---|
| aws | >= 3.13, < 4.0 |
| helm | >= 1.0, < 3.0 |
| kubernetes | >= 1.10.0, < 3.0.0 |
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| aws_region | AWS region where services are stored. | string |
n/a | yes |
| cluster_identity_oidc_issuer | The OIDC Identity issuer for the cluster. | string |
n/a | yes |
| cluster_identity_oidc_issuer_arn | The OIDC Identity issuer ARN for the cluster that can be used to associate IAM roles with a service account. | string |
n/a | yes |
| cluster_name | The name of the cluster | string |
n/a | yes |
| create_namespace | Whether to create Kubernetes namespace with name defined by namespace. |
bool |
true |
no |
| enabled | Variable indicating whether deployment is enabled. | bool |
true |
no |
| helm_services | n/a | list(object({ |
[ |
no |
| mod_dependency | Dependence variable binds all AWS resources allocated by this module, dependent modules reference this variable. | any |
null |
no |
| namespace | Kubernetes namespace to deploy ACK Helm chart. | string |
"ack-system" |
no |
| settings | Additional settings which will be passed to the Helm chart values. | map |
{} |
no |
No output.
Module managed by DNX Solutions.
Apache 2 Licensed. See LICENSE for full details.