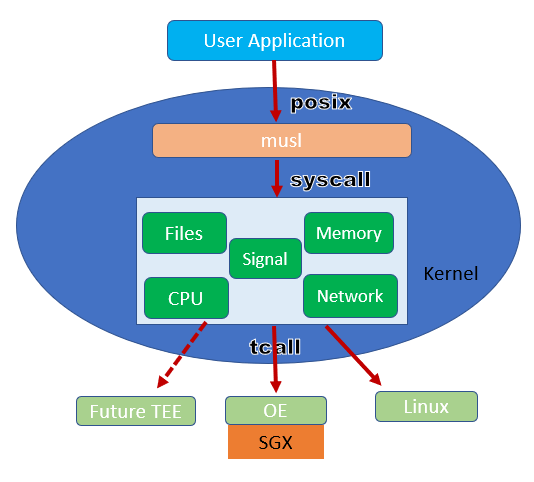
Mystikos is a set of tools for running applications in a hardware trusted execution environment (TEE). The current release supports Intel ® SGX while other TEEs may be supported in future releases. Linux is also a supported target, though only suitable for testing purposes as it provides no additional protection.
- Enable protection of application code and data while in memory through the use of HW TEEs. This should be combined with proper key management, attestation and hardware roots of trust, and encryption of data at rest and in transit to protect against other threats which are out of scope for this project.
- Lift and shift applications, either native or containerized, into TEEs with little or no modification.
- Allow users and application developers control over the makeup of the trusted computing base (TCB), ensuring that all components running inside the TEE are open source.
- Simplify re-targeting to other TEE architectures through a plugin architecture.
Mystikos consists of the following components:
- a C-runtime based on musl libc
- a "lib-os like" kernel
- the kernel-target interface (TCALL)
- a command-line interface
- some related utilities
Today, two target implementations are provided:
- The SGX target (based on the Open Enclave SDK)
- The Linux target (for verification on non-SGX platforms)
The minimalist kernel of Mystikos manages essential computing resources inside the TEE, such as CPU/threads, memory, files, networks, etc. It handles most of the syscalls that a normal operating system would handle (with limits). Many syscalls are handled directly by the kernel while others are delegated to the target.
Some distributions come with the SGX driver already installed; if it is, you don't need to re-install it. You can verify this by running:
dmesg | grep -i sgxIf the output is blank, install the driver manually by downloading it from Intel.
NOTE: The script below may not refer to the latest Intel SGX DCAP driver. Check Intel's SGX Downloads page to see if a more recent SGX DCAP driver exists.
sudo apt -y install dkms
wget https://download.01.org/intel-sgx/sgx-dcap/1.7/linux/distro/ubuntu18.04-server/sgx_linux_x64_driver_1.35.bin -O sgx_linux_x64_driver.bin
chmod +x sgx_linux_x64_driver.bin
sudo ./sgx_linux_x64_driver.binecho 'deb [arch=amd64] https://download.01.org/intel-sgx/sgx_repo/ubuntu bionic main' | sudo tee /etc/apt/sources.list.d/intel-sgx.list
wget -qO - https://download.01.org/intel-sgx/sgx_repo/ubuntu/intel-sgx-deb.key | sudo apt-key add -
sudo apt update
sudo apt -y install libsgx-enclave-common libsgx-dcap-ql libsgx-dcap-ql-devYou can download the latest build here then simply decompress it, add it to your path, and run it.
# change this to match the latest version
LATEST='0.1.2'
RELEASE="mystikos-${LATEST}-x86_64"
# this will create the "mystikos" directory within your current working directory
curl -sSL --ssl https://github.com/deislabs/mystikos/releases/download/v${LATEST}/${RELEASE}.tar.gz | tar -xzf -
# you can use mystikos from your home directory, or any path
export PATH="$PATH:$(pwd)/mystikos/bin"
You may also build Mystikos from source. In our experience, this takes about 20 minutes.
NOTE that Mystikos can only be built on Ubuntu 18.04 due to current limitations in Open Enclave SDK.
Eager to get started with Mystikos? We've prepared a few guides, starting from a simple "hello world" C program and increasing in complexity, including demonstrations of DotNet and Python/NumPy.
Give it a try and let us know what you think!
- A Simple "Hello World" in C: click here
- A Simple "Hello World" in Rust: click here
- Packaging your "Hello World" app in Docker: click here
- Introducing Enclave Configuration with a DotNet program: click here
- Running Python & NumPy for complex calculations: click here
Sometimes, you want to take advantage of specific properties of the Trusted Execution Environment, such as attestation. The following example shows how to write a C program which changes its behaviour when it detects that it has been securely launched inside an SGX enclave.
- Getting started with a TEE-aware program: click here
We've got plans for a lot more documentation as the project grows, and we'd love your feedback and contributions, too.
- Key features of Mystikos: click here
- Deep dive into Mystikos architecture: [coming soon]
- How to implement support for a new TEE: [coming soon]
- Kernel limitations: click here
- Multi-processing and multi-threading in Mystikos and limitations: [coming soon]
Looking for information to help you with your first PR? You've found the right section.
- Developer's jump start guide: click here
- Signing and packaging applications with Mystikos: click here
- Release management: click here
- Notable unsupported kernel features and syscalls: [coming soon]
For more information, see the Contributing Guide.
This project is released under the MIT License.
Please DO NOT open vulnerability reports directly on GitHub.
Security issues and bugs should be reported privately via email to the Microsoft Security Response Center (MSRC) at secure@microsoft.com. You should receive a response within 24 hours. If for some reason you do not, please follow up via email to ensure we received your original message.
This project has adopted the Microsoft Code of Conduct. All participants are expected to abide by these basic tenets to ensure that the community is a welcoming place for everyone.