cf-k8s-networking
Routing and networking for Cloud Foundry running on Kubernetes.
Deploying
CF-K8s-Networking is a component of CF-for-K8s. To deploy CF-for-K8s reference the following documentation:
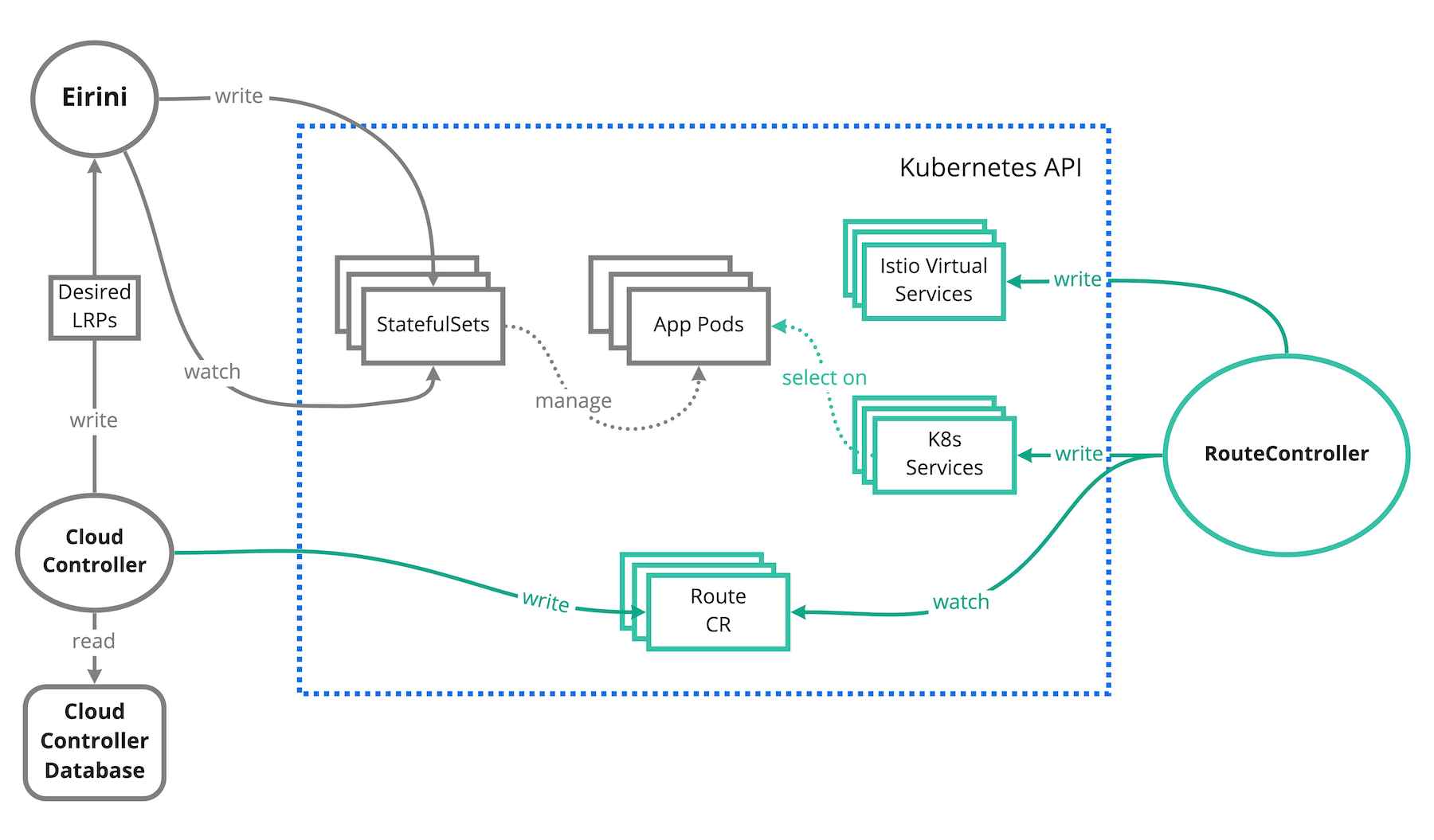
Architecture
-
RouteController: Watches the Kubernetes API for Route CRs and translates the Route CRs into Istio Virtual Service CRs and Kubernetes Services accordingly to enable routing to applications deployed by Cloud Foundry.
-
Istio: CF-K8s-Networking currently depends on Istio.
- Istio serves as both our gateway router for ingress networking, replacing the role of the Gorouters in CF for VMs, and service mesh for (eventually) container-to-container networking policy enforcement.
- We provide a manifest for installing our custom configuration for Istio, here.
- Istio provides us with security features out of the box, such as:
- Automatic Envoy sidecar injection for system components and application workloads
SidecarKubernetes resources that can limit egress traffic from workloadPods- Transparent mutual TLS (mTLS) everywhere
- (Eventually) app identity certificates using SPIFFE issued by Istio Citadel
- Istio should be treated as an "implementation detail" of the platform and our reliance on it is subject to change
- Istio config is located in cf-for-k8s and it's managed by the cf-k8s-networking team.
Contributing
For information about how to contribute, develop against our codebase, and run our various test suites, check out our Contributing guidelines.