Mobile Security Framework (MobSF)
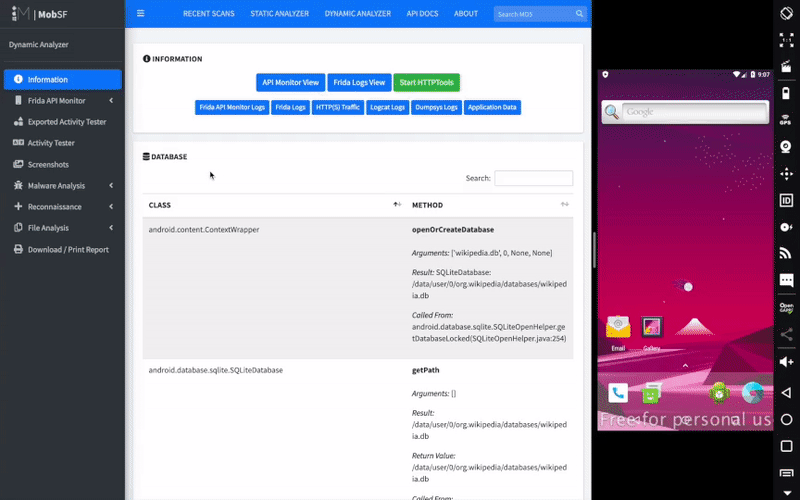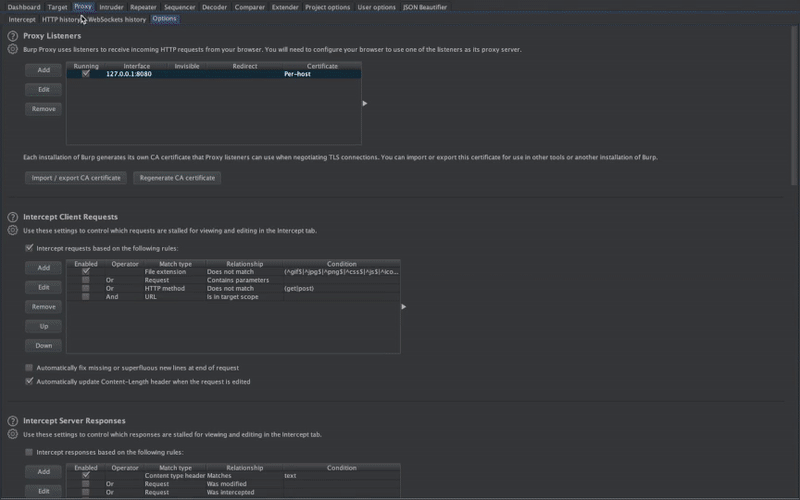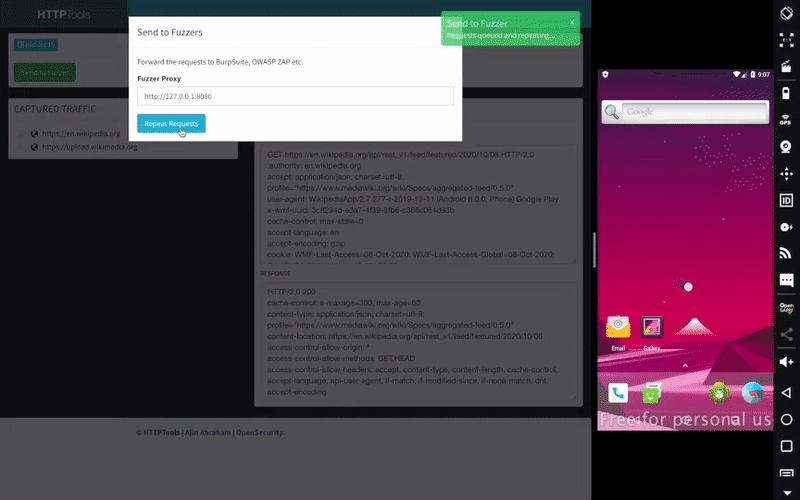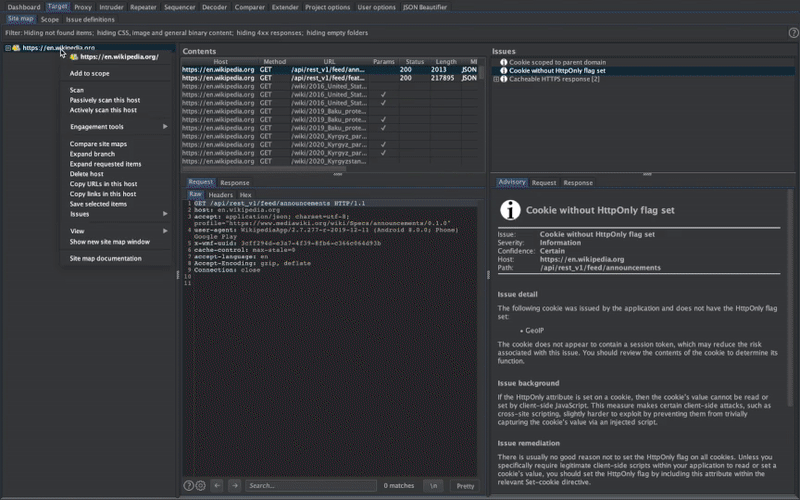
Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing static and dynamic analysis. MobSF support mobile app binaries (APK, IPA & APPX) along with zipped source code and provides REST APIs for seamless integration with your CI/CD or DevSecOps pipeline.The Dynamic Analyzer helps you to perform runtime security assessment and interactive instrumented testing.
MobSF is also bundled with Android Tamer and BlackArch
Support MobSF
Documentation
- Try MobSF Static Analyzer Online:

- Conference Presentations: Slides & Videos
- MobSF Online Course: OpSecX MAS
- What's New: See Changelog
Collaborators
Ajin Abraham  | Magaofei
| Magaofei  | Matan Dobrushin
| Matan Dobrushin  | Vincent Nadal
| Vincent Nadal 
e-Learning Courses & Certifications
 Automated Mobile Application Security Assessment with MobSF -MAS
Automated Mobile Application Security Assessment with MobSF -MAS
 Android Security Tools Expert -ATX
Android Security Tools Expert -ATX
MobSF Support
- Free Support: Free limited support, questions, help and discussions, join our Slack channel
- Enterprise Support: Priority feature requests, live support & onsite training, see
Contribution, Feature Requests & Bugs
- Read CONTRIBUTING.md before opening bugs, feature requests and pull request.
- For Project updates and announcements, follow @ajinabraham or @OpenSecurity_IN.
- Github Issues are only for tracking bugs and feature requests. Do not post support or help queries there. We have a slack channel for that.
Static Analysis - Android
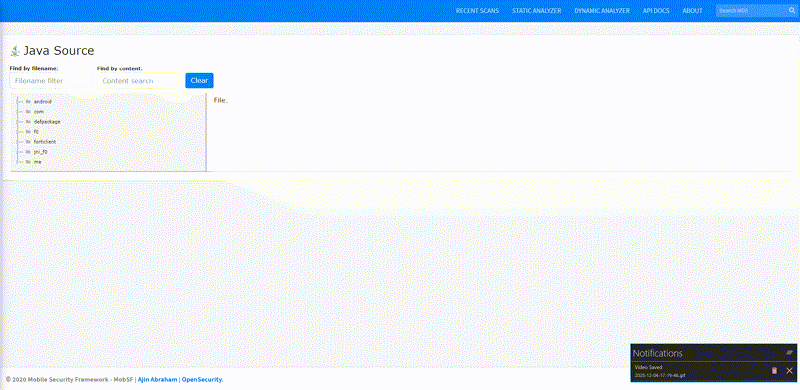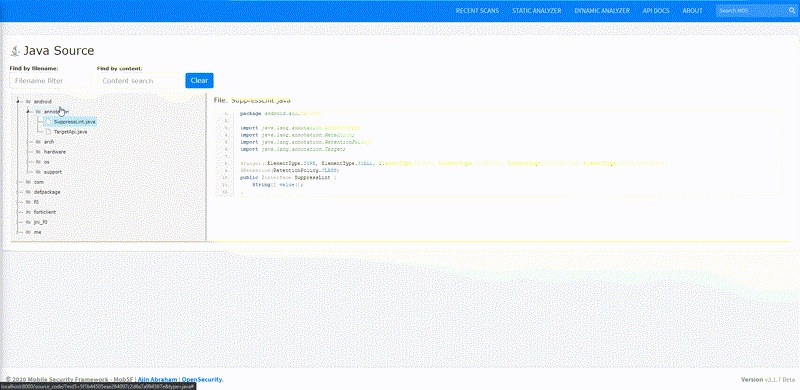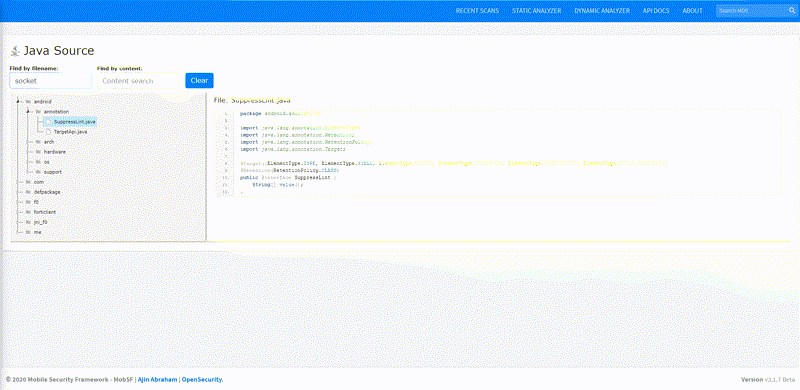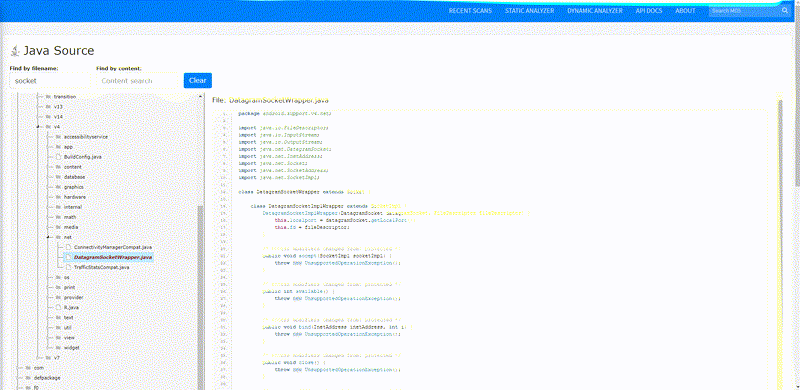
Static Analysis - Android Source Tree-view
Static Analysis - iOS
Dynamic Analysis - Android APK
Web API Viewer
Past Collaborators
Honorable Contributors
- Amrutha VC - For the new MobSF logo
- Dominik Schlecht - For the awesome work on adding Windows Phone App Static Analysis to MobSF
- Esteban - Better Android Manifest Analysis and Static Analysis Improvement.
- Matan Dobrushin - For adding Android ARM Emulator support to MobSF - Special thanks goes for cuckoo-droid
- Shuxin - Android Binary Analysis
- Abhinav Saxena - (@xandfury) - For Travis CI and Logging integration
 Netguru (@karolpiateknet, @mtbrzeski) - For iOS Swift support, Rule contributions and SAST refactoring.
Netguru (@karolpiateknet, @mtbrzeski) - For iOS Swift support, Rule contributions and SAST refactoring.- Maxime Fawe - (@Arenash13) - For Matching Strategy implementation of SAST pattern matching algorithms.
Shoutouts
- Abhinav Sejpal (@Abhinav_Sejpal) - For poking me with bugs, feature requests, and UI & UX suggestions
- Anant Srivastava (@anantshri) - For Activity Tester Idea
- Anto Joseph (@antojoseph) - For the help with SuperSU
- Bharadwaj Machiraju (@tunnelshade) - For writing pyWebProxy from scratch
- Rahul (@c0dist) - Kali Support
- MindMac - For writing Android Blue Pill
- Oscar Alfonso Diaz - (@OscarAkaElvis) - For Dockerfile contributions
- Thomas Abraham - For JS Hacks on UI
- Tim Brown (@timb_machine) - For the iOS Binary Analysis Ruleset
- Shanil Prasad (@Rajuraju14) - For improving iOS ATS Analysis